June 27, 2013
Did Alan Greenspan blow the bubble that blew up the world?
If you, like me, are a fan of Alan Greenspan, you'd also be wondering what went wrong in the 2000s. His book is enlightening, but not conclusive. Observations that there were a series of heart-starting adrenalin injections into the economy -- the dotcom crash, 9/11, Fannie Mae, Bear-Stearns and Lehman Brothers, 2007, etc -- are illuminating but again not conclusive.
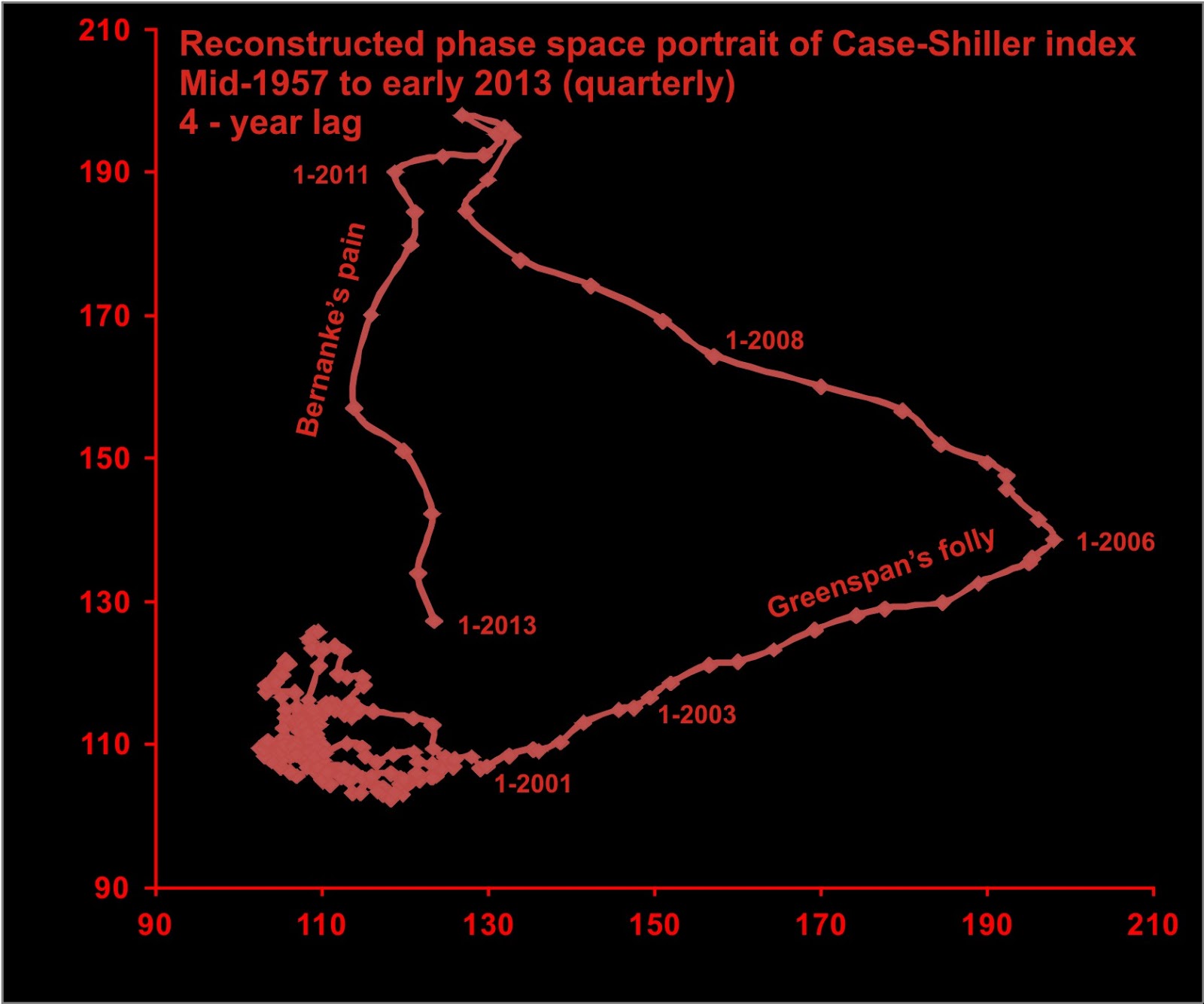
Even to establish that the train ran off the tracks is hard. Here comes a graph from WorldComplex blog (h/t to Zerohedge) that pretty much nails it:
The train not only ran off the tracks, it left the reservation. The beauty of these graphs is that you don't even have to understand them to realise that something really crazy happened after 2000.
