February 27, 2006
Identity on the move II - Microsoft's "Identity Metasystem" TM, R, Passport-redux
A commercial presentation on Microsoft's Infocard system is doing the rounds. (Kim Cameron's blog.) Here's some highlights and critiques. It is dressed up somewhat as an academic paper, and includes more of a roadmap and analysis view, so it is worth a look.
The presentation identifies The Mission as "a Ubiquitous Digital Identity Solution for the Internet."
By definition, for a digital identity solution to be successful, it needs to be understood in all the contexts where you might want to use it to identify yourself. Identity systems are about identifying yourself (and your things) in environments that are not yours. For this to be possible, both your systems and the systems that are not yours – those where you need to digitally identity yourself – must be able to speak the same digital identity protocols, even if they are running different software on different platforms.In the case of an identity solution for the entire Internet, this is a tall order...
Well, at least we can see a very strong thrust here, and as a mission-oriented person, I appreciate getting that out there in front. Agreeing with the mission is however an issue to discuss.
Many of the problems facing the Internet today stem from the lack of a widely deployed, easily understood, secure identity solution.
No, I don't think so. Many of the problems facing the Internet today stem from the desire to see systems from an identity perspective. This fails in part because there is no identity solution (and won't be), in part because an identity solution is inefficient, and in part because the people deploying these systems aren't capable of thinking of the problem without leaning on the crutch of identity. See Stefan Brands' perspective for thinking outside the tiny cramped box of identity.
A comparison between the brick-and-mortar world and the online world is illustrative: In the brick-and-mortar world you can tell when you are at a branch of your bank. It would be very difficult to set up a fake bank branch and convince people to do transactions there. But in today’s online world it’s trivial to set up a fake banking site (or e-commerce site …) and convince a significant portion of the population that it’s the real thing. This is an identity problem. Web sites currently don’t have reliable ways of identifying themselves to people, enabling imposters to flourish. One goal of InfoCard is reliable site-to-user authentication, which aims to make it as difficult to produce counterfeit services on the online world as it is to produce them in the physical world.
(My emphasis.) Which illustrates their point nicely - as well as mine. There is nothing inherent in access to a banking site that necessitates using identity, but it will always be an identity based paridigm simply because that's how that world thinks. In bricks-and-mortar contrast, we all often do stuff at branches that does not involve identity. In digital contrast, a digital cash system delivers strength without identity, and people have successfully mounted those over web sites as well.
That aside, what is this InfoCard? Well, that's not spelt out in so many words as yet:
In the client user interface, each of the user’s digital identities used within the metasystem is represented by a visual “Information Card” (a.k.a. “InfoCard”, the source of this technology’s codename). The user selects identities represented by InfoCards to authenticate to participating services. The cards themselves represent references to identity providers that are contacted to produce the needed claim data for an identity when requested, rather than claims data stored on the local machine. Only the claim values actually requested by the relying party are released, rather than all claims that the identity possesses (see Law 2).
References to providers is beginning to sound like keys managed in a wallet, and this is suggested later on. But before we get to that, the presentation looks at the reverse scenario: the server provides the certificate:
To prevent users from being fooled by counterfeit sites, there must be a reliable mechanism enabling them to distinguish between genuine sites and imposters. Our solution utilizes a new class of higher-value X.509 site certificates being developed jointly with VeriSign and other leading certificate authorities. These higher-value certificates differ from existing SSL certificates in several respects.
Aha. Pay attention, here comes the useful part...
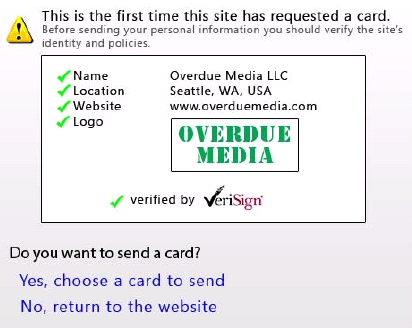
First, these certificates contain a digitally-signed bitmap of the company logo. This bitmap is displayed when the user is asked whether or not they want to enter into a relationship with the site, the first time that the site requests an InfoCard from the user.Second, these certificates represent higher legal and fiduciary guarantees than standard certificates. In many cases, all that having a standard site certificate guarantees is that someone was once able to respond to e-mail sent to that site. In contrast, a higher-value certificate is the certificate authority saying, in effect, “We stake our reputation on the fact that this is a reputable merchant and they are who they claim to be”.
Users can visit sites displaying these certificates with confidence and will be clearly warned when a site does not present a certificate of this caliber. Only after a site successfully authenticates itself to a user is the user asked to authenticate himself or herself to the site.
Bingo. This is just the High Authentication proposal written about elsewhere. What's salient here is that second paragraph, my emphasis added. So, do they close the loop? Elsewhere there has been much criticism of the proposals made by Amir and myself, but it is now totally clear that Microsoft have adopted this.
The important parts of the branding proposal are there:
- The site is identified

- the statement is made by the verifier of the site:

- the verifier is named, and
- the verifier's logo is present.

The loop is closed. Now, finally, we have a statement with cojones.
There remain some snafus to sort out. This is not actually the browser that does this, it is the InfoCard system which may or may not be available and may or may not survive as this year's Microsoft Press Release. Further, it only extends to the so-called High Assurance certs:
To help the user make good decisions, what’s shown on the screen varies depending on what kind of certificate is provided by the identity provider or relying party. If a higher-assurance certificate is provided, the screen can indicate that the organization’s name, location, website, and logo have been verified, as shown in Figure 1. This indicates to a user that this organization deserves more trust. If only an SSL certificate is provided, the screen would indicate that a lower level of trust is warranted. And if an even weaker certificate or no certificate at all is provided, the screen would indicate that there’s no evidence whatsoever that this site actually is who it claims to be. The goal is to help users make good decisions about which identity providers they’ll let provide them with digital identities and which relying parties are allowed to receive those digital identities.
