January 30, 2005
How Ideas Evolve as a Shared Resource
Recently, I stumbled across a logical economics space where a decision had to be made and no rational information was available. It wasn't exactly that there was no information, but that there was too much noise, and the working hypothesis was that risky decisions would be made without any rational process being successful or potential, for the average participant. (I defined 'rational' as being related to the needs in some direct positive sense.)

Which led me to ponder how shared memes arise outside any framework of feedback. Is this a sales activity? A hype activity? A long search (ok, surf) brought me to the following list of possibilities. They are scattered, and tangential, and to cut a long story short, I remain irrationally indecisive on this process. I actually don't know where to look for this, so comments are also searched for?!
(Links: 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15)
I posted one theory a week back, the Big Lie, and I was somewhat surprised at the heckles raised. In a perverse sense, the response proved one thing, that information and truth can be hidden behind a subject of revulsion (and there are plenty of contempory revulsions with which to hide behind). Coincidentally, the Big Lie also provides one theory on how the shared memes arise, that of the conspiracy by the original big liars. It's a theory, but I'm not convinced it explains the space adequately or even in more than a small minority of cases of the Big Lie itself.
The next thread is what happens when a person knows the truth, and the world ignores him. For example, the case of Tsunami Smith, who warned in 1998 that a tsunami could hit in the Indian ocean; we know now he was ignored.
Another thread is how to extract the info. You could go and ask people, but people don't want to reveal their information. Here's two links (Educated Guesswork, and sharad) on how to extract sensitive information from users. Such games remind me of the old british army technique of the firing squad - 6 privates line up and are handed 5 bullets and one dummy. As none of them know which is the dummy, none of them are totally sure that they were responsible for the death of the victim.
Which leads us to the evolving science of the Ideas market. This is an idea by Robin Hanson whereby many people aggregate their opinions, but there are some tricks to overcome the barriers. Firstly, people get rewarded in some fashion for voting on ideas. Of course, few of us can predict the future, so most of the votes are non-useful. But some of the voters actually know what they are talking about. So, in order to overcome the 'popular vote' effect (which is close to what I'm looking at above), people who vote correctly are rewarded by increased value in their 'shares' in the idea's future, and those who vote incorrectly lose their investment. It's "put your money where your mouth is" time. (I have to of course mention my own contribution, the Task Market where you get to own the results of the choices as well.)
Memes are an idea that have been around for a long time - concepts or ideas that pass from person to person. I know this was a hot concept years ago, but I never paid attention to it. Wikipedia has some good starters on it, but it doesn't answer my question; how do these things arise? I do not know, but Wikipedia has a great example of the most popular net meme of all. If only it were that simple!?

You're probably facing some meme resistance by now. Karl Popper advocated this in the strongest possible terms: "the survival value of intelligence is that it allows us to extinct a bad idea, before the idea extincts us." I liked that quote so much I posted it on my SSL page. The only problem is, I don't know where and when he said it, which probably shows its memity.
The self as a meme - I am reminded of a habit I had (have?) when engaging a particularly stupid idea by someone convinced of same. This habit became known by those punished with it, and replicated. So much so that one day I was sitting beside a woman who did it, without realising where it came from ... No, I decline to document the meme, but those who know will.
This post on Boyd and Military Strategy provides an interpretation of what we are observing in certain security goods within OODA (observation-orientation-decision-action) loops. In brief: Observation has initially failed to reward observers, so alternate strategies are formed within Orientation. As there is insufficient feedback in the loop, the Orientation gets more and more powerful, until it is no longer capable of dealing with Observations. That is, those Observations that are in accord with the Orientation are accepted and trumpeted, and those against are discarded. (Those that are ambiguous are open to misinterpretation!)
And finally, Crowds and Power is a book I am reading by Elias Canetti. The mob ruleth, and I shall report back when I've discovered how to rule the mob. Also on the list is Extraordinary Popular Delusions. With a title like that, it just has to have some secrets hidden within.
Which, all tantalising snippets aside, gets me no closer to understanding how decisions are made when there is insufficient information. Maybe that's the way it has to be...
Addendum #1: Adam reminds me to add the Keynesian Beauty Contest:
The Keynesian beauty contest is the view that much of investment is driven by expectations about what other investors think, rather than expectations about the fundamental profitability of a particular investment. John Maynard Keynes, the most influential economist of the 20th century, believed that investment is volatile because investment is determined by the herd-like “animal spirits” of investors. Keynes observed that investment strategies resembled a contest in a London newspaper of his day that featured pictures of a hundred or so young women. The winner of the contest was the newspaper reader who submitted a list of the top five women that most clearly matched the consensus of all other contest entries. A naïve strategy for an entrant would be to rely on his or her own concepts of beauty to establish rankings. Consequently, each contest entrant would try to second guess the other entrants’ reactions, and then sophisticated entrants would attempt to second guess the other entrants’ second guessing. And so on. Instead of judging the beauty of people, substitute alternative investments. Each potential entrant (investor) now ignores fundamental value (i.e., expected profitability based on expected revenues and costs), instead trying to predict “what the market will do.” The results are (a) that investment is extremely volatile because fundamental value becomes irrelevant, and (b) that the most successful investors are either lucky or masters at understanding mob psychology – strategic game playing. “Animal spirits” are now known as “irrational exuberance,” and this beauty contest model is an explanation for such phenomena as stock market bubbles. Contrast this model with efficient markets and present value.
RFID attacked - to impact Passport Debate
The cryptography in RFIDs used as keys into cars has been successfully attacked by a team of cryptographers and security specialists. The system, known as the Texas Instruments DST (digital signature transponder) does a challenge-response based on a proprietary algorithm and a 40 bit key.

The team cracked open the secret algorithm by probing the device and gradually isolating it from the responses; this is called an 'oracle' attack. Then, with the algorithm bare, they were able to build a brute force 16-way key space searcher (with some optimisation) and figure out keys. Allied with a device they constructed to simulate the challenge-response, the team were then able to unlock the vehicle.
It was their own vehicle, but they also used the same techniques on SpeedPass tokens to create a device to purchase fuel at gas stations.
How plausible is this attack? Reasonable. With optimisation, car owners could be at risk. But, consider this: they are still at less risk than all the others who don't have this technology. And, it's not a 100% breach, in that there are quite severe costs left over to turn this into a real live attack. Don't expect any serious news for another year, I'd say, and it is likely that SpeedPass is the more risky area, but even then, it is not an easy attack (considering that in order to steal a tank of petrol, you have to drive past the cameras ...).
Some will say this is evidence that "things should have been done properly!" To that I say Balderdash! When this system was conceived, it is likely that it couldn't have been much stronger. More, it's done its job, for that we should thank the designers. Even better, by all reasonable analysies, it is going to continue to do its job, albeit with higher risks.

Further, we now have something of inestimable value: a data point. The system was invented, deployed and attacked. On this day, in its history, it was attacked. Up until then it was a theoretical unknown, but now we have a fairly good idea of how much it costs to attack it.
That information will be of inestimable value in designing the replacement systems. The systems people now have a baseline and can happily assess what they need for the next ten years. Without this attack, that would not have been possible, as everything would have been based on theoretical projections, which have proven to be rather shy of useful in some cases.
What will be more important is how this crack shakes up the debate on Passports with RFIDs. Already under challenge, this will cause the heads over at DHS to duck down from the rampants faster than you can say challenge-response. It will be interesting to see how that primarily political project evolves!
CostaGold case Settles - Leaving Ugly Dilemma for Open Governance Issuers
Over on the CostaGold settlement blog (yep, class action is now done by blog!) there is news that the court has granted final approval for the settlement of the seized funds. This hopefully brings the sorry episode to a close, but the black spot on G&SR and the consequent unanswered questions for the future of the sector remain.
To briefly summarise the story (I'm being fast and furious with the facts here): Costagold started up as one of the boom games around Y2K that ploughed into e-gold's booming market. Growth in e-gold was 10 times per year, and the sky was no limit. People wanted to play, and they played anything, including what latter came to be seen as obvious Ponzis or Pyramids or variants.
Costagold amassed a pot of e-gold from these players, and at some point got scared enough to start pulling it out. They sold through G&SR, the joined-at-the-hip exchange provider for e-gold, and that's when things went wrong: As they started exchanging, G&SR seized the e-gold and held it.
Nominally, it was because, G&SR said, they wanted to identify the owners. Skipping the question marks about all this, G&SR now held this pot, and did ... nothing with it. Eventually, some of the nominal owners found their way out of ignomy and filed a class action suit, using a real law firm. The case wound on as these things do, and just last week a settlement was finally agreed.