But that said, let's try and interpret them. The graph shows accelerating USA housing prices beyond the norm. The pre-2000 blob(s) on the bottom left corner shows stability over the long run, which is to say that housing prices were stable across the USA, over time. For the norm, housing prices were a direct reflection of the rest of the economy, and in stability.
Then, movement to the right shows rapidly increasing prices, as it measures the index of prices for a given year over 4 years before. Movement to the left shows rapid collapse, the reverse. Movement up&right shows overall (sustained?) increase in prices, movement down& left shows overall (sustained?) lowering.
 I think then, this is compelling evidence. There was a bubble blown from the year 2000 to 2006 of epic proportions. It then collapsed between 2006 and 2013, still on-going (we're still 20 points above long run stability).
I think then, this is compelling evidence. There was a bubble blown from the year 2000 to 2006 of epic proportions. It then collapsed between 2006 and 2013, still on-going (we're still 20 points above long run stability).
Only the Federal Reserve could blow such a bubble. And, it was done on Alan Greenspan's watch.
I'm still a fan of the magician. He did, overall, a far better job than Bernanke is doing right now. But, there is no doubt that the Federal Reserve lost the plot while under Greenspan's watch.
Which, for future economic historians, leaves a compelling research project: what went wrong? And for the rest of us, a mess.
June 25, 2013
2 ways out of crushing debt
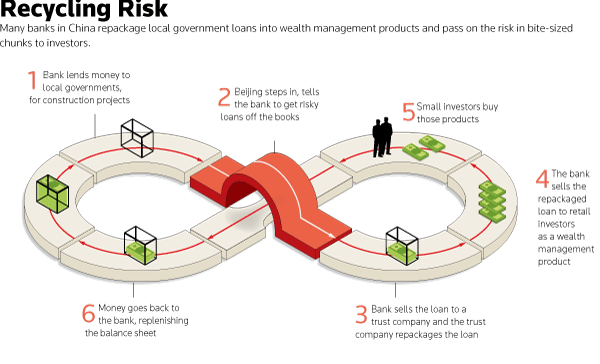 From Chris's FinancialServicesClub,
From Chris's FinancialServicesClub,
(I’m a bank teller at a large national bank. A customer in her mid-twenties comes up to my till.)Me: “Welcome to [bank name]! How can I help you today?”
Customer: “Yeah, can I find the total amount I owe for my student loans?”
Me: “Sure, what is your full name?”
(She gives me her name, and I give her the amount owed. It is a fairly large amount.)
Customer: “Perfect!”
(With a large smile, she hands me a cashier check from another bank, for the exact amount, totally paying off all loans she has with this bank. I enter the info, and print her receipt. I quickly run to the back to see my manager.)
Me: “Can I give this customer a couple of the promotional items that we usually give to people that open checking accounts?”
(My manager see the amount that she is paying, and that this means the customer has totally paid off the loans.)
Manager: “You can give her whatever you want!”
(I grab some items, and bring them back up to the till.)
Me: “Congratulations on paying off all your loans. Here’s your receipt, and a few gifts for paying off such a large loan amount.”
Customer: “Thank you very much! What I’m about to say has nothing to do with you; you are a great person, and thank you very much for the free gift. So, just go with everything I’m about to do.”
Me: “…Okay?”
(She holds up the receipt above her head, and speaks in a loud voice.)