The authors don't say it but they intend to reward merchants who pay more money for the "high-assurance". That's in essence a commercial response to the high cost of the DD that Geotrust/RSA/Identrus are trying to float. This also means that they won't show the CA as the maker of a "lower assurance" statement, which means the vast bulk of the merchants and users out there will still be phishable, and Microsoft will be liable instead of the statement provider. But that's life in the risk shifting business.
(As an explanatory note, much of the discussion recently has focussed on the merchant's logo. That's less relevant to the question of risk. What is more relevant is VeriSign's name and logo. They are the one that made the statement, and took money for it. Verisign's brand is something that the user can recognise and then realise the solidity of that statement: Microsoft says that Verisign says that the merchant is who they are. That's solid, because Microsoft can derive the Verisign logo and name from the certificate path in a cryptographically strong fashion. And they could do the same with any CA that they add into their root list.)
Finally, the authors have not credited prior work. Why they have omitted this is obscure to me - this would be normal with a commercial presentation, but in this case the paper looks, writes and smells like an academic paper. That's disappointing, and further convinces people to simply not trust Microsoft to implement this as written; if Microsoft does not follow centuries-old academic customs and conventions then why would we trust them in any other sense?
That was the server side. Now we come to the user-centric part of the InfoCard system:
2.7. Authenticating Users to Sites InfoCards have several key advantages over username/password credentials:
- Because no password is typed or sent, by definition, your password can not be stolen or forgotten.
- Because authentication is based on unique keys generated for every InfoCard/site pair (unless using a card explicitly designed to enable cross-site collaboration), the keys known by one site are useless for authentication at another, even for the same InfoCard.
- Because InfoCards will resupply claim values (for example, name, address, and e-mail address) to relying parties that the user had previously furnished them to, relying parties do not need to store this data between sessions. Retaining less data means that sites have fewer vulnerabilities. (See Law 2.)
What does that mean? Although it wasn't mentioned there, it turns out that there are two possibilities: Client side key generation and relationship tracking, as well as "provider generated InfoCards" written up elsewhere:
Under the company's plan, computer users would create some cards for themselves, entering information for logging into Web sites. Other cards would be distributed by identity providers -- such as banks or governmental agencies or online services -- for secure online authentication of a person's identity.To log in to a site, computer users would open the InfoCard program directly, or using Microsoft's Internet Explorer browser, and then click on the card that matches the level of information required by the site. The InfoCard program would then retrieve the necessary credentials from the identity provider, in the form of a secure digital token. The InfoCard program would then transmit the digital token to the site to authenticate the person's identity.
Obviously the remote provision of InfoCards will depend on buy-in, which is a difficult pill to follow as that means trusting Microsoft in oh so many ways - something they haven't really got to grips with. But then there are also client-generated tokens. Are they useful?
If they have client-side key generation and relationship caching, then these are two of the missing links in building a sustainable secure system. See my emphasis further above for a hint on relationship tracking and see Kim Cameron's blog for this comment: "Cameron: A self-issued one you create yourself." Nyms (as per SSH and SOX) and relationship tracking (again SSH, and these days Trustbar,Petname and recent other suggestions) are strong. These ideas have been around for a decade or more, we call it opportunistic cryptography as a school.
Alternatively, notice how the credentials term is slipped in there. That's not how Stefan Brands envisages it (from Identity on the move I - Stefan Brands on user-centric identity management), but they are using his term. What that means is unclear (and see Identity on the move III - some ramblings on "we'll get it right this time, honest injun!" for more).
Finally, one last snippet:
3.6. Claims != “Trust” A design decision was to factor out trust decisions and not bundle them into the identity metasystem protocols and payloads. Unlike the X.509 PKIX [IETF 05], for example, the metasystem design verifies the cryptography but leaves trust analysis for a higher layer that runs on top of the identity metasystem.
Hallelujah! Trust is something users do. Crypto systems do claims about relationships.
Identity on the move I - Stefan Brands on user-centric identity management
Stefan Brands has moved over to the podcasting world, with an interview on user-centric identity management. Here's my notes from listening (my comments injected in parenthesies, my errors everywhere):
Stefan relates cash payments as ways to transfer information, Hayekian style, for user-centric transactions. This time, instead of doing an application like digital cash, he is concentrating on an engine to wrap the data for user-controlled privacy.
Consider the large-scale distributed system of medical data management. Specialists across domain boundaries have only their own information on you. How do we allow the doctor to get access to the information in other domains? (Here's a canonical example were we assume a priori that such access is a good thing.)
Classically, would we put it all in a central database and shove some access control on it? This we don't do, because the access control doesn't work well enough - hackers and insiders get widespread access. This was the Passport approach.
The second approach is the federated identity management approach of Liberty Alliance. Here, we hook up all the silos of data together through a centralised party - could be a hospital. The doctor contacts the centralised party and asks for access to the info on the patient. What it gets is the access keys, and can then get the data it needs from the various sources.
The ability to move the data has to be facilitated by a central party - which means the party now knows what you are up to. (Insurance of course wants to know who is visiting which doctor...) It's similar to the credit card model with users, merchants and VISA in the middle. The centre might not know what you are "purchasing" but it does see the amount and the merchant. Does this give the user payment privacy? No, not like cash.
My Doctor typically knows me, and a merchant might as well - but should there be a central party that also knows me? The central party would also know all the clients of a doctor - breaching the patient-doctor autonomy, something that doctors in Quebec rejected when the provice tried to roll out a PKI.
