February 03, 2015
News that's news: Kenya's M-Kopa Solar Closes $12.45m
 If there's any news worth blogging about, it is this:
If there's any news worth blogging about, it is this:
Breaking: Kenya's M-Kopa Solar Closes $12.45 million Fourth Funding Round
M-KOPA Solar has today closed its fourth round of investment through a $12.45 million equity and debt deal, led by LGT Venture Philanthropy. The investment will be used to expand the company's product range, grow its operating base in East Africa and license its technology to other markets.
Lead investor LGT Venture Philanthropy has backed M-KOPA since 2011 and is making its biggest investment yet in the fourth round, which also includes reinvestments from Lundin Foundation and Treehouse Investments (advised by Imprint Capital)and a new investment from Blue Haven Initiative.
In less than two and a half years since launch, M-KOPA Solar has installed over 150,000 residential solar systems in Kenya, Uganda and Tanzania, and is now connecting over 500 new homes each day. The company plans to further expand its distribution and introduce new products to reach an even larger customer base.
Jesse Moore, Managing Director and Co-Founder M-KOPA Solar says, "Our investors see innovation and scale in what M-KOPA does. And we see a massive unmet market opportunity to provide millions of off-gridhouseholds with affordable, renewable energy. We are just getting started in terms of the scale and impact of what we will achieve.
Oliver Karius, Partner, LGT Venture Philanthropy says, "We believe that we are at the dawn of a multi-billion dollar 'pay-as-you-go' energy industry. LGT Venture Philanthropy is a long-term investor in M-KOPA Solar because they've proven to be the market leaders,both in terms of innovating and delivering scale. We have also seen first-hand what positive impacts their products have on customers lives - making low-income households wealthier and healthier."
This deal follows the successful $20 million (KES1.8 billion) third round funding closed in December 2013 - which featured a working capital debt facility, led by the Commercial Bank of Africa.
The reason this is real news in the "new" sense is that indigenous solutions can work because they are tailored to the actual events and activities on the ground. In contrast, the western aid / poverty agenda typically doesn't work and does more harm than good, because it is an export of western models to countries that aren't aligned to those assumptions. Message to the west: Go away, we've got this ourselves.
August 24, 2014
On how to interface to regulation and law: follow Michael Jackson of Skype's advice
If you've ever wondered how to deal with the legal side of business, here's the answer, written out by someone who's done it:
To put it bluntly – every bitcoin actor should be reading the law very carefully and finding the loopholes. You should all invest a great deal of time in this – it is hugely important. For example, are you really moving ‘currency’ or are you simply exchanging some sort of token?Life is going to be a lot easier if we take the latter position, as there are no rules that prevent the exchanging of keys. Likewise there are no rules that say keeping a string of data in a cold storage vault makes a business a bank.
So far, many of the proponents of bitcoin have been taking entirely the wrong approach – making claims that attract a raft of unwanted rules and regulations.
Michael Jackson (former COO of Skype and current venture capital investor at Mangrove Capital Partners) has got Bitcoin community's number. I mean that in the sense that he understands, whereas they don't.
Don’t ask permissionCompanies need to just carry on doing what they are doing, if they can make a case for themselves that they don’t need regulation, they shouldn’t even go near it.
People do what they love best: regulators like regulations and want to apply them. If they didn’t, they would have a different job. So, asking for advice is framing the discussion. Once again, companies should read the rules, argue why they are not covered by the rules and use that analysis as a defence, but they should only ask for permission if they are sure it is necessary.
Furthermore, companies shouldn’t ask a lawyer. Expecting a lawyer to find a loophole in the law and to state it on paper simply won’t happen. People should read, understand and learn it themselves. They can test their argument on a lawyer, indeed on anyone, but should not expect anyone else to come up with it.
I feel so much less alone. If you're in a cryptocurrency startup, read that article.
May 11, 2014
(B) The Business Choice of making a Business Investment in Bitcoin (part B of ABC)
Last month, I launched a rocket at those who invest in Bitcoin as the Coin or the Currency. It's bad, but I won't repeat the arguments against it.
For those of you who've survived the onslaught on your sensitivities, and are genuinely interested in how to make an investment into the cryptocurrency world, here is part B: the Business! The good news is that it is shorter.
If one was to look for a good Bitcoin investment in a business, what would it be? I think you should be asking questions like these:
- The business in question has a regulatory model. It doesn't need to be right or sustainable, more that the business owners just need to understand the word. That's because, whether they know it or not, the word is coming for them one day.
- hey have a governance model. Ditto.
- You as investor understand the difference. This is where it gets messy. Most people think the above two terms are the same thing, but they are not. A regulatory model is imposed by a regulator, and is mostly about compliance with something that protects others such as the regulator or their flock (banks). Whereas a governance model is imposed by yourself, over your own operations, to protect your assets and the assets of the customer. Completely different, and completely misunderstood in the eyes of the external stakeholder community. Therefore, likely misaligned in the eyes of the Bitcoin CEO. Do you see where this is going?
- They have a Sean Parker. By this, I mean the person with real experience of this broad Internet / money / social networking business space, the guy who's been there twice before, and this time, *he's there* at the critical juncture to that 2 kids and a fridge full of beer all the way to a big business. See the Facebook movie if this doesn't make any sense.
Signs of a bad investment:
- Wanting to be the next big exchange.
- No relevant experience in the chosen direct business model. This is distinct from the Sean Parker point above. By this I mean, if wanting to do an exchange, the people have / do not have (select one) prior experience in what a daily trading model is, what 5PM is, what governance is, what an internet security model is. E.g., Mt Gox, which traded without understanding any of these things.
- Belief that tech solves all problems.
- No knowledge of what came before the Bitcoin paper.
- Deal hinges in part on banks or regulators. For example, these guys are DITW:
Part of laying the groundwork is bringing the establishment on board, Malka said. “We need more banks participating in this. We need regulators. I’m part of the Bitcoin Foundation – we are out there trying to educate regulators.” Getting regulators on board will help get the banks to come along, Liew predicted. “If the regulators explicitly set forth rules that say, ‘Bright line, do this, you will find a bank that is willing to take on bitcoin customers,’” Liew said.
That's my B list so far. You'll note that it includes no conventional things, because you already have those. All it includes is pointers to the myths-of-doom peddled in the current bitcoin world as business talk. It's designed to separate out the happy hopefuls from the actual business possibilities, in a world where talking is deeper than walking.
Next up, when I get to it, is my A list: a point I believe so important I saved it for another post. Watch this space.
February 03, 2014
FC++ -- Bitcoin Verification Latency -- The Achilles Heel for Time Sensitive Transactions
New paper for circulation by Ken Griffith and myself:
Bitcoin Verification Latency
The Achilles Heel for Time Sensitive TransactionsAbstract.Bitcoin has a high latency for verifying transactions, by design. Averaging around 8 minutes, such high latency does not resonate with the needs of financial traders for speed, and it opens the door for time-based arbitrage weaknesses such as market timing attacks. Although perhaps tractable in some markets such as peer to peer payments, the Achilles heel of latency makes Bitcoin unsuitable for direct trading of financial assets, and ventures seeking to exploit the market for financial assets will need to overcome this burden.
As with the Gresham's paper, developments moved fast on this question, and there are now more ventures looking at the contracts and trading question. For clarification, I am the secondary author, Ken is lead.
October 29, 2013
Confirmed: the US DoJ will not put the bankers in jail, no matter how deep the fraud
 I've often asked the question why no-one went to jail for the frauds of the financial crisis, and now the US government has answered it: they are complicit in the cover-up, which means that the financial rot has infected the Department of Justice as well. Bill Black writes about the recent Bank of America verdict:
I've often asked the question why no-one went to jail for the frauds of the financial crisis, and now the US government has answered it: they are complicit in the cover-up, which means that the financial rot has infected the Department of Justice as well. Bill Black writes about the recent Bank of America verdict:
The author of the most brilliantly comedic statement ever written about the crisis is Landon Thomas, Jr. He does not bury the lead. Everything worth reading is in the first sentence, and it should trigger belly laughs nationwide.
Bank of America, one of the nation’s largest banks, was found liable on Wednesday of having sold defective mortgages, a jury decision that will be seen as a victory for the government in its aggressive effort to hold banks accountable for their role in the housing crisis."
“The government,” as a statement of fact so indisputable that it requires neither citation nor reasoning, has been engaged in an “aggressive effort to hold banks accountable for their role in the housing crisis.” Yes, we have not seen such an aggressive effort since Captain Renault told Rick in the movie Casablanca that he was “shocked” to discover that there was gambling going on (just before being handed his gambling “winnings” which were really a bribe).
There are four clues in the sentence I quoted that indicate that the author knows he’s putting us on, but they are subtle. First, the case was a civil case. “The government’s” “aggressive effort to hold banks accountable” has produced – zero convictions of the elite Wall Street officers and banks whose frauds drove the crisis. Thomas, of course, knows this and his use of the word “aggressive” mocks the Department of Justice (DOJ) propaganda. The jurors found that BoA (through its officers) committed an orgy of fraud in order to enrich those officers. That is a criminal act. Prosecutors who are far from “aggressive” prosecute elite frauds criminally because they know it is essential to deter fraud and safeguard our financial system. The DOJ refused to prosecute the frauds led by senior BoA officers. The journalist’s riff is so funny because he portrays DOJ’s refusal to prosecute frauds led by elite BoA officers as “aggressive.” Show the NYT article to friends you have who are Brits and who claim that Americans are incapable of irony. The article’s lead sentence refutes that claim for all time.
The twin loan origination fraud epidemics (liar’s loans and appraisal fraud) and the epidemic of fraudulent sales of the fraudulently originated mortgages to the secondary market would each – separately – constitute the most destructive frauds in history. These three epidemics of accounting control fraud by loan originators hyper-inflated the real estate bubble and drove our financial crisis and the Great Recession. By way of contrast, the S&L debacle was less than 1/70 the magnitude of fraud and losses than the current crisis, yet we obtained over 1,000 felony convictions in cases DOJ designated as “major.” If DOJ is “aggressive” in this crisis what word would be necessary to describe our approach?
Read on for the details of how Bill Black forms his conclusion.

May 01, 2013
MayDay! MayDay! British Banking Launches new crisis of titanic proportions...
 Yes, it's the first of May, also known as May Day, and the communist world's celebration of the victory over capitalism. Quite why MayDay became the international distress message over radio is not known to me, but I'd like to know!
Yes, it's the first of May, also known as May Day, and the communist world's celebration of the victory over capitalism. Quite why MayDay became the international distress message over radio is not known to me, but I'd like to know!
Meanwhile, the British Banking sector is celebrating its own version of MayDay:
The bank went through their customer base and identified which businesses were asset rich and cash poor.Typically, the SME (small to medium enterprise) would require funding for expansion or to cover short term exposures, and the bank’s relationship manager would work with the business owner on a loan funding cover.
The loan may be for five or ten years, and the relationship manager would often call the client after a short time and say “congratulations, you’ve got the funding”.
The business owner would be delighted and would start committing the funds.
Only then would the relationship manager call them back and say, “ah, we have a concern here about interest rates”.
This would start the process of the disturbance sale of the IRSA.
The rest you can imagine - the bank sold an inappropriate derivative with false information, and without advising the customer of the true costs. This time however the costs were more severe, as it seems that many such businesses went out of business in whole or in part because of the dodgy sale.
In particular, the core issue is that no-one has defined whether the bank will be responsible for contingent liabilities.The liabilities are for losses made by those businesses that were mis-sold these products and, as a result, have now gone into bankruptcy or been constrained so much that they have been unable to compete or grow their business as they would have if they had not taken these products.
 Ouch! I have to applaud Chris Skinner and the Financial Services Club here for coming forth with this information. It is time for society to break ranks here and start dealing with the banks. If this is not done, the banks will bring us all down, and it is not clear at all that the banks aren't going to do just that.
Ouch! I have to applaud Chris Skinner and the Financial Services Club here for coming forth with this information. It is time for society to break ranks here and start dealing with the banks. If this is not done, the banks will bring us all down, and it is not clear at all that the banks aren't going to do just that.
Meanwhile back to the scandal du jour. We are talking about 40k businesses, with average suggested compensation of 2.5 million quid - so we are already up to a potential exposure of 100 billion pounds. Given this, there is no doubt that even the most thickest of the dumbest can predict what will happen next:
Mainly because of the Parliamentary investigation, the Financial Services Authority was kicked into action and, on June 29 2012, announced that it had found "serious failings in the sale of IRSAs to small and medium sized businesses and that this has resulted in a severe impact on a large number of these businesses.”However, it then left the banks to investigate the cases and work out how to compensate and address them .
The banks response was released on January 31 2013, and it was notable that between the June announcement and bank response in January that the number of cases rose from 28,000 to 40,000. It was also noteworthy that of those 40,000 cases investigated, over 90% were found to have been mis-sold. That’s a pretty damning indictment.
Even then the real issue, according to Jeremy [of Bully Banks], is that the banks are in charge of the process.
Not only is the fox in charge of the chickens, it's also paying off them off for their slaughter. Do we really need to say more? The regulators are in bed with the banks in trying to suppress this scandal.
Obviously, this cunning tactic will save poor banks money and embarrassment. But the emerging problem here is that, as suggested many times in this blog (e.g., 2, 3, 4, ...) and elsewhere, the public is now becoming increasingly convinced that banks are not healthy, honest members of society.
 Which is fine, as long as nothing happens.
Which is fine, as long as nothing happens.
But I see an issue emerging in the next systemic shock to hit the financial world: if the public's patience is exhausted, as it appeared to be over Cyprus, then the next systemic shock is going to cause the collapse of some major banks. For right or wrong, the public is not going to accept any more talk of bailouts, taxpayer subsidies, etc etc.
The chickens are going to turn on the foxes, and they will not be satisfied with anything less than blood.
One hopes that the old Lady's bank tear-down team is boned up and ready to roll, because they'll be working hard soon.
December 16, 2012
Broadly Technical at Mobile Payments Startup (while musing on the impossibility of the reliable social network)
I'm now back in the payments space after a long hiatus. To draw a line from the past, I had a go at updating LinkedIn (yes, that business social network site that everyone complains about and everyone uses) to reflect that, and it just gave me the sense of how bad these systems really are. Minor point is that it insists on a job title - which means what? More oddly, the site led me into the endorsements section and the inevitable flood of claims over people I know.
The end result was? Noise. Looking at the results such as others endorsements over self, there is so much noise -- impossible claims, unlikely falsehoods and let's face it, lies -- in the system that the overall result is unreliable.
I mean that in a specific sense -- The system's only value is found when you are not relying on it. Therefore worthless, QED.
As my friend Ken has it, any claim is only worth the risk you take on it. Since social networking involves no risk, value is capped at somewhere between noise and zero.
But it doesn't have to be that way. In deep contrast, a claim made in CAcert's community of Assurers is worth something. The risk is that you can be arbitrated against for false claims, and people have been. That's a risk -- it might not be easy to put a number on that risk, but it is still a tangible, touchable and definable risk. It's painful when it happens, it's unforgettable.
Other systems and places in society have this worked out. For example, they make you sign statements on paper with words to effect "I make these statements as if in front of a judge and will be found guilty of perjury if I lie." So it is not as if the solutions aren't out there, and by some lights, what happened at CAcert was simply a copy of these other systems. To make light of the CAcert success - it is engineerable and it can be done.
We can imagine a reliable social network, but it seems an unlikely fit with the current vision.
Where existing social networks will fall down in my opinion is that they are too light-weight, almost risk-free. One cannot see the marketing-heavy approach working, one can only see the network collapsing as mouthpieces try and turn their customer base from a lightweight graph into a reliable society. Making someone reliable means turning thumbscrews on them, and every social network is based on exactly not doing that - they promise a pain-free environment, and beyond a certain measure of customer mass, this ensures a value-free environment.
And, counterintuitively, this is why I'm back in the payments space. It is my view that if you want to create a reliable community, you need to do it with thumbscrews. In this case, the payments world has the contractual thumbscrew known as the payment. If Alice pays Bob, they've both got skin in the game, as the North American expression has it. The payments world already gives us cryptographically basis for payments, and therefore for reliable claims.
I'm not talking here about Java crypto and secure receipts and invoicing messages and so forth - all the good old cryptoplumber magic in the last cycle. The really interesting question is the old FC7 thesis -- what are we going to do with it? I don't know the answer as yet but I do know what I'm thinking at a conceptual level: the reliable society.
December 14, 2011
the five parties model, and SPDR GLD invites users to play spot-your-gold-bar
Back in the old days, I invented the five parties model so as to protect static assets that had to be protected. I don't have a good URL for it, because to a large extent I was still in my pre-naivete phase, in which I thought this stuff is basic engineering, don't bother me with doco.
So in brief: A repository stores the metal, on behalf of the issuer of a financial instrument. A signatory, independently to the issuer signs incoming and outgoing metal, so as to stop the secret sales of metal. A Manager receives customer metal and disburses out of a kitty, and interacts via the signatory into the repository for large amounts. Finally, all of the preceeding 4 parties publish reports in real time to the fifth party, the public, who relies on the reports to guard against fudged account and re-use of assets, a.k.a. theft and fraud.
It's as easy as 1,2,3,4,5. Or so I thought:
...just ask Gerald Celente what happened to his so-called gold held at MF Global, or as it is better known now: "General Unsecured Claim", which may or may not receive a pennies on the dollar equitable treatment post liquidation. What, however, was less known is that physical gold in the hands of the very same insolvent financial syndicate of daisy-chained underfunded organizations, where the premature (or overdue) end of one now means the end of all, is also just as unsafe, if not more. Which is why we read with great distress a just broken story by Bloomberg according to which HSBC, that other great gold "depository" after JP Morgan (and the custodian of none other than GLD) is suing MG Global "to establish whether he or another person is the rightful owner of gold worth about $850,000 and silver bars underlying contracts between the brokerage and a client."
In short, the legal titleholder of the silver (MF Global) seems to have re-used the metal of customers, in a process known as hypothecation. Apparently legal, but definately dodgy. As, when MF Global went down due to increasing margin calls on dodgy financial calls, the creditors were left to sort out the opposing positions. Which causes a crisis in faith in the system itself:
Silver positions are being liquidated by COMEX traders after the MF Global fiasco uncovered the fragility of paper assets. ... The issue has been worsened as the CME Group has been unable to refund investor money even after a month after the MF Global filed for bankruptcy. Many traders have pulled out their money from the markets while many are advising others to close their paper trading accounts and instead focus on the physical metal itself.
Now, my view on this was clear: don't do that! The metal held on trust should have been simply held with one-to-one ties between the physics and the paper. Although it is common practice with other assets to loan out customer assets ( http://www.zerohedge.com/news/shadow-rehypothecation-infinte-leverage-and-why-breaking-tyrrany-ignorance-only-solution ) that shouldn't be done with gold or arguably with silver. Precious metal's special feature is its vote against the financial system, which it only preserves when done simply. Not in complexity.
Another point of favourite polemic from those days was whether the gold was ever really there in the first place. Many observers didn't really trust the repositories, a point which was underscored when LBMA announced a few years back that for the first time in around a century, it would start assaying bars at random. How do we know the bars that have been in there for decades are really bars at all?
Auditing technique such as point-in-time spot checks are good ones for flushing out long-lived frauds: tell me right now, on the spot, which is my gold! And then I'll count it. Maybe assay it too.

My idea here in the sense of open governance was to have well known representatives of the body public come in and also audit the stuff. Unlike auditors who were hopelessly conflicted, the five parties thesis said that users could be responsible for auditing the system, *iff* they were given the tools. Then, I too would be delighted that this idea has come of age:
... we were delighted to see that after years of ridicule and provocations, the SPDR GLD ETF finally cracked and decided to do a wholesale PR campaign to comfort the investing public it actually does own its gold, by inviting none other than Bob Pisani in its secret warehouse which allegedly contains 40 million ounces of gold,
When an unbiased user goes in there and touches the gold, she has no particular incentive to do anything than report what is seen. All parties are incentivised to make it real. Or so we thought:
While the 4 minute PR campaign is enjoyable and we invite readers to watch it, what is amusing is that it is sure to set off another set of conspiracy theories. Here's the reason: amusingly the very gold bar that Pisani demonstrates so eagerly for the camera, Rand Refineries ZJ6752, is somehow, at last check, missing from the full barlist as posted daily by the GLD. Whose is it? Where did it go? When was this clip shot? Inquiring minds want to know...
Oops! Not their bar... At the direct level, the visit by none-other-than Bob Pisani proved *NOTHING* about the reserves of gold. It did show that the issuer SPDR GLD ETF felt that it could do a pretty marketing presentation, and that would substitute for real governance.
It did however prove everything about the five parties model and the wider question of open governance: The User closes the circle, if the circle exists and can be closed. Read the above post for the conspiracy theories and supporting analysis that the bar so displayed was not "in the vault" at all. I'll just leave you with this insight into open governance:
Our advice: please tell your client HSBC to open up its vault to general observation and assay: at that point, we are confident all conspiracies will end. Until then, be prepared to be retained by HSBC on a frequent basis as more and more ask themselves: what is really in that vault?
The users have called SPDR GLD ETF's bluff. Is there gold in the vaults? To me, this stinks, and raises a sell question over SPDR GLD. Just as you insist on real gold in your real issuance of Internet gold, don't go short on the governance. Insist on full open governance with five parties in control. Demand those reports, insist on independent visits.
Now, more than ever. Chances are good that everyone will see their governance model tested within the next 12 months.
August 07, 2011
Regulating the future financial system - the double-entry headache needs a triple-entry aspirin
How to cope with a financial system that looks like it's about to collapse every time bad news turns up? This is an issue that is causing a few headaches amongst the regulators. Here's some musings from Chris Skinner over a paper from the Financial Stability gurus at the Bank of England:
Third, the paper argues for policies that create much greater transparency in the system.This means that the committees worldwide will begin “collecting systematically much greater amounts of data on evolving financial network structure, potentially in close to real time. For example, the introduction of the Office of Financial Research (OFR) under the Dodd-Frank Act will nudge the United States in this direction.
“This data revolution potentially brings at least two benefits.
“First, it ought to provide the authorities with data to calibrate and parameterise the sort of network framework developed here. An empirical mapping of the true network structure should allow for better identification of potential financial tipping points and cliff edges across the financial system. It could thus provide a sounder, quantitative basis for judging remedial policy actions to avoid these cliff edges.
“Second, more publicly available data on network structures may affect the behaviour of financial institutions in the network. Armed with greater information on counterparty risk, banks may feel less need to hoard liquidity following a disturbance.”
Yup. Real time data collection will be there in the foundation of future finance.
But have a care: you can't use the systems you have now. That's because if you layer regulation over policy over predictions over datamining over banking over securitization over transaction systems … all layered over clunky old 14th century double entry … the whole system will come crashing down like the WTC when someone flies a big can of gas into it.
The reason? Double entry is a fine tool at the intra-corporate level. Indeed, it was material in the rise of the modern corporation form, in the fine tradition of the Italian city states, longitudinal contractual obligations and open employment. But, double entry isn't designed to cope with the transactional load of of inter-company globalised finance. Once we go outside the corporation, the inverted pyramid gets too big, too heavy, and the forces crush down on the apex.
It can't do it. Triple entry can. That's because it is cryptographically solid, so it can survive the rigours of those concentrated forces at the inverted apex. That doesn't solve the nightmare scenarios like securitization spaghetti loans, but it does mean that when they ultimately unravel and collapse, we can track and allocate them.
Message to the regulators: if you want your pyramid to last, start with triple entry.
PS: did the paper really say "More taxes and levies on banks to ensure that the system can survive future shocks;" … seriously? Do people really believe that Tobin tax nonsense?
January 31, 2011
Zuckerberg urged to go social... by hacking the lending space?
There's something poignant about this:
A bug allowed an unidentified person to post a message on Facebook chief executive Mark Zuckerberg's fan page on Tuesday.The odd message garnered more than 1,800 'likes' and around 400 comments before it was taken down. The message read:
"Let the hacking begin: If facebook needs money, instead of going to the banks, why doesn't Facebook let its users invest in Facebook in a social way? Why not transform Facebook into a 'social business' the way Nobel Price [sic] winner Muhammad Yunus described it?"
The social network meets social lending. In some sort of whiteboarding sense, this could be done. If Facebook had good payments tech, a good marketplace, and a good offering, then something like a social-net investment could emerge within. Many plausible alternatives exist such as Spring Street or Zopa, and all of them are fun to talk about.
But realities interfere somewhat to make this a workable idea. Facebook exists in an environment that would mitigate against Facebook itself getting involved; the regulatory and media attention to its business is rather different to that of Bangladesh 30 years ago. Also, the challenge for Facebook is not to tap the social network to solve a problem for its people, but to monetarise its network in time for IPO. Grameen's concept is too small-scale to effect that need much, and Spring Street was demonstrably at the opposite end of a very long scale.
October 16, 2010
Skype -- the mobile leader?!
Finanser posted this great picture from Sameer Zafar on mobile payment systems:
in commenting on some talks from Safar and Dave Birch. Well, you probably had to be there, but the picture is quite a compelling one, if you're interested in Skype, VoIP and the mobile market. For reading, these are probably more useful:
Dave [Birch] developed on his themes, and presented one slide that was incredibly insightful statistically speaking. There are:
- 5 billion active mobile phone subscribers out there
- 4.1 billion actively used mobile telephones
- 4 billion text message users, increasing at 19% per annum
- 2.2 billion bank accounts in use
- 1.6 billion television sets
- 1.4 billion email users, increasing at 7% per annum
- 1.25 landlines at its peak, as there are now 1.15 billion and falling
- 1.2 PCs of any kind
According to Dave's research, half of all phones In the developing world are 3G and a third are smartphones whilst, in the emerging world, only 4% of all phones are 3G and 8% are smart. Meanwhile, 1 in 10 phones are never used for voice calls, and data now represents a quarter of all mobile revenues.
Which leads into an old theme here at FC: what's with Skype and payments?
September 04, 2010
UN convention on Electronic Transactions: knowns and unknowns
Someone at the UN has a clue about financial transactions [1]. In the UNCITRAL's Convention on Electronic Transactions, there is this (pp2):
Article 2. Exclusions2.1. This Convention does not apply to electronic communications relating to any of the following:
(a) contracts concluded for personal, family or household purposes;
(b) (i) transactions on a regulated exchange; (ii) foreign exchange transactions;
(iii) inter-bank ... systems... ; (iv) the transfer of security rights....
2.2. This Convention does not apply to bills of exchange [snip, similar] ... or any transferable document or instrument that entitles the bearer or beneficiary to claim the delivery of goods or the payment of a sum of money.
The first lot (a) are approximately consumer contracts, which ordinarily attract specific consumer contract protection.
The second group (b) and 2.2 are financial transactions that will resonate with all financial cryptographers. Here's what the document observed in the Explanatory note (pp14):
7. ... These transactions have been excluded because the financial service sector is already subject to well-defined regulatory controls and industry standards that address issues relating to electronic commerce in an effective way for the worldwide functioning of that sector.
And (pp34):
78. The transactions in paragraph 1(b) relate essentially to certain financial service markets governed by well-defined regulatory and contractual rules that already address issues relating to electronic commerce in a manner that allows for their effective worldwide functioning. Given the inherently cross-border nature of those markets, UNCITRAL considered that this exclusion should not be left for country-based declarations under article 19.
So, because these transactions are sufficiently well designed and resolved in the first place, no need for the UNCITRAL to stick its oar in. Another way of putting it is that anyone engaged in those headline activities is big enough and ugly enough to look after themselves.
However, UNCITRAL went on to lay out a more rigourous rationale for their exclusion. Firstly (in my order), they observe:
... the Convention does not apply to negotiable instruments or documents of title, in view of the particular difficulty of creating an electronic equivalent of paper-based negotiability, a goal for which special rules would need to be devised.
In other words, the UNCITRAL people had not seen how to do this, and they knew it was a hard problem. Proving the asset in qualitative form, as a document in paper or electronic form, was the role of the Ricardian Contract. Its rather odd digitally-signed form was directed at proving equivalence with paper form, something we called the rule of one contract or more shortly, prove the electronic form to the judge!
Yes, it's a hard problem. Empirically, only a few times has the Ricardian Contract been copied as a way to cut the gordian knot of digital description of contracts. The problem is as much conceptual as anything, as those expert in technology typically start from an assumption of a database, which unfortunately clashes with the legal foundation of contracts. This fruitless chase down a blind alley is something that neither the lawyers nor the technologists really appreciate until they've spent all their investment.
Moreover (pp35):
80. Paragraph 2 of article 2 excludes negotiable instruments and similar documents because the potential consequences of unauthorized duplication of documents of title and negotiable instruments—and generally any transferable instrument that entitles the bearer or beneficiary to claim the delivery of goods or the payment of a sum of money—make it necessary to develop mechanisms to ensure the singularity of those instruments.81. The issues raised by negotiable instruments and similar documents, in particular the need for ensuring their uniqueness, go beyond simply ensuring the equivalence between paper and electronic forms, which is the main aim of the Electronic Communications Convention and justifies the exclusion provided in paragraph 2 of the article. ...
My emphasis. What UNCITRAL refers to as the need to ensure uniqueness and singularity is the quantitative challenge of the payment system, aspects that can be seen in SOX, and also DigiCash's design to do rollovers of blinded coins.
Finally, there is this seemingly accidental flash of wisdom:
79. It should be noted that this provision does not contemplate a broad exclusion of financial services per se, but rather specific transactions such as payment systems, negotiable instruments, derivatives, swaps, repurchase agreements, foreign exchange and bond markets. The criterion for the exclusion in paragraph 1(b) is not the type of the asset being traded but the method of settlement used ...
Which, indeed gets right to the heart of of the ultimate test. Once we have cracked the equivalence issue, and qualitatively locked down the value in a payment system, what remains is to settle trades. Trading is easy, settlement is hard. With that one simple test, we can identify whether the entire architecture is solid, which for UNCITRAL's purposes, means whether the overall system meets their exclusion.
Kudos to the UNCITRAL team for having enough understanding of the financial minefield to know what they were up against, and stepping aside carefully. As they summarise, which I interpret for all three of the key design challenges raised:
81 ... UNCITRAL was of the view that finding a solution for this problem required a combination of legal, technological and business solutions, which had not yet been fully developed and tested.
What they see as a known unknown, is also an unknown known :) But it is fair to say that the deployment of financial cryptography that solves the issues they identify is not as widespread as we had hoped. The solutions are known, it will just take a lot longer for them to percolate.
[1] I found the information used in this post in the Standing Committee of Australian Attorneys-General' review on the Convention (look for consultation paper, November 2008).
September 18, 2009
Where does the accounting profession want to go, today?
 So, if they are not doing audits and accounting, where does the accounting profession want to go? Perhaps unwittingly, TOdd provided the answer with that reference to the book Accounting Education: Charting the Course through a Perilous Future by W. Steve Albrecht and Robert J. Sack.
So, if they are not doing audits and accounting, where does the accounting profession want to go? Perhaps unwittingly, TOdd provided the answer with that reference to the book Accounting Education: Charting the Course through a Perilous Future by W. Steve Albrecht and Robert J. Sack.
It seems that Messrs Albrecht and Sack, the authors of that book, took the question of the future of Accounting seriously:
Sales experts long ago concluded that "word of mouth" and "personal testimonials" are the best types of advertising. The Taylor Group1 found this to be true when they asked high school and college students what they intended to study in college. Their study found that students were more likely to major in accounting if they knew someone, such as a friend or relative, who was an accountant.
So they tested it by asking a slightly more revealing question of the accounting professionals:
When asked "If you could prepare for your professional career by starting college over again today, which of the following would you be most likely to do?" the responses were as follows:
Type of Degree % of Educators Who Would % of Practitioners Who Would Who Would Earn a bachelor's degree in something other than accounting and then stop 0.0 7.8 Earn a bachelor's degree in accounting, then stop 4.3 6.4 Earn a Master's of Business Administration (M.B.A.) degree 37.7 36.4 Earn a Master's of Accountancy degree 31.5 5.9 Earn a Master's of Information Systems degree 17.9 21.3 Earn a master's degree in something else 5.4 6.4 Earn a Ph.D. 1.6 4.4 Earn a J.D. (law degree) 1.6 11.4 These results are frightening,...
Well indeed! As they say:
It is telling that six times as many practicing accountants would get an M.B.A. as would an M.Acc., over three times as many practitioners would get a Master's of Information Systems degree as would get an M.Acc., and nearly twice as many practitioners would get a law degree instead of an M.Acc. Together, only 12.3 percent (6.4% + 5.9%) of practitioners would get either an undergraduate or graduate degree in accounting.2 This decrease in the perceived value of accounting degrees by practitioners is captured in the following quotes:We asked a financial executive what advice he would give to a student who wanted to emulate his career. We asked him if he would recommend a M.Acc. degree. He said, "No, I think it had better be broad. Students should be studying other courses and not just taking as many accounting courses as possible. ...My job right now is no longer putting numbers together. I do more analysis. My finance skills and my M.B.A. come into play a lot more than my CPA skills.
.... we are creating a new course of study that will combine accounting and
information technology into one unique major.......I want to learn about information systems.
(Of course I'm snipping out the relevant parts for speed, you should read the whole lot.) Now, we could of course be skeptical because we know computing is the big thing, it's the first addition to the old list of Reading, Arithmetic and Writing since the dark ages. Saying that Computing is core is cliche these days. But the above message goes further, it's almost saying that Accountants are better off not doing accounting!
The Accounting profession of course can be relied upon to market their profession. Or can they? Todd was on point when he mentioned the value chain, the image in yesterday's post. Let's look at the wider context of the pretty picture:
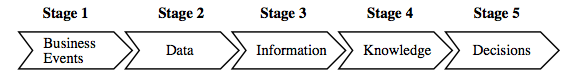
Robert Elliott, KPMG partner and current chairman of the AICPA, speaks often about the value that accountants can and should provide. He identifies five stages of the "value chain" of information. The first stage is recording business events. The second stage is summarizing recorded events into usable data. The third stage is manipulating the data to provide useful information. The fourth stage is converting the information to knowledge that is helpful to decision makers. The fifth and final stage is using the knowledge to make value-added decisions. He uses the following diagram to illustrate this value chain:This five-stage breakdown is a helpful analysis of the information process. However, the frightening part of Mr. Elliott's analysis is his judgment as to what the segments of the value chain are worth in today's world. Because of the impact of technology, he believes that:
- Stage 1 activity is now worth no more than $10 per hour
- Stage 2 activity is now worth no more than $30 per hour
- Stage 3 activity is now worth $100 per hour
- Stage 4 activity is now worth $300 per hour
- Stage 5 activity is now worth $1,000 per hour
In discussing this value chain, Mr. Elliott urges the practice community to focus on upper-end services, and he urges us to prepare our students so they aim toward that goal as well. Historically, accounting education has prepared students to perform stage 1- and stage 2-type work.
Boom! This is compelling evidence. It might not mean that the profession has abandoned accounting completely. But it does mean that whatever they do, they simply don't care about it. Accounting, and its cousin Audits are loss-leaders for the other stuff, and eyes are firmly fixed on other, higher things. We might call the other stuff Consulting, and we might wonder at the correlation: consulting activities have consumed the major audit firms. There are no major audit firms any more, there are major consulting firms, some of which seem to sport a vestigial audit capability.
Robert Elliot's message is, more or less, that the audit's fundamental purpose in life is to urge accountancy firms into higher stages. It therefore matters not what the quality (high?) is, nor what the original purpose is (delivering a report for reliance by the external stakeholder?). We might argue for example whether audit is Stage 2 or Stage 3. But we know that the auditor doesn't express his opinion to the company, directly, and knowledge is the essence of the value chain. By the rules, he maintains independence, his opinion is reserved for outsiders. So audit is limited to Stages 3 and below, by its definition.
Can you see a "stage 4,5 sales opportunity" here?
Or perhaps more on point, can you avoid it?
It is now very clear where the auditors are. They're not "on audit" but somewhere higher. Consulting. MBA territory. Stage 5, please! The question is not where the accounting profession wants to go today, because they already got there, yesterday. The financial crisis thesis is confirmed. Audits are very much part of our problem, even if they are the accounting profession's solution.
What is less clear is where are we, the business world? The clients, the users, the reliers of audit product? And perhaps the question for us really is, what are we going to do about it?
September 02, 2009
Robert Garigue and Charlemagne as a model of infosec
Gunnar reports that someone called Robert Garigue died last month. This person I knew not, but his model resonates. Sound bites only from Gunnar's post:
"It's the End of the CISO As We Know It (And I Feel Fine)"......First, they miss the opportunity to look at security as a business enabler. Dr. Garigue pointed out that because cars have brakes, we can drive faster. Security as a business enabler should absolutely be the starting point for enterprise information security programs.
...Secondly, if your security model reflects some CYA abstraction of reality instead of reality itself your security model is flawed. I explored this endemic myopia...
This rhymes with: "what's your business model?" The bit lacking from most orientations is the enabler, why are we here in the first place? It's not to show the most elegant protocol for achieving C-I-A (confidentiality, integrity, authenticity), but to promote the business.

How do we do that? Well, most technologists don't understand the business, let alone can speak the language. And, the business folks can't speak the techno-crypto blah blah either, so the blame is fairly shared. Dr. Garigue points us to Charlemagne as a better model:
King of the Franks and Holy Roman Emperor; conqueror of the Lombards and Saxons (742-814) - reunited much of Europe after the Dark Ages.He set up other schools, opening them to peasant boys as well as nobles. Charlemagne never stopped studying. He brought an English monk, Alcuin, and other scholars to his court - encouraging the development of a standard script.
He set up money standards to encourage commerce, tried to build a Rhine-Danube canal, and urged better farming methods. He especially worked to spread education and Christianity in every class of people.
He relied on Counts, Margraves and Missi Domini to help him.
Margraves - Guard the frontier districts of the empire. Margraves retained, within their own jurisdictions, the authority of dukes in the feudal arm of the empire.