Customer: “Ha! Six years ago I sold my soul to this bank! But after going through the nine circles of hell, I have finally gotten free of it! I now owe you nothing, zip, zero, nada! I am free; no more bills, payments, fees, nothing. I’M FREEEEEEE!”
(Even as she walks out the doors, she’s yelling and dancing. The dozen or so other customers and workers watch her the whole time. Another customer speaks loud enough so just about everyone can hear him.)
Customer #2: “Raise your hand if you wish you could do that.”
(Just about everyone else in the bank raises their hand.)
Strange and contradictory notions, indeed. In contrast, the impatient bears over at ZeroHedge point to Iceland:
Iceland Debt Forgiveness Reaches $2 Billion Since Crisis By Omar R. Valdimarsson - 2013-06-24T15:26:26ZIceland’s lenders have forgiven household debt equal to about 12.4 percent of gross domestic product since the island’s 2008 financial collapse.
Lenders had written off 212.2 billion kronur ($1.7 billion) in household debt through the end of 2012, the Icelandic Financial Services Association said in a letter to parliament. The group estimated a further 35.3 billion kronur will be forgiven this year after they recalculate loan agreements to meet a Supreme Court ruling.
About 141.2 billion kronur of that follows a ruling from the island’s top court stating that mortgage loans indexed to foreign exchange rates were illegal, it said.
The island’s biggest banks failed in October 2008, after defaulting on about $85 billion in debt. The collapse plunged the island’s economy into a crisis that sent unemployment surging nine-fold and triggered a recession.
The association said that of the total, 45.8 billion kronur in private debt was forgiven as part of an agreement that stipulated that debts exceeding 110 percent of a property’s value must be written off.
This is germane because, as ZeroHedge do not hesitate to remind us, "Iceland is so far the only success story in the continent of Europe, which continues sliding into an ever deeper depressionary black hole, as a result of the complete destruction of its financial sector and its subsequent rise from the ashes..."
If you're still interested, here's Chris's generational perspective and his gentle reminders that Britain has a "a £27.1 billion capital shortfall in the UK banking system" and a few random other troubled bank reports. Probably unimportant in the scheme of things.
Wait, one of those is a third way to get out of crushing debt:
Taped telephone recordings (from the bank's own systems) from inside doomed Anglo Irish Bank reveal for the first time how the bank's top executives lied to the Government about the true extent of losses at the institution. ...Anglo itself was within days of complete meltdown – and in the years ahead would eat up €30bn of taxpayer money. Mr Bowe speaks about how the State had been asked for €7bn to bail out Anglo – but Anglo's negotiators knew all along this was not enough to save the bank.
...The plan was that once the State began the flow of money, it would be unable to stop. Mr Bowe is asked by Mr Fitzgerald how they had come up with the figure of €7bn. He laughs as he is taped saying: "Just, as Drummer (then-CEO David Drumm) would say, 'picked it out of my arse'."
And a picture makes 4. I should change the title, but who cares about numerical accuracy these days?

June 19, 2013
On casting the first cyber-stone, USA declares cyberwar. Everyone loses.
Following on from revelations of the USA's unilateral act of cyberwar otherwise known as Stuxnet, it is now apparent to all but the most self-serving of Washington lobbyests that Iran has used their defeat to learn and launch the same weapons. VanityFair has the story:
On the hidden battlefields of history’s first known cyber-war, the casualties are piling up. In the U.S., many banks have been hit, and the telecommunications industry seriously damaged, likely in retaliation for several major attacks on Iran. Washington and Tehran are ramping up their cyber-arsenals, built on a black-market digital arms bazaar, enmeshing such high-tech giants as Microsoft, Google, and Apple.
The headline victim of the proxy war is the Saudi's state-run oil company bank called Saudi Aramco:
The data on three-quarters of the machines on the main computer network of Saudi aramco had been destroyed. Hackers who identified themselves as Islamic and called themselves the Cutting Sword of Justice executed a full wipe of the hard drives of 30,000 aramco personal computers. For good measure, as a kind of calling card, the hackers lit up the screen of each machine they wiped with a single image, of an American flag on fire.
