April 22, 2006
News and Views - Mozo, Elliptics, eBay + fraud, naïve use of TLS and/or tokens...
Firefox, the free open-source Web browser from Mozilla Corp., quietly gained enough users in March to finally grab 10% of the Web browser market, according to a report released yesterday by Web audience-measurement firm NetApplications.com.
Funny, I thought that happened long ago.... On the even better news front, Frank Hecker is now posting weekly diaries of action at the Mozilla Foundation. This is an excellent idea, as they are stuck between a rock and a hard place - a non-profit with lots of money and no obvious way to govern it. Here's a snippet of some relevance to FC but the real news is that Mozilla do seem to be taking the search for governance seriously. A snippet:
PKI R&D Workshop. I attended the PKI R&D Workshop at NIST in Gaithersburg MD, and participated on a panel discussion on browser security. Note also that Bob Relyea of Red Hat spoke about work by Red Hat and Sun to support elliptic curve cryptography in the NSS crypto library and hence in Firefox and other Mozilla-based products, as well as in server products from Red Hat and Sun. For more information see Bob's presentation; the rest of the workshop presentations and papers are also available online.
Presumably Red Hat and Sun are interested in supporting the NIST Suite B because of potential USG sales. It will be interesting to watch how this falls out - will the endorsement of NIST (and in the background, the NSA) push elliptic curve cryptography forward to adoption? Or will the patent free (and therefore cheap) alternatives we already have maintain their open dominance?
A great post by Cubicle on fraud over at eBay. He talks about how the company has drifted and postured to the point where they are now providing infrastructural support for scammers - because it is the scammers that pay their fees.
The mere existence of “Second Chance” is interesting because it indicates to me that ebay has significant enough outtrade and settlement risk issues that they’re losing a significant number of sellers, so they’ve created Second Chance as a mechanism to help sellers better mitigate settlement risk. Unfortunately, they’ve tilted the balance in favor of unscrupulous sellers in the process.Look at the risks of Shill Bidding from the seller’s perspective. If they get too greedy, they will exceed the limit of their bidders and wind up “winning” their own auction. This costs them whatever the listing fee on the item was and they still have to re-list (and re-pay the fee), doubling their transaction cost and hope that they don’t overbid the auction again.
Now, thanks to Second Chance, ebay has effectively provided a safeguard which mitigates the risk to a greedy seller of exceeding the buyer’s maximum price. The dishonest seller can now safely discover the real winning bidder’s limit without having to double their transaction fee to obtain the information.
Cubicle has it right. Either you take on fraud by the horns, or it takes you on in very nasty ways. eBay and PayPal chose the latter course, and will always provide a high-cost, low reliability experience for the users. Luckily they got there in an environment when the competition wouldn't stay the course, but things have changed in the payments business lately. Signs are that they recognise the party's over, and Paypal are madly diversifying their base into credit cards and cell/mobile payments.
Viega and Messier talk in ACMQueue about how using SSL to get security is likely to be a bit of a fantasy:
Security Is Harder Than You Think, by John Viega and Matt MessierMany developers see buffer overflows as the biggest security threat to software and believe that there is a simple two-step process to secure software: switch from C or C++ to Java, then start using SSL (Secure Sockets Layer) to protect data communications. It turns out that this naïve tactic isn't sufficient. In this article, we explore why software security is harder than people expect, focusing on the example of SSL.
I'd agree - saying that you use TLS for your security model has generally correlated with a lightweight approach. Likewise, Bruce Schneier writes in Interactions of the ACM that two factor tokens are "too little, too late."
Man-in-the-Middle Attack. [phishing ... snipped]Trojan Attack. An attacker gets the Trojan installed on a user's computer. When the user logs into his bank's Web site, the attacker piggybacks on that session via the Trojan to make any fraudulent transaction he wants.
See how two-factor authentication doesn't solve anything? In the first case, the attacker can pass the ever-changing part of the password to the bank along with the never-changing part. And in the second case, the attacker is relying on the user to log in.
Although people are now happy to point out that the SSL, certificate infrastructure, and the browser security model out there is like swiss cheese, there still seems to be a sense that if the developers and the implementers just read the right books and just did the job fully, then we would have security ... I think the major point here is that ACMQueue and Interactions are happy to print articles pointing out the flaws which is probably a necessary step if we are to move forward.