Missi Domini - Messengers of the King.
In other words, the role of the security person is to enable others to learn, not to do, nor to critique, nor to design. In more specific terms, the goal is to bring the team to a better standard, and a better mix of security and business. Garigue's mandate for IT security?
Knowledge of risky things is of strategic valueHow to know today tomorrow’s unknown ?
How to structure information security processes in an organization so as to identify and address the NEXT categories of risks ?
Curious, isn't it! But if we think about how reactive most security thinking is these days, one has to wonder where we would ever get the chance to fight tomorrow's war, today?
July 13, 2009
Goldman Sachs caught with their pants down?
In the world of trading there is a scandal erupting. At first blanche, it was just another insider job. JPMay points to "Goldman: Pwned?". Snippets to get the general thrust. Firstly, GS drops off the trading reports:
This week's NYSE Program Trading report was very odd: not only because program trading hit 48.6% of all NYSE trading, a record high ... but what was shocking was the disappearance of the #1 mainstay of complete trading domination (i.e., Goldman Sachs) from not just the aforementioned #1 spot, but the entire complete list. In other words: Goldman went from 1st to N/A in one week.
Matt Goldstein apparently led the story, reporting that they were inside-hacked, asking "Did someone try to steal Goldman Sachs' secret sauce?"
... a Russian immigrant living in New Jersey was being held on federal charges of stealing secret computer trading codes from [Goldman Sachs].
So, the press made a lot about how this, but it is old news. For the techies reading today, here is how they said they 'got their man':
...the affidavit that Zerohedge has makes clear what they claim they've got this guy cold on - the "bash history" file they're referring to is a Unix system log that the "shell", or command interpreter, automatically keeps. Said alleged offender apparently was aware of this file and tried to erase it after doing his deed, but was unaware that the system he was working on had auditing enabled (oops.)
"Industrial espionage is nothing new of course." Nor is logging the activities of insiders :) This is a standard requirement imposed by audits, whether you like it or not, whether you can do it or not. However, the story grows bigger. This open comment lays it out:
...GS, through access to the system as a result of their special gov't perks, was/is able to read the data on trades before it's committed, and place their own buys or sells accordingly in that brief moment, thus allowing them to essentially steal buttloads of money every day from the rest of the punters world.
The unbacked, unevidenced allegation in the popular blogs is this: the code that was stolen might be been the code that drove a system that "saw" others' trades before they could be executed. More technically, it is claimed:
The big ticket, the magic wand for a rogue quant shop is technology to grab off FIX PROTOCOL, OCX, or SWIFT messages that precede every transaction_commit at the Exchanges.
If true in fact, this is almost guaranteed to lead to front-running. That is, if Goldman Sachs has any such magic wand, they would need to be bona fide arch-angels to avoid the temptation to read the trades coming, and beat them into the market. We're not talking millions here, but billions, or as that blog claimed "The profitability of this split-second information advantage would have been and could have been extraordinary. Observed yielding profits at $100,000,000 a day."
The structural details match: they are given special access for various reasons, and they are on the relevant security committees. Which is perversely backed by the actual claims of the bank:
Assistant U.S. Attorney Joseph Facciponti told a federal magistrate judge at his July 4 bail hearing in New York. The 34-year-old prosecutor also dropped this bombshell: “The bank has raised the possibility that there is a danger that somebody who knew how to use this program could use it to manipulate markets in unfair ways.”
Unlike most other claims written here, this has some degree of reliance. If the prosecutor said it, then, more or less, Goldman Sachs said it. And, the guy from Bloomberg asked the right question:
How could somebody do this? The precise answer isn’t obvious -- we’re talking about a black-box trading system here. And Facciponti didn’t elaborate. You don’t need a Goldman Sachs doomsday machine to manipulate markets, of course. A false rumor expertly planted using an ordinary telephone often will do just fine.
If it is an honest trading system, it can't manipulate the market. Except by volume and sneaky trades and false rumours and so forth, but that is the market. As long as everyone is under the same rules, they are in the market. Goldman Sachs can only manipulate the market if it is in possession of information that others do not have.
The final word seems to go to thefinanser in the UK, which deliciously juxtaposed Goldman's responses to salacious gossip in a popular mag:
The story actually goes back to when Goldmans announced last week that they were fed up with rock mag, Rolling Stone, over a piece claiming that the bank had “engineered every major market manipulation since the Great Depression — and they’re about to do it again.”Goldmans responded that it was “hysterical in both senses of the word” and that the magazine had “cobbled together every conspiracy theory ever written about us and injected some hyperbole and lots of bad language and called it a story.”
back to back with the prosecutor's filed statements before court:
The problem is that in their case against this guy, Sergey Aleynikov (a Russian immigrant no less, how James Bond is this getting?), the bank's lawyer made the statement that this “raised the possibility that there is a danger that somebody who knew how to use this program could use it to manipulate markets in unfair ways.”So, the program can be used to manipulate markets, can it?
Goldmans has virtually admitted as much, and no-one is going to let them off the hook.
In fact, GATA (the Gold Anti-Trust Committee) has already raised questions with “the U.S. Securities and Exchange Commission and the U.S. Commodity Futures Trading Commission to investigate the Goldman Sachs Group Inc. computer trading program that, according to a federal prosecutor, the bank acknowledges can be used to manipulate markets.”
What is perhaps worth underlining is that this last post is a credible bunch of insiders, not the rebels-with-a-blog. If the Financial Services Club are calling BS to GS, likely other insiders are too.
And well they should, if Goldman Sachs had an insider track on all the trades into NYSE. If this proves true, we're looking at an event that will make Arthur Andersen look like a Kindergarten squabble.
February 13, 2009
Rumour: NSA offering 'billions' for Skype eavesdrop solution
A printable-quality rumour straight from El Reg:
News of a possible viable business model for P2P VoIP network Skype emerged today, at the Counter Terror Expo in London. An industry source disclosed that America's supersecret National Security Agency (NSA) is offering "billions" to any firm which can offer reliable eavesdropping on Skype IM and voice traffic.The spybiz exec, who preferred to remain anonymous, confirmed that Skype continues to be a major problem for government listening agencies, spooks and police. This was already thought to be the case, following requests from German authorities for special intercept/bugging powers to help them deal with Skype-loving malefactors. Britain's GCHQ has also stated that it has severe problems intercepting VoIP and internet communication in general.
Skype in particular is a serious problem for spooks and cops. Being P2P, the network can't be accessed by the company providing it and the authorities can't gain access by that route. The company won't disclose details of its encryption, either, and isn't required to as it is Europe based. This lack of openness prompts many security pros to rubbish Skype on "security through obscurity" grounds: but nonetheless it remains a popular choice with those who think they might find themselves under surveillance. Rumour suggests that America's NSA may be able to break Skype encryption - assuming they have access to a given call or message - but nobody else.The NSA may be able to do that: but it seems that if so, this uses up too much of the agency's resources at present.
"They are saying to the industry, you get us into Skype and we will make you a very rich company," said the industry source, adding that the obscure encryption used by the P2Pware is believed to change frequently as part of software updates.
The spyware kingpin suggested that Skype is deliberately seeking to frustrate national listening agencies, which seems an odd thing to do - Skype has difficulties enough getting revenues out of its vast user base at any time, and a paid secure-voice system for subversives doesn't seem like a money-spinner
But corporate parent eBay, having had to write down $1.4bn already following its $2.6bn purchase of Skype back in the bubble-2.0 days of 2005, might see an opportunity here. A billion or two from the NSA for a backdoor into Skype might make the acquisition seem like a sensible idea.
Maybe it was just bad timing ... or maybe eBay hasn't got the smarts. I would dearly love to monetise that asset, and that's no secret (it will be on this blog somewhere). Either way, if eBay failed to integrate Skype, it's a solid sell signal on eBay. They are now just another cash cow. Milk on!
December 13, 2008
Ecuador's default: how to tame the angry Rafael Correa
(This article was co-written with Chris Cook; although the final presentation was done by me, so I have mangled his ideas somewhat!)

The basic story: Ecuador's government is pissed & angry with the debt issuances of previous governments: accusations of bribes, misconduct, EHMs, etc. And, they are broke, or broke enough to suggest default. And it was an election promise!
So why not default? Let's run the thought experiment.
Argentina did it, and survived, or at least that theory is popular in some circles. If this were to happen, what do future partners do, like Venezuala, or the emerging Banco del Sur? Kick the Ecuadorean's sorry tail all the way to Galapogas islands, join them in default, or think about how to adopt?
It needn't be that way. The fundamental problem is that the debt has migrated from an honest contract to a dishonest circle of mutually supporting pieces. This structure no longer helps any of the participants. So here's a plan to help any bankrupt country to move to the future:
- Default on the lot?
- adopt a Peer to Peer system of issuance and trading, as found in this recent FT award, and as epitomised by zopa.com,
- move the banking sector across to a service provision model, based on p2p credit
- structure issuances as debt/equity sharing (consider LLPs). This means that bond holders are no longer simply holders of debt, they are partners and investors,
- back the instruments with guarantees provided by mutual societies; being a member automatically gives you not only the guarantee but the incentive to look after the downstream risks,
- then, in the bankrupcy of all the debt, replace all the old broken instruments with new equity/debt sharing instruments.
OK, so maybe we skip point 1 because we want to retain some friends. There are some pretty bad punishments that the financial world can levy you with. But think of the rest.
This is a good future model for banks. p2p investment has higher margins, and the banks do not have to risk their own capital to play. Indeed that's where they want to be, c.f., securitization, and we could argue they are already there.
But, where they are now, the risks are not properly spread to those who care for the instruments, so, say hello to financial crisis.
We just have to go the next step by engaging the players end-to-end. The real essence is to move the financial issuance of debt across to a flexible creation of debt/equity balanced contracts between issuers and investors. The details are for later.
(It goes without stressing, in this new financial structure, we would need the ability for smaller issuers to create flexible contracts together.)
November 25, 2008
Who would judge a contest for voting machines?
In a previous entry I suggested creating an AES-style competition for automated voting systems. The idea is to throw the design open to the world's expertise on complex systems, including universities, foundations and corporates, and manage the process in an open fashion to bring out the best result.
Several people said "Who would judge a contest for voting machines?" I thought at first blush that this wasn't an issue, but others do. Why is that? I wonder if the AES experience surfaced more good stuff than superficially apparent?
If you look at the AES competition, NIST/NSA decided who would be the winner. James points out in comments that the NSA is indeed competent to do this, but we also know that they are biased by their mission. So why did we trust them to judge honestly?
In this case, what happened is that NIST decided to start off with an open round which attracted around 30 contributions, and then whittled that down to 5 in a second round. Those 5 then went forward and battled it out under increased scrutiny. Then, on the basis of the open scrutiny, and some other not-so-open scrutiny, the NSA chose Rijndael to be the future AES standard.
Let's hypothesize that the NSA team had a solid incentive to choose the worst algorithm, and were minded to do that. What stopped them doing it?
Several things. Firstly, there were two rounds, and all the weaker algorithms were cleaned out in the first round. All of the five algorithms in the second round were more or less "good enough," so the NSA didn't have any easy material to work with. Secondly, they were up against the open scrutiny of the community. So any tricky choice was likely to cause muttering, which could spread mistrust in the future, and standards are susceptible to mistrust. Thirdly, by running a first round, and fairly whittling the algorithms done on quality, and then leading into the second round, NIST created an expectation. Positively, this encouraged everyone to get involved, including those who would normally dismiss the experiment as just another government fraud, waiting to reveal itself. At a more aggressive extreme, it created a precedent, and this exposed the competition to legal attack later on.
These mechanisms worked hand in hand. Probably, either alone was not sufficient to push the NSA into our camp, but together they locked down the choices. Once that was done, the NSA saw its natural incentives to cheat neutered by future costs and open scrutiny. As it no longer could justify the risk of cheating, its best strategy was to do the best job, in return for reputation.
The mechanism design of the competition created the incentives for the judge to vote how we wanted -- for the best algorithm -- even if he didn't want to.
So, we can turn the original question around. Instead of asking who would judge such a competition, design a mechanism such that we don't care who would judge it. Make it like the AES competition, where even if they had wanted to, the NSA's best strategy was to choose the best. Set yourself a challenge: we get the right result even when it is our worst enemy.
November 14, 2008
A voting design competition?
I'm at LISA and just listened to this one:
The State of Electronic Voting, 2008
David Wagner, University of California, BerkeleyAs electronic voting has seen a surge in growth in the U.S. in recent years, controversy has swirled. Are these systems trustworthy? Can we rely upon them to count our votes? In this talk, I will discuss what is known and what isn't. I will survey some of the most important developments and analyses of voting systems, including the groundbreaking top-to-bottom review commissioned by California Secretary of State Debra Bowen last year. I will take stock of where we stand today, the outlook for the future, and the role that technologists can play in improving elections.
The one-line summary seems to be that voting machines are in a mess, and while there are brave efforts (California's review cited), there are no easy answers. It's a mess. This accords with my own prejudices: it looks like it should be a mess, by architectural requirements. My advice is to keep away, but today I didn't follow that advice, and have a suggestion!
One thing that is frequently suggested is that if the Internet community can build an Internet, surely we should be able to build a secure voting system. We can do big secure systems on the net, right? The counter example for this is IPSec or DNSSec or S/MIME: surely we should have been able to get a secure system into widespread use, but we seem to have failed at every turn here.
One reason why these things didn't work out is that the IETF committees who put them together got bogged down in details, as different stakeholders fought over different areas. The result is that familiar camel known as a secure but unusable architecture. Committees are at their best when they are retro-standardising an already successful design, such as SSL, because then they cannot dive into their own areas. They are forced to focus on the existing successful design.
Another suggestion is to use NIST or the NSA (same thing in this context) to design the system for us. But, this only works when we don't really care so much about the results. With encryption algorithms, for example, we the public get very suspicious about funny S-Boxes and the like, and skepticism dogged the famous DES algorithm as well as Skipjack and the cryptophones. For Hash designs, we are less fussed, because in application space much less much can go wrong if there is a secret way of futzing the hash.
Now, in the late 1990s, NIST took these issues seriously and took a novel path. They created a design competition to create a new encryption algorithm, asking anyone and everyone to propose. Any team around the world could submit an algorithm, and the final winner came from Belgium. As well, all the teams were encouraged to review the others' designs, and knock themselves out with criticisms. (By way of disclosure, Raif in my old Cryptix group created the Java framework for the AES proposals. It was that open that they took in help from crazy net hackers like ourselves.)
This worked! People mutter about AES as being a bit odd, but everyone admires the open design process, the use of the free and open scrutiny, and the way that the worldwide cryptography community rose to the challenge.
Why can't we do that with voting machines? All the elements seem to rhyme: stakeholders who will bog it down, conspiracy theories in abundance, desperate need of the people to see a secure outcome, and lots and lots of students and academics who love a big design challenge. NIST seems to be the ring-in to manage the process, and the result could be a standard design, which avoids the tricky issue of "mandating use".
Just a thought! I don't know whether this will work or not, but I can't see why not?
July 20, 2008
SEC bans illegal activity then permits it...
Whoops:
SEC Spares Market Makers From `Naked-Short' Sales BanJuly 18 (Bloomberg) -- The U.S. Securities and Exchange Commission exempted market makers in stocks from the emergency rule aimed at preventing manipulation in shares of Fannie Mae, Freddie Mac and 17 Wall Street firms.
The SEC granted relief for equity and option traders responsible for pairing off orders from a rule that seeks to bar the use of abusive tactics when betting on a drop in share prices. Exchange officials said limits on ``naked-short'' sales would inhibit the flow of transactions and raise costs for investors.
``The purpose of this accommodation is to permit market makers to facilitate customer orders in a fast-moving market,'' the SEC said in the amendment.
A reader writes: "that lasted what, 12 hours ?" I don't know, but it certainly clashes with the dramatic news of earlier in the week from the SEC, as the Economist reports:
Desperate to prevent more collapses, the main stockmarket regulator has slapped a ban for up to one month on “naked shorting” of the shares of 17 investment banks, and of Fannie Mae and Freddie Mac, the two mortgage giants. Some argue that such trades, in which investors sell shares they do not yet possess, make it easier to manipulate prices. The SEC has also reportedly issued over 50 subpoenas to banks and hedge funds as part of its investigation into possibly abusive trading of shares of Bear Stearns and Lehman Brothers.
Naked selling is technically illegal but unenforceable. The fact that it is illegal is a natural extension of contract laws: you can't sell something you haven't got; the reason it is technically easy is that the markets work on delayed settlement. That is, all orders to sell are technically short sales, as all sales are agreed before you turn up with the shares,. Hence, all orders are based on trust, and if your broker trusts you then you can do it, and do it for as long as your broker trusts you.
"Short selling" as manipulation, as opposed to all selling, works like this: imagine I'm a trusted big player. I get together with a bunch of mates, and agree, next Wednesday, we'll drive the market in Microsoft down. We conspire to each put in a random order for selling large lumps of shares in the morning, followed by lots of buy orders in the afternoon. As long as we buy in the afternoon what we sold in the morning, we're fine.
On the morning of the nefarious deed, buyers at the top price are absorbed, then the next lower price, then the next ... and so the price trickles lower. Because we are big, our combined sell orders send signals through the market to say "sell, sell, sell" and others follow suit. Then, at the pre-arranged time, we start buying. By now however the price has moved down. So we sold at a high price and bought back at a lower price. We buy until we've collected the same number we sold in the morning, and hence our end-of-day settlement is zero. Profit is ours, crack open the gin!
This trick works because (a) we are big enough to buy/sell large lumps of shares, and (b) settlement is delayed as long as we can convince the brokers, so (c) we don't actually need the shares, just the broker's trust. Generally on a good day, no more than 1% of a company's shares move, so we need something of that size. I'd need to be very big to do that with the biggest fish, but obviously there are some sharks around:
The S&P500 companies with the biggest rises in short positions relative to their free floats in recent weeks include Sears, a retailer, and General Motors, a carmaker.
Those driven by morality and striven with angst will be quick to spot that (a) this is only available to *some* customers, (b) is therefore discriminatory, (c) that it is pure and simple manipulation, and (d) something must be done!
Noting that service of short-selling only works when the insiders let outsiders play that game, the simple-minded will propose that banning the insiders from letting it happen will do the trick nicely. But, this is easier said than done: selling without shares is how the system works, at its core, so letting the insiders do it is essential. From there, it is no distance at all to see that insiders providing short sales as a service to clients is ... not controllable, because fundamentally all activities are provided to a client some time, some way. Any rule will be bypassed *and* it will be bypassed for those clients who can pay more. In the end, any rule probably makes the situation worse than better, because it embeds the discrimination in favour of the big sharks, in contrast to ones regulatory aim of slapping them down.
Rules making things worse could well be the stable situation in the USA, and possibly other countries. The root of the problem with the USA is historical: Congress makes the laws, and made most of the foundational laws for stock trading in the aftermath of the crash of 1929. Then, during the Great Depression, Congress didn't have much of a clue as to why the panic happened, and indeed nobody else knew much of what was going on either, but they thought that the SEC should be created to make sure it didn't happen again.
Later on, many economists established their fame in studying the Great Depression (for example, Keynes and Friedman). However, whether any parliament in the world can absorb that wisdom remains questionable: Why should they? Lawmakers are generally lawyers,and are neither traders nor economists, so they rely on expert testimony. And, there is no shortage of experts to tell the select committees how to preserve the benefits of the markets for their people.
Which puts the lie to a claim I made repeatedly over the last week: haven't we figured out how to do safe and secure financial markets by now? Some of us have, but the problem with making laws relying on that wisdom is that the lawmakers have to sort out those who profit by it from those who know how to make it safe. That's practically impossible when the self-interested trader can outspend the economist or the financial cryptographer 1000 to 1.
And, exactly the same logic leads to the wide-spread observation that the regulators are eventually subverted to act on behalf of the largest and richest players:
The SEC’s moves deserve scrutiny. Investment banks must have a dizzying influence over the regulator to win special protection from short-selling, particularly as they act as prime brokers for almost all short-sellers...The SEC’s initiatives are asymmetric. It has not investigated whether bullish investors and executives talked bank share prices up in the good times. Application is also inconsistent. ... Like the Treasury and the Federal Reserve, the SEC is improvising in order to try to protect banks. But when the dust settles, the incoherence of taking a wild swing may become clear for all to see.
When the sheepdog is owned by the wolves, the shepherd will soon be out of business. Unlike the market for sheep, the shareholder cannot pick up his trusty rifle to equalise the odds. Instead, he is offered a bewildering array of new sheepdogs, each of which appear to surprise the wolves for a day or so with new fashionable colours, sizes and gaits. As long as the shareholder does not seek a seat at the table, does not assert primacy over the canines, and does not defend property rights over the rustlers from the next valley, he is no more than tomorrow's mutton, reared today.
June 06, 2008
BarCampBankLondon: alternative finance workshop
Thomas Barker sends this press release:
Innovators Gather in the City to Set Shape for Future of Finance
Contact: Thomas Barker
Email: tbarker(at)barcampbank[..]org
LONDON, UK, Monday June 2nd, 2008 - On Saturday July 5th, 2008, one of the most unusual conferences in the financial services industry, BarCampBankLondon (BCBL), will get underway at 9:30 AM near the heart of the City. BCB London follows the success of previous BarCampBanks in Paris, Seattle, San Francisco, New Hampshire and New York City. Ranging from interested students, to banking executives, to VCs, startup founders and internet technologists. BCBL is a forum where participants from diverse backgrounds can get together to discuss topics impacting the industry. It will attract thought leaders and innovators from as far away as America for an intense day of discussions on the future of financial services.
Event co-founder, Frederic Baud said "We wanted to get away from the typical event where a group of senior executives listen to PowerPoint slides and exchange business cards. This is really about getting together people who share a genuine interest in building the future." The event has no set speakers, agenda or sales pitches and getting in the door will only set you back £10. To ensure that the event is relevant to all those attending, the agenda will be discussed online (http://barcamp.org/BarCampBankLondon), then set by the participants on the morning of the event.
It might seem strange that an event like this has taken so long to reach London, a city often considered to be the global financial hub. Another organizer, Thomas Barker said "People might not immediately think of London as a tech cluster. But walking around the City, you can see hundred of software firms nestled in among the banks and lawyers. There's a lot happening here". So far, BCBL intends to discuss the topics of P2P lending, startup financing, mobile banking, personal finance management and micro-finance amongst others.
To attend BCBL, register online at http://bcblondon.eventbrite.com/ .
Sun Microsystems are generously hosting BCBL in their City offices. The event, which is organized by volunteers, welcomes participation from anyone who would like to help with logistics or spreading the word. Interested parties can contact Thomas Barker at tbarker [at]barcampbank,org, or Antony Evans at Antony (At) thestartupexchange D0t com.
About BarCampBank:
The aim of BarCampBank is to foster innovation and the creation of new business models in the world of banking and finance. The next BarCampBank after London will be held in Charleston, USA. For more information, please contact George Pasley at gpasley att gmail d0T com . The following one will be held in Vancouver, Canada. For more information, please contact Tim McAlpine at tmcalpine (a) currencymarketing AT ca .# # #
If you'd like more information about his event, please contact Thomas Barker (contact information above) or Antony Evans (Antony _Att_ thestartupexchange . com)
February 15, 2008
What is Apple doing with the iPhone?
Bruce Schneier has a good article from the technical side of "lock-in" in this month's Crypto-gram. If you wish to understand the forces on technology suppliers like Apple, it is a good read. It finishes with:
As for Apple and the iPhone, I don't know what they're going to do. On the one hand, there's this analyst report that claims there are over a million unlocked iPhones, costing Apple between $300 million and $400 million in revenue. On the other hand, Apple is planning to release a software development kit this month, reversing its earlier restriction and allowing third-party vendors to write iPhone applications. Apple will attempt to keep control through a secret application key that will be required by all "official" third-party applications, but of course it's already been leaked.And the security arms race goes on...
What Apple are doing is neither full lock-in nor full open. That's the confusion. Why?
The answer is from marketing, and more specifically, the product life cycle or product roll-out economics. Let's assume that there is no competition for the iPhone (as this makes it easier to model).
In a rollout of a new innovation, there is a huge problem with market understanding. The product can't sell because nobody understands what it is about. So the need is critical for what is called "early adopters" which are the relatively clever, relatively rich people who buy any toy for the fun of it, and for the "first on the block" effect. These are around 1-3% of the market, depending.
Then, these early adopters will, if the product is any good, sell it to the rest of the people around them. Your sales force is your early adopters. So this means it is critical to please the early adopters, because without them, the product won't sell.
Who are the early adopters for any new and expensive phone? Phone hackers is one good answer. (Business geeks is another.) People who hack phones won't achieve too much but they tend to be quite influential as their sex-appeal is high to the media and their knowledge is wisdom to the public. Their enthusiasm sells phones.
The challenge for Apple is revealed. They have to attract the hackers, but not so much as to lose control. The mass market wants lock-in because they want a simple solid product with few choices. The early adopters want open, the reverse. Apple therefore walks the line between the two.
So far successfully. Of course, this whole model gets much more complicated when there are competitors, which is why watching the google phone and the gnu designs are interesting ... there you will see the Apple model being challenged.
But for now, it is fairly clear that this is the strategy that Apple is following. And, in the future, Apple will simply wind the lock up a bit. Not fast, just fast enough to keep the mass market locked in, and the early adopter enthusiasm keen.
It's good stuff, my hat off to Apple, this is what strategic marketing is all about. The only thing better than watching a great strategy unroll is creating one :)
October 30, 2007
Zopa and Listed Loans
Zopa has a new service that looks like you can post your ideal loan and get people to contribute. I'm not sure how this makes it different to its previous offerings (which would be probably obvious if I followed the site more closely) but it is curious to look at.
Apparently, being an Elvis fan is a key advantage in getting loans. One muses that social anthropologists are going to have fun comparing the public's preferences to those of banks.
From an FC perspective, we can see the same thing as over at other leading edge offers of payment systems and applications such as Second Life. By aggregating enough of the FC space within the offering, the cohesive application emerges, but the limits to scaleability are clear. OTOH, the emergence of strong pure-play FC players pretty much failed due to the various barriers, so it may be that this is the way forward.
Today's pop quiz: knowing what we know today, would we start again with a pure-play FC provider or a totally aggregated and simplified top-to-bottom application? A simplified way of looking at this question is whether we would go for a pure payments system, say for games, or rather build a game with integrated accounts?
Back to Zopa's market. Another issue (and many such remote microfinance concepts) is that although it can benefit from the Internet's disintermediation of banks, it can't necessarily compete against the banks' superior knowledge of the borrower. This was a core advantage of Grameen's _5 local women_ approach, something also seen in the social insurance industry (getting health insurance for a group is much easier than for an individual). Even though the risk is shared across the lenders, in theory at least, the borrower knowledge is an advantage that the banker maintains.
February 25, 2007
The alternative to FC is unprintable - Ahmadinejad and capital markets
Sometimes someone writes a sweeping article that just happens to include why Financial Cryptography is so important, and also so misunderstood. Here's an article by Reuven Brenner (posted by RAH):
What happens when societies either do not have or destroy their financial markets? Even today very few societies have developed the institutions that can enable the development of deep financial markets - a solid legal infrastructure and free media among them. In this scenario, most people wanting access to capital have no other option but to turn to government, which will raise the money - either through taxes or borrowing - and then distribute it.
FC at its core is about all forms value. That means markets, and the forms of markets that FC just happen to excel in are capital markets.
The alternative to access to capital (in other words, FC) is unprintable, at least on this forum, as we are sensitive to the reader's desires for a cosy Sunday and our own desire to believe we are doing the right thing.
Frederich Hayek called it the Fatal Conceit, and Muhammad Yunus showed how it caused poverty. Maggie Thatcher didn't hand it over to Brussels, and more recently, Hernando de Soto said that the Mystery of Capitalism was why they don't have it and we do.
Wherever you stand on mad mullahs, the rise of totalitarianism, wars over trade or gun-ship diplomacy, we would all be well served by liquid markets for capital in emerging markets. This seems to trump everything, or have I missed something?
The National Review
December 19, 2006, 8:42 a.m.
The Economics of the Rise of Ahmadinejad
Capital markets (or their absence) are central to the emergence of evil and the one-party state.
By Reuven Brenner
When Iranian President Mahmoud Ahmadinejad visited the U.S. recently, he didn’t say explicitly that the Holocaust was a myth. Instead he asked why so much emphasis is put on the 6 million Jews who died during WWII rather than the 60 million people who perished during the conflict. Then, at a Tehran conference where Holocaust deniers congregated with Orthodox rabbis who apparently believe the state of Israel should not exist, Ahmadinejad offered a message satisfying each camp. He told the delegates that the Holocaust should be questioned and that Israel’s days are numbered.
One wonders, with the terrible lessons of 20th century totalitarianism still so ripe, how history could repeat itself so blatantly and so soon. I hold that the answer lies in just how one-party states such as modern Iran emerge, and of what happens when the access to capital is limited within societies.
Of course, the systematic extermination of the Jews started in the early 1930s. By then, Germany had rebuilt itself from the ruins of WWI and the devastating hyperinflation of the 1920s into a powerful, educated, industrialized nation, where science and technology thrived. True, all this occurred within a one-party state. Yet, if such apparent prosperity can lead to murderous instincts not being suppressed, where is the advantage of Western Civilization, which is built on the concept of prosperity? In a recent op-ed in the Wall Street Journal, Mark Bowen asked, Why is the Holocaust haunting the collective memory of the West? Bowen concluded, “what the Holocaust demonstrates is the danger of a one-party state.”
This conclusion is partially correct, but it begs the question: How did Germany get from the Weimar Republic, a democracy, to the one-party state? And why did the Germans tolerate such a state and accept its murderous ideology? Whether the Germans agreed deep down with Hitler & Co. is irrelevant. Actions — or, in this case, the lack of actions — matter.
During the 1920s, Germany, Austria, Hungary, Poland, and Russia each printed money with abandon. This brought about hyperinflation, which weakened or destroyed the capital markets in these countries. Banks failed, markets crashed, unemployment rose, and the middle classes lost their lifetime savings.
People want to live first and philosophize a bit later. With their savings gone, these Europeans turned to two other ways of accessing capital: government and crime. Predictably, each of these countries moved toward centralization — that is, government become the main financial intermediary.
When the citizens of these countries looked abroad, there was little to admire. England and the U.S. were each suffering through depressions (in the U.S., due to mistaken fiscal and monetary policies). These governments too moved toward centralization, though to a much different degree. Up sprung the jargon of “public works” and, eventually, the Keynesian term “aggregate demand.” Here the governments also would become intermediaries, charged with raising and then allocating capital. Importantly, however, this was done without England or the U.S. ever becoming one-party states.
Power is dispersed within democracies, and democracies are always weakened when more money flows through government hands. This is true even when the facade of democracy persists. When more capital sifts through the government, more groups depend on government handouts and have less access to sources of capital that are independent from the ruling political parties. But the U.K. and the U.S. retained many more independent sources of capital than did Germany, Austria, Hungary, or Russia during the 1930s.
The dangers come when a country either does not develop its capital markets or destroys them on purpose or inadvertently. When this is the case, the chances of one party taking power and imposing its ideology increase.
Conversely, when capital markets are opened, the risk that one-party states will emerge diminishes. As independent sources of capital surface, political power is dispersed and lasting prosperity follows. Thus, it is a mistake to promote democracy without first establishing the ground for letting people have access to capital and collateral — or at least coordinating such access with political change. After all, prosperity is the result of matching people with capital, while holding both sides accountable.
What happens when societies either do not have or destroy their financial markets? Even today very few societies have developed the institutions that can enable the development of deep financial markets — a solid legal infrastructure and free media among them. In this scenario, most people wanting access to capital have no other option but to turn to government, which will raise the money — either through taxes or borrowing — and then distribute it.
That’s how one-party states such as Ahmadinejad’s Iran emerge: People bet on crazy ideologies when their customary ways of living suddenly crumble and capital markets close. Capital markets are the unique feature of the West, and their democratization is the key to the civilizing process and the best insurance against the emergence of one-party states. Indeed, that’s what the U.S. should have been “exporting” all along in the Middle East, coordinating the promotion of capital markets with the necessary political changes in Iraq.
— Reuven Brenner holds the Repap chair at Desautels’ Faculty of Management, and is partner in Match Strategic Partners. The article draws on his books Force of Finance (2002) and History: The Human Gamble (1983).
October 19, 2006
The Big Shift in Voice -- the deadly embrace of handset manufacturers and telcos
In the sometimes related world of mobile telephony, Dave challenged an off-the-cuff prediction:
"The reason for this is that there are enough rebel handset manufacturers out there now"I'm curious about this Ian, could you expand a little? Because of the way the market works, the handset manufacturers sort of have to work with the operators who subsidise their handsets. Won't this serve to limit what "rebel" handset manufacturers can do?
Posted by: Dave Birch at September 20, 2006 04:36 PM
In today's Lynngram, finally, an answer worth posting in this article, VoIP revolution leaves US behind:
Nokia's decision to include a SIP stack in its E-series Symbian phones has created a small explosion of start-up service providers. Kinks abound - and the number of devices available on the market is still limited - but the benefits are tangible. As I noted yesterday, since trialling VoIP on Symbian a month ago I haven't used any cellular minutes at home - except by accident.
Forget the US part of the article, look at what Nokia is doing (this rumour has been around for some time). Basically they are shifting themselves to a supplier of handsets to the people ... and making the telcos realise their optional position in the new world order.
The other rumour I heard was that it is now possible to buy in reasonable numbers (like a thousand) handsets for $20 unit cost from Asia. That is, if you have a need for a particular phone, you can get it custom made for reasonable costs. Want Skype? $20. Want SIP? Same thing ... Want WebFunds? Where's your code... (now think hard about what the article says about Symbian!)
Put it all together: Internet, VoIP, Skype and maybe even SIP, are starting to bite. The old dual cartel of handset manufacturers and telcos starts to look like a deadly embrace, one which Nokia at least is trying to exit before the end result.
October 03, 2006
The Last Link of Security
Vlad Miller writes from Russia (translated by Daniel Nagy):
We can invent any algorithm, develop any protocol, build any system, but, no matter how secure and reliable they are, it is the human taking the final decision that remains the last link of security. And, taking into account the pecularities of human nature, the least reliable link, at that, limiting the security of the entire system. All of this has long been an axiom, but I would like to share a curious case, which serves as yet another confirmation of this fact.
We all visit banks. Banks, in addition to being financial organizations attracting and investing their clients' funds, are complex systems of informational, physical and economic defenses for the deposited cash and account money. Economic defenses are based on procedures of confirming and controlling transactions, informational defenses -- on measures and procedures guarding the information about transactions, personal, financial and other data, while physical defenses comprise the building and maintenance of a secure physical perimeter around the guarded objects: buildings, rooms and valuable items.
Yet, regardless of the well-coordinated nature of the whole process, final decisions are always taken by humans: the guard decides whether or not to let the employee that forgot his ID through the checkpoint; the teller decides whether a person is indeed the owner of the passport and the account he claims to own; the cashier decides whether or not there is anything suspicious in the presented order. A failure can occur at any point, and not only as a consequence of fraudulent activities, but also due to carelessness or lack of attention on the part of the bank's employee, a link of the security system.
Not too long ago, I was in my bank to deposit some cash on my account. The teller checked my passport, compared my looks to the photo within, took my book and signed a deposit order for the given amount. The same data were duplicated in the bank's information system and the order with my book were passed on to the cashier. Meanwhile, I was given a token with the transaction number, which I should have presented to the cashier so that she could process the corresponding order. Everybody is familiar with this procedure; it may differ a bit from bank to bank, but the general principles are the same.
Walking over to the cashier, I have executed my part of the protocol by handing over the token to the cahsier (but I did not put the cash into the drawer before having been asked to do so). She looked at my order, affixed her signature to it and to my book and ... took a few decks of banknotes out of the safe and started feeding them to the counting machine. I got curious how long it would take for the young lady to realize the error in her actions, and did not interrupt her noble thrust. And only when she turned around to put the cash into the drawer did I delicately remark that I did not expect such a present for March 8 and that I came to deposit some cash, not to withdraw. For a few seconds, the yound lady gave me a confused look, then, after looking at the order and crossing herself, thanked me for saving her from being fired.
The banking system relies a great deal on governmental mechanisms of prevention, control and reaction. Had I not, in computer-speak, interrupted the execution of the miscarried protocol, but instead left the bank with the doubled amount of money, it would not have lead to anything except for the confiscation of the amount of my "unfounded enrichment". The last link of security is unreliable: it fails at random and is strongly vulnerable to various interferences and influences. This is why control and reaction are no less important than prevention of attacks and failures.
August 30, 2006
Universal Music throws in the towel, price of music drops to $0.00
Universal Music has announced it is moving its catalogue to a "free with adverts" model:
Backed by Universal, Spiralfrog will become one of the first sites to offer free music legally. Fans will be able to download songs by the record company's roster of artists, including U2, Gwen Stefani and The Roots.The service - which will be supported by advertising, unlike other legal download sites that charge for music - will launch in the US and Canada from December. It will become available in Europe in early 2007.
If the business succeeds, that will be the new standard price. If it fails, then it will take another year or two, I would predict, before the price goes back down to $0 (in delicious irony, the above article is now only available for a pound!).
There are a few reasons to believe that the business may not succeed -- massive lobbying by the others, duff selection, lousy adverts and plenty of time before now and then -- so this is a non-trivial question. Here's another reason:
Josh Lawler, a US-based music industry legal specialist, said news of the new service was "inevitable". He said questions over how artists would be paid may make some reluctant to agree to the free service. "SpiralFrog will have to find a way to pay artists from the advertising dollars they are generating," he added. "But they're not necessarily going to know how many advertising dollars there are and so some artists are going to be hesitant about it."