Which makes the American decisions all the more curious.
For the U.S., Stuxnet was both a victory and a defeat. The operation displayed a chillingly effective capability, but the fact that Stuxnet escaped and became public was a problem.
How did they think this would not get out? What part of 'virus' and 'anti-virus industry' did they not understand?
Last June, David E. Sanger confirmed and expanded on the basic elements of the Stuxnet conjecture in a New York Times story, the week before publication of his book Confront and Conceal. The White House refused to confirm or deny Sanger’s account but condemned its disclosure of classified information, and the F.B.I. and Justice Department opened a criminal investigation of the leak, which is still ongoing.
In Washingtonspeak, that means they did it. Wired and NYT confirm:
Despite headlines around the globe, officials in Washington have never openly acknowledged that the US was behind the attack. It wasn’t until 2012 that anonymous sources within the Obama administration took credit for it in interviews with The New York Times. [snip...] Citing anonymous Obama administration officials, The New York Times reported that the malware began replicating itself and migrating to computers in other countries. [snip...] In 2006, the Department of Defense gave the go-ahead to the NSA to begin work on targeting these centrifuges, according to The New York Times.
We now have enough evidence to decide, beyond reasonable doubt, that the USA and Israel launched a first-strike cyber attack against an enemy it was not at war with. Which succeeded, damages are credibly listed.
Back to the VanityFair article: What made the Whitehouse think they wouldn't then unleash a tiger they tweaked by the tail?
Sanger, for his part, said that when he reviewed his story with Obama-administration officials, they did not ask him to keep silent. According to a former White House official, in the aftermath of the Stuxnet revelations “there must have been a U.S.-government review process that said, This wasn’t supposed to happen. Why did this happen? What mistakes were made, and should we really be doing this cyber-warfare stuff? And if we’re going to do the cyber-warfare stuff again, how do we make sure (a) that the entire world doesn’t find out about it, and (b) that the whole world does not fucking collect our source code?”
None of it makes sense unless we assume that Washington DC is so disconnected from the reality of the art of cyber-security. It gets worse:
One of the most innovative features of all this malware—and, to many, the most disturbing—was found in Flame, the Stuxnet precursor. Flame spread, among other ways, and in some computer networks, by disguising itself as Windows Update. Flame tricked its victim computers into accepting software that appeared to come from Microsoft but actually did not. Windows Update had never previously been used as camouflage in this malicious way. By using Windows Update as cover for malware infection, Flame’s creators set an insidious precedent. If speculation that the U.S. government did deploy Flame is accurate, then the U.S. also damaged the reliability and integrity of a system that lies at the core of the Internet and therefore of the global economy.
Which Microsoft is now conspiratorial in:
Microsoft Corp. (MSFT), the world’s largest software company, provides intelligence agencies with information about bugs in its popular software before it publicly releases a fix, according to two people familiar with the process. That information can be used to protect government computers and to access the computers of terrorists or military foes.Redmond, Washington-based Microsoft (MSFT) and other software or Internet security companies have been aware that this type of early alert allowed the U.S. to exploit vulnerabilities in software sold to foreign governments, according to two U.S. officials. Microsoft doesn’t ask and can’t be told how the government uses such tip-offs, said the officials, who asked not to be identified because the matter is confidential.
Frank Shaw, a spokesman for Microsoft, said those releases occur in cooperation with multiple agencies and are designed to give government “an early start” on risk assessment and mitigation.
In an e-mailed statement, Shaw said there are “several programs” through which such information is passed to the government, and named two which are public, run by Microsoft and for defensive purposes.
Notice the discord between those positions. Microsoft will now be vulnerable to civil suits around the world for instances where bugs were disclosed and then used against victims. Why is this? Why is the cozy cognitive dissonance of the Americans worthless elsewhere? Simple: immunity by the US Government only works in the USA. Spying, cyber attacks, and conspiracy to destroy state equipment are illegal elsewhere.