It is pretty clear that Costagold was a scam, a Ponzi, a fraud. It's also pretty clear that G&SR acted impetuously, and ended up in a very difficult position. What were they supposed to do now that they had seized the metal? Return it? Send it back? Find the original owners? Further, everyone knew it was a game all along, including G&SR and e-gold, so if they were going to act, why did they act when the money came into their reach?
From there, G&SR just made matters worse for themselves. Instead of seeking to resolve the situation, they held on and fobbed off attempts by difficult owners to deal. They made no attempt to unravel the Ponzi, as they had done with the Advance scam a few months before. Further, they moved the gold offshore, into the hands of Bermuda lawyers, and from there, who knows where it went?
When the class action was awarded in December 2003, instead of standing there as a disinterested party holding on to the monies of others, their actions seemed calculated to delay. G&SR filed to appeal! That was of course knocked back by the Appeals court, but still delays occurred.
The problem with all this is that even if G&SR were doing the right thing, their actions left a bad taste in the mouth. It's not good enough to simply follow the laws of the land, and play legal games in court. An Issuer also needs to stand up there and be disinterested, and be seen to be disinterested in the monies that the Issuer has under charge.
Which leaves us with a lesson. And a dilemma: An Issuer of Honour is faced with many challenges, and one of the chief remaining ones is how to deal with Ponzis.
To be fairly critical to us all, I don't think we as a sector have an answer for the Ponzi as yet.
We have much to our credit, and I shall list them: We have answers for other frauds. We've got answers for phishing, and insider fraud. Money laundering is covered, same same for terrorism and the other bogeymen. We know how to deal with theft of reserves, for example. We have privacy systems that lead the way.
But, comprehensively, we do not have a good answer for Ponzis. (I know there are some out there that think that Goldmoney's heavy identity approach kills Ponzis, but the cure is killing the patient as well. It seems that if you trigger their systems, you can be locked out of your own money - trivial amounts, too - for 3 months. Which means it isn't money any more.)
What the G&SR lesson has taught us is that the Issuer should not seize the funds. Even if they did all the right things, the mud will stick, and this will cost them in credibility. Which, as an Issuer, is surely the most important currency of all.
Which brings us back to the dilemma of handling the Ponzis. Is this an unanswerable question? Is there a way where we can push real money out on the net, and not have to face the Attack of the Killer Ponzis? Or do we have to simply accept that everyone is an adult, and they have the right to be fools, parted from their money?
I don't know the answers. But I do feel that this is one big area where the Internet money issuance business is left with an open question, and a challenge for the future.
January 29, 2005
The Authur Andersen Factor - Riggs Bank
In the governance section, often seen as squeezed between economics and grass growing in the stakes of dismality, we see an emerging trend to compare everything to Arthur Andersen. Of course, the collapsed audit house was a big (!) data point, one which everyone can agree with. So that makes it special. (Links 1, 2, 3, 4).
But let's get real. What Arthur Andersen actually did was a) obvious and b) routine. A little bit of pre-emptive shredding? Who in their right minds thinks this is not going on? By what theory of human action or agency theory or what-have-you can we show that auditors will not take the money and do the company's bidding?
As far as I can tell, what AA was caught for was some minor infraction. No doubt worse was going on under the covers. How can we tell? Because audits are mostly secret. (Read any audit report, and it doesn't really tell you what they did, and is covered by a whole bunch of weasel words.) If they are secret, then there are two possible reasons: one is to hide the information from you, and the other is .. to hide the information from you! Which is to say, they will tell you that it is competitively sensitive, but that's indistinguishable from "didn't do the job."
Which leaves us with yet another case of lemons. The market doesn't really rely on the audit report, other than its binary existence. The market does its own calculations, and looks to other fraud indicators to see what's what. (When was the last time you saw a company fail, and the auditor knew and warned?)
Which also brings us to the question of just what one is supposed to do about it. Basel II and Sarbanes-Oxley will add more and more regulation, but will not change the overall governance equation, except for the worst. That's because they make things more complex, and we are already seeing signs that boards are losing their original governance and strategic focus in a frenzy of CYA adjustment.
They also add costs, so they are 'bads' on two counts. What then is the underlying source of the rot? I believe it to be secrecy. Corporates that practice keeping things secret set themselves up for the rot to spread internally and eventually bring themselves down. The sunlight for secrecy is called disclosure, and if you look at the Enron case, it was disclosure that triggered the event: some member of the public scrutinised the _publically accessible filings_ of the company and realised that the numbers so filed didn't accord with reality.
In my emerging theory of open governance, anything that is disclosed is good, anything secret is bad. (How this theory stacks up against competitive intelligence is an unanswered question, for the moment!) In this sense, the existence of the SEC, FSA and various million or so filings that they mandate is a good thing. As long as they are public. Any rule that doesn't result in a public filing is a 'bad'.
Make no mistake, this is not a satisfactory state of affairs - the government has no clue how to mandate useful disclosure. Not because others are smarter, but simple market principles indicate that no one person knows such things. Disclosure is a competitive force, like all other 'goods' and thus an open governance society would encourage differentiation. In my favoured world, one company would decide on an audit, and another would not. Let the market judge.
(Indeed, in the evolving governance world of the 5PM, those practising it know that it costs a bundle to do it "fully," so the more realistic way is a graduated approach.)
Which brings us to Riggs Bank. It is looking like the rot was both secrecy borne of age and influence, and also a well known form of banking cancer is lurking within. The reason I say that is mostly intuition, but also, it transpires that Riggs Bank was also a favourite bank of the CIA. What this means is that aside from the normal secrecy infection leading to rot, the bank laboured under huge conflicts of interest. The CIA has a long history of infecting banks and running their own banks, and the result is never pretty, in governance terms (think Nugan-Hand, BCCI, ...).
Perversely, when the news of the CIA connection broke, Riggs shares rose heavily. This shows the market knows that the punishment will be relatively light, as Riggs now have a get out of jail card. This was already confirmed in the early plea bargain for a single criminal conviction - there is no way a bank would take a cop like that without fighting unless some other deal were done.
In closing, what can we say? Governance - it's a mess. If there are secrets there, don't expect it to be pretty when the sunlight hits. And don't expect any auditor to have picked up the Riggs situation. That's just naive.
January 27, 2005
Towards an Economic Analysis of Disclosure
Adam says an economic analysis of Disclosure (of security bugs) has never been done, and makes a good start at it (perhaps in order to distract me from the stock market losses...). His list of costs are: 1. researcher, 2. primary vendor, 3. user patching, 4. secondary (layered) vendors, 5. attacker.
To which I would add this:
A. there is a cost to the user if they *don't* patch. That is, the user faces costs regardless, and in the decision to patch or not patch, they face one of two possibilities. Patching costs are low, but in the aggregate high. Not-patching costs are high individually, but in the aggregate, low(er). The question arises what the probability for breach event is, and what the cost of that breach is. This (multiplied) would then be compared against the user's patch costs.
B. there is also the decision not to disclose. In the event of not disclosing, we are essentially taking a gamble that nobody else figures it out (i.e., the decision not to disclose is the same as the decision to use security by obscurity, but by a different party). The key question I suppose is, "what is the probability that the information will still find its way to an attacker?" If that probability is low, then there might be merit in not disclosing. But, if one can show that this is information that is likely to get to the attacker, that merit disappears.
Once we identify all these different costs .. and probabilities, it should be a snap to develop a model that gives us some predictions! So yes I'm happy, especially as the economics of stock market shifts is so much voodoo anyway ;-)
Unintended Consequences and the Case of the $100 Superbill
Axel points to a rather good article on Unintended Consequences with lots of good examples for the security thinker. If there is one cause that one had to put ones finger on, it is this: the attacker is smart, and can be expected to think about how to attack your system. Once you think like an attacker, you have a chance. If not, forget it.
Notwithstanding that minor ommission, here's the rather nice FC example, that of the mysterious $100 superbills.
Back in the 1970s, long before the revolution that would eventually topple him from power, the Shah of Iran was one of America's best friends (he was a dictator who brutally repressed his people, but he was anti-communist, and that made him OK in our book). Wanting to help out a good friend, the United States government agreed to sell Iran the very same intaglio presses used to print American currency so that the Shah could print his own high quality money for his country. Soon enough, the Shah was the proud owner of some of the best money printing machines in the world, and beautiful Iranian Rials proceeded to flow off the presses.
All things must come to an end, and the Shah was forced to flee Iran in 1979 when the Ayatollah Khomeini's rebellion brought theocratic rule to Iran. Everyone reading this undoubtedly knows the terrible events that followed: students took American embassy workers hostage for over a year as Iran declared America to be the "Great Satan," while evidence of US complicity in the Shah's oppression of his people became obvious, leading to a break in relations between the two countries that continues to worsen to this day.