Here's my favourite quote, from a HMV rep who otherwise was quite positive (pay a pound for thereference) :
"What is a little concerning is that for a long time now, the trade body, BPI, has been anxious to put across an anti-illegal or piracy message, which suggests that music is of intrinsic value and people should be prepared to pay for it, so this may give a conflicting, mixed signal."
There's nothing "conflicting, mixed" about free. To see why this was inevitable:
"A report published last month by the International Federation of Phonographic Industries (IFPI) claimed 40 illegal downloads were made for every legal one in the US. The ratio, believed to be much the same in the UK,"
Now, I don't believe those numbers, necessarily, as I doubt the IFPI even bothered to pretend they weren't exaggerating. But even if in the ballpark, the amount of sharing dominates any other use, including practically everything else that isn't to do with music. If you believe the ISP grumbles, that is.
Time for a new model - the physics is the reality, the economics is the deal, and the legal stuff just has to keep up. BigMac suggests Pandora's Music Genome Project.
Another great quote:
"The US radio industry generates $20 billion a year in revenue and they give the product away for free," he said. "Record labels generate $12 billion a year and they sell their product."
Here's some clues on the new model:
Users can download an unlimited number of songs or music videos if they register at the site and watch online advertisements.The tracks cannot be burned to a CD, but users will be able to transfer music to portable media players equipped with Microsoft Windows digital rights management software, Ford said. However, the service will not work with Apple Computer's computers or its iPod music players.
Funny source for the nitty gritty!
Oh, I forgot to mention -- what's the nexus with FC? That's easy -- all those payment systems that were banking on micropayments from music downloads can close up shop. They should have studied more economics and less marketing.
2nd addition, to stress the move to $0 content:
Sony to buy Sausalito's GrouperSony Pictures is expected to announce today that it has acquired Sausalito Internet video-sharing company Grouper for $65 million.
Teaming up with Sony further highlights the role amateur videos -- and the companies that host them -- are having in changing the Hollywood landscape.
Traditional entertainment companies are working with Silicon Valley start-ups to navigate a new, on-demand entertainment world. Tuesday, the popular video-sharing site YouTube announced a new video advertising platform, and its first client is Warner Bros., which is promoting Paris Hilton's debut album.
Grouper's technology allows a user to easily take a video from its site and post it on third-party sites such as a MySpace or Blogger page. Its videos can also be watched on devices other than your personal computer, such as a video iPod.
For more naysaying, see BigPicture as suggested by Frank in comments below.
July 23, 2006
Case Study: Thunderbird's brittle security as proof of Iang's 3rd Hypothesis in secure design: there is only one mode, and it's secure.
In talking with Hagai, it was suggested that I try using the TLS/IMAP capabilities of Thunderbird, which I turned on (it's been a year or two since the last time I tried it). Unfortunately, nothing happened. Nothing positive, nothing negative. Cue in here a long debate about whether it was working or not, and how there should be a status display, at least, and various other remedies, at most.
A week later, the cleaning lady came in and cleaned up my desk. This process, for her, also involves unpowering the machine. Darn, normally I leave it on for ever, like a couple of months or so.
On restarting everything, Thunderbird could not connect to the mail servers. Our earlier mystery is thus resolved - the settings don't take effect until restart. Doh!
So, how then did Thunderbird handle? Not so well, but it may have got there in the end. This gives me a change to do a sort of case study in 1990s design weaknesses, a critique in (un)usability, leading to design principles updated for this decade.
To predict the punch line, the big result is that there should only be one mode, and it should be secure. To get there more slowly, here's what I observed:
Firstly, Thunderbird grumbled about the certificate being in the wrong name. I got my negative signal, and I knew that there was something working! Hooray!
But, then it turned out that Thunderbird still could not connect, because "You have chosen secure authentication, but this server does not offer it. Therefore you cannot log in..." Or somesuch. Then I had to go find that option and turn it off. This had to be done for all mail accounts, one by one.
Then it worked. Well, I *guess* it did... because funnily enough it already had the mail, and again had not evidenced any difference.
Let's break this up into point form. Further, let's also assume that all competing products to be as bad or worse. I actually *choose* Thunderbird as my preferred email client, over say Kmail. So it's not as bad as it sounds; I'm not "abandoning Thunderbird", I'm just not getting much security benefit from it, and I'm not recommending it to others for security purposes.
- No caching of certs. There is no ability to say "Yes, use that cert for ever, I do know that the ISP is not the same name as my domain name, dammit!!!!" This is an old debate; in the PKI world, they do not subscribe to the theory that the user knows more than any CA about her ISP. One demerit for flat earth fantasies.
- No display anywhere that tells me what the status of the security is. One demerit. (Keep in mind that this will only be useful for us "qualified cryptoplumbers" who know what the display means.)
- I can choose "secure authentication" and I can choose "secure connection." As a dumb user, I have no idea what that means, either of them. One demerit.
- If I choose one of those ON, and it is not available, it works. Until it doesn't -- it won't connect at some later time and it tells me to turn it off. So as a user I have a confusing choice of several options, but ramifications that do not become clear until later.
Another demerit: multiple options with no clear relationship, but unfortunate consequences.
- Once it goes wrong, I have to navigate from a popup telling me something strange, across to a a series of boxes in some other strange area, and turn off the exact setting that I was told to, if I can remember what was on the popup. Another demerit.
- All this took about 5 minutes. It took longer to do the setting up of some security options than it takes to download, install, and initiate an encrypted VoIP call over Skype with someone who has *never used Skype before*. I know that because the previous night I had two newbies going with Skype in 3 minutes each, just by talking them through it via some other chat program.
- Normal users will probably turn it all off, as they won't understand what's really happening, and "I need my mail, darnit!"
(So, we now start to see what "need" means when used by users... it means "I need my email and I'll switch the darned security rubbish off and/or move to another system / supplier / etc.)
- This system is *only useable by computer experts.* The only reason I was able to "quickly" sort this out was because I knew (as an experienced cryptoplumber) exactly what it was trying to do. I know that TLS requires a cert over the other end, *and* there is a potential client-side cert. But without that knowledge, a user would be lost. TLS security as delivered here is a system is not really up to use by ordinary people - hence "brittle."
We can conclude that this is a nightmare in terms of:
- usability.
- implementation.
- design.
- standards.
Let's put this in context: when this system was designed, we didn't have the knowledge we have now. Thunderbird's security concept is at least 3 years old, probably 8-10 years old. Since those years have passed, we've got phishing, usability studies, opportunistic crypto, successful user-level cryptoapps (two, now), and a large body of research that tells us how to do it properly.
We know way more than we did 3 years ago - which was when I started on phishing. (FTR, I suggested visit counts! How hokey!)
Having got the apologies off our chest, let's get to the serious slamming: If you look at any minor mods to the Thunderbird TLS-based security, like an extra popup, or extra info or displays, you still end up with a mess. E.g., Hagai suggested that there should be an icon to display what is going on - but that only helps *me* being an experience user who knows exactly what it is trying to tell me. I know what is meant by 'secure authentication' but if you ask grandma, she'll offer you some carrot cake and say "yes, dear. now have some of this, I grew the carrots myself!"
(And, in so doing, she'll prove herself wiser than any of us. And she grows carrots!)
Pigs cannot be improved by putting them in dresses - this security system is a pig and won't be improved by frills.
The *design* is completely backwards, and all it serves to do is frustrate the use of the system. The PKI view is that the architecture is in place for good reasons, and therefore the user should be instructed and led along that system path. Hence,
"We need to educate the users better."
That is a truly utterly disastrous recommendation. No! Firstly, the system is wrong, for reasons that we can skip today. Secondly, the technical choices being offered to the users are beyond their capabilities. This can never be "educated." Thirdly, it's a totally inefficient use of the user's time. Fourthly, the end effect is that most users will not ever get the benefit.
(That would be a mighty fine survey -- how many users get the benefit of TLS security in Thunderbird? If it is less than 10%, that's a failure.)
The system should be reversed in logic. It should automatically achieve what it can achieve and then simply display somewhere how far it got:
- Try for the best, which might be secure auth, and then click into that. Display "Secure Auth" if it got that far.
- If that fails, then, fallback to second best: try the "Secure Conn" mode, and display that on success.
- Or finally, fall back to password mode, and display "Password only. Sorry."
The buttons to turn these modes on are totally unneccessary. We have computers to figure that sort of nonsense out.
Even the above is not the best way. Fallback modes are difficult to get right. They are very expensive, brittle even. (But, they are better - far far far cheaper - than asking the user to make those choices.) There is still one way to improve on this!
Hence, after 5 demerits and a handful of higher-level critiques, we get to the punchline:
To improve, there should only be one mode. And that mode is secure. There should be only one mode, because that means you can eliminate the fallback code. Code that falls back is probably twice as large as code that does not fallback. Twice as brittle, four times as many customer complaints. I speak from experience...
The principle, which I call my 3rd Hypothesis in Secure Protocol Design, reads like this:
There is only one mode, and it is secure.
If you compare and contrast that principle with all the above, you'll find that all the above bugs magically disappear. In fact, a whole lot of your life suddenly becomes much better.
Now, again, let's drag in some wider context. It is interesting that email can never ever get away from the fact that it will always have this sucky insecure mode. Several of them, indeed. So we may never get away from fallbacks, for email at least.
That unfortunate legacy should be considered as the reality that clashes with the Hypothesis. It is email that breaches the Hypothesis, and it and all of us suffer for it.
There is no use bemoaning the historical disaster that is email. But: new designs can and will get it right. Skype has adopted this Hypothesis, and it took over - it owns VoIP space in part because it delivered security without the cost. SSH did exactly the same, before.
In time, other communication designs such as for IM/chat and emerging methods will adopt Hypothesis #3, and they will compete with Skype. Some of the mail systems (Start/TLS ?) have also adopted it, and where they do, they do very well, allegedly.
(Nobody can compete with SSH, because we only need one open source product there - the task is so well defined there isn't any room for innovation. Well, that's not exactly true - there are at least two innovations coming down the pipeline that I know of but they both embrace and extend. But that's topic drift.)
April 18, 2006
Voting and more from the Red Queen
Cubicle points to a great article that contrasts voting machines with gambling machines.
It's easier to rig an electronic voting machine than a Las Vegas slot machine, says University of Pennsylvania visiting professor Steve Freeman. That's because Vegas slots are better monitored and regulated than America's voting machines.
Of course the gambling machines come out on top - they are more carefully governed because the nature of the money is very very clear. With a voting machine, you the punter has no clear picture of how it is being used to reach into your pocket, and your natural skepticism is swept aside by airy fairy claims of democracy and honesty of our public process blah blah.
In contrast to that rosy view of gambling governance, Risks points out that:
Casino can reprogram slot machines in seconds <"Peter G. Neumann"> Wed, 12 Apr 2006 11:10:27 PDTAs an enormous operational improvement, the 1,790 slot machines in Las Vegas's Treasure Island Casino can now be reprogrammed in about 20 seconds from the back-office computer. Previously this was an expensive manual operation that required replacing the chip and the glass display in each machine. Now it is even possible to have different displays for different customers, e.g., changing between "older players and regulars" during the day and a different crowd at night ("younger tourists and people with bigger budgets". (Slot machines generate more than $7B revenue annually in Nevada.) Casinos are also experimenting with chips having digital tags that can be used to profile bettors, and wireless devices that would enable players to gamble while gamboling (e.g., in swimming pools!). [Source: Article by Matt Richtel, Prefer Oranges to Cherries? Done! *The New York Times*, 12 Apr 2006, C1,C4; PGN-ed]
Well, the WaPo story was nice while it lasted. More from Risks, there are reports that votes of lesser importance were interfered with. Going to the sources:
Washington voting hijacked by computer mischiefAn online poll asking Washingtonians to pick their favorite design for the state's quarter coin was suspended, after the balloting was hijacked by computer programs whose automated scripts pushed the tally past 1 million votes over the weekend. State officials overseeing the balloting originally decided not to limit the number of votes coming from individual computers so that family members sharing a single machine could each cast a vote, Gerth said. But that philosophy was being abandoned after the weekend's voting, which showed some computers casting repeated votes for a quarter design faster than humanly possible.
[Source: Associated Press item, seen in *The Seattle Times*, 12 Apr 2006; PGN-ed]
DoIT Information on ASM Election IssuesMore specifically, DoIT detected a disparity between the number of student votes cast and the number of votes confirmed in the online election database. In the Student Council portion of the election, 94 more ballots were cast than were posted; in the referenda portion, 436 more ballots were cast than posted. After further investigation today, DoIT determined that there were no additional discrepancies in the referenda
I wrote before on the monetary aspects of voting. The first story above is about money, but it hardly seems monetary. The second is more of a political issue - but such polls often lead to power and money.
The question then arises if in any voting system it is unreasonable to assume 'honest' behaviour, even if the poll is over issues of no direct importance? Is it therefore better to assume that in any voting system, some small group of users will manipulate if given the chance? Even if there is no benefit to them?
The system of voting I wrote about last week solved this problem -- in the face of prior efforts to increase unimportant ratings fraudulently -- by checking identity on handing out the tokens. That's pretty boring. But if we decide that the only solution to proper democracy is a strong identity society, there's an awful lot of waste there, not to mention risk of identity abuse.
April 09, 2006
Votes are coins stamped with the Red Queen's head
In FC we know voting as a sort of constrained monetary auction. Indeed, some wit said political elections are just an advance auction of stolen goods. The spirit of democracy is an inspiring thing, and it suggests to many that we should be able to solve all our problems democractically, no? Well, no. Least of all money, but this doesn't stop some from trying.
I was recently coralled into becoming a sort of elections officer in a vote on funding applications. There was some large bickies to allocate to a needy public, and the story is worth recording, so here goes.
Grantees were encouraged to present their proposals before the body politic. Each person in the community was given a quantity of peanuts. These weren't the rooty / fruity kind, but pieces of paper saying "In Peanuts we Trust!" My job, alongside half a dozen others, was to verify the identity of people by checking their government-issued Identity docs, record the vital statistics, and hand over 70 peanuts to each person.

Standards on identity were curious. It had to have a photo. So credit cards did not count, but Manfred's above was accepted. If someone had not registered, all officers had to vote by show of hands to let them in. If they had no Id, then they had to find a mutual friend to vouch for them; someone who we knew, that knew them.
Why so serious? Because in a recent vote, several groups had cheated to push the rankings of their projects up the ladder! Why did they do that? Because they could, because it was art, because it was free like beer. So this time, the less amused among the community were taking no chances, it seemed.
At 21 hours, the bell rang and the issue of peanuts was over. (Luckily, the beer and some mighty fine broccali soup was still flowing.) Some 30 or so project groups had a brief 30 minutes to collect votes from each other. This phase exhibited one major flaw in that there was no anonymity - project marketeers running around with envelopes were able to employ a gamut of social pressures to secure their peanuts, and smaller, less marketing-savvy projects suffered.
While this was going on, we back in the issuance room were madly collating and cross-checking to validate the total issued peanuts.
| Number of voters: | 169 |
| Total Peanuts: | 70 * 169 == 11830 |
| Cost to Issue: | (2 days * 1 for printing) + (3 hours * 6 for issuance) |
| Value of Peanut: | 4.22 |
In order to make the voting serious, groups were given a limit - each group had to exceed a low watermark and not exceed a high watermark. This was to stop large projects dominating and small projects diminishing, or something.
So when the scores were announced, the obvious thing happened - projects that were below the low watermark ran around and grouped up into larger projects. Or, they sold their peanuts for promises of funds to other projects. And projects over the high watermark did the same thing! Meanwhile, over at the bar, all night there had been a ready cash market for peanuts. The first trades were observed at 7, and finally settled at 2, which is indicative of quite good estimating by the market.
Which means that the peanuts were money, but shackled with the inefficiency an imposed spirit of democracy. Quite a common suffering these days, it seems. A more ideal distribution system is then to simply give all people the peanuts as money, and instead of encouraging some notion of voting, encourage as many transactions as possible. Perhaps the rule is that there are 3 rounds, all transactions are anonymous and nobody gets to see their total at any time? When it finally settles, the hope would be that the decisions have best reflected the voice of the market.
This mirrors recent results in the economics of privatisation. In disbursing the value of communist assets such as factories, mines, etc, those newly freed countries in Eastern Europe that moved fastest benefitted more quickly. The end results indicated that speed, efficiency, and certainty paid off, even at the expense of some hypothetical losses to those who "missed out."
The vote got the whole thing over with in one evening, and I find comfortable parallel with recent results in the economics of privatisation. In disbursing the value of communist assets such as factories, mines, etc, those newly freed countries in Eastern Europe that moved fastest benefitted most, and more quickly. The end results indicated that speed, efficiency, and certainty paid off, even at the expense of some hypothetical losses to those who "missed out."
From the pov of the grantor, then, it has to be judged a fast, efficient and certain success. Now everyone knows -- a valuable thing.
March 26, 2006
How does the dominatrix of the open source world encourage her clients to pay for their pain?
OpenBSD asks for more contributions coz it's running at a loss. Mozilla asks for help in giving away money coz it's washing in funds. What a funny world.
Humour aside it is worthwhile to analyse these differences. Mozilla delivers browsers and email clients to the great masses of Internet users. Yours and my mom might use Firefox. BSD is an obscure operating that gets used by people who know what it is for, and probably have more than a passing ability to read and hack the code. Hard-core geeks in other words.
Mozilla stresses community and tries to get along, CEO Mitchell talks about personal lessons from falling off the trapeze; in contrast Theo de Raadt has a reputation for not getting along and frequently stars in flame wars over some security issue or other.
What's the core difference here? It's in the mission. Mozilla's software is standing in front of the user, and offering her an experience. Indeed, they say that part of the mission is improving the experience, which of necessity means getting all close and cozy with the users - all of them. You cannot improve your users' experiences unless you get into their hearts, their souls, their minds.
OpenBSD's mission in contrast is security, which isn't close and cozy anywhere anytime. Quite the opposite - for OpenBSD, the user is as much a threat as a beneficiary. In the hard security world, everything and everyone is treated with suspicion until proven otherwise. And even then, we have our doubts...
Which means that on first, second and third blush the OpenBSD project is unfriendly. The nicest thing you could say about those guys is that they are uncompromising, whereas the Mozilla guys are quite compromising. So here's where it all comes together: to cut a deal with Yahoo or Google that is worth 8 figures in revenue (numbers not available but widely speculated) you do need to be compromising - very compromising. Yahoo and Google want serious compromises for their dosh.
OTOH, you can imagine what would happen if Google turned up with a suggestion of, say, putting their disk searching technology into OpenBSD. (For a fee, of course.) We want an uncompromising response to that, forsooth, the nastier the better. I feel quite comfortable when I hear of the latest security spat - because I know that an uncompromising attitude is essential to security.
I wouldn't go so far as to say you have to be downright nasty to be secure. But it is certainly very hard to be secure when you have a mission of embracing all. A nice trick to pull off, if you can do it, and please tell us about it.
Getting back to OpenBSD. Just how does an open source project that makes a mission of being, ahem, uncompromising, go about doing some deals to get some revenue? Just who in business wants to pay for pain? Tough one, that. Those who solicit the dominatrix's services aren't saying, either.
February 08, 2006
Brand matters (IE7, Skype, Vonage, Mozilla)
In branding news: IE7 is out in Beta 2 and I'm impatiently waiting for the first road tests. (Roight... as if I have a Microsoft platform around here...) Readers will recall that Microsoft took the first steps along the branded security path by putting the CA name up on the chrome. This places them in the lead in matters of risk.

Sadly, they also got a bit confused by the whole high-end super-certs furfie. IE7 only rewards the user with the CA brand if the site used these special high-priced certs.
Plonk! That kind of ruins it for security - the point of the branding is that the consumer wants to see the Bad Brand or Unknown Brand or the Missing Brand or the Bland Brand ... up there as well. Why? So as to close off the all-CAs-are-equal bug in secure browsing. (Preferably before the phishers start up on it, but just after the first sightings will do nicely, thanks, if you subscribe to post-GP theories.)
By choosing to promote a two-tiered risk statement, Microsoft then remains vulnerable to a takeover in security leadership. That's just life in the security world; leadersip is a bit of a lottery when you allow your security to become captive to marketing departments' zest for yet another loyalty program. Also, annoyingly, IE7 promises to mark any slightly non-formal certificated site (such as FC) as a Red Danger Danger site. Early indications are that this will result in an attack on brand that hasn't hitherto been seen, and has interesting strategic implications for you-know-who.

The CA branding idea is not new nor original. It was even (claimed to be) in the original Netscape design for secure browsing, as was the coloured security bar. Using brand is no more than an observation deriving from several centuries of banking history - a sector that knows more about risk matters than the Internet, if only because they lose money every time they get it wrong.
Consider some more in the flood of evidence that brand matters - over in VoIPland look at how things have changed:
In Europe, branded VoIP represented 51.2 percent of all VoIP calls in the last quarter of 2005, while Skype accounted for 45 percent of VoIP minutes. Vonage took less than one percent of the market while other third-party VoIP providers represented 3.5 percent of all VoIP traffic, the report said."Twelve months ago, Skype represented 90 percent of all VoIP minutes. Now people are buying branded services," Chris Colman, Sandvine's managing director for Europe, said Tuesday.
Whaaa.... 90% to 45% of the market in 12 months! No wonder Skype sold out!
The same trend was found in the North American market. The study found that U.S. branded VoIP represented 53 percent of VoIP minutes on broadband networks. Vonage, with a 21.7 percent share, and Skype, with 14.4 percent, were the leading third-party providers.
I'll bet Vonage are kicking themselves... Stop Press!
TECHNOLOGY ALERT from The Wall Street Journal. Feb. 8, 2006
Internet-phone company Vonage Holdings has filed to raise up to $250 million in an initial public offering. The company also named Mike Snyder, formerly president of security company ADT, as its new CEO. Founder Jeffrey Citron, who had served as CEO, remains chairman.
FOR MORE INFORMATION, see:
http://wsj.com/technology?mod=djemlart
I didn't know you could file an IPO in just minutes like that!
Meanwhile, one group that have traditionally resisted the risk nexus of brands ... just got hit over the head with their own brand! Mozilla earnt a spot in the 10 ten most influential brands last year. More influential that Sony! Heady praise indeed. Well done, guys. You have now been switched on to the miracle of brand, which means you have to defend it! Even as this was happening, Firefox lost market share in the US. Predicted of course, as IE7 rolls out, Microsoft users start to switch back. Nice. Competition works (in security too).
So, what's the nexus between brand and risk? Newbies to the brand game will blather on with statements like "we protect our brand by caring about the security of our users." Can you imagine a journo typing that up and keeping a straight face?
No, brand is a shorthand, a simple visual symbol that points to the entire underlying security model. Conventional bricks&mortar establishments use a combination of physical and legal methods (holograms and police) to protect that symbol, but what Trustbar has shown is that it is possible to use cryptography to protect and display the symbol with strength, and thus for users to rely on a simple visual icon to know where they are.
Hopefully, in a couple of years from now, we'll see more advanced, more thoughtful, more subtle comments like "the secured CA brand display forms an integral part of the security chain. Walking along this secured path - from customer to brand to CA to site - users can be assured that no false certs have tricked the browser."
February 01, 2006
Why passports will have RFIDs
The Register revealed the scandalous behaviour of the Dutch promiscuous passports. Quickest description is on EC:
The secret key is made up of the passport expiry date, birth date and the passport number stored in the passport's Machine Readable Zone. The Dutch passport numbering scheme proves to be sequential and has a relation with the passport expiry date. Further, the last digit of the number is a checksum introducing additional predictability. The selection of a new and unpredictable passport numbering scheme would considerably improve the security.
Oops. History does not reveal how it is that the Dutch - normally a country steeped in deep privacy and cryptography that they run things like WhatTheHack where it was first announced - managed to make such a blunder.
One quibble. Adam goes on to say "The radio has no function." I think that's a bit tough to sustain. The point of using RFIDs and so forth comes from long hard-won experience. The experience pans out roughly like this:
- smartcard people wanted to do money
- smartcards are too expensive for money
- only mass transits had the wherewithall to finance smartcards as money
- mass transits also have mass queues
- only very fast systems work in mass transits
- contactless smarts are the only ones that are fast
- smartcard money therefore had to be RFID.
- people thinking smartcards therefore think RFID
From there, the decision to add smart cards to passports means they more or less had to include RFIDs. All experience points in that direction, and experience is everything in the smart card world (mostly because there is so little of it).
So the question then reduces to ... how applicable is mass transit experience to the passport issue? This might be considered to be the LAX factor - the answer is "quite a lot" if you've ever been stuck in a queue at a major US airport carefully calculating the time to the gate close on your connection.
Which does nothing to answer the next question: does the LAX factor - the benefit of radio-enhanced fast entry - outweigh the downsides? That seems to be the experiment that the various passport offices are intending to run on their captive subjects, so we will know for sure in about 10 years.
December 20, 2005
eCash is prior art to Amazon one click?
In the retail world, Amazon's one-click patent is well known. What wasn't realised, it seems, is that DigiCash's eCash software shipped with the same functionality... Nick describes how Peter Calveley is looking to get the patent re-examined using docs from wayback machine.
Calveley is the first to point out, as far as I know, that the automated payment policy setting of ecash, combined with a single click to order an item (e.g. to download a file or to make a wager), is a very good prior art reference which anticipates the Amazon one-click patent (or at least makes it even more blindingly obvious than we software engineers already thought it was).
Nick is also callout for all old DigiCash buffs - can you help?
If you have personal information or know of further documentation about this feature, or any other product or design prior to 1997 that used one-click ordering, both myself and Peter Claveley are greatly interested in collecting this information.
Calveley is also collecting pledges to cover the fee - using PledgeBank which in itself is a newsworthy item. I should think anyone who's been terrorised by the patent would donate! I wonder what form of eCash he'll take?
December 13, 2005
GP2 - Growth and Fraud - Instructing Security at GP
In the previous discourse (Meet at the Grigg Point), we discussed how growth works, and said that GP was the tipping point at which the demo became a system. From this model, we can make a number of observations, chief of which is about Security to which we now turn.
One of the security practitioner's favourite avisos is to suggest that the security is done up front, completely, securely, with strong integration, not to mention obeisance. Imagine the fiercely wiggling finger at this point. Yet, this doctrine has proven to be a disaster and the net's security pundits are in the doldrums over it all. Let's examine some background before getting to how GP helps us with this conundrum.
Hark to the whispering ghosts of expired security projects. Of those that took heed of the doctrine, most failed, and we do mean most. Completely and utterly, and space does not permit a long list of them, but it is fair to say that one factor (if not the sole or prime factor) is that they spent too much on security and not enough on the biz.
Some systems succeeded though, and what of them? These divide into three:
- those that implemented the full model,
- those that implemented a patchwork or rough security system, and
- those that did nothing.
Of those few systems that heeded the wiggling finger and succeeded, we now have some substantial experience. Heavily designed and integrated systems that succeeded initially went on to expose themselves to ... rather traumatic security experiences. Why? In the worst cases, when the fraud started up (around GP) it simply went around the security model, but by that time the model was so cast in mental concrete that there was no flexibility to deal with it. One could argue that these models stopped other forms of fraud, but these arguments generally come from managers who don't admit the existence of the current fraud, so it's an argument designed to be an argument, not something that pushes us forwards.
Perversely, those systems that did nothing had an easier time of it than even those that implemented a patchwork, because they had nothing to battle.
fig 4. Investment directs the Revenue Curve
Why is this? I conjecture that at the beginning of a project the business model is not clear. That is, none of us really knows what to do, but darn it we're inspired! Living and dreaming in Wonderland as we are, this suggests that the business model migrates very quickly, which means that it isn't plausible to construct a security model that lasts longer than a month. Which means several interlinked things:
- until the business model is proven, there is little point in building a security model for security per se as an unproven model doesn't deserve to be protected,
- the more attention that is put into the security model, the more the security model kicks back and insists that the business model stop changing, dammit!,
- the more money that is put into the security model, the less money there is available for business activity, and
- the security system puts a cost on the whole system, slowing growth.
Now, anyone who's aware of compounding knows where to put the value: building the business, and security rarely if ever builds business, what it does is protect business that is already there. It's the issue of compounding we turn to now. Figure 4 depicts the cost of investment down below the horizontal axis, and the growth above. Investment isn't exponential, so it's not a straight line. Initially it grows well, but then hits limits to growth which doom it to sub-exponential growth, which is probably just as well as any investor I've met prefers less than exponential growth in contributions!
While not well depicted in that figure, consider that the pattern of investment fundamentally sets the growth model. The Orange line dictates the slope and placement of the Blue!
Now let's fiddle a bit in figure 5. Assume that investment is fixed. But we've decided to invest upfront in a big way in security, because that's what everyone said was the only way to sleep well at nights. Now the Orange Region of total investment over time is divided into two - above the thin line is what we invest in the business, and below the line is the security. The total is still the same, so security investment has squeezed us upfront.
fig 5. More Costs means Growth is Flatter and GP is Later
See what happens? Because resources were directed away from business, into security, the growth curve started later, and when the security model kicked in, the curve flattened up. That's because all security has a cost. If you're lucky, and your security team is hot (and I really do mean blistering here, see what I wrote about "most" above...) the kink won't be measurable.
Why is it so big? And why don't managers wade in there with mallet and axe and bash it back into forward growth before we can say hedonism is the lifeblood of capitalism? Oddly, the chances of a manager seeing it are pretty remote because seeing drivers to growth is a very hard art, most people just can't see things like that and assume that either today goes for ever, or tomorrow will solve everything. The end users often notice it, and respond in one of two ways: they scream and holler or they stop using the system. An example of the former is from the old SSL days when businesses screamed that it sucked up 5 times the CPU ... so they switched to hybrid SSL/raw sites. An example of the latter is available every time you click on a link and it asks you to register for your free or paid account to read an article or to respond to an article.
Students of security will be crying foul at this point because security does good. So they say. In fact what it does is less bad: until we draw in the fraud curve which security nicely attempts to alleviate the bad done by fraud, security is just a cost. And a deadweight one at that. Which brings us to our third observation: the upfront attention to security has pushed GP way over to the right, as it must do if you agree with the principle of GP.
So where is all this leading us? At this point we should understand that security is employed too early if employed at the beginning - the costs incur a dramatic shift of the curve of growth. Both to the right, and a flattening due to the additional drain. And we haven't even drawn in the other points above: restarts and kickback.
This logic says that we should delay security as long as we can, but this can't go on forever. The point where the security really kicks in and does less bad is when the bad kicks in: the fraud curve that slides up and explodes after GP. Then, the ideal point in which to kick security is after GP and before the fraudulent red line runs in ink onto the balance sheet.
Which leads us to question - finally, for some, no doubt - When is GP?. That is saved to another day :-)
December 11, 2005
GP1 - Growth and Fraud - Meet at the Grigg Point
Imagine if you will a successful FC system on the net. That means a system with value, practically, but for moment, keep close in your mind your favourite payments system. Success means solid growth, beyond some point of survival, into the area where growth is assured. It looks like this:
fig 1. Exponential Growth
That's an exponential curve, badly drawn by hand. It's exponential because that's what growth means; all growth and shrinkage is exponential. Let's draw that as a logarithmic curve, so we see a straight line:
fig 2. Growth Crosses the Value Tipping Point
I've observed in many businesses of monetary nature that there is a special tipping point. This is where the system transitions from being a working demo that is driven forwards by the keenness of its first 100 or so users, to being a system where the value in the system is inherent and cohesive. In and of itself, the value in the system is of such value that it changes the dynamics of the system.
That's why I labelled it the Self-Sustaining Value Growth Tipping Point, or GP for short. Before this point, the system will simply stop if we the founders or we the users stop pushing. After this point, there is a sustained machine that will keep rolling on, creating more and more activity. In short, it's unstoppable, at least as compared to beforehand.
The shortened term indicates who to blame when you reach that point, because there is something else that is going to happen here: fraud! When the system passes GP, and the value is now inherently stealable for its value, then someone will come along and try to steal it.
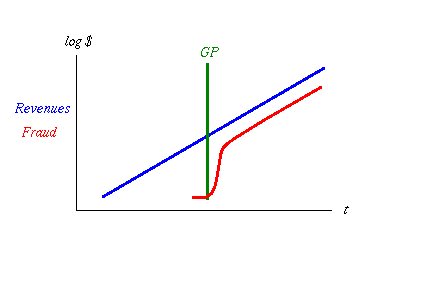
fig 3. Fraud Kicks Off then Levels Off
And that theft will probably work, if history is any judge. You'll get a rash of frauds breaking out, either insider or outsider fraud, and all will appear to be chaos. Actually, it's not chaos, it's just competition for different fraud models, and soon it will settle down to a set of best practices in fraud. At this point, when all the mistakes have been made and the surviving crooks know what they are about, fraud will rise rapidly, then asymptotically approach its long run standard level. Ask any credit card company.
Remember that the graph above has a logarithmic vertical axis, so vertical distances of small amounts mean big distances in absolute amounts. The long run gap between those lines - red to blue - is about two if the vertical was log 10. Assuming that, 102 gives us 100 which means fraud is 1% of total at any time. 1% is a good benchmark, a great number to use if you have no other number, even if the preceeding mathematics are rather ropey. Some systems deliver less, some deliver more, it all depends, but we're in the right area for a log chart.
Now that we have the model in place, what can we do with GP? Quite a lot, it seems, but that waits for the next exciting installment of Growth and the Big GP!
This is Part 1 of Growth and Fraud:
November 21, 2005
Frank Hecker goes to the Mountain - mapping the structure of the Certificate Authority
Frank takes aim at the woeful business known as certificate authorities in an attempt to chart out their structural elements and market opportunities.
Frank argues that CAs can be viewed as providers of one of encryption, DNS-fixes, site identity proofs, or as anti-fraud services. Depending on which you choose, this has grave ramifications for what follows next -- Frank's thesis implicitly seems to be that only one of those can be pursued, and each have severe problems, if not inescapable and intractable contradictions. In the meantime, what is a browser manufacturer supposed to do?
For those who have followed the PKI debate this will not surprise. What is stunningly new -- as in news -- is that this is the first time to my knowledge that a PKI user organisation has come out and said "we have a problem here, folks!" Actually, Frank doesn't say that in words, but if you understand what he writes, then you'd have to be pre-neanderthalic not to detect the discord.
What to do next is not clear -- so it would appear that this essay is simply the start of the debate. That's very welcome, albeit belated.
November 13, 2005
Amazon starts a Task Market
Amazon have started what looks like a task market with an unusual name - the Amazon Mechanical Turk. Pointed to by C Walsh.
This could be successful if only for its two cool features: the cool name and the incorporation of webservices. The core idea itself has been around for yonks and even well before I presented on task markets at FC97.
What is curious is that instead of going for the geek in everyone, they've actually listed very small low value tasks. They truely are targetting the brains of the net, not the geeks. Here's such a task:
You are presented with the name and address of a business as well as a set of photos taken along the street where the business is supposed to be located. Your task is to identify the best photo of the business that is listed.
For that task you will be paid 3 cents into your Amazon account!
November 05, 2005
Musings on IP - one good way for DRM and one bad way?
Darren points to a great story about the development of intellectual property ("IP") - someone in the United States has apparently succeeded in applied for a patent on a unique plot line for a novel or film.
Process of relaying a story having a unique plotAbstract A process of relaying a story having a timeline and a unique plot involving characters comprises: indicating a character's desire at a first time in the timeline for at least one of the following: a) to remain asleep or unconscious until a particular event occurs; and b) to forget or be substantially unable to recall substantially all events during the time period from the first time until a particular event occurs; indicating the character's substantial inability at a time after the occurrence of the particular event to recall substantially all events during the time period from the first time to the occurrence of the particular event; and indicating that during the time period the character was an active participant in a plurality of events.
Do we need IP control over plot lines? It is not clear to me that it helps at all as the costs of managing such seem in excess of the benefit. Unlike the filer, I don't think we are doomed to just use the same old plot lines forever because we have no incentive to innovate - the artists I know are continually experimenting on new ideas and need no additional incentives in that direction.
On the other hand they do need better systems to exploit commercially what they have made. (Don't we all?) So rather than expand plot lines to patentable ideas, why not concentrate on what we have - the better commercialisation of the property that is there?
That's what I am looking at now. Take some copyrighted material like a song. Whack a licence on it and push it out to the net. How then can we sell it?
One idea is to turn the material into some form digital contract variant - write a contract, describe the IP, add some clauses, sign, seal and deliver. (Savvy FCers will recognise the Ricardian flavour there.) Then, we could issue a bunch of these.
How does this make a market? One way is that the rights could only be exploited - used - if you have one of these in your portfolio. So if I have released a song under these licences, you'd have to buy one of these rights on the open market. Now here's the cool part: when you have finished with the song and got bored of it, you could sell it on!
The Issuer would be happy with this as pricing would then reach some sort of stability around demand. Supply could be set initially as fixed - just like editions of prints by picture artists. And, if there was a transaction fee for transfer of a few percentage points, every time the song right got sold, there would be a steady revenue stream coming into the rights holder's pot.
I can't see a flaw in this design, although I can see some arbitrary complications I skipped over for brevity. Any comments?
PS: this is not an enforced design - all this does is trade the rights, not control them. It would work for those that choose to participate. (Also, I'm not entirely sure that I'm the first person to think of it. But it doesn't seem to relate to other people's designs that I'm aware of.)
October 12, 2005
The Mojo Nation Story - Part 2
[Jim McCoy himself writes in response to MN1] Hmmm..... I guess that I would agree with most of what Steve said, and would add a few more datapoints.
Contributing to the failure was a long-term vision that was too complex to be implemented in a stepwise fashion. It was a "we need these eight things to work" architecture when we were probably only capable of accomplishing three or four at any one time. Part of this was related to the fact the what became Mojo Nation was originally only supposed to be the distributed data storage layer of an anonymous email infrastructure (penet-style anonymous mailboxes using PIR combined with a form of secure distributed computation; your local POP proxy would create a retrieval ticket that would bounce around the network and collect your messages using multiple PIR calculations over the distributed storage network....yes, you can roll your eyes now at how much we underestimated the development complexity...)