And:
For at least a decade, Western governments—among them the U.S., France, and Israel—have been buying “bugs” (flaws in computer programs that make breaches possible) as well as exploits (programs that perform jobs such as espionage or theft) not only from defense contractors but also from individual hackers. The sellers in this market tell stories that suggest scenes from spy novels. One country’s intelligence service creates cyber-security front companies, flies hackers in for fake job interviews, and buys their bugs and exploits to add to its stockpile. Software flaws now form the foundation of almost every government’s cyber-operations, thanks in large part to the same black market—the cyber-arms bazaar—where hacktivists and criminals buy and sell them. ...In the U.S., the escalating bug-and-exploit trade has created a strange relationship between government and industry. The U.S. government now spends significant amounts of time and money developing or acquiring the ability to exploit weaknesses in the products of some of America’s own leading technology companies, such as Apple, Google, and Microsoft. In other words: to sabotage American enemies, the U.S. is, in a sense, sabotaging its own companies.
It's another variant on the old biblical 30 pieces of silver story. The US government is by practice and policy undermining the trust in its own industry.
So where does this go? As I have oft mentioned, as long as the intelligence information collected stayed in the community, the act of spying represented not much of a threat to the people. But that is far different to aggressive first-strike attacks, and it is far different to industrial espionage run by the state:
Thousands of technology, finance and manufacturing companies are working closely with U.S. national security agencies, providing sensitive information and in return receiving benefits that include access to classified intelligence, four people familiar with the process said.These programs, whose participants are known as trusted partners, extend far beyond what was revealed by Edward Snowden, a computer technician who did work for the National Security Agency. The role of private companies has come under intense scrutiny since his disclosure this month that the NSA is collecting millions of U.S. residents’ telephone records and the computer communications of foreigners from Google Inc (GOOG). and other Internet companies under court order.
...
Along with the NSA, the Central Intelligence Agency (0112917D), the Federal Bureau of Investigation and branches of the U.S. military have agreements with such companies to gather data that might seem innocuous but could be highly useful in the hands of U.S. intelligence or cyber warfare units, according to the people, who have either worked for the government or are in companies that have these accords.
Pure intelligence for state purposes is no longer a plausible claim. Cyberwar is unleashed, pandorra's box is opened. The agency has crossed the commercial barriers, swapping product for information. With thousands of companies.
Back to the attack on Iran. Last week I was reading _The Rommel Papers_, the post-humous memoirs of the late great WWII general Erwin Rommel. In passing, he opined that when the 'terrorists' struck at his military operations in North Africa, the best strategy was to ignore it. He did, and nothing much happened. Specifically, he eschewed the civilian reprisals so popular in films and novels, and he did not do much or anything to chase up who might be responsible. Beyond normal police operations, presumably.
The USA's strategy for pinprick is the reverse of Rommel's. Attacks on the Iranians seem to elicit a response.
Sure enough, in August 2012 a devastating virus was unleashed on Saudi Aramco, the giant Saudi state-owned energy company. The malware infected 30,000 computers, erasing three-quarters of the company’s stored data, destroying everything from documents to email to spreadsheets and leaving in their place an image of a burning American flag, according to The New York Times. Just days later, another large cyberattack hit RasGas, the giant Qatari natural gas company. Then a series of denial-of-service attacks took America’s largest financial institutions offline. Experts blamed all of this activity on Iran, which had created its own cyber command in the wake of the US-led attacks.
So, let's inventory the interests here.
For uninvolved government agencies, mainstreet USA, banks, and commercial industry there and in allied countries, this is total negative: They will bear the cost.
For the NSA (and here I mean the NSA/CIA/DoD/Mossad group), there is no plausible harm. The NSA carries no cost. Meanwhile the NSA maintains and grows its already huge capability to collect huge amounts of boring data. And, launch pre-emptive strikes against Iran's centrifuges. And the program to sign up most of the USA's security industry in the war against everyone has yielded thousands of sign-ups, thus tarring the entirety of the USA with the same brush.