April 21, 2006
Unique Transaction Numbers in SWIFT
Mark posts this story by Mike Williams to risks. Recorded here as a nice case study in unique transaction numbers.
I used to work on the S.W.I.F.T. payments system, and even that wasn't 100% perfect at eliminating duplicates and spotting omissions.In the many years that I worked with the system, we had one situation where everybody followed the rules, and yet a payment for ten million pounds got lost.
It all started when an operator at Bank A mistyped 10,000,000 instead of 20,000,000 on the initial payment. The error was spotted pretty quickly - banks have systems in place for double checking the total amount that gets paid in and out.
The operator could have sent a cancellation for 10,000,000 and a new payment for 20,000,000 and all would have been well, but cancellations can take days to process and someone would have to pay the overnight interest. What actually happened was that they sent a second payment for the remaining 10,000,000.
Now Bank A happened to use a system whereby the SWIFT Transaction Sequence Number is the same as the initial paperwork that caused the payment to be made, so the two payment messages were sent with the same TSN, the same amount, date, payer and payee. In fact the two payment messages were identical. (My bank didn't work like that, my programs always used a unique TSN, but that's partly because I wanted to use our TSN as a unique index on our outgoing files to make the coding simpler).
Unfortunately, at some point in its journey round the world, the initial payment hit a comms glitch. These were the days when electronic data communications were far less reliable than they are now. The relay station didn't get a confirmation ("ACK") so it sent a copy of the message with a "PDS" marker (Possibly duplicated by SWIFT network).
When the payments arrived at Bank B, they got passed to one of my programs that checks the possible duplicates. Because the payments were 100% identical, and one of them was flagged "PDS", that payment was dumped into the "real duplicate" file.
Mike Williams, Gentleman of Leisure [Forwarded to RISKS by Mark Brader]
April 19, 2006
Numbers on British Fraud and Debt
A list of numbers on fraud, allegedly from The Times (also) repeated here FTR (for the record).
| Regular credit card number: | $1 |
| Credit card with 3-digit security code: | $3-$5 |
| Credit card with code and PIN: | $10-$100 |
| Social security number (US): | $5-$10 |
| Mother's maiden name: | $5-$10 |
THE BIG NUMBERS
£56.4 ($100) billion: Total amount owed on British credit cards 141.1 million: Number of credit, debit and charge cards in Britain 1.9 billion: Number of purchases on credit and charge cards in Britain a year £123 billion: Total value of credit and charge card purchases a year 5: Number of credit, debit and charge cards held by 1 in 10 consumers £58: Average value of a purchase on a credit card £41: Average value of a debit card purchase 88 percent: Proportion of applicants who have been issued with a credit card without providing proof of income £504.8 ($895) million: Total plastic-card fraud losses on British cards a year £1.3 ($2.3) million: Amount of fraud committed against cards each day 7: Number of seconds between instances of fraud £696 ($1,235): Average size of fraud, 2004
(Printing them in USD is odd, but there you go... I've preferred the Times' UKP amounts above, as there were a number of mismatches.)
April 18, 2006
Security Gymnastics - Risk-based from RSA, security model rebuilding from MS, and taking revocation to the next level?
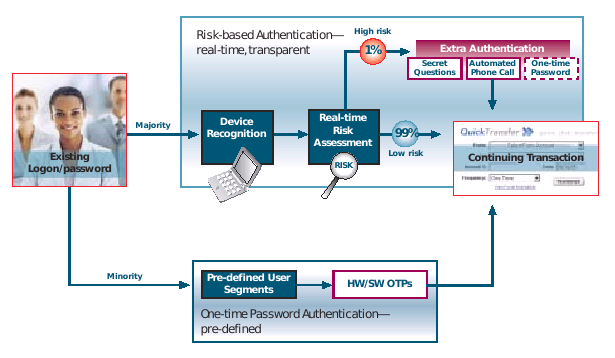
RSASecurity is now pushing a thing called Adaptive Authentication
The risk-based authentication module is a behind-the-scenes technology that is designed to score the level of risk associated with a given activity or transaction—like account logon, bill payment or wire transfer—in real time. If that activity exceeds a predetermined risk threshold the user is prompted for an additional authentication credential to validate his or her identity. ...One-time password authentication offers tangible, time-honored security for the segments of your user base who routinely engage in sufficiently risky activities or who feel better protected by physical security and will reward your institution for providing this through consolidation of assets increased willingness to transaction online.