As Bram has shown, stripping MN down to its core and eliminating the functionality that was required for persistent data storage turned out to create a pretty slick data distribution tool. I personally placed too much emphasis on the data persistence side of the story and the continuing complexity of maintaining this aspect was probably our achilles heel, if we had not focused on persistence as a design goal and let it develop as an emergent side-effect things might have worked but instead it became an expensive distraction.
In hindsight, it seems that a lot of our design and architecture goals were sound, since most of the remaining p2p apps are working on adding MN-like features to their systems (e.g. combine Tor with distributed-tracker-enabled BitTorrent and you are 85% of the way towards re-creating MN...) but the importance of keeping the short- term goal list small and attainable while maintaining a compelling application at each milestone was a lesson that I did not learn until it was too late.
I think that I disagree with Steve in terms of the UI issues though. Given the available choices at the time we could have either created an application for a single platform or use a web-based interface. The only cross-platform UI toolkit available to us at the time (Tk) was kinda ugly and we didn't have the resources to put a real UI team together. If we were doing this again today our options would include wxWidgets for native UI elements or AJAX for a dynamic web interface, but at the time a simple web browser interface seemed like a good choice. Of course, if we had re-focused on file-sharing instead of distributed persistent data storage we could have bailed on Linux & Mac versions and just created a native win32 UI...
The other point worth mentioning is that like most crypto wonks, we were far too concerned with security and anonymity. We cared about these features so we assumed our users would as well; while early adopters might care the vast majority of the potential user base doesn't really care as much as we might think. These features added complexity, development time, and a new source of bugs to deal with.
Jim
Back to Part 1 by Steve.
eBay migrates to the Payments business
Jim points out that eBay is to purchase the VeriSign payments gateway business:
eBay’s PayPal said the acquisition would enable it to include new small- and medium-size business customers in its user base, as well as expand its repertoire of payment processing options. Recently, many startups have entered the online payments business, especially those targeting the market that has sprung up around the purchase and sale of digital content.
And more at PaymentNews. This adds further strength to the thoughts that came out of the Skype purchase. eBay is moving into the payments world in a big way; it's establishing a stable of user bases that all trade money around a common payment system.
So why Skype? Firstly, the Skype user base chews through lots of little payments in the SkypeOut service. And they aren't going to stop doing that. Secondly, Skype is secure (**) and has a downloaded client base with a plugin architecture. For business people that's very ho-hum, but for students of money, that's golden. Thirdly, Skype has the communications future all sown up: it's chat and it's IM. The significance of this is immense when you consider that PayPal is web, it's email, and it's ridden with fraud with no end in sight.
And, what held back Skype? Access to payments. Within their world, people had to work very hard to get money into the accounts so they could do the SkypeOut thing. Obviously nobody was that interested in helping Skype get access to payment systems on a mass scale. With eBay's clout, and VeriSign's mature payments business this is a solved problem.
Look for Skype to integrate a payment system some time. It might be branded PayPal but it probably won't be the same thing under the hood (or bonnet). Also, look to eBay buying more user bases and more facilitation architecures (e.g., plugins) that are small-payment oriented. (I can think of one right now, but people will be angry if I state it ...)
Risks: the same thing that happened to Bill Gates when he said he wanted to get into payments. When the banks realise that eBay is building a bigger and better payments infrastructure, they will complain to their mamas and papas and ask them to go beat up the bad boy. (Problem is, the rationale for discrimination of payments v. banking v. business is pretty darn weak these days, so if eBay has its eye on the ball, this won't be the slam dunk that Bill G had to accept.)
Recommendation: eBay is probably a buy if this is really their strategy.
(**) I mean here, more secure than the alternate which is approximately PayPal.
October 09, 2005
Journal of Internet Banking and Commerce
Vol 10 No. 2 Summer 2005 of JIBC is out now:
- From JIBC Publisher Nahum Goldmann
- From Editor-in-Chief Nikhil Agarwal
General and Review Articles
- Belgium EEMA: Focus on Technical and Legal Issues of e-Business in the European Union (By: Edwin JACOBS,University of Leuven)
- China Current Development Situation of E-Commerce in China (By: Alamusi, ChinaEClaw.com)
- USA B2B Marketers Integrate Precision Search to Boost Profitability and Increase Satisfaction Across the eCommerce Value Chain (By: Larry R. Harris, EasyAsk, a division of Progress Software)
- Canada Trust and Confidence and the Digital Economy: Issues and Challenges (By: Prabir K. Neogi and Arthur J. Cordell, Industry Canada)
Research Papers
- Belgium Security as a Legal Obligation: About EU Legislation Related to Security and Sarbanes Oxley in the European Union (By: Edwin JACOBS, University of Leuven)
- Belgium The Law on Electronic Medical Prescription (By: Francis de Clippele, Lawyer in Antwerp, Assistant Lecturer at the University of Antwerp)
- Canada Trust and Confidence and the Digital Economy: Issues and Challenges (By: Prabir K. Neogi, Arthur J. Cordell, Electronic Commerce Branch, Industry Canada)
- India Technical and Entrepreneurial Research Information System: An Applied e-Model for Sustainable Entrepreneurship Development (By: Dhrupad Mathur, S P Jain Institute of Management & Research, Mumbai)
- India A Framework for Evaluating e-Business Models and Productivity Analysis for Banking Sector in India (By: NVM Rao, Prakash Singh, and Neeru Maheshwari, BITS, Pilani)
- Malaysia Do Foreign Banks Lead in Internet Banking Services (By: Boon Han YEAP, Monash University Malaysia, and Kooi Guan CHEAH, Universiti Sains, Malaysia)
- Malaysia Marketing Mix: A Review of 'P' (By: Chai Lee GOI, Curtin University of Technology, Malaysia)
- Qatar E-banking Service Quality: Gaps in the Qatari Banking Industry (By: Norizan M. Kassim, University of Qatar)
- USA and Singapore A Case Study of Electronic Bill Presentment and Payment (EBPP) Integration Using the COIN Mediation Technology (By: Sajindra Jayasena, National University of Singapore, Stephane Bressan, Sloan School of Management and Stuart Madnick, Massachussets Institute of Technology)
Read on for abstracts....
General and Review Articles
BELGIUM: EEMA: Focus on Technical and Legal Issues of e-Business in the European Union
(By Edwin Jacobs)
http://www.aaraydev.com/commerce/JIBC/EdwinJacobs_EEMA_210705,asp
EEMA is Europe's leading independent association for e-Business and promotes collaboration concerning all technical (ICT), legal and business aspects of e-business. EEMA puts the emphasis on today's practical issues. In this respect, EEMA's Legal Interest Group, headed by Prof. Jos Dumortier, focuses on all legal aspects of e-business, i.e. electronic signature, e-invoice, identity management, security legislation (e.g. Sarbanes Oxley in the EU), privacy, etc. On November 22nd and 23 rd this year EEMA will organise a two-day seminar about electronic invoicing and electronic archiving in Brussels.
CHINA: Current Development Situation of e-Commerce in China
(By Alamusi)
http://www.arraydev.com/commerce/JIBC/2005-08/china.htm
The Chinese government puts a great deal of emphasis on E-Commerce work extremely. Generally speaking, the China E-Commerce market contains huge commercial opportunity, the development prospect of which is extremely broad. The relevant organizations are complying with and guiding commercial transformation tendency, absorbing latest international achievement of technical platform, payment system, creditability system, platform construction and safety guarantee system in E-Commerce, further optimizing the external environment, and speeding up development and innovating application complying with national features.
USA: B2B Marketers Integrate Precision Search to Boost Profitability and Increase Satisfaction Across the e-Commerce Value Chain
(By Larry R. Harris)
http://arraydev.com/commerce/JIBC/2005-08/Harris.asp
This article will describe the central role that site search and navigation plays in B2B eCommerce, as well as the defining characteristics of a successful search implementation from both a technical and marketing perspective. This article will also outline how integrating precision search into an existing eCommerce infrastructure can result in higher productivity, streamlined processes, increased conversion rates, greater commercial buyer and partner satisfaction, and higher profits per transaction.
Research Papers
BELGIUM: Security as a Legal Obligation: About EU Legislation Related to Security and Sarbanes Oxley in the European Union
(By Edwin Jacobs)
http://www.arraydev.com/commerce/JIBC/2005-08/security.htm
Since the Sarbanes-Oxley Act there is a worldwide focus on security issues in general. This new focus seems to emphasize that security is a new kind of legal obligation. However, security is already a legal obligation for all EU companies since the early nineties. On top of that, in electronic banking there is a whole range of legal obligations in some way related to security, that were already (and remain) applicable, notwithstanding a possible application of the Sarbanes-Oxley Act on some EU companies. The criterion of what can be 'reasonably expected' as 'bonus pater familias' from service providers, but equally also from their customers, becomes increasingly important.
BELGIUM: The Law on Electronic Medical Prescription
(By Francois de Clippele)
http://www.arraydev.com/commerce/JIBC/2005-08/EMV.HTM
Health care is one of the most important economic and business areas. The European Union has therefore worked out an e-health care strategy to achieving stronger growth and increased effectiveness of services. The application of information and communications technologies (ICT) that affect the health care sector is developing fast in Europe. In this respect various countries have launched pilot projects in order to modernize their medical prescription practices. A model of the electronic medical prescription must respect patient's rights and can only be deployed in a system of security in order to protect the confidentiality.
CANADA: Trust and Confidence and the Digital Economy: Issues and Challenges
(By Prabir K. Neogi and Arthur J. Cordell)
http://www.arraydev.com/commerce/JIBC/2005-08/Negi.htm
Globalization and technological change continue to profoundly affect economic growth and wealth creation. Information and Communications Technologies (ICTs) have been a key enabler and driver of globalization, which is likely to continue as trade and investment barriers continue to fall and communications become ever cheaper, easier and more functional. Every economy requires a physical, institutional and legal infrastructure, as well as understandable and enforceable marketplace rules, in order to function smoothly. In this paper the authors maintain that such an infrastructure must be developed for the new digital economy and society, one that provides trust and confidence for all those who operate in or are affected by it.
INDIA: Technical and Entrepreneurial Research Information System: An Applied e-Model for Sustainable Entrepreneurship Development
(By Dhrupad Mathur)
http://www.arraydev.com/commerce/JIBC/2005-08/DhrupadMathur.asp
This article stresses on the need for an e-application like Technical and Entrepreneurial Research Information System (TERIS), which enables interaction among academia, industry and various agencies related to researchers for sustainable entrepreneurship development. The functional details of the model are also discussed. This article is based on inputs with reference to the state of Rajasthan. However, the model can very well be replicated elsewhere.
INDIA: A Framework for Evaluating e-Business Models and Productivity Analysis for Banking Sector in India
(BY N.V.M. Rao, Prakash Singh ans Neeru Maheshwari)
http://www.arraydev.com/commerce/JIBC/2005-08/maheshwari.htm
This study is an effort to draw together some of the e-Business models and real-life experiments that has been circling around the e-business models. To study the sweeping changes brought about by e-initiative measures in the banking sector some banks were chosen, from public sector like SBI, BOB etc and from private sector like ICICI, HDFC etc.
MALAYSIA: Do Foreign Banks Lead in Internet Banking Services
(By Boon Han Yeap and Kooi Guan Cheah)
http://www.arraydev.com/commerce/JIBC/2005-08/JIBC_yeap%20&%20cheah.asp
Internet banking has been increasingly used as a delivery channel in retail consumer banking. As far as the provision of internet banking services in developing countries is concerned, foreign banks definitely enjoy distinct advantages over domestic banks due to their experiences in other, more advanced financial markets. This paper reports a study that examined the levels of retail internet banking services provided by foreign and domestic commercial banks in Malaysia over a period of two years. The study found that while foreign banks are marginally more sophisticated at information provision level, domestic banks offer a significantly higher level of transactional facilities in both years.
MALYASIA: Marketing Mix: A Review of "P"
(By Chai Lee Goi)
http://www.arraydev.com/commerce/JIBC/2005-08/goi.HTM
There has been a lot of debate in identifying the list of marketing mix elements. The traditional marketing mix by McCarthy (1964) has regrouped Borden's (1965) 12 elements and has comprised to four elements of product, price, promotion and place. A number of researchers have additionally suggested adding people, process and physical evidence decisions (Booms and Bitner, 1981; Fifield and Gilligan, 1996). The other suggested Ps are personnel, physical assets and procedures (Lovelock, 1996; Goldsmith, 1999); personalization (Goldsmith, 1999); publications (Melewar and Saunders, 2000); partnerships (Reppel, 2003); premium price, preference of company or product, portion of overall customer budget and permanence of overall relationship longevity (Arussy, 2005); and 2P+2C+3S formula (Otlacan, 2005), therefore personalisation, privacy, customer Service, community, site, security and sales promotion.
QATAR: E-Banking Service Quality: Gaps in the Qatari Banking Industry
(By Norizan M. Kassim)
http://www.arraydev.com/commerce/JIBC/2005-08/KassimTry.asp
Financial liberalization and technology revolution have allowed the developments of new and more efficient delivery and processing channels as well as more innovative products and services in banking industry. Banking institutions are facing competition not only from each other but also from non-bank financial intermediaries as well as from alternative sources of financing, such as the capital markets. Another strategic challenge facing banking institutions today is the growing and changing needs and expectations of consumers in tandem with increased education levels and growing wealth. Consumers are becoming increasingly discerning and have become more involved in their financial decisions. For this reason, they are demanding a broader range of products and services at more competitive prices through more efficient and convenient channels. This study investigates the discrepancy between customer's expectation and perception towards the e-banking services.
USA/SINGAPORE: A Case Study of electronic Bill Presentment and Payment (EBPP) Integration Using the CON Mediation Technology
(By Sajindra Jayasena and Stephane Bressan)
http://arraydev.com/commerce/JIBC/2005-08/Jayasema.asp
By its very nature, financial information, like the money that it represents, changes hands. Therefore the interoperation of financial information systems is the cornerstone of the financial services they support. In this paper we illustrate the nature of the problem in the Electronic Bill Presentment and Payment industry. In particular, we describe and analyze the difficulty of the integration of services using four different formats: IFX, OFX and SWIFT standards, and an example proprietary format. We then propose an improved way to accomplish this integration using the Context Interchange (COIN) framework.
Administrative Notice
Journal of Internet Banking and Commerce
JIBC is a leading edge publication that informs banking and electronic commerce professionals and executives on principal developments, benchmark practices, and future trends in the Internet-based marketing practices of governments and industry. This free online interactive journal is a way to keep in touch, to share information, and to establish business contacts (networking) for worldwide professionals that specialize in electronic commerce, governance and banking
solutions.
In JIBC you will find informed discussion of the latest internet-based banking and electronic trends and practices from around the world. Our priority is quality, not quantity. We want to maintain JIBC as a service that provides substantial information and an effective forum for your articles, your letters, your insights and ideas.
JIBC invites banking and electronic commerce professionals, academicians and publishers to submit important announcements, original articles, guest columns and significant feature presentations. We also welcome surveys, book reviews and letters to the Editor. Technical discussions in highly specialized areas of expertise will be kept to an absolute minimum.
JIBC is formally issued three to four times a year when an email summary of current articles is distributed to subscribers. The full text of current articles is posted on the JIBC Web site at
http://www.ARRAYdev.com/commerce/JIBC/current.asp.
The publication is complemented by the Compendium of Internet Banking and Commerce Initiatives at:
http://www.arraydev.com/frames/f-guest_comp.htm.
We invite readers to provide brief descriptions of products, books, and services that they think others will find interesting.
The Journal of Internet Banking and Commerce (JIBC) is provided as a service by ARRAY Development based in Ottawa, Canada. Views expressed are those of the authors and are not necessarily shared by ARRAY Development. Firms or individuals interested in sharing sponsorship of this project may contact array (at) ARRAYdev.com.
The JIBC Web Archive
http://www.arraydev.com/commerce/jibc/articles.htm contains all articles published to date.
You can reach the Editor-in-Chief Nikhil Agarwal with any questions or comments by email at:
nikhil.jibc (at) gmail.com
Publisher Nahum Goldmann is at:
Nahum.Goldmann (at) ARRAYdev.com.
Editorial Board
Publisher and Member of the Editorial Board: Nahum Goldmann
Chief Editor: Nikhil Agarwal
Founding Chief Editor Emeritus and Member of the Editorial Board: Gord Jenkins
Assistant Editor: Xin "Robert" Luo
Mailing List Managing Editor: Anne-Marie Jennings
Contributing Editors
U.K. Contributing Editor: David G.W.Birch
Australia Contributing Editor: Dale Pinto
Japan Contributing Editor: Carin Holroyd
Nordic Countries Contributing Editor: Minna Mattila
Legal Contributing Editor: Edwin Jacobs
Middle East Contributing Editor: Raed Awamleh
Africa Contributing Editor: Alemayehu Molla
France Contributing Editor: Jean-Michel Sahut
Please send any questions related to maintenance of this Web site to:
array (at) ARRAYdev.com
Information and subscription for JIBC mailing list is available via:
http://groups.yahoo.com/group/JIBC/
August 21, 2005
Computer characters mugged in virtual crime spree
I often say that you can only tell if some FC application is successful when you see crime start to appear. Games are now massive successes in creating value and payment systems, again showing that the Finance layer is more important than the rest put together.
Computer characters mugged in virtual crime spree 11:31 18 August 2005 NewScientist.com news service Will KnightA man has been arrested in Japan on suspicion carrying out a virtual mugging spree by using software "bots" to beat up and rob characters in the online computer game Lineage II. The stolen virtual possessions were then exchanged for real cash.
The Chinese exchange student was arrested by police in Kagawa prefecture, southern Japan, the Mainichi Daily News reports.Several players had their characters beaten and robbed of valuable virtual objects, which could have included the Earring of Wisdom or the Shield of Nightmare. The items were then fenced through a Japanese auction website, according to NCsoft, which makes Lineage II. The assailant was a character controlled by a software bot, rather than a human player, making it unbeatable.
Ren Reynolds, a UK-based computer games consultant and an editor of the gaming research site Terra Nova, says the case highlights the problem of bots in virtual worlds. Arms race
By performing tasks within a game repetitively or very quickly, bots can easily outplay human-controlled characters, giving unscrupulous players an unfair advantage. Many games firms employ countermeasures to detect this bot activity. For example, they can ask the character questions or present them with an unfamiliar situation and monitor their response.
"There's an ongoing war between people who make bots and games companies," he told New Scientist. "And making real money out of virtual worlds is getting bigger."
...
August 11, 2005
A Small Experiment with Voting - Mana v. Medici
Voting is a particularly controversial application (or feature) for FC because of the difficulty in both setting the requirements, and the 'political requirement' of ensuring a non-interfered vote for each person. I've just got back from an alpine retreat where I participated in a small experiment to test votes with tokens, called Beetle In A Box. The retreat was specifically purposed to do the early work to build a voting application, so it was fun to actually try out some voting.
Following on from our pressed flower production technique, we 'pressed & laminated' about 100 'beatles,' or symbols looking like squashed beatles. These were paired in plus and minus form, and created in sets of similar symbols, with 5 colours for different purposes. Each person got a set of 10, being 5 subsets of two complementary pairs each.
The essence of the complicated plus and minus tokens was to try out delegated voting. Each user could delegate their plus token to another user, presumably on the basis that this other user would know more and was respected on this issue. But they could always cast their minus to override the plus, if they changed their minds. More, it is a sad fact of voting life that unless you are in Australia, where political voting is compulsory, most people don't bother to turn up anyway.
To simulate this, we set up 4 questions (allocating 4 colours) to be held at 4 different places - a deliberate conflict. One of the questions was the serious issue of naming the overall project and we'd been instructed to test that; the others were not so essential. Then we pinned up 21 envelopes for all the voters and encouraged people to put their plus tokens in the named envelope of their delegatee.
When voting time came, chaos ensued. Many things went wrong, but out of all that we did indeed get a vote on the critical issue (not that this was considered binding in any way). Here's the stats:
Number of direct voters: 4 Number of delegated votes: 3 Therefore, total votes cast: 7 Winning project name: Mana, with 3 votes.
So, delegated voting increased the participation by 75%, taking total participation to 33% (7 of 21 participants). That's significant - that's a huge improvement over the alternate and indicates that delegated voting may really be useful or even needed. But, another statistic indicates there is a lot more that we could have done:
Number of delegated votes, not cast: 9
That is, in the chaos of the game, many more people delegated their votes, but the tokens didn't make it to the ballot. The reasons for this are many: one is just the chaos of understanding the rules and the way they changed on the fly! Another is that many delegatees simply didn't participate at all, and in particular the opinion leaders who collected fat envelopes forgot they were supposed to vote, and just watched the madness around them (in increasing frustration!).
Canny FCers will recognise another flaw in the design - having placed the tokens into envelopes, the delegators then had to become delegatees and collect from their envelopes. And, if they were not to then attend that meeting (there were 4 conflicting meetings, recall) then the delegatees would become delegators again and re-delegate. Thus forcing the cycle to start again, ad infinitum.
Most people only went to the pinboard once. So the formal delegation system simply failed on efficiency grounds, and it is lucky that some smart political types did some direct swaps and trades on their delegated votes.
How then to do this with physical tokens is an open question. If one wants infinite delegation, I can't see how to do it efficiently. With a computer system, things become more plausible, but even then how do we model a delegated vote in software?
Is it a token? Not quite, as the delegate vote can be overridden and thus we need a token that can be yanked back. Or overridden or redirected. So it could be considered to be an accounting entry - like nymous account money - but even then, the records of a payment from alice to bob need to be reversable.
One final result. Because I was omnipresent (running the meeting that took the important vote) I was able to divine which were the delegated votes. And, in this case, if the delegated votes had been stripped out, and only direct voting handled, the result of the election decision would have changed: the winning name would have been Medici, which was what I voted for.
Which I count as fairly compelling evidence that whatever the difficulties in implementing delegated voting, it's a worthwhile goal for the future.
July 18, 2005
How to do Hayekian Private Issuance
Robert Murphy defends Hayek's proposals for private issuance against Mises and Rothbard. Such is of course welcome but bemusing; as it does not take into account modern developments in the financial cryptography world, it seems quaint and historical. This is now a solved problem, and I suppose if I'd thought about it I would have written a paper on it!
Private issuance of monies by corporations is easy and within reach of all. The technical problems are solved, as are the economic interests and the value feedback equations. I know this because I - or my company - have been issuing for two (oops not four) years now, and even though our scale is tiny, it still works so efficiently that I cannot see a circumstance where the company would choose not to issue.
Corporate issuance works like this:
A company creates a contract that redeems for any service the company offers. Not gold, not a basket of Walmart items, etc etc. It redeems in its own services and units. All commercial companies have some sort of service or good, by definition, although I grant non-profits sometimes do not. This of course means we need an external unit of account, but that's no problem.
Then, the corporation pays all its people in the issue. Every month their paychecks come in the corporate unit. As this is a digital operation, it is painless and quick.
Finally, all purchasers to the company are instructed to pay all invoices in the corporate issue. In order to get their corporate units they contact the employees and arrange a trade. Purchasers might have gold, dollars or some other unit, and employees often need exactly those things. A trade is arranged, the value moves from the employees to the purchasers, and then back to the company as the invoice is paid.
All else is evolution. How does the company pay for bills in local national currency? Simple - we post a bill on the notice board (perhaps virtually) with an offer of X+1% in the corporate unit to get it paid. Maybe we need to up the number to 2% the next day, but soon enough someone will decide to do take the profit.
How do buyers find sellers? In our small scenario by word of mouth. But markets would no doubt spring up once a threshhold is reached, and a market is nothing but a mailing list or a chatroom.
How does a big purchaser deal with lots of little sellers? Someone stands in as an intermediary, of course, a process that we have seen arise in recent times. How do profits get taken? How do shares dividends get paid? Taxes, etc etc - all the same way. These are all bills.
How is accountancy handled? This is perhaps the best bit. The system is its own accountancy system. Everyone has their own books for their own transactions (a la Triple Entry Accounting in FC++ #2) and the need to keep a separate book of accounts disappears.
How is bankrupcy handled? Perhaps testament to the power of this system, it works as well in times of lean payments as it does in boom time. That's because of the strong recording capabilities of the digital payments system means that what was liquid converts seamlessly into debt, thus relieving everyone of the need to account for their position. In fact, we originally floated the new issue in a time of quasi-bankrupcy, and within a single weekend, every employee had converted their notes, their promises, their deferred invoices into corporate issue. Because it was so much easier and so much clearer.
Is it efficient? On a small scale, for users, it can be about as much work as dealing with the average invoice, per transaction. As scale ramps up, it reduces to about the same order of cost of getting a coffee out of a coin-powered machine.
For the issuer, it has one final magic component - it raises long term financing on floating terms. Nominally at zero percent, the costs of holding and converting and indeed financing the working capital are worked out in the exchange rate between the corporate rate and local units. Your employees are your investment bank; it's painless and obviates the need for a CFO until you've added another two zeros to the revenues. Yet another saving.
June 22, 2005
Skype - a prince but still covered in warts
Skype might be justly lauded in these pages for doing something that only one other product has ever done - getting crypto to the masses in a usable fashion. And it is fair to say that Skype is a killer app in the making. Truly a rising star, definately a joy to watch its progress.
But other than those positive points, it seems that Skype is just like any other crummy business with a crummy app and a crummy attitude to users. Yesterday I spent an afternoon trying to get it working on a linux box, and failed.
Here's the bug list: no obvious way to test the product, no selftest feature, no button, no ping is evident on the screen for both chat or voice. It turns out there is a voice test server called echo123, but that's buried in a FAQ somewhere. No help for the newbie at all as even in the FAQ it isn't clear what they were talking about unless you happen to have used one of these things before.
Secondly, the FAQs could not help. All the basic "windows user level" stuff like where to find your windows firewall was covered, but what it didn't cover was whatever was wrong with this fairly boring setup. (Linux box, Fedora core 3 distro, behind a DHCP router, all outgoing ports open.) The actual failure mode was this: No connection made for voice - to echo or anywhere else, the application just sits there saying "connecting...." forever. (No timouts even. This is a sick app.)
So without a proper way to test and some sort of feedback, it's not possible to even guess where the problem lies. Oddly, chat would send ONE and exactly one message out, and receive ONE and exactly one message in, before disengaging and shutting up. Restarting the application gets you another one message, in and out.
Meanwhile, within 24 hours of starting, I got sent a phish on the email address I created for the account yesterday. Thanks guys - there is really no point in you collecting email addresses if you are going to give them out to phishers. In this case it was a fairly obvious "answer this survey" but what happens when the phishers get smart and learn how to spell? What happens when I need to change my password and the spam filters have blocked that email address?
June 01, 2005
Software Licensing and the Know-how to Issue
Software charging for big ticket sellers is getting more complex again, as dual cores from AMD and Intel start to invade the small end. Oracle, which made billions charging on the muscle power of CPUs, will have to do something, and we've by now all seen IBM's adverts on TV suggesting "on demand" with its concommitant charging suggestion: You demand, we charge.
I've done a lot of thinking over the years about how to licence big ticket items like issuance software. In practice it is very difficult, as the only revenue model that makes sense for the supplier is for large up front licence fees to recover large up front capital and sunk costs. But for the demander (issuer and user of the software) the only model that makes sense is to pay later, when the revenues start flowing...
Issuance software has all the hallmarks of an inefficient market and I don't think there has been successful case of issuance licencing yet, as those two "sensible" options do not leave any room for agreement. This may be rational but it's very frustrating. Time and again, we see the situation of people wanting to get into the issuance market who think they can produce the software themselves for a cheaper price. And they always end up spending more and getting a lesser quality product.
In practice what we (Systemics) have been doing is this: running the software ourselves as "operator", and charging operating costs, with some future licencing or transaction flow revenues. Yet, the deal for future revenues is always based on a promise and a prayer, which is already asymmetrical given that most startups do no more than start up. (And it isn't just me bemoaning here - if you look back through history there are literally hundreds of companies that tried to build value issuance and sell it.)
Which leads to the freeware model. In the freeware world, big ticket items are given away and money is made on the consulting. This has worked relatively well in some areas, but doesn't work so well in issuance. I'm unclear of the full reason why open source software doesn't work in issuance, but I think it is mostly the complexity, the sort of complexity I wrote about in FC7. It's not that the software can't capture that complexity but that the financial cryptography business often finds itself so squeezed for management complexity that partnering with a strong software supplier are beyond capabilities.
What will potentially help is p2p issuance. That is, "everyone an issuer." We've always known this model existed even as far back as 1995, but never really considered it seriously because too many questions arose. Little things like how we teach grandma to sign a digital contract. We've now done enough experiments in-house to confirm that the corporate internal issue and the individual issue are workable, sustainable economic models but we have to get other companies and individuals to do that and for the most part they still don't do anything they don't understand.
I'm guessing the way forward here is to turn client software into issuance software. This brings up a whole host of issues in financial cryptographic architecture. For a start it can never seriously scale simply because people do silly things like turn off their laptops at night.
But, more and more, the barriers to issuance and financial cryptography in general I believe are spreading the knowledge, not the tools and tech. Every year our tools and tech get better; but every year our real barriers seem the same - how to get users and customers to make their first tentative issue of a currency of value. Oh, and how to make money so as to keep us all alive, which was the starting point on this long rant of liberal licence.
A couple of footnotes: In a similar thread over at PGP Inc, Will Price reveals how they've managed to get out of the legacy freeware version trap:
"When the 30 Day Trial version of PGP Desktop Home expires, it reverts to a set of functionality comparable to what used to be known as Freeware, and said functionality remains available indefinitely -- under the same license conditions as Freeware used to be under."
Nice one. That works for client software, not for server software.
Here's a further article on how the big companies are also working out how big ticket software isn't the way to go:
May 10, 2005
Games, P2P and currency ...
It's not often we see Finance layer thoughts out there. Here's a fascinating snippet:
Take "Second Life," the virtual world created by Linden Labs. Rather than offer a traditional game environment like "EverQuest," it provides a growing world in which inhabitants can build their own homes, create their own "in-game" games, run businesses or do pretty much anything else that strikes their fancy."Second Life" has 28,000 people online today, and some inhabitants are already making more than $100,000 a year in real-world money by selling digital wares constructed inside the world or running full-fledged role-playing games.
"Second Life" is built on a distributed model, in which numerous servers are connected together, each one representing about 16 acres of land in the digital world. Those patches of digital space are seamlessly connected together to create the world as experienced by visitors.
Today, all of those servers are run by Linden Labs, but the world was built to ultimately support a peer-to-peer model, where players might add their own 16-acre plot into the world from their own computer, said Linden Labs' chief executive officer, Philip Rosedale. For security reasons--including the fact that a real currency is traded inside the world--the company hasn't taken that step yet, however.
...
March 28, 2005
Euromail - Slate's Eric Weiner asks a question?
Rarely does anyone bother to sit down and ponder why the world is so crazy, and ask why those people over the other side are so different. Asking questions is anathema to the times we live in, and I have living proof of that - I occasionally throw out completely unbelievable statements and rarely if ever am I asked about them. I'm told, I'm challenged, and I'm damned. But never asked...
So it is with some surprise that an American (!) has sat down and thought about why Europeans email the way they do, and why Americans email the way they do. A thoughtful piece. Once you've read it, I'd encourage you to try something different: ask a question, try and work out the answer.
(Oh, and the relevance to Financial Cryptography is how people communicate and don't communicate, where communication is the meta-problem that FC is trying to solve. Thanks to Jeroen to pointer... And for a more amusing perspective on asking questions, try Dilbert)
Euromail
What Germans can teach us about e-mail.
By Eric Weiner
Posted Friday, March 25, 2005, at 4:17 AM PT
North America and Europe are two continents divided by a common technology: e-mail. Techno-optimists assure us that e-mail—along with the Internet and satellite TV—make the world smaller. That may be true in a technical sense. I can send a message from my home in Miami to a German friend in Berlin and it will arrive almost instantly. But somewhere over the Atlantic, the messages get garbled. In fact, two distinct forms of e-mail have emerged: Euromail and Amerimail.
Amerimail is informal and chatty. It's likely to begin with a breezy "Hi" and end with a "Bye." The chances of Amerimail containing a smiley face or an "xoxo" are disturbingly high. We Americans are reluctant to dive into the meat of an e-mail; we feel compelled to first inform hapless recipients about our vacation on the Cape which was really excellent except the jellyfish were biting and the kids caught this nasty bug so we had to skip the whale watching trip but about that investors' meeting in New York. ... Amerimail is a bundle of contradictions: rambling and yet direct; deferential, yet arrogant. In other words, Amerimail is America.
Euromail is stiff and cold, often beginning with a formal "Dear Mr. X" and ending with a brusque "Sincerely." You won't find any mention of kids or the weather or jellyfish in Euromail. It's all business. It's also slow. Your correspondent might take days, even weeks, to answer a message. Euromail is also less confrontational in tone, rarely filled with the overt nastiness that characterizes American e-mail disagreements. In other words, Euromail is exactly like the Europeans themselves. (I am, of course, generalizing. German e-mail style is not exactly the same as Italian or Greek, but they have more in common with each other than they do with American mail.)
These are more than mere stylistic differences. Communication matters. Which model should the rest of the world adopt: Euromail or Amerimail?
A California-based e-mail consulting firm called People-onthego sheds some light on the e-mail divide. It recently asked about 100 executives on both sides of the Atlantic whether they noticed differences in e-mail styles. Most said yes. Here are a few of their observations:
"Americans tend to write (e-mails) exactly as they speak."
"Europeans are less obsessive about checking e-mail."
"In general, Americans are much more responsive to email—they respond faster and provide more information."
One respondent noted that Europeans tend to segregate their e-mail accounts. Rarely do they send personal messages on their business accounts, or vice versa. These differences can't be explained merely by differing comfort levels with technology. Other forms of electronic communication, such as SMS text messaging, are more popular in Europe than in the United States.
The fact is, Europeans and Americans approach e-mail in a fundamentally different way. Here is the key point: For Europeans, e-mail has replaced the business letter. For Americans, it has replaced the telephone. That's why we tend to unleash what e-mail consultant Tim Burress calls a "brain dump": unloading the content of our cerebral cortex onto the screen and hitting the send button. "It makes Europeans go ballistic," he says.
Susanne Khawand, a German high-tech executive, has been on the receiving end of American brain dumps, and she says it's not pretty. "I feel like saying, 'Why don't you just call me instead of writing five e-mails back and forth,' " she says. Americans are so overwhelmed by their bulging inboxes that "you can't rely on getting an answer. You don't even know if they read it." In Germany, she says, it might take a few days, or even weeks, for an answer, but one always arrives.
Maybe that's because, on average, Europeans receive fewer e-mails and spend less time tending their inboxes. An international survey of business owners in 24 countries (conducted by the accounting firm Grant Thornton) found that people in Greece and Russia spend the least amount of time dealing with e-mail every day: 48 minutes on average. Americans, by comparison, spend two hours per day, among the highest in the world. (Only Filipinos spend more time on e-mail, 2.1 hours.) The survey also found that European executives are skeptical of e-mail's ability to boost their bottom line.
It's not clear why European and American e-mail styles have evolved separately, but I suspect the reasons lie within deep cultural differences. Americans tend to be impulsive and crave instant gratification. So we send e-mails rapid-fire, and get antsy if we don't receive a reply quickly. Europeans tend to be more methodical and plodding. They send (and reply to) e-mails only after great deliberation.
For all their Continental fastidiousness, Europeans can be remarkably lax about e-mail security, says Bill Young, an executive vice president with the Strickland Group. Europeans are more likely to include trade secrets and business strategies in e-mails, he says, much to the frustration of their American colleagues. This is probably because identity theft—and other types of hacking—are much less of a problem in Europe than in the United States. Privacy laws are much stricter in Europe.
So, which is better: Euromail or Amerimail? Personally, I'm a convert—or a defector, if you prefer—to the former. I realize it's not popular these days to suggest we have anything to learn from Europeans, but I'm fed up with an inbox cluttered with rambling, barely cogent missives from friends and colleagues. If the alternative is a few stiffly written, politely worded bits of Euromail, then I say … bring it on.
Thanks to Pierre Khawand for research assistance.
Eric Weiner is a correspondent for NPR's Day to Day program.
Article URL: http://slate.msn.com/id/2115223/
March 27, 2005
S/MIME - breaching the barrier to sign
My first foray into S/MIME is ongoing. I say "ongoing" because I've completed the 3rd attempt to get it going without success and now have signing going!. The first was with the help of one of CACert's experts, and within 10 minutes or so of massive clicking around, I had a cert installed in my Thunderbird.
10 minutes to create a cert is total failure right there. There should be ONE button and it should take ONE second. No excuses. The notion that I need a cert to tell other people who I am - people who already know me - is so totally off the charts there are no words to describe. None that are polite anyway.
(Actually, there shouldn't even be a button, it should be created when the email account is created! Thanks to Julien for that observation.)
Anyway, to be a crypto scribbler these days one has to have an open mind to all cryptosystems, no matter who designed them, so I plough on with the project to get S/MIME working. No matter how long it takes. Whip me again, please.
There are three further signing problems with S/MIME I've seen today, beyond the lack of the button to make it work.
Firstly, it seems that the key exchage is based on signed messages. The distribution of your public key only happens when you sign a message! Recalling yesterday's recommendation for S/MIME signing (do not sign messages unless you know what that means) this represents a barrier to deployment. The workaround is to send nonsense signed messages to people who you want to communicate with, but to otherwise turn signing off. Techies will say that's just stoopid, but consider this: It's just what your lawyer would say, and you don't want to be the first one to feel really stoopid in front of the judge.