There are economy, privacy and security rights, and they are all interlinked. You think you are disclosing just the pertinent information for the local decision, but this can easily jump to a wider scope. When competitive intelligence comes into play, lots of parties want to know all of these details. Governments are included on both sides, where for example different provinces or states are paranoid about handing their data over to centralised federal parties as this will result in loss of autonomy in dealing with own citizens.
A centralised approach also cannot cope with dynamic queries, it has no flexibility.
The engine of Credentica is the third approach. Model 3 is a crediential system in its purest form, and is closer to how people and society functioned before the computer age. When the relying party wants richer information, the user is asked for the information. The relying party - the doctor - just wants to get the data, and it wants it from a source that it trusts. What it does not care about is how it gets there.
We can put together a device - already available - that holds credentials. Instead of saying, here is my identity, and expecting a centralised party or silo to deal with it, the user provides the credentials and gets the data herself. The user carries a token - in effect a key of some form - that allows the patient and doctor together to get the data.
The default scenario is a user with a smart card or PDA holding her credentials. It can hold the data itself - as a copy of the data held at a service provider. This data can also be accessed directly from the service provider by the user.
A relying party such as principle doctor relies directly on the user. But now the question is, can the user be trusted with the integrity of the information, such as with prescriptions. In this case, the relying party has to go to the source of that prescription, and the user now becomes the person in the middle.
Simple digital signatures aren't good enough, as this information is private and substitutable. How do we stop the user substituting in a prescription? The same applies to credit and employment questions. How does the asker know the information really applies to Alice the users?
Which brings us to the crypto engine Credentica has developed. It allows the source to take data, make assertations, and package that data for the user's token. Some sort of smart card or USB token is needed, but that is implementation details.
Depending on the threat model, the protection is variable (???). Account information for example could be wrapped by the security engine. The relying party could contact the source to verify the information.
Now, what we want to do is give the user the same capability to answer the same questions that the source knows authoritively. Yet, relying party does not trust the user as much as the source. On this "cryptographically certified data" the engine can answer questions like "are you over 18?" We can do this by revealing the birthdate, as certified by some provider, but this reveals more information than needed.
The engine allows that question to be asked and answered - are you over 18? The statement returned is self-certifying, it can reveal its own identity.
Correlation is still an issue over handles. Imagine a question of male versus female. Normally, Alice reveals she is female, but she is also generally revealing data that is matchable to other events. If every piece of data is doled out with these identifiers, this has terrible privacy implications. (At this point the interview was running out of time, so we did not hear how the engine deals with correlation and identifier matching.)
What are the business opportunities? Health data is a big area, and European and Canadian agencies are pushing more and more towards rejecting the panopticon approach. Credentica would likely partner with others in such a complicated supply chain; the engine is literally a component in the vehicle.
February 25, 2006
new cert for FC
Installing new SSL server certs is like visiting the in-laws for Christmas dinner. It's so painful, you dread it for weeks in advance. Afterwards, the relief flows through you as you know you don't have to do that for another year or two.
The eagle-eyed will notice a new certificate for Financial Cryptography, as of a week back. There have been a number of improvements: it now includes all the AltSubjectNames according to the VHostsTaskForce recommendation. It's also installed with the new Class 3 root, which is the CAcert "high-verification" root (meaning that the identity of the issuer -- me -- was checked at least to 50 points worth).
(You will need to reset your Trustbar. You should need to reset your Petname. Weird - for me, Petname is stuck on the old name transferred to the new cert???)
Getting the right setup only took 3 goes. One effort failed completely. Second time, the script I used did not include the CommonName as well in the AltServerName list. Apache barfed on that version, giving an uninterpretable error. Re-rolled with the right list, this time it worked.
There are still issues. Hopefully by the time this one expires, 2 years from now, these other problems will be solved as well:
- Apache and browsers will hopefully implement ServerNameIndication (SNI) which is the standard for sharing one SSL server over many web sites as Virtual Hosts. Like much of the planet, I have one IP# for too many web sites to administrate. Sharing virtual hosts is needed not to please me, but because it feeds into the fight against phishing. I already got hit with a request to add another domain name - which means a whole other cert, dammit.
- We'll be a bit closer to point, click, configure. CAcert's process for setting this all up is still slow and cumbersome, but at least the doco is mostly there within 10 minutes or so of it being needed. The entire process took most of my last saturday, and I won't be satisfied until the time takes less than a minute, like Skype or SSH. Crypto is meant to help protect us, not slow us down and burn up our weekends.
- Although CAs make a statement to some effect, users still don't know it. Firefox tells me the site name on the bottom, but not who said that unless I mouse-over. Safari doesn't even do that, it is still on the old model of a tiny padlock hidden somewhere. Konqueror proudly announces how many bits of crypto blah blah protection I've got. So basically users trust their browser or they are SOL.
Readers sometimes ask why FC uses CAcert instead of forking out bux to the commercial companies. It's not a political statement, I'd frankly rather we could just use crypto without the hassle (names of well designed cryptosystems available on request). Here's some of my reasons for using CAcert:
- I have a bunch of sites. They all benefit from a bit of SSL, but even at the low prices of certificate manufacturing shops, that all adds up. Also, one needs to factor in errors, reworks, extra domains added in, etc. With CAcert, it is only my time going down the drain every time something doesn't work out, not my wallet.
- CAcert have an identity program that makes sense, at least in principle (an audit process has started recently). They use what they call a web of trust and have each issuer of class 3 (identified) certs checked out by two or more people, face to face. It's not that I care to be checked out like that - in fact I despise and loathe the idea that to use crypto you have to know me - but if we are going to make a statement about identity, let's at least make a statement that means something. As a Financial Cryptographer, it behoves to take part in a process that is coherent, to the extent possible; in the past, I've used credit cards, but because I know that is a meaningless identity check, I feel stupid doing it. (FTR, I myself have 55 points which means the certificate points to an identity that was verified by at least 2 independent assurers, each of whom have at least 100 points, and are therefore verified by 4 people each, as a minimum.)