It's hard to find a pithy statement of reliability amongst the hypeware, but basically this seems to be offering a choice of authorisation methods, based on the risk. The essence here is four-fold: we are now seeing the penny drop for suppliers: security is proportional to risk. Secondly, note the per-transaction emphasis. RSASecurity are half way to a real solution to the meccano / MITB threat, but given their current line up of product, they are stuck for the time being. Thirdly, this confirms the Cyota trend spotted before. That's smart of them.
Finally, recall the security model that we all now dare not mention (#11). It's war with Eurasia, as always. Further hints of this have been revealed over at emergent chaos, where Adam comments on Infocard:
For me, the useful sentence is that 'Infocard is software that packages up identity assertions, gets them signed by a identity authority and sends them off to a relying party in an XML format. The identity authority can be itself, and the XML is SAML, or an extension thereof, and the XML is signed and encrypted.'
Spot it? As reported earlier, Microsoft is moving to put Infocard in place of any prior security model that might have existed (whatever its unname) and as we now are rebuilding the security model from scratch, it makes sense to ... have the user issue her own credentials as that will build user-base support. Oh-la-la! I wonder if they are going to patent that idea?
Over at the NIST conference on PKI, they had lots of talks on trust (!), revocation (!) and sessions on Digital Signatures (!) and also Browser Security (!). I wish I'd been there. I skimmed through the PPT for the Invited Talk - Enabling Revocation for Billions of Consumers (ppt) by Kelvin Yiu, Microsoft, for any correlations to the above (I found none).
But I did find that IE7 will have revocation enabled by default. What this means in terms of CRL and OCSP checking is unclear but one curious section entitled "Taking Revocation to the Next Level" described (sit down before reading this) a fix in TLS that will enable the web server to cache and deliver the OCSP request for an update pre-fetched to the browser. All in TLS. Apparently, this act of security gymnastics is called "stapling":
Revocation in Windows VistaHow TLS "Stapling" Scales
Contoso returns its certificate chain and the OCSP response in the TLS handshake
Stapling reduces load on the CA to # of servers, not clients
I kid you not. According to Microsoft, revocation is to be bundled in TLS - although I would like people to check those slides because I have a sneaking suspicion that NeoOffice wasn't displaying all the content. Anyone from the TLS side care to correct? Please?
Voting and more from the Red Queen
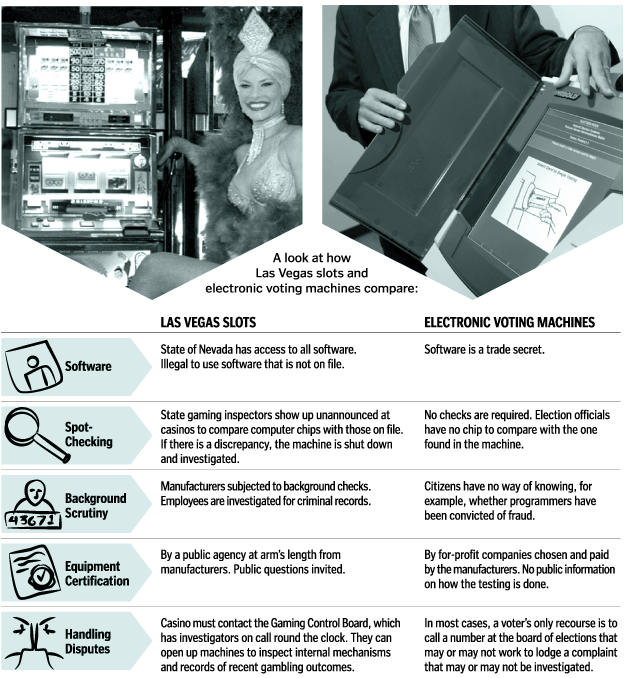
Cubicle points to a great article that contrasts voting machines with gambling machines.
It's easier to rig an electronic voting machine than a Las Vegas slot machine, says University of Pennsylvania visiting professor Steve Freeman. That's because Vegas slots are better monitored and regulated than America's voting machines.