Secondly, Daniel says that implementations first encrypt a message and sign it. That means that to show that a message is signed, you must de-sign it *and* decrypt it in one operation. As only the owner has the key to decrypt, only the owner can show it is signed! Dispute resolution is looking messy, even buggy. How can anyone be sure that that a signed message is indeed signed if there are layers separating message from signature? The RFC says:
In general, the best strategy is to "be liberal in what you receive and conservative in what you send"
Which might be good advice in Gnuland, but is not necessarily the best security advice. (I think Dan Bernstein said this.) Further, this puts the application in a big dilemma. To properly look after messages, they should be decrypted and then re-encrypted within the local database using the local keys. Otherwise the message is forever dependent on that one cert, right?! (Revoke the cert, revoke all messages?)
But if the message is decrypted, the signature is lost, so the signature can only ever form part of a message integrity function. Luckily, the RFC goes on to say that one can sign and encrypt in any order, so this would seem to be an implementation issue
That's good news. And (thirdly) it also takes the edge off of the RFC's suggestion that signatures are non-repudiable. FCers know well that humans repudiate, and dumb programs can't do a darn thing about it.
March 25, 2005
Digitally-Signed Mail in e-Commerce - FC05 survey
In a paper (sorry, PDF only) last month at FC05, Garfinkel and friends reported on an interesting survey conducted in two communities of merchants, one which received signed email from a supplier, and one which did not. This was an unusual chance to test two groups distinguished by usage of a crypto tool.
The biggest result to my mind is that users simply didn't as a body understand what the signed emails were all about. Even though these merchants were dealing with valuable transactions, the group that was receiving signed email only did a little better than the control group in knowing it (33% as opposed to 20%). This is a confusion that I'd expect, I recently installed a good cert into my Thunderbird and I still cannot send out signed or encrypted email using S/MIME (I forget why).
It's a very valuable survey, and welcome addition to the work of Ping, Friedman, et al, and of course Simson Garfinkel's thesis. I've copied the Conclusion below as anyone involved with email or user security should be aware of how real systems meet real users.
But there is one area where I take exception at. Garfinkel el al believe that commercial entities "should immediately adopt the practice of digitally-signing their mail to customers with S/MIME signatures using a certificate signed by a widely-published CA such as VeriSign."
Strongly Disagree! As there is nothing in the paper that indicates the meaning of a digital signature, this is a bad recommendation. Are they asking merchants to take on unlimited liability? Is this a simply a protection against forged emails? Or a checksum against network corruption? Without some thought as to what it is the merchant is promising, I'd recommend that signing be left off.
(Encryption, on the other hand, is fine. We can never have enough encryption. But this survey didn't cover that.)
Views, Reactions and Impact of Digitally-Signed Mail in e-Commerce
Abstract.We surveyed 470 Amazon.com merchants regarding their experience, knowledge and perceptions of digitally-signed email. Some of these merchants (93) had been receiving digitally-signed VAT invoices from Amazon for more than a year. Respondents attitudes were measured as to the role of signed and/or sealed mail in e-commerce. Among our findings: 25.2% of merchants thought that receipts sent by online merchants should be digitally-signed, 13.2% thought they should be sealed with encryption, and 33.6% thought that they should be both signed and sealed. Statistically-significant differences between merchants who had received the signed mail and those who had not are noted. We conclude that Internet-based merchants should send digitally-signed email as a best practice, even if they think that their customers will not understand the signatures, on the grounds that today s email systems handle such signatures automatically and the passive exposure to signatures appears to increase acceptance and trust.
4 Conclusions and Policy Implications
We surveyed hundreds of people actively involved in the business of e-commerce as to their views on and experience with digitally-signed email. Although they had not received prior notification of the fact, some of these individuals had been receiving digitally-signed email for more than a year. To the best of our knowledge this is the first survey of its kind
It is widely believed that people will not use cryptographic techniques to protect email unless it is extraordinarily easy to use. We showed that even relatively unsophisticated computer users who do not send digitally-signed mail nevertheless believe that it should be used to protect the email that they themselves are sending (and to a lesser extent, receiving as well).
We believe that digitally-signed mail could provide some measure of defense against phishing attacks. Because attackers may try to obtain certificates for typo or copycat names, we suggest that email clients should indicate the difference between a certificate that had been received many times and one that is being received for the first time much in the way that programs implementing the popular SSH protocol [15] alert users when a host key has changed.
We found that the majority (58.5%) of respondents did not know whether or not the program that they used to read their mail handled encryption, even though the vast majority (81.1%) use such mail clients. Given this case, companies that survey their customers as to whether or not the customers have encryption-capable mail readers are likely to yield erroneous results.
We learned that digitally-signed mail tends to increase the recipient s trust in the email infrastructure.We learned that despite more than a decade of confusion over multiple standards for secure email, there are now few if any usability barriers to receiving mail that s digitally-signed with S/MIME signatures using established CAs.
Finally, we found that people with no obvious interest in selling or otherwise promoting cryptographic technology believe that many email messages sent today without protection should be either digitally-signed, sealed with encryption, or both.
The complete survey text with simple tabulations of every question and all respondent comments for which permission was given to quote is at http://www.simson.net/smime-survey.html.
4.1 Recommendations
We believe that financial organizations, retailers, and other entities doing business on the Internet should immediately adopt the practice of digitally-signing their mail to customers with S/MIME signatures using a certificate signed by a widely-published CA such as VeriSign. Software for processing such messages is widely deployed. As one of our respondents who identified himself as a very sophisticated computer user wrote:
I use PGP, but in the several years since I have installed it I have never used it for encrypting email, or sending signed email. I have received and verified signed email from my ISP. I have never received signed email from any other source (including banks, paypal, etc, which are the organisations I would have thought would have gained most from its use).
Given that support for S/MIME signatures is now widely deployed, we also believe that existing mail clients and webmail systems that do not recognize S/MIME-signed mail should be modified to do so. Our research shows that there is significant value for users in being able to verify signatures on signed email, even without the ability to respond to these messages with mail that is signed or sealed.
We also believe that existing systems should be more lenient with mail that is digitally-signed but which fails some sort of security check. For example, Microsoft Outlook and Outlook Express give a warning if a message is signed with a certificate that has expired, or if a certificate is signed by a CA that is not trusted. We believe that such warnings only confuse most users; more useful would be a warning that indicates when there is a change in the distinguished name of a correspondent or even when the sender s signing key changes indicating a possible phishing attack.
March 15, 2005
More Pennies
Stefan posted a bunch of materials on a phone based ecash system.
On Identity theft, America's cartoonists are striking back. Click here and then send me your credit card number....
On the HCI thread of how users view web security, Chris points out that "Simson Garfinkel's dissertation is worth looking at in this context." This relates to the earlier two papers on what users think on web security.
Scott reports ``Visa International has published a white paper titled "Financial Flows and Supply Chain Efficiency" (sorry, in PDF) authored by Professor Warren H. Hausman of Stanford University.'' It's interesting if somewhat self-serving, and feeds into the whole message is the payment thread.
Stefan via Adam pointed me to a new blog on risks called Not Bad For a Cubicle. I shall pretend to know what that means, especially as the blogger in question claims knowledge of FC ... but meanwhile, the author takes task with persistent but poor usage of the word security, where 'risks' should be preferred. This makes a lot of sense. Maybe I should change all uses of the word over?
Because it's more secure becomes ... because it's less risky! Nice. But, wait! That would mean I'd have to change the name of my new paper over to Pareto-risk-free ... Hmm, let's think about this some more.
March 09, 2005
PayPal plus eBay - it's FC, not banking
FCers will recognise the confusion in this article by Kevin Kelleher about how to analyse eBay + Paypal:
"Here's a little-known fact about eBay (EBAY:Nasdaq) : It's not one of the most successful e-commerce companies in the world.It's actually two of the most successful e-commerce companies in the world -- eBay, the global network of auction and retail sites, and PayPal, its online-payment technology subsidiary that fuels the bulk of eBay transactions. Of the two, PayPal may emerge as the bigger phenomenon in the long run."
FCers see further than trying to model a payment system as a bank; it is a financial cryptography system that happens to have branded its Value structure. The Finance component is the auction, and the fact that the two companies grew up apart and together is simple reflection of the FC observation that you need both the finance and the value.
March 02, 2005
What is FC (iii) - Start from the Top.
In terms of definitions for FC, applying crypto to banking and finance doesn't work. Mostly because those doors are simply closed to us, but also because that's simply not how it is done. And this brings us to the big difference between Bob's view and FC7.
In Bob's view, we use crypto on anything that's important. Valuable - which is much more open than, say, the 'bank' view. But this is still bottom-up thinking and it is in the implicit assumption of crypto that the trouble lies.
Applications are driven top down. That means, we start from the application, develop its requirements and then construct the application by looking downwards to successively more detailed and more technical layers. Of course, we bounce up and down and around all the time, but the core process is tied to the application, and its proxy, the requirements. The requirements drive downwards, and the APIs drive upwards.
Which means that the application drives the crypto, not the other way around. Hence it follows that FC might include some crypto, or it might not - it all depends on the app! In contrast, if we assume crypto from the beginning, we're building inventions looking for a market, not solving real world problems.
This is at heart one of the major design failures in many systems. For example, PKI/SSL/HTTPS assumed crypto, and assumed the crypto had to be perfect. Now we've got phishing - thanks guys. DigiCash is the same: start from an admittedly wonderful formula, and build a money system around it. Conventional and accepted systems building practices have it that this methodology won't work, and it didn't for DigiCash. Another example is digital signatures. Are we seeing the pattern here? Assume we are using digital signatures. Further assume they have to be the same as pen&ink signatures.... Build a system out of that! Oops.
Any systems methodology keeps an open mind on the technologies used, and that's how it is with FC7. Unlike the other definitions, it doesn't apply crypto, it starts with the application - which we call the finance layer - and then drives down. Because we *include* crypto as the last layer, and because we like crypto and know it very well, chances are there'll be a good component of it. But don't stake your rep on that; if we can get away with just using a grab bag of big random numbers, why wouldn't we?
And this is where FC7 differs from Bob H's view. The process remains security-oriented in nature. The people doing it are all steeped in crypto, we all love to add in more crypto if we can possibly justify it. But the goal we drive for is the goal of an application and our solution is fundamentally measured on meeting that goal; Indeed, elegance is not found in sexy formulas, but in how little crypto is included to meet that goal, and how precisely it is placed.
The good news about FC7 is it is a darn sight more powerful than either the 'important' view, and a darn sight more interesting than the banking view. You can build anything this way - just start with an 'important' application (using Bob's term) and lay our your requirements. Then build down.
Try it - it's fun. There's nothing more satisfying than starting with a great financially motivated idea, and then building it down through the layers until you have a cohesive, end-to-end financial cryptography architecture. It's so much fun I really shouldn't share it!
February 02, 2005
Microsoft back in the currency game - Loyalty Points for using groupware
Regular FCers will know what this means: Microsoft Launches Loyalty Program For Live Meeting Meeting organizers can get prizes if they earn enough "frequent meeting miles."
By Messaging Pipeline Staff February 01, 2005 Messaging Pipeline
Microsoft has launched what may be the first loyalty marketing program for groupware applications. Live Meeting Rewards sets out to compensate frequent users of the company's premiere online meeting product with prizes they can redeem from a catalogue published at a special web site.
Meeting organizers are the target of this "frequent meeting miles" program, and they get various rewards for certain activities:
There is also a special 10,000 point reward program for new host users who register before March 31, 2005.
Meeting organizers can qualify into one of four different membership status levels -- Bronze, Silver, Gold, and Platinum, and their status level will determine how many points are earned for each Live Meeting session. Live Meeting Rewards members can redeem points for a folio of items, including prizes in the Rewards Catalog (not yet published), airline miles and charity donations.
For further information, or to sign up for Live Meeting Rewards, go to http://www.livemeetingrewards.com/login.m.
January 27, 2005
DIMACS Workshop on Information Markets
An interesting workshop on information markets (2-4 Feb) has enough of a nice description to lift and post. (Think BlogShares...) Sadly, registration is already closed - I wonder why this one hid its light under a bushel?
DIMACS workshop on information markets
February 2-4, 2005 DIMACS Center, Rutgers University, Piscataway, NJ
A market designed for information gathering and forecasting is called
an information market. Information markets can be used to elicit a
collective estimate of the expected value or probability of a random
variable, reflecting information dispersed across a population of
traders. The degree to which market forecasts approach optimality in
practice, or at least surpass other known methods of forecasting, is
remarkable. Supporting evidence can be found in empirical studies of
options markets, commodity futures markets, political stock markets,
sports betting markets, horse racing markets, market games, laboratory
investigations of experimental markets, and field tests. In nearly all
these cases, market prices reveal a reliable forecast about the likely
unfolding of future events, often beating expert opinions or polls.
Despite a growing theoretical and experimental literature, many
questions remain regarding how best to design, deploy, analyze, and
understand information markets, including both technical challenges
and social challenges.
This workshop will include talks on information markets by a number of
distinguished invited speakers. Speakers will cover a range of topics
including mechanism design, experiments, analysis, policy, and
industry experience. Speakers will include representatives from
academia, industry, and government. The workshop will feature research
talks, opinions, reports of industry experience, and discussion of
government policy from the perspective of a number of fields,
including economics, business, finance, computer science,
gambling/gaming, and policy. See the workshop program for more
details: http://dimacs.rutgers.edu/Workshops/Markets/program.html
The workshop will feature a tutorial session on Wednesday afternoon
(Feb. 2, 2005) to help those new to the field get up to speed. The
workshop will include a panel discussion on the Policy Analysis Market
(a.k.a., "Terror Futures") and a "rump" session where anyone who
requests time can have the floor for five minutes to speak on any
relevant topic. To participate in the rump session, please email David
Pennock: pennockd --AA@TT- yahoo-inc.com.
*********************************************************************
Workshop Program:
tentative schedule, subject to change
Wednesday, February 2, 2005
Tutorial Session I
12:00 - 1:30 Lunch and Registration - 4th Floor, Lounge, CoRE Building
Registration for the tutorial will be
limited to the first 60 registrations.
1:30 - 3:00 Information Markets I: Examples, Rules, History, Mechanics,
Studies, Participants, Ambiguity, Laws
Joyce Berg, Accounting, University of Iowa
3:00 - 3:30 break
Tutorial Session II
3:30 - 5:00 Information Markets II: Theory, Outputs, Inputs, Foul Play,
Combinatorics, Applications
Robin Hanson, Economics, George Mason University
Thursday, February 3, 2005
8:15 - 8:45 Registration and Breakfast - 4th Floor, Lounge, CoRE Building
8:45 - 9:00 Welcome and Opening Remarks
Fred Roberts, DIMACS Director and
David Pennock, Yahoo! Research Labs
Session: Policy, Politics, & Open Questions
9:00 - 9:30 Michael Gorham, Business, Illinois Institute of Technology
9:30 - 9:55 Robert Hahn, AEI-Brookings Institute
9:55 - 10:20 Information Markets and Politics
Adam Meirowitz, Politics, Princeton University and
Joshua Tucker, Public and International Affairs, Princeton University
10:20 - 10:45 Five open questions about prediction markets
Justin Wolfers, Business, University of Pennsylvania
10:45 - 11:15 break
Session: Experimental Economics
11:15 - 11:40 An Experimental Test of Combinatorial Information Markets
John Ledyard, Humanities and Social Sciences,
California Institute of Technology
11:40 - 12:05 Information markets and decision makers
Tony Kwasnica, Management Science, Pennsylvania State University
12:05 - 12:30 Information aggregation: Experiments and industrial applications
Kay-yut Chen, Hewlett Packard Labs
12:30 - 2:00 Lunch
Session: Business Models, Industry & Field Experience, Part I
2:00 - 2:15 Internal markets: Why and for who?
Carol Gebert, Incentive Markets
2:15 - 2:30 Tee Time with Admiral Poindexter
Todd Proebsting, Microsoft Research
2:30 - 2:45 Information markets as a platform for improved corporate communications
Steven Ostrover, EconOne
2:45 - 3:00 Challenges of Bringing Information Markets to the Organization
Ken Kittlitz, The Foresight Exchange
3:00 - 3:15 TBA
3:15 - 3:45 break
Session: Design and Implementation
3:45 - 4:10 Carsten Schmidt, Max Planck Institute
4:10 - 4:35 Expert identification via virtual stock markets: Finding
lead users in consumer product markets
Martin Spann, Business and Economics, Frankfurt University
4:35 - 5:00 Are prediction markets robust against manipulation? A lab experiment
Martin Strobel,Economics, Maastricht University
5:00 - 6:00 Rump session
I'm glad to see you've all discovered the Delphi method!
Murray Turoff, Information Systems, New Jersey Institute of Technology
Does money matter?
Emile-Servan Schrieber, Newsfutures
Auto-arbitrage in multi-outcome markets
Emile-Servan Schrieber, Newsfutures
7:30 - 9:00 Banquet - the Holiday Inn in South Plainfield
Friday, February 4, 2005
8:30 - 9:00 Registration and Breakfast - 4th Floor, Lounge, CoRE Building
Session: Economics, Finance, and Gambling
9:00 - 9:30 Leighton Vaughn Williams, Economics, Nottingham University
9:30 - 9:55 Manipulation in prediction markets: Evidence from historical
and contemporary election markets
Koleman Strumpf, Economics, University of North Carolina
9:55 - 10:20 Manipulators increase information market accuracy
Robin Hanson, Economics, George Mason University
10:20 - 10:45 Information aggregation and manipulation in an experimental market
Ryan Oprea, Economics, George Mason University
Session: Iowa Electronic Market
11:15 - 11:40 George Neumann, Economics, University of Iowa
11:40 - 12:05 Public signal bias and prediction market accuracy
Thomas Gruca, Marketing, University of Iowa
12:05 - 12:30 Searching for Google's value: Using prediction markets
to forecast market capitalization prior to an IPO
Thomas Rietz, Finance, University of Iowa
12:30 - 2:00 Lunch
Session: Business Models, Industry & Field Experience, Part II
2:00 - 2:15 HedgeStreet: An introduction
Russell Andersson, Hedgestreet.com
2:15 - 2:30 Emile Servan-Schreiber, Newsfutures
2:30 - 2:45 Chris Hibbert, CommerceNet
2:45 - 3:00 Emphasizing the mundane: Making a business of information markets
Charles Polk, Common Knowledge Markets
3:00 - 3:15 TBA
Session: Computation
3:45 - 4:10 Computational complexity issues in information markets
Lance Fortnow, Computer Science, University of Chicago
4:10 - 4:35 Michael Wellman, Computer Science, University of Michigan
4:35 - 5:00 A dynamic pari-mutuel market for hedging, wagering,
and information aggregation
David Pennock, Yahoo! Research Labs
5:00 - 6:00 Post-mortem panel discussion on the Policy Analysis Market
(a.k.a., "Terror Futures")
Robin Hanson, Economics, George Mason University
John Ledyard, Humanities and Social Sciences,
California Institute of Technology
Charles Polk, Common Knowledge Markets
January 26, 2005
Poll predicts Instant Messaging to take over
In one piece of news, BlowSearch, an offerer of secured IM, gives "gold" users 4096-bit encryption, "silver" users 256-bit encryption and bronze users 56-bit encryption. That's comforting to know! (I couldn't find their URL so I guess we just have to feel safer now.) And in other news, rumour of Google's chat client, built around sharing photos! Finally, getting to the point, a Poll portends an IM takeover in the next few years:
Will Instant Messaging Take Over?
Sage Research and Messaging Pipeline both asked if instant messaging would become more important than e-mail for enterprise messaging. And the answer is . . .
By John Dickinson
Messaging Pipeline January 25, 2005
In Sage Research's latest "Market Pulse" which was published today, the company reported that 51% of its respondents believed that instant messaging will surpass e-mail as the preferred form of business communications within their organization. Another 41% did not think it would happen, and the rest had no opinion.
A recent Messaging Pipeline poll had similar results, with 51% believing that IM would become more important than e-mail, and 49% thinking that it would not. Both polls had about the same number of respondents and the question was formed in a similar fashion.
Sage's poll went a little deeper by asking respondents to speculate about the timeframe of such a switchover. Most, 23%, respondents who thought that IM would dominate thought it would happen within three years, while 12% thought it might happen in their organizations this year.
The jury is out, and you have to wonder if it isn't all about personal preferences rather than practical business and technology issues. In any case, it's an interesting set of trends, and well worth keeping an eye on.
For more information visit www.sageresearch.com.
http://www.sageresearch.com/
January 23, 2005
BlogShares - fantasy trading in blogs and ideas
Information, and it's alternate, information overload, is the currency of our generation. Hayek's stunning observation that prices are the messages of needs and desires in our economy, and Mises calculation argument - that the humans are the computers, and they work better (only?) when distributed - are the bedrocks of our Internet economy. Yet the flood of Hayekian messages leads simply to an overload on my poor old Misean brain, so much so that I wish his calculation argument didn't signal the death knell of centralised thought processes. I need someone to tell me what to do!
In the last 5 years, we've seen several emerging technologies that have worked with information in new ways. They are - check my enumeration here - Blogs, p2p, community currencies, reputational auctions. I might have missed a few, but here's my point: all of these promise great things, but like Napster, isolated they fail.
Here's a great example of a tech that has successfully integrated several emerging paradigms. Blogshares is a market place for fantasy trading of blogs-as-companies. (Check off blogs, community currencies, and reputational auctions!) More than that, it has an ideas market in it . (Check off reputational auctions, again!) It lacks peer to peer, but there's only so much you can do, and I rate 3 out of 4 pretty highly.
Check it out, unless you are busy. The site is clunky, slow, and difficult to navigate, which is unfair in the context of only 2 guys working on it, but fair in terms of your time. When all those things are sorted out, I suspect it will bloom.
If you have a blog then you may want to dive in there, create an account, and claim your blog. If only because you want to vote it into useful categories. I don't fully recommend this as yet, because it takes a while to sort out, and it seems to matter not if others vote you in. Also, the categories are a single hierarchical tree, which went out with the Dewey Decimal System.
For example, FC is impossible to categorise, simply because by definition, it's cross leaf and broad, not deep and sectoral. Currently, it's been incarcerated in Economics. (More dismal yet, they are currently working on a system to penalise broad voting :-/ )
Here's my hard description: BlogShares is a fantasy stock market and ideas market where weblogs are the companies. Players invest fictional dollars on shares in blogs. Blogs are valued by their incoming links and add value to other blogs by linking to them. Prices can go up or down based on trading and the underlying value of the blog. Players can vote 'industry' sectors on blogs, and establish Ideas. The combination of fantasy trading, ideas market and corporate currencies makes this idea a winner, although the site is still clunky and hard to learn.
January 19, 2005
Online or Invisible - the case for open publication
Adam has pointed me to a paper on citation rates for open work: "Online or Invisible" by Steve Lawrence. In brief, it suggests that if ones work is openly available on the web, it is cited 3-4 as many times in others' work.
It has been blindingly obvious for a decade now that the letters 'WWW' signalled the end of the academic publishing industry. The latter's only value added was their ability to get the words distributed, for which they charged a fee. Well, WWW does that for free.
But there are still lots of holdouts. Academic conferences still walk the party line and want sign-over of copyrights. Their logic runs thusly; in order to attract academics they have to show a formal academic proceedings which distributes their work. The proceedings publisher requires to own the copyright so as to benefit from reprints and subsidise the costly distribution of the books.
But this was a confusion of means with ends. The end required is the distribution of the work, not the attraction of a well reputed journal. That's only the preferred means in a pre-WWW world. Now, as I say, this should have been blindingly obvious, but it wasn't and is perhaps the best evidence of scientists not understanding basic economics and marketing processes. We now have some scientific evidence that using a 'reputable scientific journal' will reduce the distribution of the work. Of course, the paper, published by Nature, is available online.
What's this to do with FC? A lot; by analogy, the same story is being told by the DRM school - music and films. Slightly different calculations but the same bases in economics. Just much more money and dollops of politics, law and crypto.
January 09, 2005
Identity Theft: Why Hollywood has to take one for the team.
The Year of the Phish has passed us by, and we can relax in our new life swimming in fear of the net. Everyone now knows about the threats, even the users, but what they don't know is what happens next. My call: it's likely to get a lot worse before it gets better. And how it gets better is not going to be life as we knew it. But more on that later.
First... The Good News. There is some cold comfort for those not American. A recent report had British phishing loses under the millions. Most of the rich pickings are 'over there' where credit rules, and identity says 'ok'. And even there, the news could be construed as mildly positive for those in need of good cheer. A judge recently ruled a billion dollar payout against spammers who are identified in name, if not in face. We might never see their faces, but at least it feels good. AOL reported spam down by 75% but didn't say how they did it.
Also, news that Microsoft is to charge extra for security must make us believe they have found the magic pixie dust of security, and can now deliver an OS that's really, truly secure, this time! Either that, or they've cracked the conundrum of how to avoid the liability when the masses revolt and launch the class action suit of the century.
All this we could deal with, I guess, in time, if we could as an industry get out collective cryptographic act together and push the security models over to protecting users (one month's coding in Mozilla should do it, but oh, what a long month it's been!). But there is another problem looming, and it's ...
The Bad News: the politicians are now champing at the bit, looking for yet another reason to whip today's hobby horse of 'identify everyone' along into more lather. Yes, we can all mangle metaphors, just as easily as we can mangle security models. Let me explain.
The current project to identify the humanity of the world will make identity theft the crime of the century. It's really extraordinarily simple. The more everything rests on Identity, the more value will Identity have. And the more value it has, the more it will be worth to steal.
To get a handle on why it is more valuable, put yourself in the shoes of an identity thief. Imagine our phisher is three years old, and has a sweet tooth for data.
How much sugar can there be found in a thousand cooperating databases? Each database perfectly indexed with your one true number and bubbling over with personal details, financial details, searchable on demand. A regulatory regime that creates shared access to a thousand agencies, and that's before they start sharing with other countries?
To me, it sounds like the musical scene in the sweets factory of Chitty Chitty Bang Bang, where the over indulgent whistle of our one true identity becomes our security and dentistry nightmare. When the balance is upset, pandemonium ensues. (I'm thinking here the Year of the Dogs, and if you've seen the movie you will understand!)
Now, one could ask our politicians to stop it, and at once. But it's too late for that, they have the bits of digital identity between their teeth, and they are going to do it to us to save us from phishing! So we may as well be resigned to the fact that there will be a thousand interlinked identity databases, and a 100 times that number of people who have the ability to browse, manipulate, package, steal and sell that data. (This post is already too long, so I'm going to skip the naivete of asking the politicians to secure our identity, ok? )
A world like that means credit will come tumbling down, as we know it. Once you know everything about a person, you are that person, and no amount of digital hardware tokens or special biometric blah blahs will save the individual from being abused. So what do people do when their data becomes a phisher's candyfest?
People will withdraw from the credit system and move back to cash.This will cost them, but they will do it if they can. Further, it means that net commerce will develop more along the lines of cash trading than credit trading. In ecommerce terms, you might know this better as prepaid payment systems, but there are a variety of ways of doing it.
But the problem with all this is that a cash transaction has no relationship to any other event. It's only just tractable for one transaction: experienced FCers know that wrapping a true cash payment into a transaction when you have no relationship to fall back to in event of a hiccup is quite a serious challenge.
So we need a way to relate transactions, without infecting that way with human identity. Enter the nym, or more fully known as the psuedonymous identifier. This little thing can relate a bunch of things together without needing any special support.
We already use them extensively in email, and in chat. There are nyms like iang which are short and rather tricky to use because there are more than one of us. We can turn it into an email address, and that allows you to send a message to me using one global system, email. But spam has taught us a lesson with the email address, by wiping out the ease and reliability of the email nym ... leading to hotmail and the throw away address (for both offense and defense) and now the private email system.
Email has other problems (I predict it is dying!) which takes us to Instant Messaging (or chat or IM). The arisal of the peer-to-peer (p2p) world has taken nyms to the next level: disposable, and evolutionary.
This much we already know. P2P is the buzzword of the last 5 years. It's where the development of user activity is taking place. (When was the last time you saw an innovation in email? In browsing?)
Walking backwards ... p2p is developing the nym. And the nym is critical for creating the transactional framework for ecommerce. Which is getting beaten up badly by phishing, and there's an enveloping pincer movement developing in the strong human identity world.
But - and here's the clanger - when and as the nymous and cash based community develop and overcome their little difficulties, those aforementioned forces of darkness are going to turn on it with a vengeance. For different reasons, to be sure. For obvious example, the phishers are going to attack looking for that lovely cash. They are going to get rather rabid rather quickly when they work out what the pickings are.
Which means the mother of all security battles is looming for p2p. And unfortunately, it's one that we have to win, as otherwise, the ecommerce thing that they promised us in the late nineties is looking like a bit more like those fairy tales that don't have a happy ending. (Credit's going to be squeezed, remember.)
The good news is that I don't see why it can't be won. The great thing about p2p is the failure of standards. We aren't going to get bogged down by some dodgy 80's security model pulled out of the back pages of a superman comic, like those Mr Universe he-man kits that the guy with the funny name sold. No, this time, when the security model goes down in flames (several already have) we can simply crawl out of the wreckage, dust off and go find another fighter to fly into battle.
Let's reel off those battles already fought and won and lost. Napster, Kazaa, MNet, Skype, BitTorrent. There are a bunch more, I know, I just don't follow them that closely. Exeem this week, maybe I do follow them?
They've had some bad bustups, and they've had some victories, and for those in the systems world, and the security world, the progress is quite encouraging. Nothing looks insurmoutable, especially if you've seen the landscape and can see the integration possibilities.
But - and finally we are getting to the BIG BUT - that means whoever these guys are defeating ... is losing! Who is it? Well, it's the music industry. And hollywood.
And here's where it all comes together: ecommerce is going to face a devastating mix of over rich identity and over rich phishers. It'll shift to cash based and nym based, on the back of p2p. But that will shift the battle royale into p2p space, which means the current skirmishes are ... practice runs.
And now we can see why Hollywood is in such a desperate position. If the current battle doesn't see Hollywood go down for the count, that means we are in a world of pain: a troubling future for communication, a poor future for ecommerce, and a pretty stark world for the net. It means we can't beat the phisher.
Which explains why Hollywood and the RIAA have found it so difficult to get support on their fight: everyone who is familiar with Internet security has watched and cheered, not because they like to see someone robbed, but because they know this fight is the future of security.
I like Hollywood films. I've even bought a few kilograms of them. But the notion of losing my identity, losing my ability to trade and losing my ability to communcate securely with the many partners and friends I have over the net fills me with trepidation. I and much of the academic and security world can see the larger picture, even if we can't enunciate it clearly. I'd gladly give up another 10 years of blockbusters if I can trade with safety.
On the scales of Internet security, we have ecommerce on one side and Hollywood on the other. Sorry, guys, you get to take one for the team!
Addendum: I've just stumbled on a similar essay that was written 3 weeks before mine: The RIAA Succeeds Where the Cypherpunks Failed by Clay Shirky.
December 16, 2004
Email is dying ... Stats from Postini
Whenever I see more evidence that Email is dying, the John Lennon refrain of "War is over" pops into my head. There must be some art in this. Anyway, here's two pieces of evidence: you will get this email TWICE - I'm sorry about that, let me know if you want unsubscribed, but MT for some reason has decided to double send the emails.
The second piece of evidence is more supporting of the thesis that email is dying. Postini, a mail applications and spam filter provider company, has released some stats on the year according to spam. The headlines: last year (2003) 22% of emails were legitimate. This year that number is down to 12%, and next year, 2005, Postini predicts that only 8% of emails will be legit.
For me the number is more like 5%, so I'd be happy with that :) But, joking aside, it lends credence to the notion that email is becoming more expensive than it is worth. Young people already have ditched it, and older people are also learning the joys of phones, chat, blogs and other ways to stay in touch. Which is good, as email has proven to be an archaic tool over which to do business. FC applications much prefer chat and phones. So say I, at least.
Oh, and Postini also said that virus-infected mails have exploded: 2003 had an average of one in 200, and towards the end of this year they saw 1 in 25! Hard numbers for those who think this is a passing phase.
"Email is dying ... War is over ..." I wish I knew what song that was.
http://www.prnewswire.com/cgi-bin/stories.pl?ACCT=104&STORY=/www/story/12-15-2004/0002634215&EDATE=
Addendum, further evidence from Fm is this Korean article on the new generation not using email.
JP spotted this this article. If you can ignore the American superiority complex (common in popularist american writings), it includes some good stuff about how the blogs are spreading into areas desperate for communication.
December 08, 2004
2006, and beyond...
Over at EmergentChaos, Adam asked what happens when "the Snail" gets 10x worse? I need several cups of coffee to work that one out! My first impressions were that ... well, it gets worse, dunnit! which is just an excuse for not thinking about the question.
OK, so gallons of coffee and a week later, what is the natural break on the shift in the security marketplace? This is a systems theory (or "systemics" as it is known) question. Hereafter follows a rant on where it might go.
(Unfortunately, it's a bit shambolic. Sorry about that.)
A lot of ordinary users (right now) are investigating ways to limit their involvement with Windows due to repeated disasters with their PCs. This is the the first limiting factor on the damage: as people stop using PCs on a casual basis, they switch to using them on a "must use" basis.
(Downloading Firefox is the easy fix and I'll say no more about it.) Some of those - retail users - will switch to Macs, and we can guess that Mac might well double its market share over the next couple of years. A lot of others - development users and poorer/developing countries - will switch to the open source Unix alternates like Linux/BSD. So those guys will have a few good years of steady growth too.
Microsoft will withdraw from the weaker marketplaces. So we have already seen them pull out of supporting older versions, and we will see them back off from trying to fight Firefox too hard (they can always win that back later on). But it will maintain its core. It will fight tooth and nail to protect two things: the Office products, and the basic windows platform.
To do that, the bottom line is that they probably need to rewrite large chunks of their stuff. Hence the need to withdraw from marginal areas in order to concentrate on protecting that which is core, so as to concentrate efforts. So we'll see a period characterised by no growth or negative growth by Microsoft, during which the alternates will reach a stable significant percentage. But, Microsoft will come back, and this time with a more secure platform. My guess is that it will take them 2 years, but that's because everything of that size takes that long.
(Note that this negative market growth will be accompanied by an increase in revenues for Microsoft as companies are forced to upgrade to the latest releases in order to maintain some semblance of security. This is the perversity known as the cash cow: as the life cycle ends, the cash goes up.)
I'd go out on a limb here and predict that in 2 years, Microsoft will still control about half of the desk top market, down from about 90% today.
There are alternates outside the "PC" mold. More people will move to PDAs/cellular/mobile phones for smaller apps like contact and communications. Pushing this move also is the effect we've all wondered about for a decade now: spam. As spam grows and grows, email becomes worse and worse. Already there is a generation of Internet users that simply do not use email: the teenagers. They are chat users and phone users.
It's no longer the grannies who don't use email, it is now the middle aged tech groupies (us) who are feeling more and more isolated. Email is dying. Or, at least, it is going the way of the telegram, that slow clunky way in which we send rare messages like birthday, wedding and funderal notices. People who sell email-based product rarely agree with this, but I see it on every wall that has writing on it [1] [2].
But, I hear you say, chat and phones are also subject to all of the same attacks that are going to do Microsoft and the Internet so much damage! Yes, it's true, they are subject to those attacks, but they are not going to be damaged in the same way. There are two reasons for this.
Chat users are much much more comfortable with many many identities. In the world of instant messaging, Nyms are king and queen and all the other members of the royal family at the same time. The same goes for the mobile phone world; there has been a seismic shift in that world over to prepaid billing, which also means that an identity that is duff or a phone that is duff can simply be disposed of, and a new one set up. Some people I know go through phones and SIMs on a monthly basis.
Further, unlike email, there are multiple competing systems for both the phone platform and the IM platform, so we have a competition of technologies. We never had that in email, because we had one standard and nobody really cared to compete; but this time, as hackers hit, different technologies can experiment with different solutions to the cracks in different ways. The one that wins will attract a few percentage points of market share until the solution is copied. So the result of this is that the much lauded standardisation of email and the lack of competition in its basic technical operability is one of the things that will eventually kill it off.
In summary so far; email is dying, chat is king, queen, and anyone you want to be, and your mobile/cellular is your pre-paid primary communications and management device.
What else? Well, those who want email will have to pay *more* for it, because they will be the shrinking few who consume all the bandwidth with their spam. Also, the p2p space will save us from the identity crisis by inventing the next wave of commerce based on the nym. Which means that we can write off the Hollywood block buster for now.
Shambolic, isn't it!
[1] "Scammers Exploit DomainKeys Anti-phishing Weapon"
http://story.news.yahoo.com/news?tmpl=story2&u=/zd/20041129/tc_zd/139951
[2] "Will 2005 be the year of the unanswered e-mail message?"
http://www.iht.com/bin/print_ipub.php?file=/articles/2004/12/06/business/netfraud.html
October 24, 2004
Online gaming? How about online trading...
Gaming prodigy Jules Urbach has created a platform for instant-message-based video games and other applications that he plans to offer free to hobbyist developers and others. Urbach says the Otoy game engine is the key to leveraging instant messaging for a multitude of purposes, including huge multiplayer games that are free. "What I've always been most interested in is the idea of a virtual community, and AOL had the first chat room and IM," he says of his admiration for America Online's sometimes derided approach to the Internet. Urbach is a co-founder of video game firm Groove Alliance, which makes low-memory, online 3D games for clients such as Nickelodeon, Disney, Shockwave, and Electronic Arts; he is currently designing a Star Trek-like game for the Otoy platform that will be run in a window linked to the users' instant-messaging application, so that numerous players can be involved in the game simultaneously and use a separate window to chat with each other. Urbach says his Otoy games are highly componentized and could provide fertile ground for advertisers who could, for example, paste clickable billboards on virtual spaceships: "Each piece in a game can be a separate, encrypted stream," Urbach notes. Otoy will be made available as a free download next year, and Urbach hopes individual developers will use it to create applications that pull up Web browsers, MP3 files, Excel spreadsheets, or whatever other applications they can cook up. Urbach developed Hell Cab, one of the first CD-ROM games that became a best seller in 1992, and created the first 3D video game using Macromedia Director software.