- CAcert is building a membership structure that harkens back to the good old days of the net. Members work for each other. The doco is patchy and the accents are odd, but the lists are not antagonistic to the honest user who lacks a PhD in mathematics. Security for the common man. And you get free certs. As there's no interest in how many certs are sold, concentration on core security is more likely. In fact, over on the CAcert lists, it's possible to propose some interesting security ideas and get some thoughtful response. Very refreshing.
- Readers will recall the age-old scandal of phishing. One core weapon in the fight against phishing is to get as much traffic onto SSL as possible, and then tools like Trustbar, Petname and maybe Ping's new design can better protect users. It's a virtuous cycle - more SSL means more certs means more tools and more protection. For ordinary users. So it pays for us financial cryptographers to keep the pressure on for more SSL. CAcert is definately there to help that process. Who else is? Whatever your views on whether High Authentication will work, it is hardly designed to increase the amount off SSL in use.
Of course, not all is light, joy and bounty. Far from it, CAcert is only the least worst of a bad bunch, but if we want to address phishing something must be done. A couple of notable flaws in the CAcert process: Their docs are all scattered around and their processes have not been beaten up. The linkage from the relying party to the cert to the signer to the statement to the CPS is unclear (but that's common of all).
( Note to FC readers: CAcert's root is currently only being distributed into various Linux distros and now FreeBSD! For other platforms, you will need to travel to CAcert's root page to install the root into their browser by hand -- for Firefox users, click on the line that says Class 3 PKI Key Root Certificate (PEM Format) if want to be part of the CAcert community. For Safari, Konqueror, Opera, IE7 users ... I don't know. I tried to load the root into Safari but failed. )
February 19, 2006
Branded Experiments
Adam writes that he walks into a hotel and gets hit with a security brand.

For quite some time, Ian Grigg has been calling for security branding for certificate authorities. When making a reservation for a Joie de Vivre hotel, I got the attached Javascript pop-up. (You reach it before the providing a credit card number.)I am FORCED to ask, HOWEVER , what the average consumer is supposed to make of this? ("I can make a hat, and a boat...") Who is this VERISIGN, and why might I care?
Well, precisely! They are no-one, says the average consumer, so anything they have done to date, including the above, is irrelevant.
More prophetically, one has to think of how brand works when it works - every brand has to go through a tough period where it braves the skeptics. Some of the old-timers might recall rolling around the floor laughing at those silly logos that Intel were putting in other supplier's adverts! And stickers on laptops - hilarious !
These guys will have to do that, too, if things are to this way pass. It will involve lots of people saying "so what?" until one day, those very same skeptics will say "Verisign... now I know."
The word Verisign isn't a link. It's not strongly tied to what I'm seeing. (Except for the small matter of legality, I could make this site pop up that exact same dialog box.) It is eminently forgeable, there's no URL, there's nothing graphical.
Right, so literally the only thing going on here is a bit of branding. The brand itself is not being used as part of a security statement in any sense worthy of attention. To recap, the statement we are looking for is something like "Comodo says that the certificate belongs to XYZ.com." That's a specific, verifiable and reliable statement. What you're seeing on the ihotelier page is a bit of fluff.
Nevertheless, it probably pre-sages such dialog boxes popping up next to the colored URL bar, and confusing the message they're trying to send.
I guess it presages a lot of bad experimentation, sure. What should he happening in the coloured URL bar is simply that "CAcert claims that Secure.com is who you are connected to." It's very simple. a. the remote party, b. the CA, and c. the statement that the CA says the remote party is who it is. Oh, and I almost forgot: d. on the chrome so no forgeries, thanks, Mr Browser.
Why does all this matter? To close the loop. Right now, Firefox says you are connected to Paypal.com. And IE6 says you are connected to BoA. If you get phished, it's the browser that got it wrong, not the CA. As the CA is the one that collected the money for securing the connection we need to reinsert the CA into the statement.
So when the user sues, she does so on the proper design of the PKI, not some mushed up historical accident.
More dots than you or I can understand (Internet Threat Level is Systemic)
fm points to Gadi Evron who writes an impassioned plea for openness in security. Why? He makes a case that we don't know the half of what the bad guys are up to. His message goes something like this:
DDoS -> recursive DNS -> Fast Flux -> C2 Servers -> rendevous in cryptographic domainname space -> bots -> Phishing
Connecting the dots is a current fad in america, and I really enjoyed those above. I just wish I knew what even half of them meant. Evron's message is that there are plenty of dots for us all to connect, so many that the tedium of imminent solution is not an issue. He attempted to describe them a bit later with his commentary on the recent SSL phishing news:
Some new disturbing phishing trends from the past year:POST information in the mail message
That means that the user fills his or her data in the HTML email message itself, which then sends the information to a legit-looking site. The problem with that, is how do you convince an ISP that a real (compromised) site is indeed a phishing site, if there is no phishy-looking page there, but rather a script hiding somewhere?Trojan horses
This is an increasing problem. People get infected with these bots, zombies or whatever else you’d like to call them and then start sending out the phishing spam, while alternating the IP address of the phishing server, which brings us to…Fast-Flux
Fast Flux is a term coined in the anti spam world to describe such Trojan horses’ activity. The DNS RR leading to the phishing server keeps changing, with a new IP address (or 10) every 10 minutes to a day. Trying to keep up and eliminate these sites before they move again is frustrating and problematic, making the bottle-neck the DNS RR which needs to be nuked.
We may be able to follow that, but the bigger question is how to cope with it. Even if you can follow the description, dealing with all three of the above is going to stretch any skilled practitioner. And that's Evron's point:
What am I trying to say here?All these activities are related, and therefore better coordination needs to be done much like we do on the DA and MWP groups, cross-industry and open-minded. R&D to back up operations is critical, as what’s good for today may be harmful tomorrow (killing C&C’s as an example).