Of course the gambling machines come out on top - they are more carefully governed because the nature of the money is very very clear. With a voting machine, you the punter has no clear picture of how it is being used to reach into your pocket, and your natural skepticism is swept aside by airy fairy claims of democracy and honesty of our public process blah blah.
In contrast to that rosy view of gambling governance, Risks points out that:
Casino can reprogram slot machines in seconds <"Peter G. Neumann"> Wed, 12 Apr 2006 11:10:27 PDTAs an enormous operational improvement, the 1,790 slot machines in Las Vegas's Treasure Island Casino can now be reprogrammed in about 20 seconds from the back-office computer. Previously this was an expensive manual operation that required replacing the chip and the glass display in each machine. Now it is even possible to have different displays for different customers, e.g., changing between "older players and regulars" during the day and a different crowd at night ("younger tourists and people with bigger budgets". (Slot machines generate more than $7B revenue annually in Nevada.) Casinos are also experimenting with chips having digital tags that can be used to profile bettors, and wireless devices that would enable players to gamble while gamboling (e.g., in swimming pools!). [Source: Article by Matt Richtel, Prefer Oranges to Cherries? Done! *The New York Times*, 12 Apr 2006, C1,C4; PGN-ed]
Well, the WaPo story was nice while it lasted. More from Risks, there are reports that votes of lesser importance were interfered with. Going to the sources:
Washington voting hijacked by computer mischiefAn online poll asking Washingtonians to pick their favorite design for the state's quarter coin was suspended, after the balloting was hijacked by computer programs whose automated scripts pushed the tally past 1 million votes over the weekend. State officials overseeing the balloting originally decided not to limit the number of votes coming from individual computers so that family members sharing a single machine could each cast a vote, Gerth said. But that philosophy was being abandoned after the weekend's voting, which showed some computers casting repeated votes for a quarter design faster than humanly possible.
[Source: Associated Press item, seen in *The Seattle Times*, 12 Apr 2006; PGN-ed]
DoIT Information on ASM Election IssuesMore specifically, DoIT detected a disparity between the number of student votes cast and the number of votes confirmed in the online election database. In the Student Council portion of the election, 94 more ballots were cast than were posted; in the referenda portion, 436 more ballots were cast than posted. After further investigation today, DoIT determined that there were no additional discrepancies in the referenda
I wrote before on the monetary aspects of voting. The first story above is about money, but it hardly seems monetary. The second is more of a political issue - but such polls often lead to power and money.
The question then arises if in any voting system it is unreasonable to assume 'honest' behaviour, even if the poll is over issues of no direct importance? Is it therefore better to assume that in any voting system, some small group of users will manipulate if given the chance? Even if there is no benefit to them?
The system of voting I wrote about last week solved this problem -- in the face of prior efforts to increase unimportant ratings fraudulently -- by checking identity on handing out the tokens. That's pretty boring. But if we decide that the only solution to proper democracy is a strong identity society, there's an awful lot of waste there, not to mention risk of identity abuse.
April 16, 2006
Separation of Roles - an example
Having created the five parties model for digital governance, one of the things that has persisted is the difficulty in getting this implemented. Some DGCs have adopted it completely, more or less (goldmoney and Pecunix rise to mind), others only partially (e-gold for example only did parts of the physical metal side, and even that has fallen fallow) and yet others not at all. We don't mention the ones that do not ... at least in a governance post ... because it is hard to comment on their lack of governance.
So why is it so difficult to convince issuers of value to implement governance? Partly it is because the issuers of new value all hail from beyond the traditional accounting and banking spheres, so they simply don't know what's awaiting them. And, it is more information than people care to absorb, especially when the focus is on the customer's short term needs, not the defence against some hypothetical attacker. Partly of course, it is because it is not well explained.
(I think the model is really simple! The Issuer creates a new role called the Mint/co-signatory who is responsible for changes in the total value of issue. Another role created is the manager, who takes that day-to-day value increase and decrease and manages it. This means the Issuer never gets his hands dirty. The Operator runs the systems, and never does numbers, so his hands are clean, too. Finally, the User is the 5th party. She monitors all, leading to the need for open governance.)