During the early 90s, counterfeit $100 bills began to flood the Mideast, eventually spreading around the world. Known as "superbills" or "superdollars" by the US Treasury due to the astounding quality of the forgeries, these $100 bills became a tremendous headache not only for the US and its economy, but also for people all over the world that depend on the surety of American money. Several culprits have been suggested as responsible for the superbills, including North Korea and Syria, but many observers think the real culprit is the most obvious suspect: an Iranian government deeply hostile to the United States ... and even worse, an Iranian government possessing the very same printing presses used to create American money.
If you've ever wondered just why American currency was redesigned in the 1990s, now you know. In the 1970s, the US rewarded an ally with a special machine; in the 1990s, the US had to change its money because that ally was no longer an ally, and that special machine was now a weapon used to attack the US's money supply, where it really hurts. As an example of the law of unintended consequences, it's powerful, and it illustrates one of the main results of that law: that those unintended consequences can really bite back when you least expect them.
Read the rest... Unintended Consequences.
DIMACS Workshop on Information Markets
An interesting workshop on information markets (2-4 Feb) has enough of a nice description to lift and post. (Think BlogShares...) Sadly, registration is already closed - I wonder why this one hid its light under a bushel?
DIMACS workshop on information markets
February 2-4, 2005 DIMACS Center, Rutgers University, Piscataway, NJ
A market designed for information gathering and forecasting is called
an information market. Information markets can be used to elicit a
collective estimate of the expected value or probability of a random
variable, reflecting information dispersed across a population of
traders. The degree to which market forecasts approach optimality in
practice, or at least surpass other known methods of forecasting, is
remarkable. Supporting evidence can be found in empirical studies of
options markets, commodity futures markets, political stock markets,
sports betting markets, horse racing markets, market games, laboratory
investigations of experimental markets, and field tests. In nearly all
these cases, market prices reveal a reliable forecast about the likely
unfolding of future events, often beating expert opinions or polls.
Despite a growing theoretical and experimental literature, many
questions remain regarding how best to design, deploy, analyze, and
understand information markets, including both technical challenges
and social challenges.
This workshop will include talks on information markets by a number of
distinguished invited speakers. Speakers will cover a range of topics
including mechanism design, experiments, analysis, policy, and
industry experience. Speakers will include representatives from
academia, industry, and government. The workshop will feature research
talks, opinions, reports of industry experience, and discussion of
government policy from the perspective of a number of fields,
including economics, business, finance, computer science,
gambling/gaming, and policy. See the workshop program for more
details: http://dimacs.rutgers.edu/Workshops/Markets/program.html
The workshop will feature a tutorial session on Wednesday afternoon
(Feb. 2, 2005) to help those new to the field get up to speed. The
workshop will include a panel discussion on the Policy Analysis Market
(a.k.a., "Terror Futures") and a "rump" session where anyone who
requests time can have the floor for five minutes to speak on any
relevant topic. To participate in the rump session, please email David
Pennock: pennockd --AA@TT- yahoo-inc.com.
*********************************************************************
Workshop Program:
tentative schedule, subject to change
Wednesday, February 2, 2005
Tutorial Session I
12:00 - 1:30 Lunch and Registration - 4th Floor, Lounge, CoRE Building
Registration for the tutorial will be
limited to the first 60 registrations.
1:30 - 3:00 Information Markets I: Examples, Rules, History, Mechanics,
Studies, Participants, Ambiguity, Laws
Joyce Berg, Accounting, University of Iowa
3:00 - 3:30 break
Tutorial Session II
3:30 - 5:00 Information Markets II: Theory, Outputs, Inputs, Foul Play,
Combinatorics, Applications
Robin Hanson, Economics, George Mason University
Thursday, February 3, 2005
8:15 - 8:45 Registration and Breakfast - 4th Floor, Lounge, CoRE Building
8:45 - 9:00 Welcome and Opening Remarks
Fred Roberts, DIMACS Director and
David Pennock, Yahoo! Research Labs
Session: Policy, Politics, & Open Questions
9:00 - 9:30 Michael Gorham, Business, Illinois Institute of Technology
9:30 - 9:55 Robert Hahn, AEI-Brookings Institute
9:55 - 10:20 Information Markets and Politics
Adam Meirowitz, Politics, Princeton University and
Joshua Tucker, Public and International Affairs, Princeton University
10:20 - 10:45 Five open questions about prediction markets
Justin Wolfers, Business, University of Pennsylvania
10:45 - 11:15 break
Session: Experimental Economics
11:15 - 11:40 An Experimental Test of Combinatorial Information Markets
John Ledyard, Humanities and Social Sciences,
California Institute of Technology
11:40 - 12:05 Information markets and decision makers
Tony Kwasnica, Management Science, Pennsylvania State University
12:05 - 12:30 Information aggregation: Experiments and industrial applications
Kay-yut Chen, Hewlett Packard Labs
12:30 - 2:00 Lunch
Session: Business Models, Industry & Field Experience, Part I
2:00 - 2:15 Internal markets: Why and for who?
Carol Gebert, Incentive Markets
2:15 - 2:30 Tee Time with Admiral Poindexter
Todd Proebsting, Microsoft Research
2:30 - 2:45 Information markets as a platform for improved corporate communications
Steven Ostrover, EconOne
2:45 - 3:00 Challenges of Bringing Information Markets to the Organization
Ken Kittlitz, The Foresight Exchange
3:00 - 3:15 TBA
3:15 - 3:45 break
Session: Design and Implementation
3:45 - 4:10 Carsten Schmidt, Max Planck Institute
4:10 - 4:35 Expert identification via virtual stock markets: Finding
lead users in consumer product markets
Martin Spann, Business and Economics, Frankfurt University
4:35 - 5:00 Are prediction markets robust against manipulation? A lab experiment
Martin Strobel,Economics, Maastricht University
5:00 - 6:00 Rump session
I'm glad to see you've all discovered the Delphi method!
Murray Turoff, Information Systems, New Jersey Institute of Technology
Does money matter?
Emile-Servan Schrieber, Newsfutures
Auto-arbitrage in multi-outcome markets
Emile-Servan Schrieber, Newsfutures
7:30 - 9:00 Banquet - the Holiday Inn in South Plainfield
Friday, February 4, 2005
8:30 - 9:00 Registration and Breakfast - 4th Floor, Lounge, CoRE Building
Session: Economics, Finance, and Gambling
9:00 - 9:30 Leighton Vaughn Williams, Economics, Nottingham University
9:30 - 9:55 Manipulation in prediction markets: Evidence from historical
and contemporary election markets
Koleman Strumpf, Economics, University of North Carolina
9:55 - 10:20 Manipulators increase information market accuracy
Robin Hanson, Economics, George Mason University
10:20 - 10:45 Information aggregation and manipulation in an experimental market
Ryan Oprea, Economics, George Mason University
Session: Iowa Electronic Market
11:15 - 11:40 George Neumann, Economics, University of Iowa
11:40 - 12:05 Public signal bias and prediction market accuracy
Thomas Gruca, Marketing, University of Iowa
12:05 - 12:30 Searching for Google's value: Using prediction markets
to forecast market capitalization prior to an IPO
Thomas Rietz, Finance, University of Iowa
12:30 - 2:00 Lunch
Session: Business Models, Industry & Field Experience, Part II
2:00 - 2:15 HedgeStreet: An introduction
Russell Andersson, Hedgestreet.com
2:15 - 2:30 Emile Servan-Schreiber, Newsfutures
2:30 - 2:45 Chris Hibbert, CommerceNet
2:45 - 3:00 Emphasizing the mundane: Making a business of information markets
Charles Polk, Common Knowledge Markets
3:00 - 3:15 TBA
Session: Computation
3:45 - 4:10 Computational complexity issues in information markets
Lance Fortnow, Computer Science, University of Chicago
4:10 - 4:35 Michael Wellman, Computer Science, University of Michigan
4:35 - 5:00 A dynamic pari-mutuel market for hedging, wagering,
and information aggregation
David Pennock, Yahoo! Research Labs
5:00 - 6:00 Post-mortem panel discussion on the Policy Analysis Market
(a.k.a., "Terror Futures")
Robin Hanson, Economics, George Mason University
John Ledyard, Humanities and Social Sciences,
California Institute of Technology
Charles Polk, Common Knowledge Markets
January 26, 2005
The market punishes bad news, not bad not-news
Adam responded over on his blog to my claim that it was FUD that the market was shifting to, not the loss of confidentiality. So I'll try and argue my case more.