The industry needs to get off its high tree and see the light. There are good people who never heard about BGP but eat Trojans (sounds bad) for breakfast, and others need to see that just because some don’t know how to read binary code doesn’t mean they are not amazingly skilled and clued with how the network runs.
This is not my research alone. I can only take credit for seeing the macro image and helping to connect the dots, as well as facilitate cooperation across our industry. Still, as much as many of this needs to remain quiet and done in secret-hand-shake clubs, a lot of this needs to get public and get public attention.
Over-compartmentalizing and over-secrecy hurts us too, not just the US military. If we deal in secret only with what needs to be dealt in secret, people may actually keep that secret better, and more resources can be applied to deal with it.
Some things are handled better when they are public, as obviously the bad guys already know about them and share them quite regularly. “Like candy” when it comes to malware samples, as an example.
The Internet threat level is now systemic, and has been since the arisal of industrialised phishing, IMO. I've written many times before about the secrecy of the browser sector in dealing with phishing, and how the professional cryptographic community washed its hands of the problem. Microsoft's legendary castles of policy need no reminder, and it's not as if Apple, Sun, Symantec, Verisign or any other security company would ever do any better in measures of openness.
Now someone over the other side of the phishing war is saying that he sees yet other tribes hiding in their fiefdoms, and I don't even know which tribes he's referring to. Gadi Evron concludes:
-opinion-Our fault, us, the people who run these communities and global efforts, for being over-secretive on issues that should be public and thus also neglecting the issues that should really remain under some sort of secrecy, plus preventing you from defending yourself.Us, for being snobbish dolts and us, for thinking we invented the wheel, not to mention that we know everything or some of us who try to keep their spots of power and/or status by keeping new blood out (AV industry especially, the net-ops community is not alone in the sin of hubris).
It’s time to wake up. The Internet is not about to die tomorrow and there is a lot of good effort from a lot of good people going around. Amazing even, but it is time to wake up and move, as we are losing the battle and the eventual war.
Cyber-crime is real crime, only using the net. Cyber-terrorism will be here one day. If we can’t handle what we have on our plate today or worse, think we are OK, how will we handle it when it is here?
February 14, 2006
Birch on Blogs, decimal points matter with houses, too, and Bill Gates predicted...
News snippets for today: Dave Birch steps into the blogging world with Digital Money. Welcome! Dave is one of the grandfathers of FC, having led Consult Hyperion, spiritually at least, through a thousand and one conferences, work outs, contracts and so forth, all in their narrow field of technomoney and other things valuable.
Several people sent me references to this house that was erroneously valued at $400million. Now, such a blunder is just a typing mistake .. until the value gets fed into the budget, and the money gets spent before it is collected:
Most local officials did not learn about the mistake until Tuesday, when 18 government taxing units were asked to return a total of $3.1 million of tax money. The city of Valparaiso and the Valparaiso Community School Corp. were asked to return $2.7 million. As a result, the school system has a $200,000 budget shortfall, and the city loses $900,000.
Many people will look for many excuses in many strange corners ... but the answer is clear - don't spend money that doesn't exist. Corollary - use a real hard money system, not one based on promises. It won't happen again, I promise.
Dave points at bit-tech that checks the predictions of Bill Gates. Here's one:
What do you carry on your person now? Probably at least keys, identification, money, and a watch. Quite possibly you also carry credit cards, a checkbook, traveller’s checks, an address book, an appointment book, a notepad, reading material, a camera, a pocket tape recorder, a cellular phone, a pager, concert tickets, a map, a compass, a calculator, an electronic entry card, photographs, and perhaps a loud whistle to summon help.You’ll be able to keep all these and more in another information appliance we call the Wallet PC. It will be about the same size as a wallet, which means you’ll be able to carry it in your pocket or purse. It will display messages and schedules and also let you read or send electronics mail and faxes, monitor weather and stock reports, and play both simple and sophisticated games. At a meeting you might take notes, check your appointments, browse information if you’re bored, or choose from amongst thousands of easy-to-call-up photos of your kids.
Rather than holding paper currency, the new wallet will store unforgeable digital money...
Whether it happened like that or not, we'll leave others to judge. Or you can what Dave wrote.
Todd Boyle: value of transactions versus security model
Todd Critiques! iang wrote:
> Financial Cryptography Update: Brand matters (IE7, Skype, Vonage, Mozilla)
> [........]
> No, brand is a shorthand, a simple visual symbol that points to the
> entire underlying security model. Conventional bricks&mortar
> establishments use a combination of physical and legal methods
> (holograms and police) to protect that symbol, but what Trustbar has
> shown is that it is possible to use cryptography to protect and display
> the symbol with strength, and thus for users to rely on a simple visual
> icon to know where they are.
>
> Hopefully, in a couple of years from now, we'll see more advanced, more
> thoughtful, more subtle comments like "the secured CA brand display
> forms an integral part of the security chain. Walking along this
> secured path - from customer to brand to CA to site - users can be
> assured that no false certs have tricked the browser."
The statement above seems incorrect to me, and inconsistent with statements you have made for many years.
Any security that works on ordinary general purpose computers is going to work as long as one of the following: no high value transactions at stake, no large numbers of users, and.or not in the marketplace very long.
In other words, any mac or windows or linux thing that gets into common use by very many people, that actually has any money at stake, will be cracked before very long. There is some type of a destruction curve that starts out slow, then reaches a steep slope or catastrophic collapse, again depending on how much money is at stake, aggregated over the number of users.