One of the fundamentals is the centuries-old tradition of separation of roles. Here's an example of what goes wrong, talking about how 'Apparent authority' doctrine complicates credit card liability. An accounting manager went on a spending spree with her company credit card. She ordered the card, she paid the bills. When the gig was up ... $133k later ... the company argued that it gave no authority for this:
When Kathy's fraud was finally discovered, the company sued American Express, the card issuer, seeking a refund of everything it had paid over $50. But American Express (which has had considerable experience with this sort of thing) resisted, arguing apparent authority.The company responded: "Nonsense. We never said anything or did anything to make American Express think Kathy had authority to use our card for personal purchases. Heck, we didn't even know she had a card. She ordered it herself."
But American Express prevailed, convincing the court that allowing Kathy to pay the credit card bill every month over a long period of time was enough to create apparent authority in Kathy to use the card.
Right, and that makes some sort of sense. Intiutively, the company is responsible for its employees, more or less. We can't go sticking it to the bank just because we weren't watching what was going on. But what was the one specific thing the company should have done? Here:
There are many lessons to be learned here, but the one that leaps to mind is: Don't let the same employee review the company's credit card statements and also write the checks to pay them.
Precisely. Separation of roles. There should always be at least two people responsible for controlling some asset - in this case the ability to order credit cards, run them up and pay them off.
Just how far you go with this depends on the circumstances - security should be proportional to risk. In the five parties model (5PM), I suggest that you start off with the Mint being controlled by the same person as the Operator. And the Issuer can be the Manager. That's because this is how it falls out in operational terms ... Later on as the risk grows, the security needs grow, so the Issuer needs to look at expanding the number of parties from 3 to 5. And beyond, as each of those parties simply divide internally.
But, if you do none of these things - if you implement no separation of roles, no 5PM, no governance at all - then history tells us what happens. One day, as Issuer, you'll be looking for someone to blame, and it might come as a shock to discover it is yourself.
April 12, 2006
Worldwide Internet boom to finish by 2009
From a BBC article sent by Daniel, we find these figures:
| Worldwide: | 12.8% |
| USA: | 68.1% |
| UK: | 62.9% |
| EU: | 49.8% |
| Russia: | 16.5% |
| Ukraine: | 11.4% |
| China: | 8.5% |
| Uzbekistan: | 3.3% |
Also, this comment:
By the turn of the century, Russia had about two million users and now, 10 years later, it accounts for nearly 24 million. At 16.5% of the population, Russia's web community is still small compared to the European Union, where the average is nearly 50%, and about 30% in newer member-states from the east, such as Hungary and Poland.
Which tells us that Internet growth in Russia is running around 70% per annum. At that rate, Russia will cross 50% within 2 years. If the rest of the world is growing at the same rate, it will cross 50% within 3 years. China will be there within months, middle of 2009.
Crossing the halfway mark is strategically important - growth generally has to slow down, and generally it hits a brick wall. You rarely get to 100%, and the US and UK are still stuck between 60-70% - a good working number.
(This is what happened in 2000. Those who saw it coming will recall that PC and Internet sizes both passed the 50% mark around the turn of the century in the western economies. The bubble ended, like clockwork.)
PS: the rest of the article is laughable, a reason in and of itself for reading blogs not traditional news feeds.
April 11, 2006
Threatwatch - Voice Threat Models are Snafu - Situation Normal All F***ed Up
Something bothers me about the recent spate of crypto voice news - it looks like we have bungled the threat model, yet again. Do we never learn?
For some reason phone tapping, VoIP and the like is much in the news, and a couple of references have been spotted to suggestions that we should rise to defend that space. Firstly over at the cryptography list, where all are agog about wiretapping in Greece, secondly in many articles to-ing and fro-ing over zFone and Skype (go guys!) and now a more serious call from Bruce Schneier in Wired:
"This is why encryption for VOIP is so important. VOIP calls are vulnerable to a variety of threats that traditional telephone calls are not. Encryption is one of the essential security technologies for computer data, and it will go a long way toward securing VOIP."
I'm all for it! But the repeated references to encryption have that earthly Douglas Adams feel to them - somewhere between "mostly harmless" and downright dangerous through systemic underestimation.