And indeed, for the NSA, the responses by Iran -- probably or arguably justifiable and "legal" under the international laws of war -- represent an opportunity to further stress their own growth. It's all upside for the them:
Inside the government, [General Alexander] is regarded with a mixture of respect and fear, not unlike J. Edgar Hoover, another security figure whose tenure spanned multiple presidencies. “We jokingly referred to him as Emperor Alexander—with good cause, because whatever Keith wants, Keith gets,” says one former senior CIA official who agreed to speak on condition of anonymity. “We would sit back literally in awe of what he was able to get from Congress, from the White House, and at the expense of everybody else.”
What about Iran? Well, it has made it clear that regime change is not on the agenda which is what the USA really wants. As it will perceive that the USA won't stop, it has few options but to defend. Which regime would be likely to back down when it knows there is no accomodation on the other side?
Iran is a specialist in asymmetric attacks (as it has to be) so we can predict that their Stuxnet inspiration will result in many responses in the past and the future. Meanwhile, the USA postures that a cyber attack is cause for going physical, and the USA has never been known to back down in face of a public lashing.
All signs point to escalation. Which plays into the NSA's hands:
The cat-and-mouse game could escalate. “It’s a trajectory,” says James Lewis, a cybersecurity expert at the Center for Strategic and International Studies. “The general consensus is that a cyber response alone is pretty worthless. And nobody wants a real war.” Under international law, Iran may have the right to self-defense when hit with destructive cyberattacks. William Lynn, deputy secretary of defense, laid claim to the prerogative of self-defense when he outlined the Pentagon’s cyber operations strategy. “The United States reserves the right,” he said, “under the laws of armed conflict, to respond to serious cyberattacks with a proportional and justified military response at the time and place of our choosing.” Leon Panetta, the former CIA chief who had helped launch the Stuxnet offensive, would later point to Iran’s retaliation as a troubling harbinger. “The collective result of these kinds of attacks could be a cyber Pearl Harbor,” he warned in October 2012, toward the end of his tenure as defense secretary, “an attack that would cause physical destruction and the loss of life.” If Stuxnet was the proof of concept, it also proved that one successful cyberattack begets another. For Alexander, this offered the perfect justification for expanding his empire.
Conclusion? The NSA are not going to be brought to heel. Congress will remain ineffective, shy of governance and innocent of the war it has signed-off on.
The cyber divisions are going to have their day in the field. And the businesses of the USA and its public allies are going to carry the cost of a hot cyberwar.
The U.S. banking leadership is said to be extremely unhappy at being stuck with the cost of remediation—which in the case of one specific bank amounts to well over $10 million. The banks view such costs as, effectively, an unlegislated tax in support of U.S. covert activities against Iran. The banks “want help turning [the DDoS] off, and the U.S. government is really struggling with how to do that. It’s all brand-new ground,” says a former national-security official. And banks are not the only organizations that are paying the price. As its waves of attacks continue, Qassam has targeted more banks (not only in the U.S., but also in Europe and Asia) as well as brokerages, credit-card companies, and D.N.S. servers that are part of the Internet’s physical backbone.
And, it's going to go kinetic.
...at a time when the distinction between cyberwarfare and conventional warfare is beginning to blur. A recent Pentagon report made that point in dramatic terms. It recommended possible deterrents to a cyberattack on the US. Among the options: launching nuclear weapons.
Not a smart situation. When you look at the causes of this, there isn't even a plausible cassus belli here. It's more like boys with too-big toys playing a first-person shoot-em-up video game, where they carry none of the costs of the shots.
But it gets worse. Having caused this entire war to come, the biggest boy with the biggest toy says:
Alexander runs the nation’s cyberwar efforts, an empire he has built over the past eight years by insisting that the US’s inherent vulnerability to digital attacks requires him to amass more and more authority over the data zipping around the globe. In his telling, the threat is so mind-bogglingly huge that the nation has little option but to eventually put the entire civilian Internet under his protection, requiring tweets and emails to pass through his filters, and putting the kill switch under the government’s forefinger. “What we see is an increasing level of activity on the networks,” he said at a recent security conference in Canada. “I am concerned that this is going to break a threshold where the private sector can no longer handle it and the government is going to have to step in.”