FOR the past year, Jules Urbach has been crunching computer code in a converted bedroom on the second floor of his mother's house in Sherman Oaks, Calif., fine-tuning a piece of software that may well revolutionize online gaming. Mr. Urbach, whose words come in a caffeinated rush, is so excited about introducing his invention on the Web that he never stops working on it; his fingers dance across his Dell keyboard even as he delivers a frantic verbal sales pitch.
"I mean, there's really no telling what's going to happen with this thing," said the 30-year-old video-game designer. "Who knows what developers are going to do when they see this?"
Mr. Urbach hopes they will be inspired to irrevocably change the online gaming landscape. His invention, which he calls Otoy, is a game engine that piggybacks on instant messaging, and thus it is something of a Holy Grail in the software world. For years, developers have been trying to figure out ways to turn instant messaging into a multipronged medium that goes beyond mere chat to integrate games, e-mail and Web browsing; in the gloaming of a guest bedroom, Mr. Urbach believes he may well have come up with the skeleton key that will open IM to an era of hyper-functionality.
"I think a lot of people are going to be blown away by this," said Clay Sparks, a character designer and movie miniature artist ("The League of Extraordinary Gentlemen") who has designed games for Mr. Urbach's company, Groove Alliance.
Mr. Urbach is a video game prodigy. In 1992, shortly after graduating from Harvard-Westlake School in Los Angeles, he created one of the first CD-ROM games (the best-selling Hell Cab), then became the first developer to design a 3-D video game (Real Pool, www.shockwave.com) using Macromedia Director software, a feat that even Macromedia's executives had thought was impossible.
In 1998, Mr. Urbach founded Groove Alliance with Chris Kantrowitz and Peter Laufenberg. Groove was one of the first game companies that created 3-D products exclusively for online use, churning out dozens of titles for Nickelodeon, Disney, Shockwave and Electronic Arts, among others, and providing a healthy living for Mr. Urbach, who now pays the mortgage on his mother's house.
Yet despite his success, he was restless. He suspected that there was some unexplored online games frontier, and he wanted to get there first. Instant-messaging services already offered primitive elemental games like tic-tac-toe, but Mr. Urbach wanted to integrate his 3-D games into IM, which he believed could help spread them more widely. "I wanted multiplayer games to be available to everyone, and I wanted it to be free," Mr. Urbach said.
Mr. Urbach's inspiration for Otoy came from a unlikely source: America Online. AOL is regarded by many as an online dinosaur, but Mr. Urbach, who has maintained his original AOL account since the early 90's, is one of its fans.
"What I've always been most interested in is the idea of a virtual community, and AOL had the first chat room and IM," he said. "I love picking a character and going into a room and leading a virtual life. I love everything about AOL, actually."
Mr. Urbach is a populist; he wants his games to be played by casual gamers - thousands of them playing against one another, if all goes according to plan - and not necessarily the hard-core addicts who spend countless hours on pay-for-play online games. "I look at something like Everquest, which is very complex and very addictive, and I see that working for simpler games as well," Mr. Urbach said. "That desire to be part of a larger community is just part of human nature."
To that end, Mr. Urbach has figured out how to use compelling low-memory games, many of them Groove games that occupy less than 70 kilobytes of memory, for Otoy. Users will see a link in their instant-messaging windows that will open a second window, adjacent and slightly larger. This is Mr. Urbach's versatile Otoy IM portal.
Click on a game link and the window reveals a constellation of stars and spaceships operated by individual players, or a prehistoric tableau with treasure-seeking dinosaurs. A chat room window can be overlaid on the games so that players can converse as they play.
Each component in a game designed for Otoy can be added or eliminated by the players with a few simple command lines. "I can componentize everything," Mr. Urbach said. "Each piece in a game can be a separate, encrypted stream." Mr. Urbach hopes this feature will be manna for advertisers, who can paste a billboard on a spaceship as a hot link, and then have players send the ship virally - when gamers send a ship to other players, the ad will be imbedded on the ship - to thousands of other players, who can then click on the link to reach the advertiser's Web site.
Otoy, which Mr. Urbach plans to make available next year for free downloading, can also be used to pull up Web browsers, MP3 files or Excel spreadsheets, depending on the programmer's intent. Mr. Urbach also has Photoshop built into Otoy.
He is not certain how all of this is going to come together. Like a mad scientist unsure of what he has wrought, he is leaving that to the armchair developers and open-source programmers who he hopes will tap into Otoy's seemingly limitless potential. The code language for Otoy is streamlined and easily comprehensible - a kind of Esperanto script that Mr. Urbach hopes will spur innovation from unlikely sources.
As for Mr. Urbach's own content for Otoy, he is working on a potential Star Trek project. "I wish I had this technology when I was 17," he said. "This is just a fulfillment of a desire to do things like this when I was a kid."
July 02, 2004
GoldMoney challenges for pole position
Goldmoney's newly released bar count shows, as predicted, that it has now overtaken e-gold as the largest issuer of gold currency. Last quarter growth was 42%, and as e-gold have been flat or declining for many years now, goldmoney's future leadership is a near certainty. Congratulations!
However, this only applies to grams of gold - arguably the most important measure but not the full story. If e-gold's silver, platinum and palladium is taken into account, e-gold is still slightly larger (calculate on Examiner). Swapping white metals into gold (via USD) gives e-gold a total basket of 1,813,748.30, slightly larger than goldmoney's 1,783,552.182gg.
Until the next 3 bars goes in, that is. Unfortunately, as goldmoney only releases its figures every quarter, we won't know for another three months, and until then, goldmoney can't report that they are the biggest.
Damn those auditors, curse them! If only there was a solution to this....
-------- Original Message --------
Subject: [dgc.chat] new bar count
Date: Fri, 02 Jul 2004 13:11:10 -0400
From: James Turk
The 30 Jun 2004 quarterly stats for GoldMoney have been posted today at
http://goldmoney.com/en/report.html
There are now 1,783,552.182gg in circulation, representing 142 LBMA good delivery bars.
http://goldmoney.com/en/bar-count.html
That's an increase of 42 bars from the 100 bars in GoldMoney as of 31 Mar 04, or 42% growth for the quarter.
Importantly, the total grams of gold reported by VIA MAT (gold in the vault) and total goldgrams reported by Dimension Data (digital gold currency in the database) are identical, again confirming that GoldMoney is 100% gold, always.
Regards
James
subscribe: send blank email to dgcchat-join@lists.goldmoney.com
unsubscribe: send blank email to dgcchat-leave@lists.goldmoney.com
digest: send an email to dgcchat-request@lists.goldmoney.com
with "set yourname@yourdomain.com digest=on" in the message body
June 28, 2004
P2P's Tragedy of the Commons
Nightblade [1], a coder on p2p netrworks, wrote about the "tragedy of the commons" and how it tended to destroy systems. His words were too dangerous, as now the site is down. I've scraped the google cache, below [2].
Tragedy of the Commons is something we've all known about [3]. I recall Bob H going on about it all the time. The solution is simple - property where there is scarcity. Unfortunately, property requires rights allocation, and payments, and methods of exchange.
Now, we've built all these things, but those building the p2p systems have not. Instead of going that distance - admittedly way beyond the expectation - comments in reply to his problem description (unpreserved) have stressed that there is a social element to this and if only the right social engineering approach can be found, it will all work. Which of course will not work, but it's a timely reminder of the sort of soft social thnking that has spread from the legacy of GPL.
Then, in our world, we've built the superlative rights allocation mechanisms. We've created strong payment systems (the field is littered with these), and we've done the exchange mechanisms. I've seen these things in operation, and when they are humming, the world moves dangerously quicker. Yet our application side has never carried it far enough.
So we have two worlds. One world knows how to build p2p. The other world knows how to solve the resource allocation problem. The question is, when do the worlds start colliding?
This was the central message of FC7 [4]: Don't underestimate the complexity of the words. It is a multidisciplinary problem, which means there is a huge need to reach across to the other disciplines (I identified 7 core areas, and that's a lot to deal with. In brief, p2p chat would be a layer 7 application, and the above rights, payments, exchange are all layers 1 through 6.)
But FC7 was widely ignored, and in my discussions on many (other) issues, I've come to the conclusion that we as a species don't like multidisciplinary concepts. We want the whole solution to live in our space of expertise. We get all woolly and nervous when we're asked to dwell into unfamiliar territory, as seen by the desire to cast the tragedy of the commons into the familiar "social" context of the GPL crowd.
Our Internet Commons of Ideas and Potential Applications seems hardly in danger of over-grazing. More, we have a group of deaf dumb and blind developers sitting at the edge of the commons, occasionally falling over dead from starvation, while in the middle there is good grazing.
[1] Nightblade - dead link:
http://www.i2p.net/user/view/13?PHPSESSID=077353367d123d3309d79f4837895bee
[2] Google cache
http://216.239.59.104/search?q=cache:5T_lYTAG1HIJ:www.i2p.net/node/view/215+I2P+P2P+IIP+chat&hl=en&ie=UTF-8
[3] Tragedy of the commons
http://en.wikipedia.org/wiki/Tragedy_of_the_commons
[4] Financial Cryptography in 7 layers
http://iang.org/papers/fc7.html
Why P2P Networks Fail
Submitted by Nightblade on May 16, 2004 - 19:35.
This is something I have been thinking about for a long time. I believe it is one the main reasons P2P networks fail. (Another related theory is called the "prisoner's dilemma")
Here is an example from my own experiences:
A long time ago, I had a freesite on Freenet. Initially I was able to insert the site with no difficulty. However, as the network conditions grew worse over the weeks and months I found it more and more difficult to insert new editions of my site.
When I had inserted the first editions of my site, I used HTL values like 10 to 13 and only inserted the site once. I figured that would be enough to make it so people could see it, and they could. However as the network degraded I had to increase my HTL value to the maximum of 25, and perform multiple inserts over several hours before my site became viewable to other Freenet users. Part of this was prompted by Freenet coding bugs, but I think part of it was also caused by "overcrowding" - too much data was being inserted, causing sites to be lost too quickly as Freenet became more popular.
At the same time, I imagine other freesite authors were doing the exact same thing as I was, increasing their HTL and doing multiple inserts, possibly from multiple locations. While in the short term this solved the problem, it eventually turned into an "arms race." I remember just before I gave up on Freenet I was spending the entire day - 12 hours or more - continually ramming my site into the network with FIW, hoping it would work!
In addition to this madness there was Frost, which was a very heavy user (some would say abuser) of Freenet network resources. The end result was that the "commons" of Freenet - bandwidth and data stores, were overused and became nonfunctional.
Lest someone say that such problems in Freenet were caused by Freenet itself (i.e. bugs) rather than commons-overuse, let me give another example.
Take for instance Gnutella. At one time I shared about half my hard drive on Gnutella, but over the months and years I used Gnutella I got pissed off at all the "freeloaders" (people who download but don't share much), and I started reducing the number of files I shared. Other Gnutella users have done the same thing as I did. Now when I go on to Gnutella (or any other popular file sharing network) I find it very difficult to find anyone sharing files. Nobody shares anymore, they just leech. This is because the "commons" - bandwidth - was "overgrazed" by a few people, and those who were sharing stopped and began to leech instead, thus destroying the commons of Gnutella.
I also see this same problem potentially occuring in I2P.
At the moment, everyone is friendly and does not overuse the commons (bandwidth), but what will happen when I2P becomes more popular? Those without such altruistic behaviour as ourselves will begin wasting valuable I2P bandwidth.
Define "waste", you say? Suppose I develop a filesharing application which runs on I2P. People use my application to pirate the latest software, for example, Microsoft Office. Suddenly I2P becomes painfully slow. What do we do? We do not know which tunnels carry pirated software, because they are encrypted and anonymous. We can only sit and hope for the software pirates to become bored and go somewhere else.
Perhaps you do not find software piracy a wasteful activity.... then instead consider a government agency which creates multiple I2P routers and sends millions of gigabytes of garbage data across the network (WAV files of white noise, for example). That would have the same effect as the pirates would.
What is the solution to the "Tragedy of the Commons Attack?" This is what I have been thinking about, and so far I have come up with some solutions - private members-only networks in the style of WASTE seem to be the most promising.
What do you think?
June 22, 2004
Semblance of order amid the chaos
Finally, some good news amid the scandals and disasters... The Banker reports that the Bank of England led a project to put in place a new payment system into Iraq [1]. Two companies, Visa and E-Go, were selected by the Old Lady to put in place a network of 80 laptops and Inmarsat satellite linkups. On the laptops were Visa's software, although details are scant as to how that works.
The Bank of England continues to impress in the lacklustre world of central banking.
Semblance of order amid the chaos
Published on: 03 May, 2004
The exchange desk for the new Iraqi currency at a branch of Rafidain Bank
An improbable mix of coincidence, personal ingenuity and innovative technology gave Iraq a sorely needed payments system.
Stabilising the political environment in post-war Iraq is one issue; rebuilding its wrecked financial infrastructure is quite another. Amid the carnage and devastation, a little known tale of extraordinary innovation and ingenuity has defied the logic of logistics and produced a payments system for Iraq which may have provided, in its own way, more stability for the country than much of the military hardware.
In July last year, the embattled Central Bank of Iraq produced an ambitious goal but with little idea how it could be achieved. On October 15 the launch of the new Iraqi dinar (without Saddam Hussein on the note) was planned. Getting the notes printed abroad was not the problem - De La Rue obliged. But to enable the re-emergence of Iraq as a self-supporting economy, a secure currency and trading backbone was essential and far from easy to implement.
Impossible task
With no telecommunications infrastructure, nor a reliable power grid, the Iraqi banks were looking for a solution which would provide them with the ability, reliability and security to network their banks' branches country-wide. A network of 80 sites throughout the country was required. And this was before personal security, attacks and all military aspects were considered.
Solution emerges
The Central Bank of Iraq called on the Bank of England for help last July and through an extraordinary series of coincidences, personal initiatives and creative use of technology, a solution emerged.
Key to putting together the initial core network package was Kathleen Tyson-Quah, who had broad global experience in developing banking systems and who acted as 'solution architect' for the project. Given the unique nature of the Iraqi situation and the extremely tight October deadline, traditional approaches were not possible. A project that could take years under normal conditions was desperately needed in less than three months, and conditions in Iraq were far from normal.
Ms Tyson-Quah needed providers who not only could do the job but were already active in the area; there was no time to acclimatise. Post-war Iraq had no countrywide commercial communications network. What telecoms and IT systems existed had not been updated for years, and relied on DOS-based systems. It was clear that a major technology gap existed. "With the 10-week deadline many people thought I was insane," she noted, but some were willing to rise to the challenge.
In July 2003, a tender from Iraq's three leading banks was issued for a new infrastructure and payments system, and 16 companies responded. In August, in Baghdad, the order was signed for Visa International and E-Go Solutions, a partnership between NSSL and TET Satellite Solutions, to deliver the system.
Technology
Visa International and E-Go proposed a network solution based on the regional BGAN system operating via Inmarsat. Each of the 80 bank branches would need nothing more than a safe with cash, a dual language laptop carrying applications based on VISA software and a regional BGAN satellite modem to run operations. High-integrity customised security was built into both hardware and software, as well as over the network via VPN. The UK-based server supplied and maintained by E-Go offered full redundancy, using Cisco and HP systems with uninterrupted power supplies and tape back-up.
Against all odds, the 80-laptop system was up on time and its benefits are now beginning to be felt. Visa's Stuart Brocklehurst, who played a critical role in pulling the project together, says: "The ability to transfer wages and payments electronically gives the banks greater control and security. As more people gain confidence in the banks as a safe place to leave their money, they will be able to save. As a result more money stored in the banks will give the institutions the opportunity to lend money, thus allowing the Iraqi economy to grow more quickly." Since March, Mr Brocklehurst adds, most banks, including the 19 private banks, have come onstream with the payments system.
The new network ensured the smooth introduction of the new currency. The VisaNet/E-Go solution provides not only a viable system for Iraq but also a model for other countries with complicated payments needs.
June 18, 2004
U.S. banks fail to attract immigrant remittance business
As I've frequently observed, the worst companies to encourage into new money businesses are banks. Frank Trotter, now the Chairman of the highly successful Internet bank, Everbank, once famously observed that the companies best placed to enter the new money business were mass transits, telcos and couriers. I think he was dead right; and he's been proven correct, 2 out of 3 so far.
Here's a report about banks failing to get into the remittances business. The reasons should be fairly easy to spot, so I'll not bore with yet another list of critical factors.
U.S. banks fail to attract immigrant remittance business
Eduardo Porter NYT
Tuesday, June 08, 2004
The entry of big U.S. banks into the business of handling immigrants' remittances of money back home was expected three years ago to produce a financial revolution with potentially powerful policy implications for the United States and Latin America.
So far, the revolution does not seem to have panned out.
According to a report that was set for release on Monday by the Pew Hispanic Center, a nonprofit research group, banks have captured only a trifling share of the money flow. And the price of remitting money - which fell sharply in the late 1990s - has leveled off.
For the 10 million Latin American immigrants in the United States who last year sent $30 billion to their families back home, linked bank accounts and international cash-machine networks offer a cheaper way to send money than using traditional cash-based services like Western Union, a subsidiary of First Data, and Moneygram, which is owned by Viad. Through remittance services, banks also hoped to draw these immigrants - more than half of whom do not have U.S. bank accounts - into the formal financial sector.
Treasury Secretary John Snow has been a major promoter of this cause. In April, he joined finance ministers and central bank governors of the Group of 7 industrialized nations in a statement promising to continue working on ways to make it easier and cheaper for immigrants to send money to their home countries and "to integrate remittance services in the formal financial sector."
The fee for sending small amounts, after dropping from about 15 percent in the late 1990s to 9 percent in 2001, has not fallen much further. The average fee for sending around $200 to Latin America this year is 7.6 percent of the amount sent, according to the study.
"The banks have gone through all this effort; it's still early, but the numbers are still fairly small, given the size of the operation and the extent of their investment," said Roberto Suro, director of the Pew center. "Prices have stabilized, especially in Mexico, the biggest market, despite very substantial increases in volume and competition."
Today, some 50 companies vie for a slice of the roughly $1.2 billion a month that flows to Mexico. And banks have focused on the Mexican market. It was the Mexican government's decision to issue new identity cards for its expatriates in the United States, and the U.S. Treasury's decision to allow banks to accept the cards as identification when opening accounts, that drew many banks into the remittance business three years ago.
But despite hefty marketing efforts, the banks still have only a meager share of the business. According to the Pew report, the four largest banks in the business - Citibank, Wells Fargo, Bank of America and Harris Bank - together handle about 100,000 transfers a month. That is less than 3 percent of the 40 million remittance transactions to Mexico each year. And banks' effect on prices also seems muted. The average fee to send $200 to Mexico is 7.3 percent, compared with 8 percent in 2001.
Offerings from the banks have changed the market to some extent. Flat-fee structures make it less expensive to transfer larger sums of money: The average fee to send $400 to Mexico is 4.4 percent. And some of their products and services are cheaper than other transfer methods. But the banks remain hampered by many immigrants' lack of familiarity with formal banks and financial services as well as by other obstacles - like the small cash-machine networks and bank branch systems of Mexico and other Latin American countries, which seldom extend into rural areas.
Manuel Orozco, a remittance expert at Georgetown University who put together the report for Pew, said that U.S. banks had been aggressively pursuing the business for only about three years and were still learning how to gain new customers.
"The cost will fall," Orozco said, "as banks attract more customer deposits and so they can finance the transfers."
The New York Times
May 23, 2004
Paypal moves further away from money
Paypal have announced their new list of "unacceptable goods" as covered by Wired [1]. It includes such odd things as human body parts, event tickets, batteries, food, medical equipment, malls, copies of software, ...
The list is 64 items long and an amazing read [2]. I'd hazard a guess that if anyone complained about some item, on the list it goes! Wired comments that postcards portraying topless subjects are permitted, as is food in the shape of genitalia, yet any other adult content must only be transacted on eBay. How long will it be before the "Mothers against evil uses of fruit" put a stop to that?
Pretty soon, the only thing left will be Paypal subscription fees.
The observation has been made (by Paypal themselves to industry conferences) that Paypal is best understood as a lower segment credit card facility for merchants. They permit small merchants to take payments. Paypal's heritage as a Palm Pilot person-to-person money is long forgotten, and now it seems that they have moved even closer to conservative values when it comes to deciding what's right and what's wrong for you to buy from approved merchants.
Luckily, over in the DGC community, there appears to be an alternate. Instead of focusing on the common carrier principle, and banning certain uses of the product, the gold issuers have adopted a customer rejection approach. Partly because of their historical background as privacy supporters, and partly due to free market leanings, the principle is that any Issuer retains the right to discharge a person's account, for any reason whatever.
I.e., the Issuer of a gold currency does not offer the service to just anyone, and you don't have your normal consumer right of equal service. This seems to have resulted in some quite fierce closures of accounts, but it also seems to have preserved the currencies as, well, currency.
[1] "PayPal Tightens Transaction Reins," By Christopher Null
http://www.wired.com/news/print/0,1294,58208,00.html
[2] "PayPal Acceptable Use Policy,"
http://www.paypal.com/cgi-bin/webscr?cmd=p/gen/ua/use/index_frame-outside
May 03, 2004
Bufflets
Warren Buffet is in the news again, over on the goldmember list, and no doubt countless thousands of lesser media [1]. At the annual shareholder meeting, the 10,000 or so shareholders turn up for what amounts to a great big party. As well as a meeting where the company actually talks to the shareholders.
"Vice Chairman Charles Munger and Buffett fielded questions from the crowd for about six hours about their investment philosophy, succession plans and reaction to criticism to Buffett's board seat on Coca-Cola Co. [2]"
What other company does that? Companies I know don't hold any shareholder meetings, let alone let them ask questions. Warren Buffet, is every investor's hero, and the founders of google recently wrote him up as their God, as well.
"Shares of Berkshire, which owns energy, aviation, paint and carpet companies, have increased 28 percent in the past year compared with a 19 percent gain for the Standard & Poor's 500 Index. The shares fell $110 to $93,390 in New York Stock Exchange composite trading on Friday. [3]"
Mr. Buffet never splits, and thus the price goes higher and higher and higher ... His motive here is quite simple. Buffet, the world's best investor, wants to exclude small shareholders from his register. This price is so high that not only can no ordinary investor afford even one of his shares, but most systems cannot quote a price in it. (Check the WSJ, it's not there, last I heard.)
He has basically excluded all of the hoi polloi. In marketing terms, this is called "price discrimination." He has chosen an educated base of shareholders, using the proxy of wealth, as the tool to select his shareholders. Quite valid stuff, albeit an unusual use of an old marketing tool.
Here's how we arbitrage it. To frustrate him, we (being Ivan, a potential issuer) would buy one Berkshire-Hathaway share. One will do for now, we can always pick up another later! This share we escrow in the normal fashion with a transfer agent.
Then, we designate our one share as reserves for an issue of Ricardian instruments. Instead of issuing one derivative share backed by the one real Berkshire-Hathaway share, we would issue 100,000 microshares. These instruments I call Bufflets, and their price would be more likely around ninety three cents.
Hey presto, we arbitrage the marketing. With our 100,000 Bufflets, even your 10 year old can afford to become an investor in Berkshire-Hathaway. Mind you, only one of us gets to go to the party every year, but that's maybe the subject of a shareholder's meeting yet to come.
[1] Warren Buffett joins Kerry campaign
[2] Buffett Says He Has Increased Bet Against U.S. Dollar (Update3)
[3] Ibid.
April 16, 2004
Sharing Files is still a "Hard App"
How hard can finance be? Real hard. Below is a snippet from techwatchers NTK (below) that reports on the state of simple file sharing amongst a bunch of mates.
Our own little efforts to add this feature to Ricardo were illuminating. It took me 3 days to write the protocol additions to SOX, add the storage into the existing backends, and confirm via self-tests. Ricardo is now fully capable of sharing files, encrypted, authenticated, and all that, across a bunch of, well, mates!
That just leaves the client. Whoops... it took me a week just to compile, due to a serialization bug (an oxymoron, if ever I heard it). Anyway, that part's done, and if I can just wade my way through a month of SWING, then we might be able to show file sharing done the Ricardo way.
Sum total: infrastructure wise, almost any app is easy in Ricardo. Client wise? That's where all the work is. Now read NTK, as if your weekend depends on it:
>> TRACKING << sufficiently advanced technology : the gathering
The big new (yet old) killer app this year is going to be a
some dinky little program that lets you easily and
selectively share individual files with groups and
sub-groups of your friends. It seems such a simple idea, but
given the number of Known Clever People struggling to
implement it, it has to be harder than it looks. The
Nullsoft guys tried it with WASTE, but that was too
crypto-tastic to succeed; Ximianites have adopted Novell's
iFolder as their effort, but that's still pre-alpha. Now
ex-Audiogalaxy staffers are working on FolderShare.
FolderShare has some of the right idea - it just sits in
the background, talking P2P with your mates, and silently
rsyncing their shared directories with yours. Weirdly it
requires a central logon, but still won't cope when you and
your friend are both behind NATs or firewalls; you'd think
having a central server, they'd be up for negotiating some
connections. The ACL stuff is still, in the way of ACLs,
confusingly powerful instead of usefully simple. It's also,
tragically, Windows only. It might yet grab the Napster
crown of reaching critical-mass usability, but there's still
a way to go.
http://www.foldershare.com/ - can't help feeling the hard part is a compelling UI
http://usefulinc.com/edd/blog/contents/2004/03/08-ifolder/read - uh-oh virtual file systems!
http://forge.novell.com/modules/xfmod/project/?ifolder - uh-oh C#!
Oh, and "Copying is fine, but include URL: http://www.ntk.net/ "
April 15, 2004
Spammers have stats?
The following email from spammers & scammers indicates that the view of e-gold and Paypal is about the same - a round 400k each of addresses. I don't believe that there are that many e-gold active users out there, but it may be that their more heavy duty approach to financial transactions increases the punch of their lower numbers.
One of the great difficulties with these markets (decried frequently by superlative marketeers such as JPMay) is that there are no statistics on ... well, everything. It would be sad if we had to rely on the biased view of scammers to conduct our business. Still, worse things happen at sea, at least their biases will be where the money is.
------------ Forwarded Message ------------
Date: 15 April 2004 15:56 -0400
From: Tom Theroux
To: Domains
Subject: RE: Emails of PayPal customers
Hello:
We are offering 2 email databases which allow to contact PayPal and e-Gold
customers (both sellers and shoppers).
These are individuals that buy and sell items using PayPal and e-Gold
payment systems. (Please notice that 90% of PayPal customers are also
customers of eBay.)
These databases will be perfect for selling your products/services, because
we are providing you unique prospects who purchase and sell online more
than anybody else! Besides, the data provided contains personal email
addresses of only those PayPal and e-Gold members who were active
(purchased or sold something) in the last 2 months.
PayPal - 406,000 records
e-Gold - 372,000 records
The databases will be delivered to you in any format of your choice (Excel,
ASCII, CSV, etc.). By default they are provided in 4-6MB TXT files.
New updates will be released quarterly.
The total price we are asking for both databases is $365. To place the
order please fill out the form: http://www.gmthost.com/paypal.php
To contact me please email to service@gmthost.com (THIS EMAIL ONLY! DO NOT
'REPLY').
Please notice that we also maintain a variety of other b2b and b2c lists.
Best,
Tom Dullex
---------- End Forwarded Message ----------
April 09, 2004
When Play Money Becomes Real
The virtual games world has been around for a long long time, and recent years have seen an explosion of interest as gamers from around the world bid to buy and sell their game artifacts for real money.
Certainly potential there for setting up virtual monies that are in some way related to the normal monies for meatspace. One thing: there isn't the usual security problem, as players have some incentive to act honestly, and some way to punish those that don't.
By Daniel Terdiman 02:00 AM Apr. 07, 2004 PT
The buying and selling of virtual currencies, weapons and other goods from massively multiplayer online games like EverQuest and Ultima Online may be off most people's radar, but it is truly big business.
One company, Internet Gaming Entertainment, or IGE, has more than 100 full-time employees in Hong Kong and the United States who do nothing but process its customers' hundreds of thousands of annual orders for virtual goods, the lion's share of which average nearly a hundred dollars each. And demand is so strong, says IGE CEO Brock Pierce, that the company is hiring about five new people a week.
IGE is by no means the only outfit on the Internet that's trafficking in items from games like EverQuest, Ultima Online, Dark Age of Camelot and others, but it is the biggest.
"In this industry, it's eBay and us," boasts Pierce. "We're the major players. We've consolidated most of the other players out there."
While IGE has had several hundred thousand customers since its inception in 2001, it depends on a stable of more than 100 suppliers -- hard-core players who sell IGE surplus currency, weapons and other goods they regularly accumulate.
"They can play games all day and make a little money for it," says Pierce. "Most of the time, they're selling off their garbage, but one man's garbage may be another man's treasure.... They'll sell us that (extra) suit of armor, or sell the suit of armor in the game and sell us the currency, and then they'll go pay their rent with it."
IGE's business treads into controversial waters in the gaming world. That's because its buyers are spending real cash to improve their lot in life, or at least in the games they play, without having to spend the time to do so.
Some game companies, like Origin, which produces Ultima Online, say they don't mind if players buy and sell the virtual goods in secondary markets because, ultimately, it increases interest in the game. Linden Lab, which produces the metaverse Second Life, actively encourages secondary-market trading, because it sees such activity as part of a larger social and economic experiment, with its game at the center.
And still others, like EverQuest publisher Sony Online Entertainment, see such trafficking as nothing but a headache.
"The official line is that the selling of characters, items or equipment in EverQuest goes against our end-user licensing agreement," says Sony Online Director of Public Relations Chris Kramer. "It's currently not something the company supports and causes us more customer-service and game-balancing problems than probably anything else that happens within the game."
Kramer adds that Sony Online's objections are based mostly on the idea that such trafficking isn't fair to players who've spent countless hours in the game.
"From a design perspective, our developers don't like it, because essentially what it comes down to is it rewards the rich. It sort of cheapens the experience for people who have invested the time in the game to get to a certain level.
"We have people who have been playing for a number of years in EverQuest," he continues. "They've invested a large number of hours into creating their character, (and) amassing a small fortune in platinum. To have a person who has spent that much time and effort turn around and see someone else who has a character with equal abilities who has done nothing more than buy it on eBay, it turns off a lot of our players."
Yet despite the fact that trafficking in EverQuest goods runs counter to the game's end-user licensing agreement, it is the driving force that keeps IGE's operations center in Hong Kong running 24 hours a day, every day of the year, says Pierce.
To some, like Sony Online's chief creative officer, Raph Koster, the question boils down to different philosophical approaches to the creation of virtual worlds. Some companies, like Linden Lab, There and, to some extent, Origin, get excited watching what happens when their players take elements of their virtual worlds out into real secondary markets. Others, like Sony Online, see them as games, and nothing more.
"We don't happen to regard being a game as being somehow less noble of a goal," says Koster. "It's not a bad thing. A lot of people will want that. That doesn't mean that as a company and as individuals, we're not excited (with) virtual worlds as exciting and interesting places. But at the same time, if we've created one that's specifically a game, the audience wants it to be a game. We try to do right by that philosophical desire: to keep it a game."
But it is impossible to ignore that, percolating within many of the MMORPGs in operation today, including EverQuest, are economies that straddle the real and virtual worlds.
This has led IGE to bring on Ken Selden, a Hollywood screenwriter and leading peddler of virtual goods, as its chief economist.
"There's a relationship between real-life economies and a virtual economy," says Selden. "I happen to believe that these virtual economies are very real, serious economies."
Selden says the strength of a virtual economy is determined largely by how stable its currency is. And because IGE is the largest secondary market for the currencies of games like EverQuest, it has a lot of influence over the stability of the exchange rates between the game currencies and U.S. dollars.
"Everything circulates around the exchange rate between a real and virtual-world economy," explains Selden. "We set the rates that we buy and sell at, and those are divined by supply and demand. The amount of currency in circulation at any point is extremely important to the out-of-game exchange rate."
He also explains that real-world events often have an impact on what people pay for the virtual currencies.
"Bubbles in the economy, they'll also impact the exchange rate between the two economies, because by and large the buying and selling of virtual-world economies are something I would consider to be a luxury," says Selden. At "tax refund time, demand goes up, because there's more money. The consumer wants to spend (and) he has more discretionary income."
Kramer says Sony Online is aware of IGE and has spoken with the company.
"At this point, we're still sort of trying to decide what direction the company's going to move in on this topic," he says.
But whether Sony Online likes it or not, EverQuest players are lining up to buy the game's currency, weapons and armor from IGE all day, every day.
And Selden thinks the game companies should accept that fact and learn that they can benefit from supporting the secondary markets in their games' goods.
"One of the problems is that there isn't enough communication between the people who are minting the currency and the people outside who are selling it and defining it," he argues. "It's almost like the treasury isn't talking to the federal reserve in these worlds. And I think it's because the game companies are just waking up to how important it is."
April 04, 2004
Media shift - Cellphones go soapie
[comment:] Phones are different to prior broadcast media - they are 2 way, and one can run protocols over them such as payments. Given this, the mobile phone world is the nearest thing that the old world has to the Internet. Here's another development that indicates how the Empire is striking back:
April 04 2004 at 12:15PM By Audrey Stuart
Cannes, France - The launch of TV's first-ever soap for the tiny cellphone screen might not suit everyone's taste, but it is living proof that the TV and digital worlds are merging.
With this convergence due to transform the average consumer's entertainment fix, a record number of mobile-phone operators -including heavy-hitters such as Vodafone, Nokia and Telefonica -turned up in large numbers at this week's international MiPTV and MILIA trade shows.
Aside from ringtones and music, games, news and sports results are the current favourites of cellphone users, many of them children and younger adults. And now the race is on to attract new audiences, with the big strides achieved in video streaming to phones throwing up new opportunities.
Movie lovers are also in for a treat
"The quality of content, like video, is improving as are the handsets. It's a step change in the level of service," Vodafone's Graham Ferguson told a forum in this Riviera town.
The first soap-drama specifically made for cellphones, called Hotel Franklin, has just been launched by media giant News Corporation. The episodes last just one-minute because, said News Corp.'s Lucy Hood, this "seems to us to be the natural length" for phone viewers.
That time frame allows for enough character development and plot before leaving a hook at the end to get viewers to look at the next episode.
The hugely popular dysfunctional Simpson family characters star in another News Corporation initiative to tap into the big cellphone market.
Phone users can call up cute, short clips featuring The Simpsons with messages like I'm tired or Happy Birthday to send to their friends.
Hit TV game shows such as Who Wants To Be A Millionaire are also transferring to telephones, and a deal to license a Millionaire phone game, developed by Active media, and an SMS text version, was unveiled here this week.
Movie lovers are also in for a treat. There has been a huge rise in the number of homes with broadband connections opening the way for video-on-demand services and on-demand television (IPTV).
Japan's Softbank Broadmedia has led the way in video-on-demand and just a year after the service was launched, BB Cable TV subscribers can choose from a 2 300-strong video library.
A number of companies have followed in BB Cable's footsteps. The world's largest cable company, Comcast, offers a large selection of interactive video-on-demand products, which are proving popular with over 50 per cent of its 23 cable subscribers. "We're getting lots of mileage out of video-on-demand," Comcast's Ty Ahmad-Taylor said here.
Viewers appear to appreciate the ease of the system, which enables calling up a movie directly on the TV set, without having to leave home. The cost of the "rental" is either included in a subscription or automatically put onto the phone bill.
The millionaire-studded principality of Monaco was one of the first in Europe to launch the VOD concept in Europe but it is also available elsewhere, notable in Britain through Video Networks.
The more optimistic market watchers believe it might not be long now before all digital devices in the home, including the DVD, mobile phones, digital cameras and the brand-new digital video recorders known as DVRs are hooked up together.
If and when that happens, the PC could play the central link-up, upstaging the power of the television.
With the number of remote controls that are scattered around many people's homes that might be a great step forward. But other experts are hedging their bets about how long this may take to happen, if it comes about at all.
As one key speaker at MILIA, Joichi Ito, pointed out, "traditionally, the (content) industry has been wrong about how consumers use these devices."
So while there may be a lot of balls in the air, no one really knows for the moment which ones are going to stay up and which are going to fall.
Sapa-AFP
April 02, 2004
The Dollar on the Move
As international currency is one of the big possible applications for Financial Cryptography, the way the currencies move makes for an important business backdrop. It's well known that volatility is good for business, and a rising market is good for startups...
In this vein, the prediction that the US Dollar is losing its pole position is starting to show true. James Turk, in goldmoney's Founder's Notes, presents "What Future for the U.S. Dollar?", being discussion by W. Joseph Stroupe of the Central Banks' of Japan and India decision to "ease up in buying dollars."
This signalling away from single-minded support of the dollar, by means of lesser reserves purchasing, will mean their currencies will rise, and their exports to the US will shrink. But it also means that Japan and India will be less vulnerable to the shrink in international value of their reserves, as the dollar moves further down.
This article "US complicit in its own decline", in the Asia Times, by the same author, is much longer and broader, and raises the surprising claim that Russia is manouvering to take an important position in oil supply. To become, it seems, the other Opec. Interesting stuff, which I mostly placed in the "reserved for future evidence" basket.
March 19, 2004
Online Gambling Payments - Looking for a Home?
Online Poker: Hold 'Em and Hide 'Em
By IAN URBINA Published: March 19, 2004
Ben sleeps five hours a night; the rest of the time he sits at his desk in his Brooklyn apartment playing online poker. He won $55,000 one recent evening, but in his tireless ambition for the $2.5 million world championship, this mild-mannered college graduate has become an outlaw in hiding and a twisting thorn in the side of Eliot Spitzer, the New York attorney general.