I'm afraid this will be true until there are two elements introduced: more people, real people in the community, involved in the day-to-day operation of our identity and reputation mechanisms, and, a signing device that is guaranteed to perform its function for the long term and I don't mean 99.999% but 100%. However humble its function, to be adopted at all, it must be 100% even if that's artificially nailed down by some sort of intermediary, some sort of insurance as we see with credit cards. Why is this taking so long to appear?!
In closing, we had Bruce Schneier in Seattle last weekend,
Todd
Sunday, February 12, 2006 - Page updated at 12:00 AM
500 show up to hear security guru
By Tan Vinh
Seattle Times staff reporter
Bruce Schneier once worked for the Defense Department.
Since the disclosure last month that the government authorizes warrantless domestic spying, the water-cooler chats and classroom debates have raged over privacy and constitutional rights.
But Bruce Schneier, the security guru who has rock-star status among crypto-philes, offered another take on the matter to a crowd of more than 500 people at the American Civil Liberties Union convention at the University of Washington on Saturday: This computer-eavesdropping stuff doesn't really work.
"When you have computers in charge telling people what to do, you have bad security," said Schneier, who worked for the U.S. Department of Defense in the 1980s.
Schneier, who won't reveal what he did for the Defense Department other than to say it's related to communications and security, said the domestic-eavesdropping program relies on computers to pick up words such as "bomb," "kill" or "president" in conversations and flag the participating parties as potential suspects.
Last month, the Bush administration acknowledged authorizing the National Security Agency to intercept e-mails and phone calls without warrants in cases where one party is outside the United States.
"Technology is static," Schneier said. "It doesn't adapt. But people can adapt to whatever is going on," he said. "You are better off" hiring more FBI agents to gather intelligence.
The security is not worth the cost because the computers generate too many false alarms, Schneier said.
"Replacing people with technology hardly ever works."
With his thinning hair in a ponytail, Schneier looked more like a hippie than a cryptography expert whose books have gained cult status and whose appearances draw standing-room-only crowds.
Here to speak about the nation's concern with security since the Sept. 11, 2001, attacks, the 43-year old Minneapolis resident suggested everyone step back and realize "terrorist attacks are rare. They hardly ever happen."
A funny thing happens when people get scared, he said. People give up their freedom or liberties to authority. And politicians create "movie plots" of attacks at maybe the Super Bowl or the New York subways, as if terrorists couldn't attack another event or the subway stations in Boston, he said.
"Security that requires us to guess right" is not worth the cost because there are too many potential targets, he said.
Tan Vinh: 206-515-5656 or tvinh@seattletimes.com
February 08, 2006
Brand matters (IE7, Skype, Vonage, Mozilla)
In branding news: IE7 is out in Beta 2 and I'm impatiently waiting for the first road tests. (Roight... as if I have a Microsoft platform around here...) Readers will recall that Microsoft took the first steps along the branded security path by putting the CA name up on the chrome. This places them in the lead in matters of risk.

Sadly, they also got a bit confused by the whole high-end super-certs furfie. IE7 only rewards the user with the CA brand if the site used these special high-priced certs.
Plonk! That kind of ruins it for security - the point of the branding is that the consumer wants to see the Bad Brand or Unknown Brand or the Missing Brand or the Bland Brand ... up there as well. Why? So as to close off the all-CAs-are-equal bug in secure browsing. (Preferably before the phishers start up on it, but just after the first sightings will do nicely, thanks, if you subscribe to post-GP theories.)
By choosing to promote a two-tiered risk statement, Microsoft then remains vulnerable to a takeover in security leadership. That's just life in the security world; leadersip is a bit of a lottery when you allow your security to become captive to marketing departments' zest for yet another loyalty program. Also, annoyingly, IE7 promises to mark any slightly non-formal certificated site (such as FC) as a Red Danger Danger site. Early indications are that this will result in an attack on brand that hasn't hitherto been seen, and has interesting strategic implications for you-know-who.

The CA branding idea is not new nor original. It was even (claimed to be) in the original Netscape design for secure browsing, as was the coloured security bar. Using brand is no more than an observation deriving from several centuries of banking history - a sector that knows more about risk matters than the Internet, if only because they lose money every time they get it wrong.
Consider some more in the flood of evidence that brand matters - over in VoIPland look at how things have changed:
In Europe, branded VoIP represented 51.2 percent of all VoIP calls in the last quarter of 2005, while Skype accounted for 45 percent of VoIP minutes. Vonage took less than one percent of the market while other third-party VoIP providers represented 3.5 percent of all VoIP traffic, the report said."Twelve months ago, Skype represented 90 percent of all VoIP minutes. Now people are buying branded services," Chris Colman, Sandvine's managing director for Europe, said Tuesday.
Whaaa.... 90% to 45% of the market in 12 months! No wonder Skype sold out!
The same trend was found in the North American market. The study found that U.S. branded VoIP represented 53 percent of VoIP minutes on broadband networks. Vonage, with a 21.7 percent share, and Skype, with 14.4 percent, were the leading third-party providers.
I'll bet Vonage are kicking themselves... Stop Press!
TECHNOLOGY ALERT from The Wall Street Journal. Feb. 8, 2006
Internet-phone company Vonage Holdings has filed to raise up to $250 million in an initial public offering. The company also named Mike Snyder, formerly president of security company ADT, as its new CEO. Founder Jeffrey Citron, who had served as CEO, remains chairman.
FOR MORE INFORMATION, see:
http://wsj.com/technology?mod=djemlart
I didn't know you could file an IPO in just minutes like that!
Meanwhile, one group that have traditionally resisted the risk nexus of brands ... just got hit over the head with their own brand! Mozilla earnt a spot in the 10 ten most influential brands last year. More influential that Sony! Heady praise indeed. Well done, guys. You have now been switched on to the miracle of brand, which means you have to defend it! Even as this was happening, Firefox lost market share in the US. Predicted of course, as IE7 rolls out, Microsoft users start to switch back. Nice. Competition works (in security too).