The market responds to news. It doesn't respond to not-news. Why not? The reason for that is that the not-news is already factored in. That is, Bank of America is known to have the potential for branch bank robbery, and the market puts a risk premium on it for that. Bank of America may be big enough to face a bank robbery a day, but the market knows that and doesn't respond to any individual event.
The news that a confidentiality breach has occurred then is either news or not-news. In the case of the measured companies, that dropped 5% in one study, 2% in another, it was clearly news.
Yet, confidentiality breaches are occurring all the time. Visa and Mastercard and all the banks are being raided on a routine basis. What happens when some bank announces it has arrested an insider for selling account information for $10 or $20 a pop? Nothing. That's not-news. It's not news because the market already understands that the banks and retail credit and identity systems have a huge insider problem. So it's factored in. No shift in market price, even if 100,000 accounts have been compromised.
Then, when some poor muggins who is doing something different - not the usual suspects listed above - and discovers their account database has been lifted, that is ... different! That's news - not because its bad. In fact, we can probably empirically show that it is way less bad than the above not-news because it is much rarer and the compromises are generally lighter. But no matter, the journos write about it, the righteous point fingers, and the market sells.
What the news is in this case is that the market has not understood and has not factored in the possibility of a loss of confidentiality in the new player. It might be an Internet bank, or it might be a telco, or it might be a government department. Either way, all this data sitting there and nobody knew about it nor understood that it could leak ... well, when *that* data gets lifted by a sneaky hacker, we are all surprised.
Try it some time. Look at a particular case and look deeply. I'd suggest you will come to the conclusion that there was a storm in a teacup. As in, "so what was all the fuss about?" Consider the recent Mobile-T thing. 400 users had their account information lifted. What was the scandal? What had really attracted the attention of the press was that the hack had occurred against a Secret Service agent! Very sexy! What's more, famous names had their photos downloaded. Better and better. And, shock horror, telcos are amassing huge databases of our personal lives!
If only 400 boring accounts from a telco had been lifted, what would you write about? I think that story showed a definate press bias on the "new and scary" and the market to some extent follows that. To be fair we'd need a bank insider story to compare this to - and there are quite a few. Problem is, they are so mundane that even I forget them.
Also, you can look at those X accounts and propose some metric as to how much that confidentiality is worth. Say the 400 account hack dropped Mobile-T's share price by 5%. (Hypothetically, I don't know if they got hit or not.) Now, they have many more accounts than that. I'd guess they have something in the millions.
What happens if they lose a million accounts? Does that mean their share price goes down by 100 * 5% * 1,000,000/400 = 12500% ? No of course not. Firstly, they can't go down below 100%. Secondly, even if they opened up every account they had, they still haven't got a loss of revenue stream.
Which is to say that whatever is being said by the stock market, it is *not* anything quantifiable: it is not measuring an _amount_ of confidentiality. I guess my point here is that it is the meta-loss, not the confidentiality itself that is the crime.
January 25, 2005
Do security breaches drop the share value?
According to those that think WiKID thoughts, yes. Quoting a paper by Campbell et al, there can be measured a 5% drop in stock price when confidentiality is breached. Adam demurs, thinking the market is unconcerned about the breaches of confidentiality, rather, is concerned about a) loss of customers or b) lawsuits.
I demur over both! I don't think the market cares about any of those things.
In this case, I think the market is responding to the unknown. In other words, fear. It has long been observed that once a cost is understood, it becomes factored in, and I guess that's what is happening with DDOS and defacements/viruses/worms. But large scale breaches of confidentiality are a new thing. Previously buried, they are now surfaced, and are new and scary to the market.
And the California law makes them even scarier, forcing the companies into the unknown of future litigation. But, I think once these attacks have run their course in the public mind, they will stop causing any market reaction. That isn't to say that the attacks stop, or the breaches in confidentiality stop, but the market will be so used to them that they will be ignored.
Otherwise I have a problem with a 5% drop in value. How is it that confidentiality is worth 5% of a company? If that were the case, companies like DigiCash and Zero-Knowledge would have scored big time, but we know they didn't. Confidentiality just isn't worth that much, ITMO (in the market's opinion).
The full details:
"The economic cost of publicly announced information security breaches: empirical evidence from the stock market," Katherine Campbell, Lawrence A. Gordon, Martin P. Loeb and Lei Zhou Accounting and Information Assurance, Robert H. Smith School of Business, University of Maryland, 2003.
Abstract This study examines the economic effect of information security breaches reported in newspapers or publicly traded US corporations. We find limited evidence of an overall negative stock market reaction to public announcements of information security breaches. However, further investigation reveals that the nature of the breach affects this result. We find a highly significant negative market reaction for information security breaches involving unauthorized access to confidential data, but no significant reaction when the breach does not involve confidential information. Thus, stock market participants appear to discriminate across types of breaches when assessing their economic impact on affected firms. These findings are consistent with the argument that the economic consequences of information security breaches vary according to the nature of the underlying assets affected by the breach.
Also over on Ross Anderson's Econ & Security page there are these:
Two papers, "Economic Consequences of Sharing Security Information" (by Esther Gal-Or and and Anindya Ghose) and "An Economics Perspective on the Sharing of Information Related to Security Breaches" (by Larry Gordon), analyse the incentives that firms have to share information on security breaches within the context of the ISACs set up recently by the US government. Theoretical tools developed to model trade associations and research joint ventures can be applied to work out optimal membership fees and other incentives. There are interesting results on the type of firms that benefit, and questions as to whether the associations act as social planners or joint profit maximisers.
Which leads to "How Much Security is Enough to Stop a Thief?," Stuart Schechter and Michael Smith, FC03 .
FC05 Registration Deadline
There are now (26°C) less than two weeks (writes Stuart Schechter) to register for FC05 (Dominica, 28th Feb - 3rd March, 24 °C) before the late registration rates kick in. Registering by February 6th is necessary to ensure that we can provide you with food, pre-proceedings, and a conference t-shirt (warmth is guaranteed).
If you must register late, please get in touch with me and let me know your t-shirt size and whether you will be qualifying for the general, academic, or student rate. If we don't know to expect you, we cannot guarantee that there will be pre-proceedings, t-shirts, or meal tickets available for you. (But you won't freeze.)
Best regards
Stuart Schechter
General Chair
Financial Cryptography and Data Security 2005
Registration deadline drivers:
January 25 - 26 °C, clear, sunny, warm.
February 7 - Late registration period begins at 12:00AM EST
February 7 - Orders for pre-proceedings due to printer
February 7 - Orders for t-shirts due to shirt printer
February 14 - Count of attendees due to hotel caterers
February 28 to March 3 - 24 °C, 2cm precipitation
January 23, 2005
BlogShares - fantasy trading in blogs and ideas
Information, and it's alternate, information overload, is the currency of our generation. Hayek's stunning observation that prices are the messages of needs and desires in our economy, and Mises calculation argument - that the humans are the computers, and they work better (only?) when distributed - are the bedrocks of our Internet economy. Yet the flood of Hayekian messages leads simply to an overload on my poor old Misean brain, so much so that I wish his calculation argument didn't signal the death knell of centralised thought processes. I need someone to tell me what to do!
In the last 5 years, we've seen several emerging technologies that have worked with information in new ways. They are - check my enumeration here - Blogs, p2p, community currencies, reputational auctions. I might have missed a few, but here's my point: all of these promise great things, but like Napster, isolated they fail.
Here's a great example of a tech that has successfully integrated several emerging paradigms. Blogshares is a market place for fantasy trading of blogs-as-companies. (Check off blogs, community currencies, and reputational auctions!) More than that, it has an ideas market in it . (Check off reputational auctions, again!) It lacks peer to peer, but there's only so much you can do, and I rate 3 out of 4 pretty highly.
Check it out, unless you are busy. The site is clunky, slow, and difficult to navigate, which is unfair in the context of only 2 guys working on it, but fair in terms of your time. When all those things are sorted out, I suspect it will bloom.
If you have a blog then you may want to dive in there, create an account, and claim your blog. If only because you want to vote it into useful categories. I don't fully recommend this as yet, because it takes a while to sort out, and it seems to matter not if others vote you in. Also, the categories are a single hierarchical tree, which went out with the Dewey Decimal System.
For example, FC is impossible to categorise, simply because by definition, it's cross leaf and broad, not deep and sectoral. Currently, it's been incarcerated in Economics. (More dismal yet, they are currently working on a system to penalise broad voting :-/ )
Here's my hard description: BlogShares is a fantasy stock market and ideas market where weblogs are the companies. Players invest fictional dollars on shares in blogs. Blogs are valued by their incoming links and add value to other blogs by linking to them. Prices can go up or down based on trading and the underlying value of the blog. Players can vote 'industry' sectors on blogs, and establish Ideas. The combination of fantasy trading, ideas market and corporate currencies makes this idea a winner, although the site is still clunky and hard to learn.