!
June 07, 2013
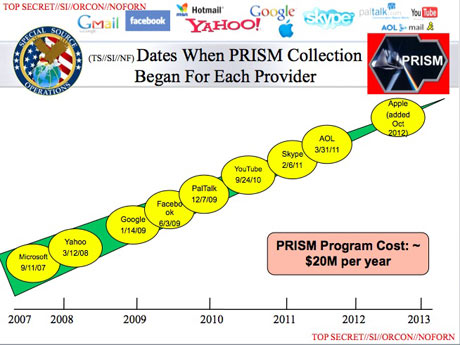
PRISM Confirmed: major US providers grant direct, live access to the NSA and FBI
 In an extraordinary clean sweep of disclosure from the Washington Post and the Guardian:
In an extraordinary clean sweep of disclosure from the Washington Post and the Guardian:
The National Security Agency and the FBI are tapping directly into the central servers of nine leading U.S. Internet companies, extracting audio and video chats, photographs, e-mails, documents, and connection logs that enable analysts to track foreign targets, according to a top-secret document obtained by The Washington Post.
The process is by direct connection to the servers, and requires no intervention by the companies:
Equally unusual is the way the NSA extracts what it wants, according to the document: “Collection directly from the servers of these U.S. Service Providers: Microsoft, Yahoo, Google, Facebook, PalTalk, AOL, Skype, YouTube, Apple.”....
Dropbox, the cloud storage and synchronization service, is described as “coming soon.”
From outside direct access might appear unusual, but it is actually the best way as far as the NSA is concerned. Not only does it give them access at Level Zero, and probably better access than the company has itself, it also provides the victim supplier plausible deniability:
“We do not provide any government organization with direct access to Facebook servers,” said Joe Sullivan, chief security officer for Facebook. ....“We have never heard of PRISM,” said Steve Dowling, a spokesman for Apple. “We do not provide any government agency with direct access to our servers, ..." ....
“Google cares deeply about the security of our users’ data,” a company spokesman said. “We disclose user data to government in accordance with the law, and we review all such requests carefully. From time to time, people allege that we have created a government ‘back door’ into our systems, but Google does not have a ‘back door’ for the government to access private user data.”
Microsoft also provided a statement: “.... If the government has a broader voluntary national security program to gather customer data we don’t participate in it.”
Yahoo also issued a denial. “Yahoo! takes users’ privacy very seriously,” the company said in a statement. “We do not provide the government with direct access to our servers, systems, or network.”
How is this apparent contradiction possible? It is generally done via secret arrangements not with the company, but with the employees. The company does not provide back-door access, but the people do. The trick is to place people with excellent tech skills and dual loyalties into strategic locations in the company. These 'assets' will then execute the work required in secret, and spare the company and most all of their workmates the embarrassment.

Patriotism and secrecy are the keys. The source of these assets is easy: retired technical experts from the military and intelligence agencies. There are huge numbers of these people exiting out of the armed forces and intel community every year, and it takes only a little manipulation to present stellar CVs at the right place and time. Remember, the big tech companies will always employ a great CV that comes highly recommended by unimpeachable sources, and leapfrogging into a stable, very well paid civilian job is worth any discomfort.
Everyone wins. It is legal, defensible and plausibly deniable. Such people are expert at keeping secrets -- about their past and about their current work. This technique is age-old, refined and institutionalised for many a decade.
Questions remain: what to do about it, and how much to worry about it? Once it has started, this insertion tactic is rather difficult to stop and root out. At CAcert, we cared and a programme developed over time that was strong and fair -- to all interests. Part of the issue is dealing with the secrecy of it all:
Government officials and the document itself made clear that the NSA regarded the identities of its private partners as PRISM’s most sensitive secret, fearing that the companies would withdraw from the program if exposed. “98 percent of PRISM production is based on Yahoo, Google and Microsoft; we need to make sure we don’t harm these sources,” the briefing’s author wrote in his speaker’s notes.