So, what's the nexus between brand and risk? Newbies to the brand game will blather on with statements like "we protect our brand by caring about the security of our users." Can you imagine a journo typing that up and keeping a straight face?
No, brand is a shorthand, a simple visual symbol that points to the entire underlying security model. Conventional bricks&mortar establishments use a combination of physical and legal methods (holograms and police) to protect that symbol, but what Trustbar has shown is that it is possible to use cryptography to protect and display the symbol with strength, and thus for users to rely on a simple visual icon to know where they are.
Hopefully, in a couple of years from now, we'll see more advanced, more thoughtful, more subtle comments like "the secured CA brand display forms an integral part of the security chain. Walking along this secured path - from customer to brand to CA to site - users can be assured that no false certs have tricked the browser."
February 07, 2006
The Market Price of a Vulnerability
More on threats. A paper Paul sent to me mentions that:
Stuart Schechter’s thesis [11] on vulnerability markets actually discusses bug challenges in great detail and he coined the term market price of vulnerability (MPV) as a metric for security strength.
A good observation - if we can price the value of a vulnerability then we can use that as a proxy for the strength of security. What luck then that this week, we found out that the price of the Windows Metafile (WMF) bug was ... $4000!.
The Windows Metafile (WMF) bug that caused users -- and Microsoft -- so much grief in December and January spread like it did because Russian hackers sold an exploit to anyone who had the cash, a security researcher said Friday.The bug in Windows' rendering of WMF images was serious enough that Microsoft issued an out-of-cycle patch for the problem in early January, in part because scores of different exploits lurked on thousands of Web sites, including many compromised legitimate sites. At one point, Microsoft was even accused of purposefully creating the vulnerability as a "back door" into Windows.
Alexander Gostev, a senior virus analyst for Moscow-based Kaspersky Labs, recently published research that claimed the WMF exploits could be traced back to an unnamed person who, around Dec. 1, 2005, found the vulnerability.
"It took a few days for exploit-enabling code to be developed," wrote Gostev in the paper published online, but by the middle of the month, that chore was completed. And then exploit went up for sale.
"It seems that two or three competing hacker groups from Russian were selling this exploit for $4,000," said Gostev.
(That's a good article, jam-packed with good info.) Back to the paper. Rainer Bohme surveys 5 different vulnerability markets. Here's one:
Vulnerability brokers are often referred to as “vulnerability sharing circles”. These clubs are built around independent organizations (mostly private companies) who offer money for new vulnerability reports, which they circulate within a closed group of subscribers to their security alert service. In the standard model, only good guys are allowed to join the club. The customer bases are said to consist of both vendors, who thus learn about bugs to fix, and corporate users, who want to protect their systems even before a patch becomes available. With annual subscription fees of more than ten times the reward for a vulnerability report, the business model seems so profitable that there are multiple players in the market: iDefense, TippingPoint, Digital Armaments, just to name a few.
OK! He also considers Bug Challenges, Bug Auctions, Exploit derivatives, and insurance. Conclusion?
It appears that exploit derivatives and cyber-insurance are both acceptable, with exploit derivatives having an advantage as timely indicator whereas cyber-insurance gets adeduction in efficiency due to the presumably high transaction costs. What’s more, both concepts complement one another. Please note the limitations of this qualitative assessment, which should be regarded as a starting point for discussion and exchange of views.
Picturing her location
On this article there is a picture. Which is worth a thousand words.
Coming to a mobile/cell near you. The text says "as of 04/11/2005 15:30:51 (2 months, 2 weeks ago), the GPS Device PERSONAL TRACKER was in the vicinity of Wimbledon"
Which reminds me of the recent Woody Allen movie, Match Point. I should also pass on Fm's pointer that as of 05/23/2005 12:00:00 (2 years, 9 months ago), the NTK Threats Tracker was in the vicinity of spot on:
Still, technology marches on. If you ask us, the real future is in *massively parallel peer-to-peer* elves. Take FLEET ONLINE. This Dutch business-oriented service was introduced a month ago to the UK. It's a pay-as-you-go site that lets companies instantly locate their employees' mobile phones, to a granularity of the nearest cell (ie 50m in urban areas). Positioning costs 25p a shot. Here's the real gimmick, though: you can sign up yourself, and then add any mobile phone you'd like to be geolocated. Oh sure, your victim will get an initial "Do you want to be tracked?" opt-in message, and then another in two weeks. But think of all the phones you can get physical access to long enough to say yes to that original text. Friends! Spouses! Potential stalking fodder! And what you could do in two weeks. Supposing you're a burgling elf: you could nick that phone, sign it up, give it back, find out where they live via the geolocator. And then *find out when they're out*! It's a RISKS Digest all of its own! http://www.fleetonline.net/ - that'll give the geourl people something to play with
February 06, 2006
Edgar Rice Burroughs on Complementary Currency
Hasan finds Gutenberg's copy of "A PRINCESS OF MARS," (1917):
"The brothers had supplied me with a reddish oil with which I anointed my entire body and one of them cut my hair, which had grown quite long, in the prevailing fashion of the time, square at the back and banged in front, so that I could have passed anywhere upon Barsoom as a full-fledged red Martian. My metal and ornaments were also renewed in the style of a Zodangan gentleman, attached to the house of Ptor, which was the family name of my benefactors."They filled a little sack at my side with Zodangan money. The medium of exchange upon Mars is not dissimilar from our own except that the coins are oval. Paper money is issued by individuals as they require it and redeemed twice yearly. If a man issues more than he can redeem, the government pays his creditors in full and the debtor works out the amount upon the farms or in mines, which are all owned by the government. This suits everybody except the debtor as it has been a difficult thing to obtain sufficient voluntary labor to work the great isolated farm lands of Mars, stretching as they do like narrow ribbons from pole to pole, through wild stretches peopled by wild animals and wilder men.