We all love encryption. But when it comes down to it, encrypting the voice channel is such a small part of the equation that I wonder why the fuss? Is it because we all get that wonderful geeky buzz when we shove 256 bits of full blooded AES right back up the NSA's pipe? Smoke that, spook!
I think that's a lot to do with it. And I wouldn't want to ruin anyone's fun - coz crypto should be fun - but while all the cryptographers are dancing around counting bits on a pinhead, they are in danger of missing the real threat.
No, I'll go further than that. We, they, me, all of us - the whole Internet security community - has actually missed the threat. Quite possibly by a decade or so.
The real threat is tracking.
Why is this? Lots of reasons, but unfortunately they are ho-hum, low tech, under the radar reasons. Not things that the geeks can get addicted to, not ones that give them a buzz. Nothing you can write about in Wired, or in cryptography lists, or the popular journalism of the security press, I suppose.
Still, let's give it a shot and see if we can't save the voice threat model before it follows its predecessors into a decade of confusion, waste, and endless laugh value for the attackers. There are a number of ways of looking at this. I'm not shy, I'll try them all.
Consider GSM, as a great forerunner to encrypted VoIP. It uses something like a 40-bit crypto algorithm that's as weak as water. After cryptoplumber Lucky Green reverse-engineered it out of the chips in a 3 month marathon hacking effort, cryptobuddies Dave and Iang (the other one) cracked the actual algorithm in an afternoon. By the time that was done, GSM as a cryptosystem was just so many bits strewn across the floor, or at least the standard version of A5 was. The journalists loved it!
Or so it seems. In fact, the security model was still good! GSM was unchallenged because Lucky and friends weren't in GSM's threat model - the papparazzi and the phone spoofers were the threat and those scum still have some deal of trouble making their attack.
Meanwhile, the GSM juggernaut rumbled on, untroubled. We are now in a Europe where there are as many phones as people - everyone but everyone has one, and every Finn has two. (And they're all encrypted - Yoo Hoo! Plus, if you have one of those supercool cryptophones, they are doubly encrypted at 256+256 volts .. er .. bits!)
The Americans aren't that far behind, with the slight notable exception of having many different systems. Asian and Latino cultures show no real slackening in cellphone worship either, probably because the lack of good copper systems overcame any braking effect of lower incomes.
Now, consider the facts. That is, the facts that are extracted from tracking versus the facts that are extracted from wiretapping. The facts we can get from tracking are hard - when, where, with whom. They look good in a database, they cross-correlate, they datamine, they stand in court. Indeed, all of society's investigative, dispute and judicial processes are based on these sorts of facts, so the new technology of person tracking fits in well with the old ways of doing things.
In contrast consider the facts in a voice conversation. They are hard to put in a database (so forget about datamining), they consume racks and racks of data storage, they have to be searched for quality, and when it comes down to it, they are pretty darn soft - recordings of voice don't stand well in court. Ludicrously, there seems to be research that suggests that use of wiretaps correlates negatively with conviction rates.
So we have this little thing in our pocket - all of us - and it's trackable. It generates a quality set of facts. All the time, whenever it's powered on. Which leaves one question only - are the facts available?
Nominally, most governments and telcos will say that such data are not available. But evidence is starting to suggest another picture. I have it on reasonable but anecdotal authority that the police in a few countries in Europe have full access to GSM tracking - at the tower. The developments in the US would suggest that the NSA isn't that far behind, unless they are already there (there's that silly story about machines collecting data not being against the rules -- what to make of that? -- well, the story is there and repeated by the spooks, so they must be saying it for a reason . . .). And, plans proceed afoot to integrate this data-that's-not-illegal across the usual suspects, the TLAs.
Here's one anecdote I might have heard. Police - your ordinary plod - can pick you up off the streets, like at a demonstration or something, and show you on TV in the vicinity of other demonstrations ... other months ... other places ... with other people ... using public surveillance cameras.
Now, how could they have correlated all that information? Perhaps they were using a blue tooth rifle on your iPod? Maybe the police are tracking the RFIDs in your clothing?
Nah - the only systems approach that makes sense is that they are datamining the tower hand-off records. How this works we leave as an exercise to the victim.
This all would have been fine and dandy 20-30 years ago when governments in the west were a bit better behaved. But these days, suppression of civil liberties, tracking the naysayers, secret databases and so forth is all the rage (much to the chagrin of the newly liberated eastern european peoples. "What, we got rid of communism . . . for this?").
