May 16, 2013
All Your Skype Are Belong To Us
It's confirmed -- Skype is revealing traffic to Microsoft.
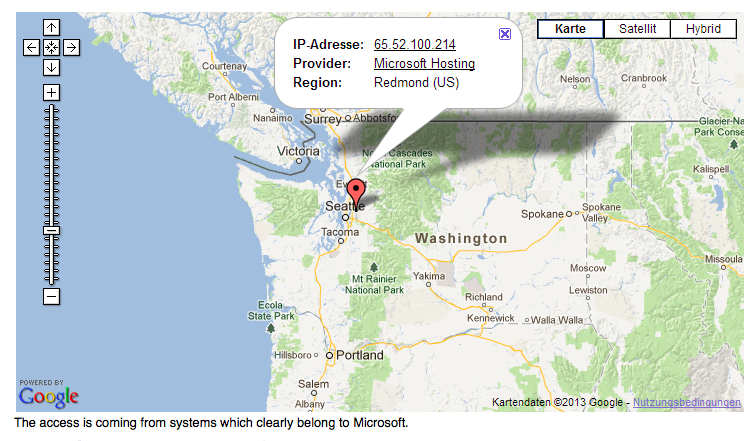
A reader informed heise Security that he had observed some unusual network traffic following a Skype instant messaging conversation. The server indicated a potential replay attack. It turned out that an IP address which traced back to Microsoft had accessed the HTTPS URLs previously transmitted over Skype. Heise Security then reproduced the events by sending two test HTTPS URLs, one containing login information and one pointing to a private cloud-based file-sharing service. A few hours after their Skype messages, they observed the following in the server log:65.52.100.214 - - [30/Apr/2013:19:28:32 +0200]
"HEAD /.../login.html?user=tbtest&password=geheim HTTP/1.1"Utrace map
Zoom The access is coming from systems which clearly belong to Microsoft.
Source: Utrace They too had received visits to each of the HTTPS URLs transmitted over Skype from an IP address registered to Microsoft in Redmond. URLs pointing to encrypted web pages frequently contain unique session data or other confidential information. HTTP URLs, by contrast, were not accessed. In visiting these pages, Microsoft made use of both the login information and the specially created URL for a private cloud-based file-sharing service.
Now, the boys & girls at Heise are switched-on, unlike their counterparts on the eastern side of the pond. Notwithstanding, Adam Back of hashcash fame has confirmed the basics: URLs he sent to me over skype were picked up and probed by Microsoft.
What's going on? Microsoft commented:
In response to an enquiry from heise Security, Skype referred them to a passage from its data protection policy:"Skype may use automated scanning within Instant Messages and SMS to (a) identify suspected spam and/or (b) identify URLs that have been previously flagged as spam, fraud, or phishing links."
A spokesman for the company confirmed that it scans messages to filter out spam and phishing websites.
Which means Microsoft can scan ALL messages to ANYONE. Which means they are likely fed into Echelon, either already, or just as soon as someone in the NSA calls in some favours. 10 minutes later they'll be realtimed to support, and from thence to datamining because they're pissed that google's beating the hell out of Microsoft on the Nasdaq.
Game over?
Or exaggeration? It's just fine and dandy as all the NSA are interested in is matching the URLs to jihadist websites. I don't care so much for the towelheads. But, from the manual of citizen control comes this warning:
First they came for the jihadists,
and I didn't speak out because I wasn't a jihadist.Then they came for the cypherpunks,
and I didn't speak out because I wasn't a cypherpunk.Then they came for the bloggers,
and I didn't speak out because I wasn't a blogger.Then they came for me,
and there was no one left to speak for me.
Skype, game over.
May 06, 2013
What makes financial cryptography the absolutely most fun field to be in?
Quotes that struck me as on-point: Chris Skinner says of SEPA or the Single-European-Payment-Area:
One of the key issues is that when SEPA was envisaged and designed, counterparty credit risk was not top of the agenda; post-Lehman Brothers crash and it is.
What a delight! Oh, to design a payment system without counterparty risk ... Next thing they'll be suggesting payments without theft!
Meanwhile Dan Kaminsky says in delicious counterpoint, commenting on Bitcoin:
But the core technology actually works, and has continued to work, to a degree not everyone predicted. Time to enjoy being wrong. What the heck is going on here?First of all, yes. Money changes things.
A lot of the slop that permeates most software is much less likely to be present when the developer is aware that, yes, a single misplaced character really could End The World. The reality of most software development is that the consequences of failure are simply nonexistent. Software tends not to kill people and so we accept incredibly fast innovation loops because the consequences are tolerable and the results are astonishing.
BitCoin was simply developed under a different reality.
The stakes weren’t obscured, and the problem wasn’t someone else’s.
They didn’t ignore the engineering reality, they absorbed it and innovated ridiculously
Welcome to financial cryptography -- that domain where things matter. It is this specialness, that ones code actually matters, that makes it worth while.
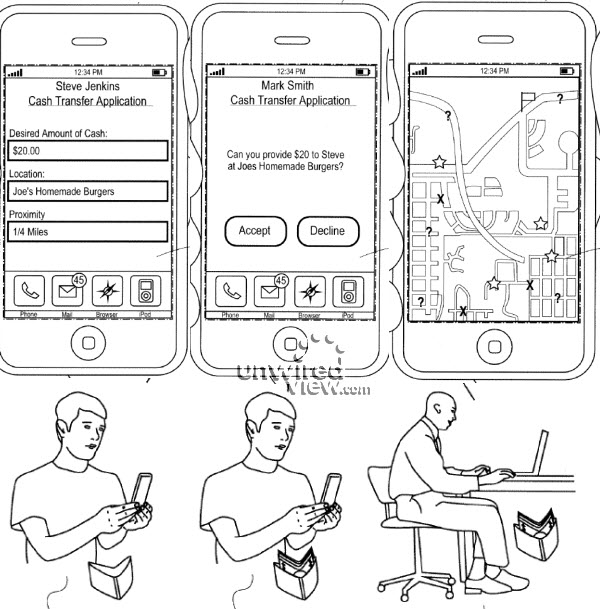
Meanwhile, from the department of lolz, comes Apple with a new patent -- filed at least.
The basic idea, described in a patent application “Ad-hoc cash dispensing network” is pretty simple. Create a cash dispensing server at Apple’s datacenter, to which iPhones, iPads and Macs can connect via a specialized app. Need some quick cash right now and there’s no ATM around? Launch the Cash app, and tell it how much do you need. The app picks up your location, and sends the request for cash to nearby iPhone users. When someone agrees to front you $20, his location is shown to you on the map. You go to that person, pick up the bill and confirm the transaction on your iPhone. $20 plus a small service fee is deducted from your iTunes account and deposited to the guy who gave you the cash.
The good thing about being an FCer is that you can design that one over beers, and have a good belly laugh for the same price. I don't know how to put it gently, but hey guys, don't do that for real, ok?!
All by way of saying, financial cryptography is where it's at!