But for the big US companies, is it likely that they care? Enough? I am not seeing it, myself, but if they are interested, there are ways to deal with this. Fairly, legally and strongly.

How much should we worry about it? That depends on (a) what is collected, (b) who sees it, and (c) who's asking the question?
There has been “continued exponential growth in tasking to Facebook and Skype,” according to the PRISM slides. With a few clicks and an affirmation that the subject is believed to be engaged in terrorism, espionage or nuclear proliferation, an analyst obtains full access to Facebook’s “extensive search and surveillance capabilities against the variety of online social networking services.”According to a separate “User’s Guide for PRISM Skype Collection,” that service can be monitored for audio when one end of the call is a conventional telephone and for any combination of “audio, video, chat, and file transfers” when Skype users connect by computer alone. Google’s offerings include Gmail, voice and video chat, Google Drive files, photo libraries, and live surveillance of search terms.
Firsthand experience with these systems, and horror at their capabilities, is what drove a career intelligence officer to provide PowerPoint slides about PRISM and supporting materials to The Washington Post in order to expose what he believes to be a gross intrusion on privacy. “They quite literally can watch your ideas form as you type,” the officer said.
Live access to everything, it seems. So who sees it?
My rule of thumb was that if the information stayed in the NSA, then that was fine. Myself, my customers and my partners are not into "terrorism, espionage or nuclear proliferation." So as long as there is a compact with the intel community to keep that information clean and tight, it's not so worrying to our business, our privacy, our people or our legal situation.
But there is no such compact. Firstly, they have already engaged the FBI and the US Department of Justice as partners in this information:
In exchange for immunity from lawsuits, companies such as Yahoo and AOL are obliged to accept a “directive” from the attorney general and the director of national intelligence to open their servers to the FBI’s Data Intercept Technology Unit, which handles liaison to U.S. companies from the NSA. In 2008, Congress gave the Justice Department authority for a secret order from the Foreign Surveillance Intelligence Court to compel a reluctant company “to comply.”
Anyone with a beef with the Feds is at risk of what would essentially be a corrupt bypass of the legal justice system of fair discovery (see this for the start of this process).
Secondly, their credibility is zero: The NSA has lied about their access. They have deceived most if not all employees of the companies they have breached. They've almost certainly breached the US constitution and the US law in gaining warrant-free access to citizens. Dismissively. From the Guardian:
"Fisa was broken because it provided privacy protections to people who were not entitled to them," the presentation claimed. "It took a Fisa court order to collect on foreigners overseas who were communicating with other foreigners overseas simply because the government was collecting off a wire in the United States. There were too many email accounts to be practical to seek Fisas for all."
The FISA court that apparently governs their access is evidently ungovernable, as even members of Congress cannot breach its secrecy.
And that's within their own country -- the NSA feels that it is under no such restrictions or niceties outside their own country.
A reasonable examination of the facts and the record of the NSA (1, 2, 3) would therefore conclude that they cannot be trusted to keep the information secret. American society should therefore be worried. Scared, even. The risk of corruption of the FBI is by itself enough to pull the plug on not just this programme, but the system that allowed it to arise.
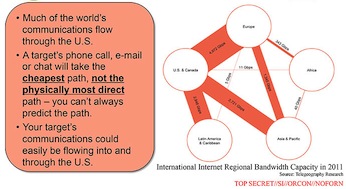
What does it mean to foreign society, companies, businesses, and people? Not a lot different as all of this was reasonable anyway. Under the history-not-rules of foreign espionage, anything goes. The only difficulty likely to be experienced is when the NSA conspires with American companies to benefit them both, or when American assets interfere with commercial businesses that they've targetted as assisting enemies.
One thing that might now get a boost is the Internet in other countries:
The presentation ... noted that the US has a "home-field advantage" due to housing much of the internet's architecture.
Take note, the rest of the world!