As it all seems to be happening in secrecy, and as there are therefore no safeguards in place, this is a valid threat. If your local police can track you, they can also blackmail you. Even before we get to dishonest police, there are the telcos.
Here's how this this threat evolves. First, they say they don't collect the data. Then they say they don't use it, except for engineering purposes. Then, they say that there are safeguards. Then, they say they don't supply it outside the company. Then, they sell it.
Then, they just make it up. It takes less than 10 years across the full life-cycle from total privacy to total piracy, and telcos have had a decade or two, already. Governments aren't any help.
Your power in anonymity is stripped away by the secret availability of such tracking databases. We the people have no clue how this information is being used - and likely the first time we find out is when we can buy it ourselves to start spying on our spouses. (oops.)
Other than switching off the phone, what's to be done?
Well, all those cryptophone projects out there are still good - they just have to adjust their threat models. They've covered threats 2 through 9, now they need to think about threat #1. VoIP phones with any encryption are still fantastically good while there isn't massive and pervasive IP# tracking. (oops.)
To advance that theme - continue to support the cryptophones - Skype, Zfone, etc. They are your friends, both. But also cast an eye to the IP detrackers: Tor and the like. In my opinion, the whole P2P space (Jim says here) is far more relevent to the future of security, privacy, etc than any product that knows how to spell AES.
Give me RC4 layered over hazenet any day. Hell, give me Rot13 if you can make a good showing that it's deeply hidden in the noise. Fixing Rot13 is child's play compared to unfixing a static IP# or a Sim#.
April 10, 2006
Why audits are so important
Jim points to this story Man clobbered with £126 trillion phone bill in El Reg:
Publican Jack Harding got the shock of his life when he received his monthly phone bill from BT demanding more than £616,000.But if you think that's bad, spare a thought for Yahaya Wahab, a 63-year-old meat importer from Malaysia. He's just been sent a bill for 806 trillion Ringgit - about £126 trillion.
According to Malaysia's New Straits Times, he's been given 10 days to cough up or face legal action.
He told the paper: "If the company wants to seek legal action as mentioned in the letter, I'm ready to face it. In fact, I can't wait to face it." ®
Threatwatch - pricing the password crack
Some stats on how much it costs to crack a password:
| Yahoo | $150 |
| MSN Hotmail | $175 |
| AOL | $200 |
| GMail | $200 |
| Others | $250 |
Found on crackspider. I'm a bit suspicious of the site as it sent firefox and konqueror into contortions ... so I'll refrain from posting the URL.
April 08, 2006
ThreatWatch - Sony is your friend, Game Over?, Meccano costs, and it'll all be better in two years
Dan Kaminsky writes on the Sony experience:
Learning from Sony: An External Perspective‘What happens when the creators of malware collude with the very companies we hire to protect us from that malware?’ Bruce Schneier, one of the godfathers of computer security, was pretty blunt when he aired his views on the AVindustry’s disappointing response to the Sony rootkit (for an overview of the rootkit and its discovery see VB, December 2005, p.11). His question was never answered, which is fine, but his concerns were not addressed either, and that’s a problem.
The incident represents much more than a black eye on the AV industry, which not only failed to manage Sony’s rootkit, but failed intentionally. The AV industry is faced with a choice. It has long been accused of being an unproductive use of system resources with an insufficient security return on investment. It can finally shed this reputation, or it can wait for the rest of the security industry to finish what Sony started. Is AV useful? The Sony incident is a distressingly strong sign that it is not.
I'm not sure what to make of the threats situation here. On the one hand, it is shocking, simply shocking to think of corporates deliberately increasing the risks of consumers so as to make more money. But, in reality, this has been going on for decades. So what we need is not less but more of the Sony threats. We need more information out in the public view so that we can all more clearly analyse the threats here. I call for more Sony rootkits :)
Has Microsoft declared Game Over?
In a rare discussion about the severity of the Windows malware scourge, a Microsoft security official said businesses should consider investing in an automated process to wipe hard drives and reinstall operating systems as a practical way to recover from malware infestation."When you are dealing with rootkits and some advanced spyware programs, the only solution is to rebuild from scratch. In some cases, there really is no way to recover without nuking the systems from orbit," Mike Danseglio, program manager in the Security Solutions group at Microsoft, said in a presentation at the InfoSec World conference here.