January 22, 2005
Eudora overcomes stupidity to tackle phishing
(JPM reports) here is a simple example from Eudora (a popular email client) for OSX.
You'll get the idea. Note that "anti phishing technology!" is stunning, stupidly simple. It's just Not That Complex.
"You need a big warning in email clients when a link is fake."
Oh.
So over at MIT people are making robots that can have intercourse with sound effects, but over in the Email Client Corner, a concept as stunningly simple as this...
"You need a big warning in email clients when a link is fake."
Is just Too Hard.
Note that anti phishing technology is far, far simpler than say "spell checking"
When you use the Eudora email client, and you make a spleliling mistake, it brings up a HUGE, CATACLYSMIC warning - the entire operating system is taken over, massive alerts 50% the size of the screen appear, if you have a printer connected, massive "SPELLING ERROR!" banners immediately shoot out of the printer. The Mac's excellent voice synthesis is employed and suddenly - before you can type the next space key - Steven Hawking's voice is telling you "YOU HAVE -- MADE A SPELLING - ERROR - ALERT!!!"
That's for a spelling error.
In contrast when an email contains a "phishing" link, the miserable alert attached flashes up for a second -- but only if you mouse over the link:
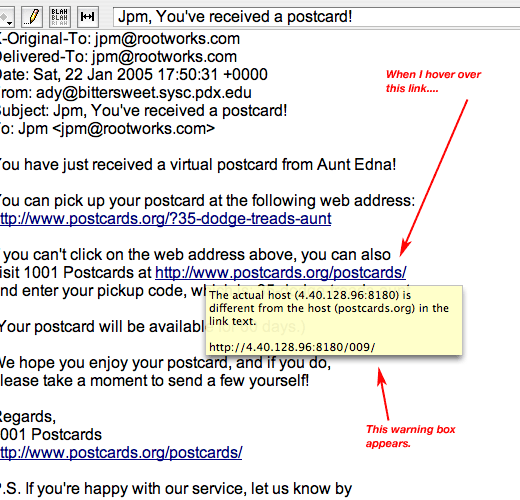
The bottom line here, as always, is that not so much software engineers, but software designers, are stunningly, hopelessly, pathetically, uselessly, staggeringly, mind-blowingly stupid.
Note that the same piece of consumer software put a HUGE amount of effort in to enable REAL TIME SMILEYS .... if you happen to type a smiley :) it notices that in real time as you type, and animates a yellow and black smiley there for you. Wow!
(thanks JPM!)
January 21, 2005
Electronic Contracting (WEC '05)
WEC '05 has announced their call for papers. You have until 28th Feb to get your submissions to them. The workshop itself is 18th July, in Munich.
This new workshop looks at contracts on the net, and my paper on The Ricardian Contract was presented at the San Diego event last year (presentation actually given by Mark Miller!). The keynote was given by Nick Szabo, the inventor of the smart contracts concept.
The idea of doing contracts over the net has always been there. People expected it to take off and sweep the world in the mid 90s, like every other thing. Yet very little has occurred, and my own experiences with the Ricardian Contract remained for a decade about as far forward as we had got with practical digitally signed contracts. (Recently, it seems that Estonia's national smart card system has been used for contractual negotiations, so it's a bit of a competition now.)
I have a new perspective on why this and other things didn't take off. I'm writing it up in a paper form, but I doubt it will be ready for this conference (maybe for the one Adam just posted on). In a nutshell, the reason contracting remains a pipe dream is because we haven't got the infrastructure in place as yet. What precisely that infrastructure is, I'm writing up!
Second IEEE International Workshop on
Electronic Contracting (WEC '05)
July 18, 2005, Munich, Germany
http://www.hpl.hp.com/personal/Claudio_Bartolini/Wec05.html
Call for Papers
Real world commerce is largely built on a fabric of contracts. Considered abstractly, a contract is an agreed framework of rules used by separately interested parties to coordinate their plans in order to realize cooperative opportunities, while simultaneously limiting their risk from each other's misbehavior. Electronic commerce is encouraging the growth of contract-like mechanisms whose terms are partially machine understandable and enforceable.
Building on the success of the First IEEE International Workshop on Electronic Contracting (WEC-04), this second edition is the forum to discuss innovative ideas at the interface between business, legal, and formal notions of contracts. The target audiences will be mainly researchers, scientists, software architects, but also contract lawyers, economists, and industry professionals who need to be acquainted with the state of the art technologies and the future trends in electronic contracting. The event will take place in Munich, Germany on July 18, 2005. IEEE WEC 2005 will be held in conjunction with The International Conference on Electronic Commerce (IEEE CEC 2005).
Topics of interest include but are not limited to the following:
Contract languages and user interfaces
Computer aided contract design, construction, and composition
Computer aided approaches to contract negotiation
Role of electronic contracts in IT governance
Relationship of electronic and legal enforcement mechanisms
Electronic vs. legal concepts of non-repudiation
Privacy vs. reputation and recourse
Contracts and mechanism design
Submissions
Authors are invited to submit original and significant research contributions in the aforementioned areas. All submissions will be peer-reviewed by the members of the international program committee. We are negotiating to publish the proceedings in the Springer Lecture Notes in Computer Science. Full papers must not exceed 16 pages and conform to the LNCS style. We accept papers in PDF and PS format.
Important Dates
Paper submission: February 28, 2005
Paper notification: April 7, 2005
Camera-ready papers: April 30, 2005
Workshop Date: July 18, 2005
Workshop Chairs
Claudio Bartolini, HP Laboratories, USA, claudio.bartolini@hp.com
Mathias Sallé, HP Laboratories, USA, mathias.salle@hp.com
Program Committee
Samuil Angelov (Eindhoven University of Technology, The Netherlands)
Boualem Benatallah (University of New South Wales, Australia)
Asit Dan (IBM Research, USA)
Aspassia Daskalopulu (University of Thessaly, Greece)
Marlon Dumas (Queesland University of Technology, Australia)
Andrew Farrell (Imperial College London, UK)
Anthony Finkelstein (University College London, UK)
Chiara Francalanci (Politecnico di Milano, Italy)
Claude Godart (University Henri Poincaré Nancy 1 and INRIA, France)
Ian Grigg (Systemics, USA)
Alexander Keller (IBM Research, USA)
Cuihong Li (Carnegie-Mellon University, USA)
Heiko Ludwig (IBM Research, USA)
Emil Lupu (Imperial College London, UK)
Tom Maibaum (McMaster University, Canada)
Dave Marvit (Fujitsu Laboratories, USA)
Zoran Milosevic (DSTC, Australia)
Enrico Nardelli (NESTOR - Universita' di Roma Tor Vergata, Italy)
Andrea Omicini (University of Bologna, Italy)
Barbara Pernici (Politecnico di Milano, Italy)
Chris Preist (HP Laboratories, UK)
Wim Van Grembergen (University of Antwerp, Belgium)
Andreas Wombacher (University of Twente, The Netherlands)
Internet 'Phishing' Scams Getting More Devious
There are about 10 articles a day on phishing, so I don't read them. What else is there to say that hasn't been said since years ago? Including the fact that it gets better and better, it's enough to drive a security guy to drink. Anyway, here's a good summary article to set a flag on the date, and an even briefer summary paragraph:
57 million americans, 122 "brands", organised crime, DNS redirection attacks, half based on spyware, convergance, get a hardware token, and this corker of a closing argument:
"Internet engineers should also figure out a way to authenticate Web addresses, much as they are currently figuring out how to make sure e-mail addresses are legitimate, he said."
Wed Jan 19, 3:03 PM ET
Internet 'Phishing' Scams Getting More Devious
By Andy Sullivan
WASHINGTON (Reuters) - Internet "phishing" scams are becoming more difficult to detect as criminals develop new ways to trick consumers into revealing passwords, bank account numbers and other sensitive information, security experts say.
Scam artists posed as banks and other legitimate businesses in thousands of phishing attacks last year, sending out millions of "spam" e-mails with subject lines like "account update needed" that pointed to fraudulent Web sites.
These attacks now increasingly use worms and spyware to divert consumers to fraudulent sites without their knowledge, experts say.
"If you think of phishers initially as petty thieves, now they're more like an organized crime unit," said Paris Trudeau, senior product manager for Internet-security firm SurfControl.