Ben quit his teaching job five months ago and now makes around $100 an hour. Five days a week, he clocks 10-hour shifts of Texas Hold 'Em on his Dell laptop computer. With reggae in the background and coffee mug in hand, he studies his competitors who sit in London, Copenhagen, Los Angeles and elsewhere, while the dealer in Costa Rica tosses cards.
A couple of blocks away, a slightly less-skilled friend of Ben's named Jimmy also works busily. While Ben plays high-stakes tournaments with pots topping $70,000, Jimmy is what is known as a "grinder" - he works the smaller virtual tables, specializing in cheaper and less risky play, but keeping three games going at all times, nickel and diming his way to decent earnings. In the past four months, Jimmy says that he made $30,000.
Ben and Jimmy would only speak to a reporter if their last names stayed out of the newspaper. That's not surprising, because they are the human faces on the wrong end of Mr. Spitzer's public campaign to shut down the hugely profitable online gambling industry.
Although they asked for anonymity, the two men say they are not hugely worried about Mr. Spitzer's campaign, despite the attorney general's relative success.
To spend the afternoon with these players is to enter a world where, at any hour and with a little luck and a touch of skill, decent wages can be had without ever changing out of one's pajamas or leaving the comfort of one's own couch. But to get there means venturing just across the border of legality. Since 2002, Mr. Spitzer has succeeded in getting more than 10 major financial institutions, including Citibank and PayPal, one of the largest Internet money transfer companies, to stop processing gambling transactions. But he has been unable to prosecute the Web site operators, most of whom are offshore, and hard pressed to arrest online gamblers because they are dispersed all over. Instead, he has tried to seal off the financial pipeline connecting the two.
In recent months, federal prosecutors from around the country have joined the effort by threatening to prosecute on charges of aiding and abetting any businesses in the United States that provide advertising and financial services to illegal Internet casinos. As a result of the pressure, several large media operations - including Infinity Broadcasting, Clear Channel Communications and the Discovery Networks - have stopped running advertisements for offshore Internet casinos.
Jimmy said the attorney general's efforts have made his life a tiny bit more complicated. "It used to take me one mouse click; now it takes two," he said. He simply shifted to Net Teller, a Canadian equivalent of PayPal, to buy chips. Ben mails a cashier's check to his poker Web site in Antigua.
Lee Jones, online manager of one of the most popular sites, Pokerstars .com, says 10,000 players can be found on the site at any given time. "Our players tend to be a pretty loyal bunch," he said.
Some are more addicted than loyal. Steve, a Long Island lawyer who like the others did not want to give his last name, said he still owed a $15,000 credit-card debt to an online poker site. Having already kicked a 10-year gambling habit, Steve fell back into poker after his wife bought a computer.
"It's not a temptation you want in my living room," he said.
Willie J., a Manhattan businessman, began attending Gamblers Anonymous meetings two years ago, after finding himself $45,000 in the red. "I had 12 credit cards and had memorized all their numbers and expiration dates," he said. "That's when I knew I was in serious trouble."
As an industry, online gambling has obvious profit potential. While casinos in Las Vegas pour hundreds of millions of dollars into show-stopping hotels, Web sites require not a drop of mortar nor one cent for lounge acts and cheap buffets. What Web sites lack in pizazz, they make up in convenience, as customers can play a quick round of $100 blackjack seconds after rolling out of bed.
Mr. Spitzer decided to clamp down on the industry in 1999 after his office won a precedent-setting case involving an Internet casino. The Web site's operators, World Interactive Gaming Corporation, based in Suffolk County, claimed they should not be subject to New York gambling laws, since their Internet servers were licensed in Antigua. However, the State Supreme Court ruled that the Caribbean location was irrelevant, since the actual transmission of information from New York via the Internet constituted gambling activity within the state.
This ruling may, in the long run, doom New York online bettors, said Ken Dreifach, chief of the state attorney general's Internet bureau.
On the federal level, online gambling remains uncharted legal territory. Many legal scholars point to the 1961 Wire Act, which makes it a crime to use a wire for transmitting betting information across state or national boundaries. But it makes no mention of the Internet and is typically viewed as being limited to sports betting. Legislation pending before Congress could amend the Wire Act to include restrictions on Internet gambling, said I. Nelson Rose, a law professor at Whittier Law School in California.
Historically, gambling regulation has fallen to the states, but few besides New York have aggressively confronted its online form, perhaps because of enforcement difficulties. Bradley J. Gibbs, a lawyer with Heller Erhman, a law firm that has handled online gambling litigation, said "arresting grandmothers and 12-year-old computer users is a sure public-relations disaster."
Mr. Dreifach says his office found an effective weak spot when it focused on the flow of online funds. The tactic also made sense, he said, because most credit-card companies processing these transactions are in New York City.
By reprogramming a couple of lines of software, Mr. Dreifach said, the code corresponding to these sites was blocked. But the effectiveness of such blocks remains to be seen. "If money is flowing, tunnels dig themselves," Professor Rose said.
Mr. Dreifach is confident his work has made its mark. In 1999 profits from online gambling were estimated at $3 billion, with indications that the number would double within three years, Mr. Dreifach said. The estimate still lingers around $3 billion, he said.
"I think we had a big part in cutting off the growth," he said.
Some poker players actually support the idea of making online gambling illegal. But they do not believe poker is a form of gambling.
"It's a game of skill, not of chance," Jimmy said.But in the eyes of the law, Mr. Dreifach said, gambling includes all games in which chance outweighs skill. "I don't know about you," he said, "but for most of us, poker is certainly a game of chance."
March 10, 2004
Civilian lists films as IPOs
Civilian Capital has entered the market for Hollywood film productions as IPOs. In Civilian's case, each film is produced by a single-film company that lists on the over-the-counter bulletin board market run by the NASD (a sort of basic NASDAQ, called OTCBB).
Originally, doing such projects as IPOs was mooted in discussions surrounding Idea Futures, Eric Hughes' piracy talk, and my own task market.
The basic assumption was that most tasks of interest can't cover the 1/2 million dollar surcharge that the regulated markets impose on access to the public. Our new breed of digital issuances reduces that cost by an order of magnitude or more, depending on the details.
That assumption's not challenged by Civilian - they are simply providing a brokerage which promotes and retails these special purpose IPOs to film entrepreneurs. It will be interesting to see how low the listing cost of Civilian's film IPOs go, via the conventional markets and regulatory filings.
For those obsessed by celluloid, check out the SEC filing for the first film/IPO: Billy Dead, Inc.
March 02, 2004
Heavy Films
I took the brave jump recently and stored all my DVDs in a caselogic case. For pure personal convenience, you understand.
232 was the final count. As I did this, I took the opportunity to weigh the cases (in their garbage bags, 60 per bag), with the notion of figuring out how much a film weighs. The less it weighs, the more convenient as a travelling companion!
This gave me a total mass of 78 grams per film, including standard cases. That's just the 20cm high case, not the battleship containers they come in, all well disposed of, mere minutes after purchase.
Toying around with these numbers, that gave me a collection mass of 18 killograms (about 40 of those imperial pounds). But, by throwing out the packaging and sticking to sleeve books, this came down to 3.2kg, or, on a per DVD basis, a mass of 13.7g.
That's better than a 80% compression, mass-wise. Which got me thinking, what's the mass of a DVD on a hard drive? Uncompressed, you can get about 40 films on a 240G drive. The bathroom scales wouldn't budge with the drives I had to hand, so I stacked up 10 of them, and averaged back to about 400g (just under a pound), giving a per-film mass of about 10 grams.
But, if we add a compression ratio, we can get that right down! Say, 5 to 1 compression, which exists, so I'm told, and I can get the whole collection onto one single disk drive. Which leads to a DVD mass of about 1.7g per.
Putting an entire collection on a single drive makes a lot of sense. One can imagine the day when one wonders why PCs weren't the primary interface to movies. Selection of movie, display of the information, quick flick through the scenes, all this stuff makes much more consumer sense when considered magnetically, not with optics.
Which means that the PC takeover will happen, given time, and the patient efforts of programmers around the world.
(Veteren FCers will recognise the DRM link to FC here.) One of the things that I thought would give the film industry a breathing space to work out a DRM architecture was the brute data size of films. That coupled with the lack of fat pipes for consumers meant that copying DVDs was a marginal activity.
No longer. It may well be that Hollywood, as it is structured, is already caught in the trap that the music industry got itself stuck in (MP3s, ages ago). Which makes the news from tinsel town even more amusing: on the one hand we have the Passion's innovative channels, and $20 DVDs of interviews !!!
On the other, the FBI claims that DRM is priority number 3 for them. Who's thinking over there, and who's just changing the colour of the pretty lights? Hollywood can't even claim that their way is more convenient - retail DVDs are just too heavy to compete against the net.
| collection size | number of DVDs |
in original packaging |
in sleeved caselogic book |
in disk drives | comments... |
| Total collection | 232 | 18. kg | 3.2 kg | (400g) | All of them... |
| single big drive worth of DVDs | 40 | 3.1 kg | 548 g | 400g | 240Gb - would need 5 drives |
| single drive, compressed | 240 | 18.6 kg | 3.2 kg | 400g | 240Gb @ 5:1 compression |
| per single DVD | 1 | 77.6g | 13.7g | 1.7g | mass per film |
February 23, 2004
DRM is FBI's 3rd highest priority?
The BBC writes that "the FBI ... says piracy is now its third biggest priority behind terrorism and counter-intelligence." Weighing in to the fight against piracy, the BBC also includes a smorgasboard of links on how, when, where to download and copy, over on the right hand side.
FBI weighs into anti-piracy fight
CDs, DVDs, and video games in the US are to get an FBI seal in an attempt to deter people from copying them.
The new labels warn consumers that criminal copyright infringement could land them with a $250,000 (£133,000) fine and five years in prison.
They each carry the seal of the FBI, which says piracy is now its third biggest priority behind terrorism and counter-intelligence.
US entertainment firms says they are losing billions of dollars to piracy.
"The theft of copyrighted material has grown substantially and has had a detrimental impact on the US economy, said the assistant director of the FBI's cyber division, Jana Monroe.
The FBI said it was up to individual companies whether the label appeared on the packaging, or on screen.
The full warning reads: "The unauthorised reproduction or distribution of this copyrighted work is illegal.
"Criminal copyright infringement, including infringement without monetary gain, is investigated by the FBI and is punishable by up to five years in federal prison and a fine of $250,000."
The label has the backing of the Recording Industry Association of America (RIAA), the Motion Picture Association of America (MPAA), and two groups representing the software industry, the Entertainment Software Association and the Software and Information Industry Association.
RIAA executive vice president Brad Buckles said: "As the seal attests, these are serious crimes with serious consequences - including federal prosecution - to making unauthorised copies or uploading music without permission, and consumers should be aware of them."
Last year the RIAA filed hundreds of lawsuits through the US courts against individuals it accused of swapping music online.
MPAA senior vice president Ken Jacobsen said the film industry was losing $3.5bn (£1.86bn) each year through piracy, before copying via the internet was taken into account.
"With hundreds of thousands of jobs at stake nationwide, piracy is a serious threat to the entire entertainment industry," he said.
Story from BBC NEWS:
http://news.bbc.co.uk/go/pr/fr/-/1/hi/entertainment/music/3506301.stm
Published: 2004/02/20 12:14:07 GMT © BBC MMIV
From Bretton Woods to GW-II
The great shifts in currency politics go on - this polemic "Bretton Woods and the Forgotten Concept of International Seigniorage" is on the background of the USD since Bretton Woods, leading up to the recent Iraq invasion. Evidence seems to be mounting that one of the major factors (of three or four) was the importance of the oil-dollar trading book as a mainstay for USD reserves at world central banks.
Bretton Woods and the Forgotten Concept of International Seigniorage
Dix Sandbeck
In the summer of 1944, delegates from 44 allied nations met for the now famous economic conference at Bretton Woods, New Hampshire. Their mandate was to finalize plans for the post-war economic order and currency cooperation that had been circulating among the Allied nations.
Some of the results of this meeting are still familiar elements of the current structure for international economic co-operation: the International Monetary Fund - and the World Bank are cases in point.
Largely forgotten today is that the establishment of an international reserve currency had also been on the agenda at the time. Keynes, chairing the British delegation, proposed the establishment of a special reserve currency, provisionally named the "bancor." President Roosevelt had at first instructed the American delegation to support such an initiative.
Keynes envisaged the bancor as an international trade currency and unit of account. Its management and issue was to be in the hands of an another planned international organization, the International Clearing Union (ICU). The value of the bancor was to be determined by the value of the different national currencies in a trade weighted basket. Values of currencies would be fixed, but could be changed by mutual agreement.
A fundamental aim of Keynes' plan was to install a truly multilateral system. No nation would be allowed to dominate; nations in surplus or in deficit would be disciplined alike. Shortly before the conference however, the Americans rescinded their support for the bancor. Presumably, they felt that the bancor scheme, with its control in the hands of the ICU, was a shrewd strategy to rob the United States of its greatest spoil of victory: unfettered post-war dominance.
Instead, the Americans insisted on a system where the US dollar would be fixed to a gold value of $35 per ounce, though convertible only for central banks. All other currencies were to be aligned to this dollar-gold anchor. If adopted, this would confer on the US an unprecedented supremacy Even Britain, at the pinnacle of her power had not enjoyed such a position. But at Bretton Woods the exhausted European nations were eager for the continued flow of dollars to finance the war and the impending reconstruction. No nation was in a position to challenge the American volte-face.
In general, the dollar-gold link has been viewed as the key feature of the Bretton Woods system. In 1971, President Nixon "closed the gold window" by officially cancelling the right for all other central banks to convert any dollar holdings into gold. Many have considered this the year of Bretton Woods' demise. However, the dollar-gold link had always been an illusion elevating the dollar to the role of a global reserve currency. The true significance of Nixon?s decree in 1971 was simply to destroy that mirage.
The fixed exchange rates served a clear purpose in the immediate post-war period when stability was at a premium. After economic activity and trade had rebounded, the tendency of fixed exchange rates to magnify misalignments took over.
International Seigniorage
Seigniorage as a concept originated in medieval times. Monarchs used their monopoly in coining precious metals as a major source of revenue. Periodically an issue of gold or silver coins would be recalled, recoined with a lesser precious-metal content. The difference in value, between the face value and value of actual gold or silver content, was the seigniorage gain. When modern states expand their monetary base, they do so by sending more money into circulation, which pays for some of their expenditures. Since money is largely credit today, the seigniorage gain is almost equal to the face value.
Countries whose money functions as international reserve currencies, benefit from seigniorage, on an international scale. They can, as a nation, pay for imports with the seigniorage gain accruing from the expansion of international reserve holdings of their currency.
Ultimately, Bretton Woods allowed the US to reap international seigniorage by providing the world with much needed reserves. As a result, the US was able to impose many of its internal problems onto other nations. This key outcome of Bretton Woods continues to be an integral part of the global economic order.
By the late seventies, the oil crises had dramatically changed the terms of trade between the oil exporting nations and the rest of the world. Through forging a close political partnership with Saudi-Arabia, the leading oil exporter, the US ensured that oil would continue to be priced in dollars.
The oil exporting countries' collective surplus of petro-dollars was recycled back into the international financial system as liquidity, which was increasingly held in off-shore accounts as eurodollars. Although many of the developed nations experienced rising trade deficits, they had little problem in financing them by drawing on these pools of liquidity. The real losers were the developing nations that ran into exploding debt burdens.
Currently, international organizations with a role in providing development assistance to the Third World are almost entirely dependent upon contributions or paid-in quotas from richer nations. The bancor plan would have made the gain from international seigniorage partially or fully accessible for development assistance, instead of, as it is now, squandering it in support of the world richest nation and its over-consumption.
The Road to Baghdad
By the late nineties, US dollar holdings were estimated to account for approximately 65% of all held international reserves. The resultant dollar strength has allowed the US to sustain imbalances in the form of budget and trade deficits, that no other nations would be capable of (as was the case during the Reagan administration). The Clinton administration successfully turned the budget deficit around, but at the cost of a trade deficit that escalated uncontrollably.
The US economy has continuously reaped the benefits from the international economic system's inability to discipline it effectively. Because of this, American administrations have become accustomed to pandering to short term economic interests of key constituencies. Not surprisingly, these policies have resulted in such abysmal deficit levels, that had a developing nation applied for IMF support with such numbers, they would have been promptly rejected or at least placed under a harsh array of conditions. However, there is evidence that the days of smooth sailing are drawing to an end.
The first problem arises from the fact that dollars need to be invested in dollar denominated assets in order to earn a return. Consequently, when the world experiences a rising dollar overhang, it creates inflationary tendencies in the pricing of dollar assets. This was no doubt a major factor behind the stock market bubble of the '90s. The subsequent correction appears to have made international dollar holders wary of repeating the cycle.
Then there is the emergence of the euro as a full-fledged currency, presently used by 12 of the EU nations. This means that all trade and tourism spending between these nations has become internalized into euro transactions. Previously, the majority of these transactions were based on non-dollar pricing and reserve holdings.
As previously mentioned, a major component in maintaining the dollar's dominant position during the wake of the oil crises, was the Saudi's commitment to preserve the dollar as the currency in which oil was priced. This leads to the third, but potentially the most worrisome, cloud in the sky for the Americans. For a long time, the majority of nations seemed to have acquiesced to the oil-dollar relation, the linchpin of its dominance in recent decades. Nevertheless, signs have emerged during the last couple of years that this is no longer the case. A clear example can be observed in the actions of Chavez in Venezuela who started to counter-trade with some of his Latin American neighbors, thus cutting the dollar out of the loop.
But the real shocker for the Americans must have been when Saddam declared in November of 2000, that Iraq would commence pricing their export under the oil-for-food program in euros. American worries were compounded by subsequent rumours that both Libya and Iran were considering a similar currency shift.
This leads to the final question concerning the real reasons behind the American attack on Iraq. Did the Americans really have such faulty intelligence that they deemed Iraq to be an imminent threat to their security?
Of course not. However, by pricing Iraq's oil in euros, WMDs or not, Saddam engaged in an ultimate act of American defiance. What definitive role it played in galvanizing the American call to war, is hard to say. What is clear however, is that toppling Saddam's regime showed everybody the big stick, and more importantly took the impending euro pricing of oil off the table.
Dix Sandbeck
from Economic Reform, Sep. 2003
February 16, 2004
PayPal acquires eMoney Licence
Over on Simon's blog, he reports that PayPal is to be licensed as an eMoney issuer by the FSA in the United Kingdom.
Simon postulates that "This is a very remarkable moment, demonstrating that of all EU supervisors, the British FSA operates best. They did not hesitate to give licenses to Internet-based new entrants companies such as Moneybookers, Prepay Technologies and now Paypal."
The eMoney licence requirement was always seen as a barrier to entry, raised by the banks to protect themselves, and of no discernable benefit to any other party such as consumers. The eventual layout of the directive said "you don't have to be a bank, but you have to look and act like a bank, and have lots of money too..."
Hence, the EU practically guaranteed that eMoney would not arise in their patch, and people like PayPal would need to bring their bona fides in from the US, which requires no special permission to experiment with Internet money.
Similarly, DGCs have never taken as much root in Europe as they have in the North American and Australasia, mostly due to the regulation and innate conservatism of the people (a.k.a. lack of entrepreneurial spirit). I've seen several efforts to create exchange providers and adjunct branches of DGCs in European countries come adrift, and it all seems to come down to the same thing in the end: eventually the people concerned bump into, and pay attention to, the "not welcome here" sign hung up by the financial regulators.
It's almost as if the message is, "who are we to interfere with the colonialisation of Europe?"
February 11, 2004
GoldMoney hits the Tonne
Goldmoney, a DGC with strong governance and strong growth, announced it had reached a metric tonne in mass of gold in accounts. That's about $13.2m worth, or about €10.3m at today's spot prices.
It also announced 10,000 customers in 100 countries.
Goldmoney's growth has been consistent at about 4 times per year for the last year. If it maintains this rate of growth, it will take over prime position from e-gold sometime around the middle of 2004, measured by mass of gold.
Other measures - primarily the number and size of transactions - are not reported byDGCs other than e-gold, the current market leader. The provision of detailed gold bar reports and statistics is necessitated by good governance practices, something that doesn't apply so clearly to transaction statistics.
February 09, 2004
Stock Trading Attacks
Zooko O'Whielacronx wrote:
"Your paper about mutual funds, which I've only begun to look at, reminds me of an attack on a "stock market implementation in E." In my own opinion, my crack was trumped by Ralph Hartley's generalization ."
Ralph Hartley's generalization (read here) is spot on, with the caveat that the attacks apply equally to any stock exchange, rather than Mark Miller's demonstration stock exchange in particular. That's because these attacks are based on the coordination problem, and the timing aspects of stock trading dynamics. In that sense, they perfectly mirror some of the attacks that are going on in the mutual fund world today.
In the testimony/paper of a few weeks back, we said that RTGS solves these problems, although that's a generalism, and depends on the assumptions. The really important point is that the shorter the timeframe for the trade settlement, the shorter the opportunity for abuse; and the financial cryptographers in the above links came to the same conclusion.
Which makes it all the more poignant that the trading world managed to get to T+3 settlement, and stopped there. Desire to move to T+1 (we are talking one day here, not minutes or seconds) is non-existent, and opportunity for fraud remains as present as it ever was - given that most of the frauds of the mutual funds industry occurred within a one day timeframe.
January 21, 2004
Where the money is - Europe
Simon's blog picks up a Wired article on sales of Ring Tones - $3.5bn this year. The comparisons were more useful: that's 10% of the world music market of $32bn, which again is beaten by the world SMS market: $40bn.
For those who don't know what SMS is, it's IM for phones. Yes, they charge for those messages, and "That figure is expected to explode as phone users get into the habit of sending multimedia and picture messages!"
Ring Tones Bringing in Big Bucks
12:57 AM Jan. 13, 2004 PT
http://www.wired.com/news/business/0,1367,61903,00.html?tw=newsletter_topstories_html
LONDON -- Sales of mobile-phone ring tones, those tiny song recordings programmed into millions of cell phones around the world, jumped 40 percent in the past year to $3.5 billion, according to a study released Tuesday.
The worldwide sale of ring tones, which started as a marketing gimmick for music labels and mobile phone companies, is roughly equivalent to 10 percent of the $32.2 billion global music market.
Replacing the standard phone ring with a few bars from Elvis or a favorite TV show was first popularized by tech-savvy teenagers in the late 1990s.
The subsequent success of ring tones is a rare bit of good news for the music industry, which has been stung by Internet piracy and fickle fans who would rather spend their money on video games than compact discs.
The popularity is also an important revenue generator for indebted mobile-phone operators who have invested vast sums on the roll-out of 3G phone networks.
Revenues for ring tones are divided between the music labels, their artists and mobile-phone operators. The average price of a ring tone is 60 cents, according to the study by London-based telecommunications consultancy, The Arc Group.
"It's become a very profitable area and there's strong growth ahead," said Richard Jesty, an analyst for The Arc Group.
Ring tone prices vary widely by region, with SK Telecom Co, South Korea's largest mobile carrier, charging the equivalent of 20 cents while Britain's Vodafone charges roughly $2.75, Jesty said.
He forecast that sales will remain brisk through 2008 when downloads will top $5.2 billion. But as higher-power phones come on the market, consumers will turn to downloading larger files such as video games, sport highlights and short video clips.
As is the case with other forms of music, piracy is a problem with a host of small websites selling cheap music downloads without authorization from music companies.
Ring tones and games still lag well behind basic text messaging, which generated $40 billion last year for mobile phone companies. That figure is expected to explode as phone users get into the habit of sending multimedia and picture messages, Jesty said.
January 17, 2004
Adult Website Prepaid Cards
As I was walking past my local supermarket, a pleasant looking young man handed me a leaflet explaining how I could acquire "Adult Website Prepaid Cards" that would let me browse instantly without the need of a credit card - no personal information required.
I'll spare you the details (quite mild and uninteresting, especially for anyone who suffers under 100 spams a day).
The point here is that if I can be handed this near my local supermarket, this means that alternate payment systems are now well-entrenched in the "fringe" world of Adult content.
This development has been expected for years, ever since Visa and various US and other regulators launched their cleanup campaign. In some senses it is a surprise that it has taken so long; in other senses, one can understand that building an alternate payments system that works is really a tough job, above and beyond the call of your average entrepreneur. (Hats off to those who succeed.)
In a sense, those in Visa got what they desired - the cleanout of all "undesirable" businesses within their system, and the spawning of dozens of hundreds of alternate payment systems.
January 14, 2004
The Web's New Currency
http://www.technologyreview.com/articles/huang1203.asp?p=0
A new generation of e-payment companies makes it easy to "pay as you go" for inexpensive Web content, portending big profits for online businesses.
By Gregory T. Huang
December 2003/January 2004
Ask Ron Rivest if he's ever been whisked away by the CIA in the middle of the night, and he laughs-but he doesn't say no. At Peppercoin, a two-year-old MIT spinoff in Waltham, MA, the renowned cryptographer oversees an operation far less secretive than an intelligence agency but almost as intense: a clearinghouse for electronic "micropayments," pocket-change transactions that may finally allow magazines, musicians, and a multitude of others to profit from selling their wares online. It's September, and with only weeks to go until commercial launch, Peppercoin's software engineers troubleshoot at all hours. Marketing executives shout across the room and over the phone, making deals.
But in the eye of the storm, Rivest is calm and collected. Eyes sparkling, real change jingling in his pocket, he even wears sandals with authority. What Peppercoin is trying to do, he says, is make it easy to "pay as you go" for inexpensive Web content-so you won't need to pay subscription fees, limit yourself to free content, or share files illegally. With a click of the mouse-and Peppercoin's software churning away behind the scenes-you can now download a single MP3 from an independent-music site, watch a news video clip, or buy the latest installment of a Web comic from your favorite artist. All for just pennies.
It sounds simple, but it wasn't possible a few months ago. Most Web merchants still can't support micropayments-transactions of about a dollar or less-because the processing fees from banks and credit card companies erase any profit. But Peppercoin, the brainchild of Rivest and fellow MIT computer scientist Silvio Micali, is in the vanguard of a new crop of companies-including BitPass of Palo Alto, CA, and Paystone Technologies of Vancouver, British Columbia-that make cash-for-bits transactions superefficient. These companies' founders are well aware of the string of defunct e-payment companies whose virtual currencies have gone the way of the Confederate dollar. But they've got something new up their sleeves: easier-to-use technology that allows Web sites to accept tiny payments by effectively processing them in batches, thereby cutting down on bank fees.
So throw out your current conceptions of Web surfing. Rather than sifting through pop-up ads and subscription offers, imagine dropping a quarter on an independent film, video game, specialized database, or more powerful search engine. If programmers and Web artists could profitably charge a few cents at a time, their businesses could flourish. And with an easy way for users to buy a richer variety of content, experts say, the current deadlock over digital piracy could effectively dissolve, giving way to a multibillion-dollar business stream that rejuvenates the wider entertainment industry the same way video rentals did Hollywood in the 1980s. Down the road, cell phones, personal digital assistants, and smart cards equipped with micropayment technology could even supplement cash in the real world.
"The key is timing and technology," says Rivest, who thinks Peppercoin has both right. The company's technical credibility, at least, is not an issue. Rivest coinvented the RSA public-key encryption system, used by Web browsers to make credit card purchases secure. Micali holds more than 20 patents on data security technologies and won the 1993 Gödel Prize, the highest award in theoretical computer science. Their system uses statistics and encryption to overcome profit-erasing transaction fees; the approach is unique and more efficient than its predecessors.
The timing looks good, too-not just for Peppercoin, but for other micropayment companies as well. "One year ago, it was, 'Will people pay?' Now it's, 'How will they pay?'" says Ian Price, CEO of British Telecommunications' Click and Buy division, which uses micropayments to sell articles, games, and other Web content to customers in more than 100 countries. And in September, Apple Computer announced that its online music store sold more than 10 million 99-cent songs in its first four months. Apple's success was the "starting gun for a track meet of companies" planning to roll out pay-per-download services by 2004, says Rob Carney, Peppercoin's founding vice president of sales and marketing.
Indeed, 40 percent of today's online companies would sell content they're currently giving away if they had a viable micropayment system, says Avivah Litan, an analyst at Gartner Research who specializes in Internet commerce. According to Forrester Research, the market for music downloads is expected to grow from $16 million in 2003 to $3 billion in 2008. And a Strategy Analytics report states that mobile-gaming revenues could top $7 billion by 2008. "The market is ready" for micropayments, says Rivest.
Even so, getting the technology to take off won't be easy. Micropayment companies need to make their systems fully reliable, secure, and easy to use. Just as important, they need to increase demand by working with Web businesses to deliver a broader range of digital products. So on the eve of Peppercoin's commercial launch, the question is not whether the timing and technology are good. It's whether they're good enough.
In Statistics We Trust
Understanding Peppercoin requires a little history. According to old English common law, the smallest unit of payment that could appear in a contract was a peppercorn. Silvio Micali's wife, a professor of law, suggested that as the name for his startup back in 2001, and it stuck (becoming "Peppercoin" for the sake of clarity). Now, in his office at MIT's Computer Science and Artificial Intelligence Laboratory, Micali is explaining what makes Peppercoin tick. On hand are technical books and papers in neat piles, should we need them. It's simple mathematics, says Micali-but don't believe him.
Micali knows two things: cryptography and coffee. His micropayment analogies involve cappuccinos. There are two standard ways of buying digital content, he says. One is like prepaying for a certain number of cappuccinos, the other like getting a bill at the end of the month for all the cappuccinos you've had. That is, the customer either pays up front for a bundle of content-say, 10 archived New York Times articles-or runs a tab that's settled every so often. The problem with both models is that the seller has to keep track of each customer's tab, and the buyer is locked into a particular store or site. But in the spring of 2001 came a "very lucky coffee break" when Micali and Rivest, whose office is just down the hall, put their heads together. "We started discussing this problem, and within minutes we had the basic solution," says Micali. "And we got very excited! First, from the discovery. Second, from the coffee."
What they discovered was a way to cut the overhead cost of electronic payments by processing only a statistical sample of transactions, like taking a poll. On average, Peppercoin might settle, say, one out of every 100 transactions-but it pays the seller 100 times the amount of that transaction. Given enough transactions, it all evens out, says Micali
It looks simple to the buyer, who only has to click on an icon to charge an item to her Peppercoin account, but the action behind the scenes is pretty complicated. In beta tests, special encryption software runs on both the buyer's and seller's computers, protecting their interactions from hackers and eavesdroppers. And encrypted in each transaction is a serial number that says how many purchases the customer has made over time, for how much, and from whom.
Ninety-nine transactions out of a hundred are not fully processed-but they're still logged by the seller's computer. One transaction out of a hundred, selected at random, is sent to Peppercoin. After Peppercoin pays the seller 100 times the value of that transaction, it bills the customer for all of her outstanding purchases from all sites that use Peppercoin. Since about one out of a hundred purchases is processed, her last bill will have come, on average, a hundred purchases ago. That's the trick: by paying the seller and charging the customer in lump sums every 100 purchases or so, Peppercoin avoids paying the fees charged by credit cards-roughly 25 cents per transaction-on the other 99 purchases. "This is fantastic," says Greg Papadopoulos, chief technology officer at Sun Microsystems and a member of Peppercoin's technical advisory board. "Ron and Silvio have done what needed to be done-get the cost of transactions down without ripping up the existing infrastructure of credit cards and banks."
But what's to keep all this fancy statistical footwork from cheating sellers out of their due? And what's to keep buyers and sellers both from cheating the system? "That's the secret sauce," says Micali.
He's talking about cryptography, the sweet science of codes and ciphers. Its inner workings are, well, cryptic-paper titles at conferences include things like unimodular matrix groups and polynomial-time algorithms-but it's used every day to keep communications, documents, and payments secure. Roughly speaking, says Rivest, statistical sampling of transactions makes the system efficient, while cryptography keeps the random selection process fair and secure. So Peppercoin charges users exactly what they owe, and if Peppercoin's payment to the seller happens to be more or less than the value of the purchases customers actually made, the discrepancy is absorbed by the seller. Over time, this jiggle will become negligible, especially compared to the amount of money Web sites will make that they couldn't make before.
Think about it for too long, and most people get a headache. But Micali and Rivest have been thinking about this sort of thing for 20 years, so they make a formidable and complementary team: Micali is as animated as Rivest is understated, like fire and ice. "They've done brilliant work over the years," says Martin Hellman, a professor emeritus of electrical engineering at Stanford University and a pioneer in cryptography going back to the 1970s. "Peppercoin has a clever approach."
But clever mathematics aside, the proof is in the pudding. In the end, Peppercoin's executives say, their system must be as easy to use as cash. Perry Solomon, Peppercoin's founding CEO, explains it this way, pulling some change out of his pocket. "I can give you this quarter, and you can look at it quickly and say, 'Okay, that's a quarter.' You don't need to call the bank to verify it." Online merchants, however, must check a credit card holder's identity and available credit before approving a purchase. Going to that trouble makes sense for a $50 sweater or a $4,495 Segway transporter, but not for a 50-cent song. So Peppercoin's software stamps each transaction with the digital equivalent of e pluribus unum-a guarantee to the seller that it's Peppercoin handling the transaction, and that payment is forthcoming. The seller can quickly verify this stamp and deliver the goods.
Bootstrapping with Bits
The theory may be impeccable, and the founders' credentials outstanding, but how does a startup transform a micropayment system into a practical, sellable product? That's the stuff of late-night whiteboard discussions enhanced by takeout Chinese food and bad TV movies, says Joe Bergeron, Peppercoin's vice president of technology. Bergeron, a baby-faced programming whiz, has the task of translating Rivest and Micali's algorithms into software. Like any good engineer at a startup, he has spent many a night under his desk trying to squeeze in a few hours of sleep. "I'm dreaming in Peppercoins now," he says.
Minting micropayments starts with hardware. A secure data center a few kilometers from company headquarters houses hundreds of thousands of dollars' worth of computing horsepower and memory. All of Peppercoin's money transfers flow electronically through these machines. A rack of 20 processors and backups and four levels of hardware security are set up in a special cage walled off by Plexiglas guaranteed to withstand a 90-minute riot; the rental contract even specifies that the cage will repel "small-arms fire and manual tools."
First Out of the Gate
Andreas Gebauer remembers the pesky young guy well. Five times in 2000, Firstgate Internet founder Norbert Stangl showed up at the Berlin offices of Stiftung Warentest (Product Testing Foundation), Germany's leading consumer reports magazine, to peddle his e-payment technology. Five times Gebauer, the magazine's online editor, said he wasn't interested. Finally, on the sixth trip, Gebauer agreed to give it a try if Stangl would just leave him alone.
Persistence pays off. "We've been very successful," says a converted Gebauer. In the three years since Stiftung Warentest adopted Firstgate's system, its monthly online revenues have skyrocketed from $5,000 to more than $100,000. And today, while the U.S. micropayment market is still in its early stages, Firstgate has some 2,500 merchant users and almost two million paying customers in Europe-and pulls in more than $1 million a month in revenues, making it one of the world's leading e-payment and distribution companies. Its users in media and publishing, the fastest-growing market segment, include the Independent, Der Spiegel, Reader's Digest, Encyclopedia Britannica, and Gruner and Jahr.
Firstgate's software, unlike Peppercoin's, must keep track of every transaction, and most are dollars rather than cents. But it works. Web customers can go to any Firstgate-enabled site, click on an article, and read it. They are billed via their credit card, debit card, or phone bill once they accrue a few dollars in charges. The system works by fetching digital content from Web merchants and delivering it only to paying customers. Firstgate charges a setup fee for merchants and pockets 10 to 30 percent of each transaction. (That may sound steep, but for micropayments, Firstgate can be cheaper than a credit card company.) Meticulously hand-tailored, the system has won a slew of European industry and consumer awards. "It's finely tuned, like a BMW," says Ian Price, CEO of British Telecommunications' Click and Buy division, which has partnered with Firstgate to sell online games, articles, and even a voting mechanism for interactive TV shows.
Most important, Firstgate has proven that a global market exists for Internet content priced in the $1 to $10 range, says Stangl, who is now the company's chairman. In late 2002, the company set up offices in New York. How will its success in signing up newspapers, magazines, and other media groups translate to the U.S. market? "We have experience working with so many online companies," says George Cain, Firstgate's CEO in North America. "What people are thinking about here, we've already got built into our system."
But Peppercoin's system must also be bulletproof to electronic problems. Take transaction speed, for instance. Peppercoin is working with one Web site that delivers 1,000 digital maps per second. For Peppercoin to handle that many purchases, and for buyers to get their content without waiting, the behind-the-scenes computations must happen in milliseconds. As Bergeron explains, sketching a flow chart on a whiteboard, the software module that identifies what the buyer is paying for, verifies that the payment is good, and sends the digital content to the buyer has been taking a few milliseconds too long in beta tests. The solution: do these steps in parallel, and manage customer queries in a flexible way by devoting more computing resources to the steps that take longer. Trimming bits of fat like this saves precious processing time per click-and ultimately keeps the system running efficiently.
Perhaps even more crucial to Peppercoin's success, though, is its sales strategy. "The challenge isn't getting people to buy the math. It's enabling a new business model for the Web," says Rob Carney. In two respects, micropayment startups are fundamentally different from online person-to-person payment companies like Mountain View, CA-based PayPal, one of the most successful of e-payment companies. First, they are enabling Web merchants to sell low-priced digital content, not physical items. Second, they don't have anything approaching the captive market that PayPal has in the customers who use eBay, the San Jose, CA, online auction house that purchased PayPal in 2002.
So Peppercoin's plan-similar to those of other micropayment startups (see table "The Micropayment Movement,")-is to go after Web merchants, work with them to decide what kinds of content to sell, and build up a brand name with which to approach larger distributors. It's a painstaking process; Solomon and Carney have attended more than 400 sales meetings in two years, trying to persuade merchants that Peppercoin's own fees-which work out to be much lower than the flat transaction fees charged by credit cards-are a small price to pay for the extra business micropayments will generate.