Basically, the OS cannot be protected, and in the event of infection, you have to re-install. That's one brave disclosure, but better they start seeding the public with this info less later than later still.
Fear of security is starting to bite in the US - in contrast to anecdotal evidence. Entrust did a survey that said:
Fear of alienating customersBanks recognize they must increase online security, but are equally concerned that making Web sites harder to use will drive customers back to telephone and branch banking.
"Telephone transactions cost banks 10 times as much to process as Internet transactions. And an in-branch transactions cost 100 times Internet transactions," Voice said.
About 18 percent of online bank customers have already cut back or stopped banking online completely because of security worries, according to an Entrust survey.
It is the cutting back or stopping that is causing the fear from the Meccano trojans I reported on a bit back (also known as MITB or Man-in-the-Browser). Forcing people back to phone or branch has massive cost and deployment ramifications. In the face of these costs, expect many banks to simply suffer the losses. Unfortunately, this won't be socially acceptable, as the majority of the costs are borne by the consumer, not the institution.
Lynn spots the latest crazy threat to invade media mindspace - Beware the 'pod slurping' employee
A U.S. security expert who devised an application that can fill an iPod with business-critical data in a matter of minutes is urging companies to address the very real threat of data theft. ...."(Microsoft Windows) Vista looks like it's going to include some capability for better managing USB devices, but with the time it's going to take to test it and roll it out, we're probably two years away from seeing a Microsoft operating system with the functionality built in," Usher said. "So companies have to ask themselves, 'Can we really wait two years?'"
This is not a new threat, just an old threat with a sexy new toy. Don't believe we had to wait for Apple for the innovative solution to employees' desperate needs to walk out with lots of data...
On the other hand, read that second paragraph above carefully. If you don't like today's scenario, you'll have to wait about 2 years, assuming that Vista has some sort of answer to whatever it is you don't like. I don't normally do stock picks but here's one that screams: buy Apple, sell Microsoft. Users will, even if you don't.
A bit of BitTorrent bother. In brief, ISPs have been using "traffic shaping" to identify Bittorrent traffic and drop it. In response, the top three clients have added an RC4 encryption capability. Threats everywhere...
In closing, 1 in 10 Laptops Stolen:
"Up to 1 in 10 laptops will be stolen during their lifetime according to one of the Law Enforcement Officers behind the new Web site Juststolen.net..."
April 04, 2006
4th April, 1984
Winston wrote in his diary, some 22 years ago:
as he stumbled into the immoral task of pouring his overburdened thoughts onto paper. I say approximately, because there are a number of uncertainties in the source, not least the date. A bit later on, Winston meets an editor of the new dictionary in the canteen, who has this to say:
"It's a beautiful thing, the destruction of words. Of course the great wastage is in the verbs and adjectives, but there are hundreds of nouns that can be got rid of as well. It isn't only the synonyms; there are also the antonyms. After all, what justification is there for a word which is simply the opposite of some other word? A word contains its opposite in itself. Take 'good,' for instance. If you have a word like 'good,' then what need is there for a word like 'bad'? 'Ungood' will do just as well -- better, because it's an exact opposite, which the other is not. Or again, if you want a stronger version of 'good,' what sense is there in having a whole string of vague useless words like 'excellent' and 'splendid' and all the rest of them? 'Plusgood' covers the meaning, or 'doubleplusgood' if you want something stronger still. Of course we use those forms already, but in the final version of Newspeak there'll be nothing else. In the end the whole notion of goodness and badness will be covered by only six words -- in reality, only one word. Don't you see the beauty of that, Winston? It was B.B.'s idea originally, of course," he added as an afterthought.
George Orwell's 1984 remains the definitive word on how a population is suppressed for the benefit of a ruling class, for one agenda or other. The techniques that he describes are so powerful that they literally cut across ideologies, and it seems, across time and experience.
The message of 1984 rose in public consciousness as the year itself approached - recall the film, the songs? But then it started to fade, almost immediately afterwards. Choosing a year in the future as the title might have seemed like a brilliant literary device 40 years earlier, but are we paying the cost now?