Phishing attacks have reached 57 million U.S. adults and compromised at least 122 well-known brands so far, according to several estimates.
At the end of 2004 nearly half of these attacks contained some sort of spyware or other malicious code, Trudeau said.
One attack, first documented last month by the Danish security firm Secunia, misdirects Web surfers by modifying a little-known directory in Microsoft Windows machines called a host file. When an Internet user types a Web address into a browser, he is directed instead to a fraudulent site.
This technique has shown up in attacks spoofing several South American banks, said Scott Chasin, chief technical officer of the security firm MX Logic.
The convergence of all of these threats means "we can expect to see some large attacks in the near term," he said.
Another more ambitious attack targets the domain-name servers that serve as virtual telephone books, matching domain names with numerical addresses given to each computer on the Internet.
IDENTITY THIEVES
If one of those computers is compromised, Internet users who type in "www.bankofamerica.com" could be directed to a look-alike site run by identity thieves.
Domain-name servers are tougher to crack, as they are typically run by businesses rather than home users, but hackers can find a way in by posing as a company's tech-support department and asking new employees for their passwords, Trudeau said.
Domain-name hijacking is suspected in incidents involving Google.com, Amazon.com, eBay Germany and HSBC Bank of Brazil, Chasin said.
Even straightforward phishing attacks are getting more sophisticated. Spelling errors and mangled Web addresses made early scams easy to spot, but scam artists now commonly include legitimate-looking links within their Web addresses, said Kate Trower, associate product manager of protection software for EarthLink Inc.
Consumers who click on links like www.citibank.com in these messages are directed to a fraudulent Web address buried in the message's technical code, she said.
MasterCard International has caught at least 10 phishing scams involving www.mastercard.com over the past two months, said Sergio Pinon, senior vice president of security and risk services.
Consumers can protect themselves with software that screens out viruses, spyware and spam. But online businesses will have to take steps as well, perhaps by issuing customers a physical token containing a changing password, Chasin said.
Internet engineers should also figure out a way to authenticate Web addresses, much as they are currently figuring out how to make sure e-mail addresses are legitimate, he said.
Copyright © 2005 Reuters Limited. All rights reserved.
http://story.news.yahoo.com/news?tmpl=story&cid=581&e=4&u=/nm/20050119/tc_nm/tech_phishing_dc
January 19, 2005
Online or Invisible - the case for open publication
Adam has pointed me to a paper on citation rates for open work: "Online or Invisible" by Steve Lawrence. In brief, it suggests that if ones work is openly available on the web, it is cited 3-4 as many times in others' work.
It has been blindingly obvious for a decade now that the letters 'WWW' signalled the end of the academic publishing industry. The latter's only value added was their ability to get the words distributed, for which they charged a fee. Well, WWW does that for free.
But there are still lots of holdouts. Academic conferences still walk the party line and want sign-over of copyrights. Their logic runs thusly; in order to attract academics they have to show a formal academic proceedings which distributes their work. The proceedings publisher requires to own the copyright so as to benefit from reprints and subsidise the costly distribution of the books.
But this was a confusion of means with ends. The end required is the distribution of the work, not the attraction of a well reputed journal. That's only the preferred means in a pre-WWW world. Now, as I say, this should have been blindingly obvious, but it wasn't and is perhaps the best evidence of scientists not understanding basic economics and marketing processes. We now have some scientific evidence that using a 'reputable scientific journal' will reduce the distribution of the work. Of course, the paper, published by Nature, is available online.
What's this to do with FC? A lot; by analogy, the same story is being told by the DRM school - music and films. Slightly different calculations but the same bases in economics. Just much more money and dollops of politics, law and crypto.
January 15, 2005
T-mobile cracker also hacks Proportionality with Embarrassment
All the blogs (1, 2, 3) are buzzing about the T-Mobile cracker. 21 year old Nicolas Jacobsen hacked into the phone company's database and lifted identity information for some 400 customers, and also scarfed up a photos taken by various phone users. He sold these and presumably made some money. He was at it for at least 6 months, and was picked up in an international sweep that netted 28 people.
No doubt the celebrity photos were embarrassing, but what was cuter was that he also lifted documents from the Secret Service and attempted to sell them on IRC chat rooms!
One would suppose that he would find himself in hot water. Consider the young guy who tried to steal a few credit cards from a hardware store by parking outside and using his laptop to wirelessly hack in and install a trojan. He didn't succeed in stealing anything, as they caught him beforehand. Even then, the maximum he was looking at was 6 credit card numbers. Clearly, a kid mucking around and hoping to strike lucky, this was no real criminal.
He got 12 years. That's 2 years for every credit card he failed to steal.
If proportionality means anything, Jacobsen is never ever going to see sunlight again. So where are we now? Well, the case is being kept secret, and the Secret Service claim they can't talk about it. This is a complete break with tradition, as normally the prosecution will organise a press circus in order to boost their ratings. It's also somewhat at odds with the press release they put out on the other 19 guys they picked up.
The answer is probably that which "a source" offers: "the Secret Service, the source says, has offered to put the hacker to work, pleading him out to a single felony, then enlisting him to catch other computer criminals in the same manner in which he himself was caught. The source says that Jacobsen, facing the prospect of prison time, is favorably considering the offer."
Which is fine, except the hardware shop hacker also helped the hardware store to fix up their network and still got 12 years. The way I read this message is that proportionality - the punishment matching the crime - is out the window, and if you are going to hack, make sure you hack the people who will come after you to the point of ridicule.
January 09, 2005
Identity Theft: Why Hollywood has to take one for the team.
The Year of the Phish has passed us by, and we can relax in our new life swimming in fear of the net. Everyone now knows about the threats, even the users, but what they don't know is what happens next. My call: it's likely to get a lot worse before it gets better. And how it gets better is not going to be life as we knew it. But more on that later.
First... The Good News. There is some cold comfort for those not American. A recent report had British phishing loses under the millions. Most of the rich pickings are 'over there' where credit rules, and identity says 'ok'. And even there, the news could be construed as mildly positive for those in need of good cheer. A judge recently ruled a billion dollar payout against spammers who are identified in name, if not in face. We might never see their faces, but at least it feels good. AOL reported spam down by 75% but didn't say how they did it.
Also, news that Microsoft is to charge extra for security must make us believe they have found the magic pixie dust of security, and can now deliver an OS that's really, truly secure, this time! Either that, or they've cracked the conundrum of how to avoid the liability when the masses revolt and launch the class action suit of the century.
All this we could deal with, I guess, in time, if we could as an industry get out collective cryptographic act together and push the security models over to protecting users (one month's coding in Mozilla should do it, but oh, what a long month it's been!). But there is another problem looming, and it's ...
The Bad News: the politicians are now champing at the bit, looking for yet another reason to whip today's hobby horse of 'identify everyone' along into more lather. Yes, we can all mangle metaphors, just as easily as we can mangle security models. Let me explain.
The current project to identify the humanity of the world will make identity theft the crime of the century. It's really extraordinarily simple. The more everything rests on Identity, the more value will Identity have. And the more value it has, the more it will be worth to steal.
To get a handle on why it is more valuable, put yourself in the shoes of an identity thief. Imagine our phisher is three years old, and has a sweet tooth for data.
How much sugar can there be found in a thousand cooperating databases? Each database perfectly indexed with your one true number and bubbling over with personal details, financial details, searchable on demand. A regulatory regime that creates shared access to a thousand agencies, and that's before they start sharing with other countries?
To me, it sounds like the musical scene in the sweets factory of Chitty Chitty Bang Bang, where the over indulgent whistle of our one true identity becomes our security and dentistry nightmare. When the balance is upset, pandemonium ensues. (I'm thinking here the Year of the Dogs, and if you've seen the movie you will understand!)
Now, one could ask our politicians to stop it, and at once. But it's too late for that, they have the bits of digital identity between their teeth, and they are going to do it to us to save us from phishing! So we may as well be resigned to the fact that there will be a thousand interlinked identity databases, and a 100 times that number of people who have the ability to browse, manipulate, package, steal and sell that data. (This post is already too long, so I'm going to skip the naivete of asking the politicians to secure our identity, ok? )
A world like that means credit will come tumbling down, as we know it. Once you know everything about a person, you are that person, and no amount of digital hardware tokens or special biometric blah blahs will save the individual from being abused. So what do people do when their data becomes a phisher's candyfest?
People will withdraw from the credit system and move back to cash.This will cost them, but they will do it if they can. Further, it means that net commerce will develop more along the lines of cash trading than credit trading. In ecommerce terms, you might know this better as prepaid payment systems, but there are a variety of ways of doing it.