But all this work is starting to pay off. "Peppercoin has been a huge benefit for us," says Rex Fisher, chief operations officer at Music Rebellion, a Terre Haute, IN, company that last June started selling 99-cent MP3s by the download, using a beta version of Peppercoin's system. The bottom line: micropayments allow the music site to triple its profit margin, as compared with traditional payment methods. As for the user interface-buyers sign up for a Peppercoin account and then click on music icons to charge songs-Fisher says he's working with Peppercoin to make it "easy and hassle free." He acknowledges that it's still early, however, and that results in the next year will say more about the overall success of micropayments.
Other users go further in their praise for e-payments as enablers of new kinds of Web content. "The promised land is filled with micropayments," gushes David Vogler, a digital-entertainment executive formerly in charge of online content at Disney and Nickelodeon. One of Vogler's current ventures is a humor site called CelebrityRants.com. There, using Peppercoin's software, you can buy animated recordings of embarrassing diatribes or confessions from celebrities caught on tape-everyone from Britney Spears to new California governor Arnold Schwarzenegger. "We explored many solutions, but Peppercoin seemed like the right horse to bet on," says Vogler. Moreover, he adds, it was "insanely easy" to get the system up and running. That and a painless consumer experience seem to be the keys to early adoption.
So this is how it starts: not with a conglomerate of media giants adopting micropayments, but with pockets of small entertainment and Web-services sites. Plenty of sites will still be free, supported by advertising, says Carney. But micropayments, alongside ad sales and subscriptions, will become another leg of the stool that supports Web businesses. And micropayment companies are hoping that their systems will give entrepreneurs and consumers the freedom to try out new kinds of commerce on the Web, and to buy and sell an ever wider variety of digital goods. "The Web was dying," says Kurt Huang, CEO of BitPass, a micropayment startup he cofounded while he was a graduate student at Stanford University. "We needed to do something to change its economics."
Take Web comics. Today there are more than 3,000 online cartoonists worldwide, and that number is growing fast, says Scott McCloud, an author and Web comic artist based in Newbury Park, CA. "Micropayments are the missing piece of the puzzle," he says. Using a beta version of BitPass's technology-users prepay a few dollars into an account-McCloud sold 1,500 copies of his comics for 25 cents each in eight weeks. Not huge numbers, to be sure, but the potential for steady growth is there. And it's not supplementary income-this is how Web artists will make their money. "We're not just slapping a price tag on what could be free," says McCloud. "This is allowing us to do work that we couldn't do before."
The Micropayment Movement
Company Technology Market/Status
BitPass (Palo Alto, CA) Costs of Web content and services are deducted from an account
prepaid via credit card or PayPal Independent artists, publishers, musicians; beta trials under way; commercial release in late 2003
Firstgate Internet (Cologne, Germany) Servers fetch Web content and deliver it to customers; charges
appear on credit card or phone bill News and analyst reports; in operation since 2000; nearly two million customers in Europe
PayLoadz
(New York, NY) Delivers digital items via e-mail after users have paid using PayPal Electronic books, music, software; commercial release in May 2002;
9,600 sellers signed up
Paystone Technologies
(Vancouver, British Columbia) Customer accesses Web content after paying via bank account Music, publishing; commercial release in May 2003; 700 sellers signed up
Peppercoin
(Waltham, MA) Uses statistics and encryption to process a sample of transactions; users pay via credit card once per 100 or so transactions Music, games, publishing; commercial release in late 2003
The Coin-Op Web?
In the 1990s, e-payment startups like DigiCash, Flooz, and Beenz crashed because dot-com companies didn't think they needed the technology to make money, and because consumers expected Web content to be free. Times have changed, but there are still plenty of skeptics who doubt micropayments will catch on broadly, considering that MP3 listeners and Web-comics fans are the technology's main U.S. consumers so far. Even those who have made their fortunes in the online-payments world acknowledge that it's an uphill battle. "It's quite possible they could fail miserably in this economic climate," says Max Levchin, cofounder and former chief technology officer of PayPal (see sidebar "The PayPal Precedent").
But both the supply of digital content and consumers' willingness to pay for it are increasing, and the micropayment companies' strategy of signing up Web merchants, one at a time, has promise. "There will be small companies who figure out how to play this chicken-and-egg game," says Andrew Whinston, director of the Center for Research in Electronic Commerce at the University of Texas at Austin. "The key is to become successful before big companies like Microsoft get into it."
The PayPal Precedent
Max Levchin believes that micropayment companies' two keys to success are a simple user interface and an aggressive distribution strategy. TR's 2002 Innovator of the Year, Levchin is the cofounder and former chief technology officer of PayPal, the online-payments pioneer that was sold to eBay for $1.5 billion in October 2002.
Technology Review: Are micropayments ready to take off?
Max Levchin: The Apple music store is a good example that 99-cent payments are a reality. What is uniquely different about the market now is that personal publishing has become a lot more pervasive than it was three to five years ago. There are literally thousands of Web sites that specialize in comics, music, and art that's only available on the Internet. [Artists] look to the Internet to actually make money. So demand is definitely increasing. The question is, are these solutions actually what the market needs?
TR: What do Peppercoin and other micropayment startups need to do to become successful?
Levchin: Most of the technical challenge is about the user interface, not the billing process. Overall, Peppercoin's [beta version] user interface is very raw. I have to download software. I have to wait for a confirmation e-mail. What if my computer crashes? You should never force people to download software. The security is a good thing, but it adds complexity.
TR: What's the greatest challenge, going forward?
Levchin: The biggest difficulty, by far, is distribution. How do you get all these people to start using the system? At PayPal, as soon as we "infected" a couple popular eBay merchants, very quickly we saw this massive growth, where buyers started pushing other merchants to sign up. But there isn't a giant market online right now where you can go to look at all digital content available. Digital merchants are very disparate. And consumers aren't going to sign up, download software, or prepay for a card, because there are not that many places to spend it yet. So marketing to digital merchants directly is one way to go. But it will take an incredible amount of human effort to get enough people to sign up.
For a glimpse into the future of micropayments, look overseas. In Japan, most mobile content and services, such as cell-phone users downloading games and ring tones, are paid. And micropayments are becoming prevalent in Europe's publishing and news-media markets. Firstgate Internet, a digital content distributor in Cologne, Germany, has nearly two million customers and 2,500 clients, including British Telecommunications' Click and Buy, and it is bringing in more than $1 million a month in revenues, says founder and chairman Norbert Stangl (see sidebar "First Out of the Gate"). Its most successful kinds of low-price content: news, research articles, and financial reports.
But Firstgate tallies each purchase separately and pays credit card fees, so its own fees are higher for merchants than most micropayment startups'. Peppercoin and BitPass hope to succeed in the U.S. market by being more efficient for small payments. So will micropayments take off here? "The truth is, nobody knows," says Guy Kawasaki, CEO of Garage Technology Ventures, a venture capital firm that is funding BitPass. "But I look around and I see 50,000 unsigned bands in the world. I see thousands of bloggers, analysts, and artists who want to publish their stuff. And how many databases would you want to search for 50 cents?" Asked when he expects to see a return on his investment, the former Apple guru laughs and says, "Before I die!"
Other observers see a clear path to adoption. "The future of micropayments is very simple," says Sun's Papadopoulos. "You'll get to a critical mass on the network. It will become the equivalent of pocket change, and you'll see fierce price competition on digital content." Falling prices, companies hope, will only increase demand. And as digital content gets cheaper, the temptation to pirate should diminish.
We're already seeing competition: last summer, the music-download store BuyMusic.com put up billboards parodying Apple's music ads and undercutting Apple's 99-cent pricing by selling songs for as little as 79 cents. With America Online, MusicMatch, and Roxio (Napster 2.0) launching stores as well, the music industry will be a proving ground-or perhaps a killing field-for e-payment technologies.
As the contest begins, most micropayment startups have enough capital to see them through the rollout phase. In September, Peppercoin announced that it had raised $4.25 million in its second round of venture funding. But in the long run, how will micropayment companies stay in business? Signing up Web merchants is fine now-deals are quick and the need is there-but an eventual goal is to hook up with a distributor that will become the eBay of bits.
So as Peppercoin makes final preparations for its commercial launch, Carney and Solomon make sales calls. Engineers sit on the edges of their seats, watching the ebb and flow of processing loads and user levels on their monitors. Rivest and Micali, ever patient, stay out of the limelight. If victory arrives, it won't come thundering out of the sky. For companies like Peppercoin, success will build up gradually, like coins clinking into a piggy bank, one by one.
The Fraud of Insider-Trading Law
A couple of articles on Insider Trading by Sheldon Richman : first part is an analysis of the Martha Stewart case . Second part is a broader look at the concept of Insider Trading .
Is Insider Trading good? Or bad? Here's some personal comments...
It's a tricky question. On the face of it, Insider Trading is a straight out-and-out fraud. An insider has internal information that will - in the insider's opinion - cause the stock price to move. So, she buys or sells ahead of the move, and takes the profits.
This is a straight fraud because it takes money from the shareholder base. The shareholders are poorer because they did not enjoy the benefits of the change in price. Of course, this assumes that an insider cannot also be a shareholder, and therein lies the conflict of interest: an insider has a fiduciary duty to shareholders, which may be breached if acting on the basis of own shareholdings.
However, the real issue that is at the heart of this fraud is that, economically, it's pretty nigh on impossible to detect and prosecute. In practical terms, the information is a) in the heads of the insiders, b) subject to misinformation constraints as much as any market noise, and c) hard to determine as being "inside" or "outside" some magic circle.
Thus in purely transaction cost terms, making Insider Trading illegal is a very difficult sell. It's a bit like the Music intellectual property debate: songs became property when records were invented, because it was now possible to control their sales by following the shellac and the pianola rolls and sheet music. Of course it took a few decades for this to shake out.
Songs lost their property characteristics with the invention of the personal MP3 player, and we are into the first decade of shaking out right now....
December 23, 2003
Microfinance Impact Assessments
http://www.wws.princeton.edu/~dkarlan/downloads/impactperils.pdf
Microfinance Impact Assessments: The Perils of Using New Members as a Control Group
Microfinance institutions aim to reduce poverty. Some assess their impact through a cross-sectional impact methodology which compares veteran to new participants, and then calls any difference between these two groups the "impact" of the program. Such studies have risen recently in popularity because they are cheap, easy to implement, and often encouraged by donors. USAID, through its AIMS project, encourages this methodology with its SEEP/AIMS practitioner-oriented tools1. This paper intends to inform practitioners about the perils of using such a strategy, and suggests a couple solutions to some of the larger problems with this approach.
This approach makes many assumptions that are untested, and others that are tested and false. For example, this approach assumes that dropouts have, on average, identical income and consumption levels to those who remain. Furthermore, this approach assumes that dropouts are not made worse off by participating in the program. This approach also assumes that when lending groups form they do not sort themselves by economic background. These assumptions not only are brave theoretically, but are contradicted by existing empirical research. This paper suggests a method to address the attrition biases, and suggests further research be conducted on the other implicit assumptions before expending resources on a plausibly unreliable assessment
methodology.
November 25, 2003
Scaling up Micro Financial Services: An Overview of Challenges and Opportunities
This paper attempts to examine specific issues in the delivery of micro financial services and outlines some new approaches towards scaling up. Section I reiterates the crucial role of micro finance in reducing vulnerability and enhancing the prospects of growth for poor households. Section II examines the broad challenges in micro finance; Section III provides an overview of the various micro financial services (insurance, savings and investment, credit and other risk management instruments). Section IV examines the issues specific to Micro Finance Institutions (MFI) in India and Section V concludes the paper by identifying the key areas for further research and debate.
November 12, 2003
High Frequency Data - an Essential Resource
http://www.olsen.ch/center/papers/essentialresource.pdf
Analysis of economic trends and research of economic processes requires access to quality data. Big investments have gone into building extensive databases of macroeconomic data. So far, high frequency or tick by tick market data has not been included in these efforts. Traditionally, economists have been of the opinion that short-term price fluctuations are irrelevant noise and not worthwhile to collect. Recent discoveries in finance have changed this assessment [1]. High frequency data has a high information content and is indicative of long-term trends. This is a plea to expand data collection to high frequency market data as an invaluable source of information.
During the course of the past 20 years, there has been a growing interest in the study of high frequency market data. A rich structure of statistical properties was discovered. Unlike long-term macroeconomic data, which is known to have Gaussian distribution properties, high frequency market data is non-stationary and increasingly fat-tailed over shorter intervals. It has also fractal properties. It is subject to a scaling law, where the average absolute price change increases by the same percentage from a ten to a twenty minutes interval, as from a one to two hour, or a one to two days or one to two month interval. Absolute price changes exhibit long-term autocorrelation properties, where a price shock lasting for only twenty minutes for example has an impact for six or more weeks. There are other properties as well, such as a 24 hour volatility pattern, which is the result of the three time zones of trading in Asia, Europe and America. Classical economics assumes that financial markets are homogeneous and that short-term price movements follow a Gaussian random walk. The complex structure of statistical properties discovered with high frequency data is the result of the heterogeneity of financial markets2. Market participants trade with different time horizons, some take positions for only minutes, others for hours, days, weeks or months. Depending on their trading horizon, they react differently to the same news events. The heterogeneity has the effect of creating a strong temporal interdependence of price moves.
With modern mathematical tools it is possible to analyze high frequency data and extract information of long-term trends and trend changes. We propose to expand data collection and create a global tick by tick market data repository. This repository would also include - synthetic data - for data that is not directly observable, such as yield curves and volatility surfaces. Today, there exists no commercial database that fulfills this task. It has been estimated that such a project would cost anywhere between 10 and 50 Mio USD.
Its usage would be manifold. First of all, it would provide us with a detailed record of how events unfolded. For historians, economists and finance specialists, it would be an invaluable resource to understand the history of events and get a deeper understanding of the diversity of phenomena that occur. Research of market liquidity would play a prominent role. Transparent and liquid capital markets constitute a "public good", which can only be safeguarded, if we have a deeper understanding of how the markets function.
The tick data time series repository could be used to feed a global early warning system that would operate similarly to a weather forecasting system providing predictive information of financial markets and the economy as a whole. Unlike existing market analysis which is fed by macroeconomic data that has a time delay due to the sparse underlying data, the global early warning system would be online and up to date. At the same time, the data repository could fulfill straight forward tasks - it would allow financial institutions to validate the transaction prices of their complex derivatives transactions by an independent third party resource and prevent losses, such as occurred with Allied Irish Bank.
-------------------------------------------------------------------------------------
1 An Introduction to High-Frequency Finance. Michael M. Dacorogna, Ramazan Gençay, Ulrich Müller, Richard B. Olsen, and Olivier V. Pictet. San Diego, CA:Academic Press, 2001. 383 pp., ISBN: 0-12-279671-3
2 Olsen, R. (2000). The Fallacy of the Invisible Hand, in Visions of Risk, edited by Carol Alexander, Pearson Education
November 04, 2003
War Against the Dollar, the Pillar of United States Power
Thierry Meyssan writes a useful summary of the "most optimistic" or the "most pessimistic" case against the dollar, depending on which side of the geo-politico-economic divide one falls. In essence, the move to switch away from the dollar as international unit of account is gaining some momentum. Perhaps surprisingly to some, the notion of an islamic gold unit is also making some ground, so it may be that there are is a triumvurate of currency stability in earth's future:
Dollars, Euros, and gold.
What's this got to do with anything? In essence, money is an application of FC. Only in understanding the way the world is looking at - and pushing - money, can we understand how a new money project might unfold.
(Ed: I added an emphasis to stress the prediction within [and 2004] now confimed in 2006, 2006-2 and 2008)
(interesting but non-financial geopolitical backdrop - snipped, see URL)
War Against the Dollar, the Pillar of United States Power
Whatever happens, Washington can no longer backtrack. In fact, the survival of the U.S. is menaced - not by an external enemy, but by internal economic weakness and tensions running between its communities. Many are becoming conscious of the fact that U.S. power is based upon a mirage, the dollar. These are only pieces of paper, printed when more are needed, while the rest of the world feels obliged to use them.
For the past three years, Jacques Chirac and Gerhard Schroder have engaged France and Germany in a pitiless war against the United States. They have sent emissaries world wide to convince other States to convert their monetary reserves to euros. The first to accept were Iran, Iraq and North Korea. Precisely the countries described by George W. Bush as those of the "axis of evil".
Meanwhile, Vladimir Putin has begun restoring the economic independence of the Russian Federation. He has reimbursed - ahead of time - the debts that Yeltsin had contracted with the International Monetary Fund and will also make an early repayment, before the end of the year, of the remaining debts to the Club of Paris.
Putin has calmly announced that he plans State control of the natural riches of his country. He has reminded others that the oligarchs made their fortunes overnight by appropriating, with the complicity of Yeltsin, all that belonged to the U.S.S.R. and that the State can demand the return of wealth which should never have been handed over to the oligarchs.
When Gerhard Schroder visited Putin at the beginning of October, Putin intimated that he would begin by regaining control over Russian gas and petrol and that he would convert their trading, now in dollars, to euros.
On his part, the Prime Minister of Malaysia, Mahatir Mohammad, has experimented with the abandonment of the dollar in international exchanges, but in order to replace it with gold. He has signed bilateral agreements with his country's business partners. Malaysian exports and imports will in future be traded in gold.
Buoyed by this, he has suggested to the Islamic Bank of Development a plan that would put an end to U.S. dominance. Inspired by the Arab cartel which created the oil shortage of 1974, he has outlined a decisive monetary assault. The idea is to switch world petrol trading to gold, thereby provoking the fall of the dollar and the collapse of the U.S. economy.
At first, Saudi Arabia, menaced by Washington neo-conservatives, was opposed to this plan, but became agreable to it. The Islamic Bank of Development presented the proposal at the summit meeting of the Organisation of the Islamic Conference (OIC) which was held recently in Malaya, presided over by Dr. Mahatir Mohammad. It was agreed that bilateral agreements for a transition to the gold standard would be prepared between Islamic countries, during the course of next year. At the next summit meeting, to be held in Senegal, the fifty-seven Member-States of the Islamic Conference would be invited to sign a multilateral agreement.
Vladimir Putin who also attended the Islamic Conference, since a large number of the citizens of the Russian Federation are Muslims, encouraged the plan.
Abandoning the dollar presents a long and difficult struggle, for Europe as well as for Muslim countries. While an international campaign accusing Dr. Mahatir Mohammed of ressuscitating anti-semitism has been launched, Henry Kissinger and Condoleeza Rice appealed to the oligarch, Mikhail Khodorkovsky, for help in order to neutralise Putin. Last weekend, however, Putin had him arrested and detained.
Whatever happens, the monetary war has been declared. In the short-term, U.S. domination is menaced.
Thierry Meyssan
Journalist, writer and President of R\xe9seau Voltaire
http://www.reseauvoltaire.net
October 27, 2003
Economists explore betting markets as prediction tools
Over at Science News Online, Erica Klarreich writes of markets as tools for prediction:
"During a highly charged week in Washington, D.C., last July, a research project sponsored by the Department of Defense sparked a furious outcry from prominent politicians and was then hastily axed by the Pentagon. The project, known as the Policy Analysis Market (PAM), was to have been a market in which participants could wager on Middle East events, say, the gross domestic product of Syria in coming years or the political instability of Iran. The project's developers, however, had made a public relations faux pas. On their Web site, they invited participants to suggest additional topics for markets and speculated that those suggestions might include terrorist attacks and political assassinations. Critics labeled the project a "terrorism futures market" and denounced it as morally repugnant and grotesque."
The PAM "doh!" is just the lead in to a nice article on non-conventional markets.
http://www.sciencenews.org/20031018/bob9.asp
October 23, 2003
Breaching those Barriers to Entry
One of the regrettable truths in this business of FC is the scant regard that entrepreneurs give to barriers to entry. These barriers start out large, get huge and huger still, generally as people skip the analysis steps that outline these barriers.
One of the barriers is institutions. They fear loss of payments, and their existance must be considered in the plan.
In general, it is very hard to include existing institutions and share the benefit, and that means having to compete with them at a later time. But, there are exceptions to this, and it now seems that - throwing all theory aside, at least in one case, a group of institutions has actually cooperated and launched a big payment system.
Even more surprising, the group includes banks, credit card companies, and telcos!
The story is almost a textbook case of the impossible:
http://www.iol.co.za/index.php?click_id=115&art_id=qw1066093560707B264&set_id=1
Here's an excerpt:
"Getting the payment-by-phone idea off the ground was not easy. It required co-operation from three industries that don't always see eye-to-eye - banking, credit cards and telecommunications."
"Park said executives laughed at him when he first approached credit card companies - with a TV remote strapped to his cell phone to demonstrate how it would work."
"Credit card companies were loath to co-operate so closely with telecoms because that would require sharing valuable customer information and transaction commissions."
"The card companies figured they already had the entire country in their grip, with an average of four cards issued for every working person. But after extended negotiations, they finally agreed, acknowledging the inevitable march of technology."
"The mobile phone companies, on the other hand, were hungry for new services. Their markets were saturated. All three major providers are now on board."
October 17, 2003
[Mises] Carl Menger: The Nature of Value
http://www.mises.org/fullstory.asp?control=1349
By Gene Callahan
[Posted October 17, 2003]
Somewhat ironically, it was one of the greatest philosophers who has ever lived, Aristotle, who was perhaps most responsible for steering the discipline of economics down a false trail. Since the time that he expounded his views, economics has been struggling to rid itself of Aristotle's first, false step.
Consider the following passage from the man known in the Middle Ages as "the philosopher":
"Money, then, acting as a measure, makes goods commensurate and equates them; for neither would there have been association if there were not exchange, nor exchange if there were not equality, nor equality if there were not commensurability." [1] (All emphases mine.)
Aristotle posits that if there were no common medium of exchange (money) that could determine equality-presumably of value-between goods, then there would be no market exchange, and, indeed, no association of humans beyond the scope of the household.
If, as per Aristotle, money serves to "measure" some "equality" between goods and exchange depends on the ability to establish such equality, then it follows that this equality must exist prior to exchange. Goods themselves must possess some property that makes seven of good X equal to three of good Y. If that is the case, then economists ought to search for the factor by which certain quantities of certain various goods can be declared equal to each other.
The two most obvious places to look for such a factor were in human effort and natural bounty. Relatively early in the history of economics, Sir William Petty (1623-1687) proposed a theory of value that relied on both of these factors. According to Petty, "all things ought to be valued by two natural Denominations, which is Land and Labour." [2] Karl Marx, among others, famously based his value theory on the amount of labor that went into a good. If the worker did not receive 100% of the final price of a good he made, he was being "exploited."
The problem with all such efforts to conceive value as dependent on some "objective" factor is that they are viciously circular. If the value of a flute depends on the labor that went into constructing it, then how do we determine the value of that labor? If the value of a head of lettuce depends on the value of the land that produced it, then how do we explain the value attached to that land?
Marx himself recognized, but didn't resolve, this difficulty. He understood that someone who labored all day vigorously smashing chairs could not expect the same pay as someone who worked building them. He declared that it was only "socially useful" labor that determined value. But how in the world could we characterize "socially useful" labor other than by the fact it produced "socially useful" things? In other words, we are still stuck in a circle, explaining the value of goods by the labor that went into them and the value of that labor by the goods it produces.
It was perhaps the Austrian economist Carl Menger who was most responsible for diverting economics from this barren path, although certainly he must share credit with William Stanley Jevons and Léon Walras, who arrived at similar conclusions as Menger almost simultaneously.
Despite his intellectual roots in Aristotlean thought, Menger was wise enough to see that Aristotle had erred in regards to exchange. One can make no sense of the relationship of value to market prices if one regards value as a property of goods themselves. Since the properties posited as "inhering" in goods, such as land and labor, are themselves traded on the market, such explanations must always beg the question as to how those "determinants" of value are priced.
Menger's breakthrough insight was to realize that "[v]alue is? nothing inherent in goods, no property of them, but merely the importance that we first attribute to the satisfaction of our needs... and in consequence carry over to economic goods as the? causes of the satisfaction of our needs." (Principles of Economics)
In other words, value is the name of an attitude or disposition that a particular person adopts toward a good: he chooses to value it. Although Menger set economics on the path to a correct theory of value in 1871, ancient errors die hard. We can still find many erroneous conceptions of value in contemporary discussions of economic issues.
For example, it is quite common to refer to money (or gold, or financial assets) as a "store of value." But an attitude cannot be stored! You cannot pour some of your attitude towards goods into a bar of gold, put it in a vault, and hope it "keeps." You can, of course, store the gold bar. And you will certainly hope that when you decide to take it from the vault and sell it, that others will choose to value it as well. But only the gold was stored.
Money is also referred to as "a measure of value." But if, following Menger, we regard valuing as an attitude people take towards things, then money certainly cannot measure value, since money itself is simply another thing that people choose to value (or not). Rather than "measuring" the value of other goods and services, money itself is valued by human actors based on its adequacy as a commonly accepted medium of exchange.
Another common, troublesome phrase claims that in free markets, people "trade value for value." But if we realize that value names an attitude or disposition, we see that the phrase is misleading. I can trade some gold that I value with you for a sheep you value. If such a trade takes place, you must also value my gold and I your sheep. In fact, you must value my gold more than you value your sheep, and I must value your sheep more than I value my gold.
When we exchange these goods, my attitude toward the gold does not transfer to you with the gold, nor does your attitude toward the sheep become mine. If that occurred, we would wind up immediately trading them back again, since before the first trade you valued the gold I was offering more than the sheep, and I valued the sheep you offered more than the gold I made available.
In fact, there is nothing fishy about my trading something I don't value at all for something you have that I do value. Perhaps I have a painting I consider awful, and I am about to throw it away. But you visit and upon seeing it exclaim: "What a great painting! I'll give you $100 for it."
Now, it might be charitable of me to say, "No, just take it." But it is not immoral for me to accept the money. Lest anyone think that the idea that it is not dishonest to profit from such a deal is a recent product of "bourgeoisie mentality," see Sir Lionel Robbins noting:
"Saint Thomas says that if a merchant arriving at a place of dearth, knowing that there are merchants, let us say, a week behind him who are due to arrive at a place of dearth and who will bring the price down, he is not committing a mortal sin if he sells at the prevailing price in the place of dearth-although Saint Thomas adds that it might be more virtuous if he revealed that there were other chaps speeding along about a week behind." [3]
The error contained in the idea of "trading value for value" is closely related to the notion that goods should sell for close to what they cost to produce. If I sell a computer program for far more than it cost me to make it, many people would call my price a "rip-off." After all, if exchanges properly take place when the "exchanged values" are "equal," then any profits earned by one party to the trade must be illicit.
We see this idea in "cost-plus" pricing to set utility rates. Of course, this tempts utility executives to drive up costs in order to charge higher rates, since some of those costs can be perks for themselves. This is known as "padding the rate base." Regulators have tried to allow only "reasonable" costs, but that raises the issue of how regulators are to gauge better than company executives what is a reasonable expense.
The subjective nature of the value of consumer goods extends to all of the layers of producer goods. Producer goods are priced according to the estimated value of the consumer goods they might produce. It is true that products requiring high-priced inputs will generally command a high price themselves. But that is because, unless a product can fetch a high price, producers will not use expensive inputs to make it. If people value diamonds highly for jewelry, no one will consider using them for ordinary windows, even if they might work well for that purpose. It is not the fact that diamonds are expensive that makes diamond rings expensive; it is the fact that people value diamond rings highly that makes diamonds expensive.
Wine producers place a high value on Napa Valley vineyards because consumers place a high value on Napa Valley wine. If they did not, real estate there still might be expensive, but it would be devoted to housing developments or something else other than vineyards. If the wine were lousy, no producer could expect a high price for it just because his land cost a bundle!
Consumers just don't care how difficult it is to manufacture a product. They care how much satisfaction they will get from it. It would be very difficult for me to write articles while holding my breath underwater, but that will not up the fee a magazine or website will pay me for an article. Of course, I might turn the process itself into a spectacle or show, but in that case I'd really be selling the spectacle plus the article.
So, in conclusion, let me ask: is there anyone out there who will pay me extra for underwater economics writing?
Gene Callahan is author of Economics for Real People. Send him MAIL, and see his Mises.org Daily Articles Archive.
October 09, 2003
Getting Out in Front of Financial Privacy
http://www.glenbrook.com/opinions/financial-privacy.html
Momentum towards stronger financial privacy for consumers in the United States has picked up a lot of steam over the last 30 days. While most welcome the change, some financial institutions are still tentative about the new direction, others are actively resisting it, and a few are not sure how to respond. But to strategic thinking institutions wanting to secure competitive advantage, we believe that now is the time to act-getting out in front of the financial privacy issue, leveraging their reputations for trust, and better serving their customers in the process.
How Did We Get Here?
The recent seeds for strengthened financial privacy were planted in 1999 when the U.S. Congress passed the Gramm-Leach-Bliley (GLB) Act. Conceptually, GLB relaxed the artificial walls between the banking, insurance, and security industries-effectively allowing a single entity to offer financial products from all three categories to customers. While not central to the act, significant financial privacy rules were also enacted, effective in 2001, that required that any financial institution that wanted to share non-public customer information with third parties to give customers an opportunity to opt-out, or block, their information from being shared.
The opt-out approach was a classic political compromise, of sorts, enabling individuals on the privacy fringe to limit how financial institutions use customer information, but was cumbersome enough to simply be ignored by most convenience-oriented customers. Significant in retrospect, GLB also gave states the right to enact even stronger financial privacy, if they saw the need and could muster the votes to pass such legislation at the state level. Several states have gone that extra mile-North Dakota, Vermont, New Mexico, and now California-to do so.
Of the state-level legislation enacted in the last few years, the just-signed California Financial Privacy law goes the furthest, extending to customers the ability to opt-out of information sharing among even affiliated companies (within the same holding company) and requiring financial institutions to have explicit customer approval, or opt-in permission, before sharing financial information with third parties. While most analysts have focused on the back and forth power struggle between partisans, in a practical sense the adoption of opt-in requirement means that strong financial privacy is the default in California beginning next July.
Financial services industry critics of privacy regulation say these state-level laws limit customer choice (by restricting the downstream offers of secondary products to consumers), increase cost (relative to revenue), and lack any consistency from state-to-state (which is true enough). Proponents say these are orthogonal arguments and are just the cost of adequately securing sensitive customer information.
In addition, federal regulatory agencies recently released for comment proposed guidelines that would require financial institutions to notify customers (under certain circumstances) if they discover unauthorized access to sensitive customer information, such as social security number, username, or password. California enacted legislation last year that effectively requires any such disclosure be communicated to any affected California citizens.
What Changed?
Why is "business as usual" in the financial services industry suddenly under assault on both the legislative and regulatory fronts? Simply stated, people are a lot more sensitive to privacy issues and abuses. This came through loud and clear in an April 2003 Harris Interactive survey of U.S. adults:
10 percent of those surveyed were "privacy unconcerned"
64 percent of those surveyed were "privacy pragmatists or people who are concerned about their privacy and want to protect themselves from abuse or misuse of their personal information by a government organization or a company"
26 percent of those surveyed were "privacy fundamentalist who believe their privacy is eroding and are trying their best to halt the process"
When 9 out of 10 bank customers say they are concerned about privacy, something very important is changing the marketplace. When one out of four customers identify themselves as "privacy fundamentalist", the genie is truly out of the bottle.
We suspect that what's really behind this dramatic shift in attitude-especially as it relates to financial services-is the dramatic increase in identity theft. Gartner reports that 7 million U.S. adults, or 3.4 percent of U.S. consumers, were victims of identity theft during the 12 months ending June 2003. The identity theft problem has become wide enough that many people, if not victims themselves, know someone else who has already been victimized.
It's also worth noting that the shift in attitude about privacy is not focused just on the financial services industry. The Health Insurance Portability and Accountability (HIPAA) Act of 1996 addressed many of the same issues with respect to sensitive medical records and personal health information.
Its Not Over Yet
While the changes to date have been dramatic, collectively we are still in the early stages of establishing a national policy in the U.S. towards financial privacy. Several large financial institutions are still publicly opposed to the recent California Financial Information Privacy Act and reserve the right to fight it through the court system. Others hope to lobby behind the scenes to influence the upcoming revision of the Fair Credit Reporting Act (FCRA) to overturn some of these state-level protections and to pre-empt local jurisdictions from enacting any broader financial privacy laws.
While it's hard to project the final outcome, it is clear that these efforts-if pursued-are flying in the face of what the average person wants and will likely paint financial service providers as anti-consumer. While not the end of the world, such a stance could erode much of the hard-won trust that financial institutions have earned from customers.
Unlike marketing costs, it's hard to place a direct monetary value on trust. Participants in other industries would love to have the same level of consumer trust as financial institutions. But they don't and they're not likely to ever earn it. Holding on to this trust will be especially critical as banks and other financial services companies move forward in the coming years to leverage new technologies and introduce new services. In the area of biometrics, for example, early deployments show significant cost savings for financial institutions-but achieving those benefits will require convincing consumers their personal biometric data is private, secure, and never available for sale or misuse.
Recasting the Problem as an Opportunity
Consumers are saying loud and clear they want and value strong financial privacy. Financial institutions should give it to them and take credit for it. Don't offer consumers financial products-offer them "privacy enhanced" financial products. Don't just provide strong financial privacy in four states-provide it universally across the institution's complete geographic footprint. Don't just give consumers the minimum privacy required by law-protect them in ways they wouldn't even dream about.
Easier said than done? Here are some ideas:
Privacy Policies. Explain privacy policies in everyday language that anyone can understand. Don't make the policy read like a contract addendum in six-point type; instead be real clear about not selling, renting, or sharing private financial information without explicit consumer consent.
Online Banking Site. Financial institutions could provide easy access to do-not-call registries and credit bureaus from their own online banking sites-and provide help and guidance to consumers wanting to utilize them. By helping customers proactive fight identity theft and frivolous direct marketing, institutions can reinforce the strong trusted reputations they already enjoy.
Credit Card Enhancements. Much like travel accident insurance is included as a credit card enhancement, financial institutions could provide identity theft insurance at no cost to the customer as another built-in card enhancement. There are distinct first mover advantages to making this move.
To the extent other financial institutions drag their feet-waiting until the last possible day to provide the minimum compliance required by law, and fighting even that in court-the savviest institutions will begin to provide strong financial privacy now, integrate it into their branding, and use it to differentiate themselves from competitors. As Harry Truman might say, the time has come to "get out in front of it and call it a parade."
And who knows, maybe privacy-concerned consumers will jump ship and move their business to privacy-friendly financial institutions. With strong financial privacy gaining momentum, what's for sale won't be my sensitive financial information-it will be my loyalty, my trust, and my business (and associated profits) to a financial institution that earns it.
October 07, 2003
Making microfinance work in the Middle East and Africa
http://www.enhyper.com/cgi-bin/jump.cgi?ID=1173
What is microfinance and why is it
important?
Microfinance programs provide financial services - such as credit, deposit, and savings services-to the entrepreneurial poor that are tailored to their needs. Good microfinance programs are characterised by:
* Small, usually short-term loans, and secure savings products.
* Streamlined, simple borrower and investment appraisal.
* Alternative approaches to collateral.
* Quick disbursement of repeat loans after timely repayment.
* Above-market interest rates to cover the high transactions costs inherent in microfinance.
* High repayment rates.
* Convenient location and timing of services.
There are many types of microenterprises. At one end of the spectrum is, for example, the woman who sells vegetables. She operates her microenterprise for just a few hours a day because she has other responsibilities, such as taking care of her children. At the other end of the spectrum is the small enterprise that employs several workers. Though microenterprises create jobs and
contribute to GDP, they are often constrained by lack of access to financial services.
Providing financial services to the entrepreneurial poor increases household income, reduces unemployment, and creates demand for other goods and services-especially nutrition, education, and health services.
September 24, 2003
Peppercoin lacks spice
Peppercoin, a venture by Ron Rivest and Silvio Micali to monetarise certain token money ideas based on statistical settlement, raised some money ($4 million on top of $1.7 million).
This is a standard crypto-hype-venture capital-DRM play. The crypto is cool, the people are the doyens of the cryptography field, and the market is open. What more perfect combination?
But, this is no new money venture. It is striking in its ignorance. Peppercoin ignores all the lessons of the past, in so complete a fashion, that one wonders what they were thinking?
It has been very clear since about the late 90's that the retail model is bankrupt. Both Paypal and e-gold - the two successful money models so far - cracked this problem in innovative ways. Yet Peppercoin decided to ignore their work and go back to the merchant-consumer model.
It's also been more or less clear that the downloaded client model is also a dead loss. I personally have been guilty of belatedly recognising that, and in the late 90s we rectified at least our understanding, if not our technology line. (The XML-X project was our answer to that.) There are ways to make the downloaded client model work, but they require integration with the application in a way that is decidedly absent in the peppercoin model.
A further delito is the micropayments trap. Simple mathematics will show that micropayments don't work. Simply take any given merchant, and calculate the most possible number of transactions, multiple by the low amount of each transaction, then work out how much revenue you got. Digital and IBM already discovered this at a cost of countless millions, and you can too, with a $5 pocket calculator.
The only thing left is that Peppercoin has some sort of secret weapon. Always possible, and always unlikely. Except them to raise another round, and then get absorbed somewhere and quietly forgotten.
September 16, 2003
Auction Types
Seen on the Agorics Site: One of the best ways to allocate goods and/or resources is to sell them using free market techniques and ideas. An auction is an excellent method of distributing goods to those who value them most highly. Auctions, however, are far more complex than most people realize.
Kate Reynolds has developed a series of articles for Agorics, explaining different auction types and some of the issues important in determining whether to use auctions and, if so, which kind. What exactly is an auction? You may think you already know. Then again . . .
http://www.agorics.com/Library/auctions.html
Copyright 1996, Agorics, Inc.