But the problem with all this is that a cash transaction has no relationship to any other event. It's only just tractable for one transaction: experienced FCers know that wrapping a true cash payment into a transaction when you have no relationship to fall back to in event of a hiccup is quite a serious challenge.
So we need a way to relate transactions, without infecting that way with human identity. Enter the nym, or more fully known as the psuedonymous identifier. This little thing can relate a bunch of things together without needing any special support.
We already use them extensively in email, and in chat. There are nyms like iang which are short and rather tricky to use because there are more than one of us. We can turn it into an email address, and that allows you to send a message to me using one global system, email. But spam has taught us a lesson with the email address, by wiping out the ease and reliability of the email nym ... leading to hotmail and the throw away address (for both offense and defense) and now the private email system.
Email has other problems (I predict it is dying!) which takes us to Instant Messaging (or chat or IM). The arisal of the peer-to-peer (p2p) world has taken nyms to the next level: disposable, and evolutionary.
This much we already know. P2P is the buzzword of the last 5 years. It's where the development of user activity is taking place. (When was the last time you saw an innovation in email? In browsing?)
Walking backwards ... p2p is developing the nym. And the nym is critical for creating the transactional framework for ecommerce. Which is getting beaten up badly by phishing, and there's an enveloping pincer movement developing in the strong human identity world.
But - and here's the clanger - when and as the nymous and cash based community develop and overcome their little difficulties, those aforementioned forces of darkness are going to turn on it with a vengeance. For different reasons, to be sure. For obvious example, the phishers are going to attack looking for that lovely cash. They are going to get rather rabid rather quickly when they work out what the pickings are.
Which means the mother of all security battles is looming for p2p. And unfortunately, it's one that we have to win, as otherwise, the ecommerce thing that they promised us in the late nineties is looking like a bit more like those fairy tales that don't have a happy ending. (Credit's going to be squeezed, remember.)
The good news is that I don't see why it can't be won. The great thing about p2p is the failure of standards. We aren't going to get bogged down by some dodgy 80's security model pulled out of the back pages of a superman comic, like those Mr Universe he-man kits that the guy with the funny name sold. No, this time, when the security model goes down in flames (several already have) we can simply crawl out of the wreckage, dust off and go find another fighter to fly into battle.
Let's reel off those battles already fought and won and lost. Napster, Kazaa, MNet, Skype, BitTorrent. There are a bunch more, I know, I just don't follow them that closely. Exeem this week, maybe I do follow them?
They've had some bad bustups, and they've had some victories, and for those in the systems world, and the security world, the progress is quite encouraging. Nothing looks insurmoutable, especially if you've seen the landscape and can see the integration possibilities.
But - and finally we are getting to the BIG BUT - that means whoever these guys are defeating ... is losing! Who is it? Well, it's the music industry. And hollywood.
And here's where it all comes together: ecommerce is going to face a devastating mix of over rich identity and over rich phishers. It'll shift to cash based and nym based, on the back of p2p. But that will shift the battle royale into p2p space, which means the current skirmishes are ... practice runs.
And now we can see why Hollywood is in such a desperate position. If the current battle doesn't see Hollywood go down for the count, that means we are in a world of pain: a troubling future for communication, a poor future for ecommerce, and a pretty stark world for the net. It means we can't beat the phisher.
Which explains why Hollywood and the RIAA have found it so difficult to get support on their fight: everyone who is familiar with Internet security has watched and cheered, not because they like to see someone robbed, but because they know this fight is the future of security.
I like Hollywood films. I've even bought a few kilograms of them. But the notion of losing my identity, losing my ability to trade and losing my ability to communcate securely with the many partners and friends I have over the net fills me with trepidation. I and much of the academic and security world can see the larger picture, even if we can't enunciate it clearly. I'd gladly give up another 10 years of blockbusters if I can trade with safety.
On the scales of Internet security, we have ecommerce on one side and Hollywood on the other. Sorry, guys, you get to take one for the team!
Addendum: I've just stumbled on a similar essay that was written 3 weeks before mine: The RIAA Succeeds Where the Cypherpunks Failed by Clay Shirky.
January 08, 2005
Skype analysed - Jedi Knights of the Crypto Rebellion, Score 1
Adam picked up an article analysing Skype. For those on the cutting edge, you already know that Skype is sweeping the boards in VOIP, or turning your computer into a phone. Download it today ... if you have a Mac. Or Linux or even Windows. (I don't.)
What might be less well known is that Skype put in crypto to secure the telephone conversation. This means that eavesdroppers can't ... well, eavesdrop! Great stuff. Now, even better, they built it themselves, so not only do we have a secure VOIP solution, downloadable for free, but we also have a mystery on our hands: is it really secure?
Unfortunately, we don't know for sure as they didn't release the source. And they won't say a thing ... Simson Garfinkel looked at the packets and the sorta look encrypted. Or compressed .. or something.
So where are we? Well, it's still a darn sight better than anything else. Go guys! We have a clear benefit over anything else on the table.
And even if it's not secure, nobody knows that. We have to wait until the cryptanalysts have pored over the packets and found the weaknesses. Or, more likely, the hackers have disassembled the core crypto code, worked out what it does, and handed the crypto guys the easy bit.
Even after they announce a weakness, it's still secure! Because nobody can exploit it, until someone else comes up with a toolkit to breach and exploit the weaknesses. (Generally, it's a different group of people, don't ask me why.)
But, even then it's still secure! Simply because nobody bothers to download the exploit and listen to people's conversation. Get real, there aren't exactly hordes of people driving around listening to poorly secured WEP connections (exploit available!) now are there?
The measure of security is positively dependent on the cost to the *attacker*. So an attacker still has to download the exploit, attach the alligator clips to the ethernet, sit in the van, chew donuts, drink bad coffee and listen to bad jokes while waiting for the call. Well, maybe, but a full analysis of the attacker's costs for eavesdropping shows ... it's too sodding expensive, even with the exploit available. Don't worry about it.
In which case, Skype gives you great security, a bit like the momentous defeat of the GSM crypto protocol over the paparazzi scanners! Scoreboard: Jedi Knights of the Crypto Rebellion, 1. Forces of the Dark Empire, 0.
January 07, 2005
The Case Of The Bandwidth Burglar
For those looking for stories of connivance, perfidy and sheer desperate cunning, normally we'd refer you to detective novels and the like. But now you can find the same thing on the net, and what's more, time reading them can be billed against your budget for governance!
Over on a blog by 'SecurityMonkey' there is a story called The Case Of The Bandwidth Burglar. SecurityMonkey is some sort of Canadian literary bdsmer who makes his readers bite their nails to the third nuckle waiting for days for the next installment. But that's all over and you can read all five installments in one pleasant saturday morning now.
Be warned, moral dilemmas, unhealthy influence of caffeine, and system administrators seen thinking and working, ahead. Not for the squeamish.
The Case Of The Bandwidth Burglar - Part I
The Case Of The Bandwidth Burglar - Part II
The Case Of The Bandwidth Burglar - Part III
The Case Of The Bandwidth Burglar - Part IV
The Case Of The Bandwidth Burglar - Conclusion
January 04, 2005
Accountants list the tech problems, Security and Sarbanes-Oxley take pole positions
A tech survey by accountants gives some interesting tips on security. The reason it is credible is because the authors aren't from our industry, so they can be expected to approach this without the normal baggage of some security product to sell. Of course their own is for sale, but that's easy to factor out in this case.
Security is still the Number One concern that accountants are seeing out there. That makes sense. It accords with everything we've seen about the phishing and identity theft explosions over the last couple of years.
Second is electronic document management. Why now? This issue has been around for yonks, and businesses have been basically doing the paperless office as and when they could. My guess is that things like Sarbanes-Oxley, Basel II and various lesser well named regulatory attacks on governance have pushed this to the fore. Now, if you haven't got your documents under control (whatever that means) you have a big risk on your hands.
Third is Data Integration. This echoes what I've seen in finance circles of late; they have gone through a phase of automating everything with every system under the sun. Now, they're faced with tieing them all together. The companies selling product at the moment are those with tools to ease the tying of things together. But so far, the companies are not exactly enticed, with many companies dreading yet another cycle based on the current web services hype.
Spam has slipped to Fourth in the rankings of the "biggest concerns". The article tries to hint at this as a general easing of the problem, but I'd suggest caution: there are far too many ways in which this can be misinterpreted. For example, the huge increase in security concerns over the last year have probably and simply overshadowed spam to the extent that spam may well have doubled and we'd not have cared. Identity Theft is now on the agenda, and that puts the spam into context. One's a nuisance and the other's a theft. Internet security experts may be bemused, but users and accountants can tell the difference.
For the rest, read on...
Information Security Once Again Tops AICPA Tech List
Jan. 3, 2005 (SmartPros) For the third consecutive year, information
security is the country's number one technology concern, according to the
results of the 2005 Top Technologies survey of the American Institute of
Certified Public Accountants.
The survey, conducted annually since 1990, seeks to determine the 10 most
important technology issues for the coming year. There were more than 300
participants in the 2005 survey, a 30 percent increase over the previous
year.
Interestingly, spam technology -- an issue closely associated with
information security -- apparently has lost some currency. It made its debut
on the 2004 list at number two. On the new list, it falls to number four.
"Because our work and personal lives are now inextricably linked to
information systems, security will always be top of mind," said Roman
Kepczyk, CPA/CITP, Chair of the AICPA's Information Technology Executive
Committee. Commenting on spam technology's lower placement on the list, he
said, "We've seen major improvements to filtering systems, which have
allowed us to bring spam under greater control. This most likely is the
reason that spam technology doesn't command the importance it did in the
previous survey."
A different issue closely allied with information security -- electronic
data management, or the paperless office -- moved up to second place. It was
number three last year.
There are two debuts on the Top Technologies list: authentication
technologies and storage technologies. Another issue, learning and training
competency, reappears at number 10 after an absence of three years.
The following are the 2005 Top 10 Technologies:
1.. Information Security: The hardware, software, processes and procedures
in place to protect an organization's information systems from internal and
external threats.
2.. Electronic Document Management (paperless or less-paper office): The
process of capturing, indexing, storing, retrieving, searching and managing
documents electronically. Formats include PDF, digital and image store
database technologies.
3.. Data Integration: The ability to update one field and have it
automatically synchronize between multiple databases, such as the
automatic/seamless transfer of client information between all systems. In
this instance, only the data flows across systems from platform to platform
or application to application. Data integration also involves the
application-neutral exchange of information. For example, the increased use
of XBRL (eXtensible Business Reporting Language) by companies worldwide
provides for the seamless exchange and aggregation of financial data to meet
the needs of different user groups using different applications to read,
present and analyze data.
4.. Spam Technology: The use of technology to reduce or eliminate unwanted
e-mail commonly known as Spam.
5.. Disaster Recovery: The development, monitoring and updating of the
process by which organizations plan for continuity of their business in the
event of a loss of business information resources through theft,
virus/malware infestation, weather damage, accidents or other malicious
destruction. Disaster recovery includes business continuation, contingency
planning and disk recovery technologies and processes.
6.. Collaboration and Messaging Applications: Applications that allow
users to communicate electronically, including e-mail, voicemail, universal
messaging, instant messaging, e-mailed voice messages and digital faxing.
Examples include a computer conference using the keyboard (a keyboard chat)
over the Internet between two or more people.
7.. Wireless Technologies: The transfer of voice or data from one machine
to another via the airwaves and without physical connectivity. Examples
include cellular, satellite, infrared, Bluetooth, WiFi, 3G, 2-way paging,
CDMA, Wireless/WiMax and others.
8.. Authentication Technologies (new): The hardware, software, processes
and procedures to protect a person's privacy and identity from internal and
external threats, including digital identity, privacy and biometric
authentication.
9.. Storage Technologies (new): Storage area networks (SAN) include mass
storage, CD-recordable, DVD, data compression, near field recording,
electronic document storage and network attached storage (NAS), as well as
small personal storage devices like USB drives.
10.. Learning and Training Competency (End Users): The methodology and
curriculum by which personnel learn to understand and use technology. This
includes measuring competency, learning plans to increase the knowledge of
individuals, and hiring and retaining qualified personnel with career
opportunities that retain the stars.
Also, each year the AICPA Top Technologies Task Force prepares a "watch
list" of five emerging technologies [...]
http://accounting.smartpros.com/x46436.xml
January 03, 2005
Frank Abagnale at CSI - Know me if you can
Axel's blog points to a storm in a teacup over at a professional association called the Computer Security Institute. It seems that they invited Frank Abagnale to keynote at their conference. Abagnale, if you recall, is the infamous fraudster portrayed in the movie Catch me if you can.

Many of the other speakers kicked up a fuss. It seems they had ethical qualms about speaking at a conference where the 'enemy' was also presenting. Much debate ensued, alleges Alex, about forgiveness, holier than thou attitudes and cashing in on notoriety.
I have a different perspective, based on Carl von Clausewitz's famous aphorism. He said something to the extent of "Know yourself and you will win half your battles. Know your enemy and you will win 99 battles out of a hundred." Those speakers who complained or withdrew have cast themselves as limited to the first group, the self-knowers, and revealed themselves as reliable only to win every second battle.
Still, even practitioners of narrow horizons should not be above learning from those who see further. So why is there such a paranoia of only dealing with the honest side in the security industry? This is the never-ending white-hat versus black-hat debate. I think the answer can be found in guildthink.
People who are truly great at what they do can afford to be magnaminous about the achievements of others, even those they fight. But most are not like that, they are continually trapped in a sort of middle level process-oriented tier, implementing that which the truly great have invented. As such, they are always on the defensive for attacks on their capabilities, because they are unable to deal at the level where they can cope with change and revolution.
This leads the professional tiers to always be on the lookout for ways to create "us" and "them." Creating a professional association is one way, or a guild, to use the historical term.

Someone like Frank Abagnale - a truly gifted fraudster - has the ability to make them look like fools. Thus, he scares them. The natural response to this is to search out rational and defensible ways to keep him and his ilk on the outside, in order to protect the delicate balance of trade. For that reason, it is convenient to pretend to be morally and ethically opposed to dealing with those that are convicted. What they are really saying is that his ability to show up the members for what they are - middle ranking professionals - is against their economic interests.
In essence, all professionals do this, and it should come as no surprise. All associations of professionals spend a lot of their time enhancing the credibility of their members and the dangers of doing business with those outside the association. So much so that you won't find any association - medical, accounting, engineering, or security - that will admit that this is all normal competitive behaviour. (A quick check of the CSI site confirms that they sell training, and they had a cyberterrorism panel. Say no more...)
So more kudos to the CSI for breaking out of the mold of us and them! It seems that common sense won over and Frank attended. He can be seen here in a photo op, confirming his ability to charm the ladies, and giving "us" yet another excuse to exclude him from our limited opportunities with "them" !
January 02, 2005
Chip&Pin liability shifts from UK bank to retailer
This weekend, there was apparently a big shift in liability in the UK retail payments market. From the BBC. Over the last year (2004) something like 600k of the 860k automated tills have been upgraded to use a new chip&pin method of account authorisation. This method is new to the UK at least, the Continentals have been using it for yonks.
What was interesting was that those who have not yet upgraded have now been lumbered with the liability. This is one of those vexing issues that circulate around soft money transactions; when the transaction gets rolled back, who carries the cost?
Traditionally, it has been said that the larger party is "more responsible." In more than one sense of the phrase. But, banks have always balked at this, and have always sought ways to shift out of the liability as much as anyone lets them.
In this case, the deal appears to be that the retailers upgrade to chip&pin, and in return they no longer have to check for signatures and identity on signed transactions. That's worthwhile. But if they choose to not upgrade, then they incur the shift in liability. (Quite how this was done in legal or contract terms is probably not something they want anyone to poke into.)
So banks are still on the hook for transactions through upgraded terminals, which would amount to most of them, they hope. I guess we would now expect to see a lot of hacker attention in how to copy the cards and steal the pins; given the inherent _two_factor_ security involved here, that will be a lot harder. But not undoable.
http://news.bbc.co.uk/1/hi/uk/4139211.stm
http://www.everywoman.co.uk/technology/article.asp?id=1630&switch=true
January 01, 2005
Journal of Internet Banking and Commerce
Recent grumbles in the comments to the recent FC papers post brought to mind an old journal called JIBC. I'd lost my "subscription" reminder to it many years ago and I guess I just assumed it had stopped. But, no, a little googling and I found it: the Journal of Internet Banking and Commerce. It is still pushing out 2-3 editions per year.
Back in the very early years, JIBC was there and publishing before things like the Financial Cryptography term had even been coined by Bob Hettinga. So I'm happy to come back and cheer them into the last year of their decade, given that the the first edition of this venerable journal was January 1996!
Some highlights include a regular column by Dave Birch, an article asking Why does SSL dominate the e-payment market ?, and an article predicting the return of digital cash in Waves Of Multimedia Banking Development.
JIBC published my second paper in 1997, the Critique on the 1994 EU Report on Prepaid Cards. Sometimes papers work out well, the lessons in that one are still useful in comparison to where Europe is now. So say I, at least.