"When I mentioned my inability to repay them for their kindness to me they assured me that I would have ample opportunity if I lived long upon Barsoom, and bidding me farewell they watched me until I was out of sight upon the broad white turnpike."
How's that for dredging ;-)
The last (US) telegram, another FV copycat, another signature snafu
Western Union sent its last telegram last week. That's a communications method that then survived 150 years - a salutory reminder as to how long some networks take to die. Perhaps in 100 years or so we'll read about the last IPv4 packet...
Samuel Morse, inventor of the Morse Code, sent the first telegram from Washington to Baltimore on May 26, 1844, to his partner Alfred Vail to usher in the telegram era that displaced the Pony Express.It read, "What hath God wrought?"
No news on what other countries are doing, typically.
WSJ writes on Paypal's response to Googles "imminent" entry into the payment systems business.
But PayPal must now contend with Google. The Mountain View, Calif., Web-search giant, which has terrified Silicon Valley with its ability to quickly create new consumer products and services, is developing a rival service called GBuy. For the last nine months, Google has recruited online retailers to test GBuy, according to one person briefed on the service. GBuy will feature an icon posted alongside the paid-search ads of merchants, which Google hopes will tempt consumers to click on the ads, says this person. GBuy will also let consumers store their credit-card information on Google.Google said that it has acknowledged publicly on many occasions that it is working on payment products. The company also said it already processes online payments for ad services, as well as fees from consumers who use features such as Google Store and Google Earth. It declined to comment on any pending products.
Basically, Google is going the conventional copy-Paypal route. Install a credit card with Google, buy your retail products and get Google to aggregate the payments. You'll probably have a balance and be billed monthly. This is the same model that First Virtual pioneered, and muffed. Paypal refined it slightly (removed the two obvious bugs) and won big time. (Peppercoin tried this, not sure how they are doing.)
Why then is it taking so long? One wonders, but I'd speculate that for Google the honeymoon is over, and they have to dot the i's and cross the t's. If they muff it they might not get a second chance. Just speculation, mind.

In non-digital signature news, consider the plight of the Chairman of Qantas caught red-handed with copies of aircraft plans on entering american airspace:
Yet when the TSA rifled through her bag last year at Los Angeles Airport, their discovery of aircraft diagrams got them salivating. "Why have you got all this this?" one asked. "'I'm the chairman of an airline. I'm the chairman of Qantas," replied Margaret. "But you're a woman," replied the TSA goon. ... After a one hour interrogation and with TSA officials unimpressed by Margaret's production of official Quantas letterhead documents, she devised a way out that speaks volumes about the nature of this whole farce.She simply wrote a note to the TSA official saying that she was CEO of Quantas and signed it.
Notice two interesting issues other than the obvious that the TSA doesn't know what planet it is on. Firstly the checker was trained to pick up on inconsistencies and picked up that a woman was calling herself Chairman. In California, that's inconsistent and politically incorrect. In Australia, that's more like a statement of pride. Oops. So there is an obvious limitation in teaching sophisticated checking of cultural cues to someone who has never left California.
Secondly, a signed statement carries enough weight to have over-ridden the entire process. What does that say about signatures? What does that say about bureaucracies and social engineering? Can you imagine the Chairman whipping out her smart card, inserting it into the TSA's reader and digitally signing a statement?
(Which brings to mind the infamous digital signing story from the 90s when the US President and the Irish PM used smart cards to sign an ecommerce agreement... After signing the treaty, they swapped the smart cards as if they were football jerseys...)
A Nokia Without A Phone
The Nokia 770 has just been released ... without a phone or a camera (photo taken from an Ericsson). But it does have a full-model Linux install and can be used for all things Unix.
(And, a VoIP phone is coming soon, they say, in the "2006 Edition." I wonder if Nokia reads the news...)
Seriously though, the nexus with FC is more than reading this morning's other blog entry - we want our own pocket PC so we can stick on our secure online payments program. Either a completely secure browser environment for online banking or WebFunds for secure payments. Unfortunately, the small model Java Mobile isn't worth the bother to rewrite all the apps.

February 04, 2006
The Price for Your Identity
So what does it cost to forge an identity? Here's a list of costs (with updates moved to end) that lead us to the answer. First off, in Britain:
When interviewed the duo said they were conducting at least eight transactions a day, totalling around 5,000 sales over two years. A passport would cost £350, a national insurance card or a driving license would cost £50 to £75.
In Japan, driver's licences are no trouble if you know a Colombian (sorry, URL is duff, see below for full story).
The Hyogo prefectural police and other police headquarters have arrested 12 members of the ring, nine of them Colombians. The police reported that some of the suspects said that in addition to the forged passports, they bought bogus driver's licenses and cash cards before entering Japan for only 20 dollars.
Back to Britain, and the Sunday Herald dives into the business of undercover policework. Here's a heavily redacted snippage indicating a top-drawer contender.
He tells us one passport costs just over £1000, but if we buy more, the price drops to around £800. ... There, Pavel brings out a sample of the kind of passport he will be able to get for us. The passports are 100% authentic to the eye. ... British immigration and passport experts who examined the document on guarantee of anonymity said it was “the very best [they’d] ever seen”. It even passed an ultraviolet light test which British passport controllers use to show up hidden watermarks which are in every genuine document.They said it was “real” and could easily be used to open a bank account without alerting any suspicion.
...
The officer, who takes the lead on ID theft within the SDEA, added: “There has been an upswing in the trade in fake documentation.
Addendums. Just found some numbers from an old post on EC:
Social Security cards run about $20, green cards about $70 and a California driver's license between $60 and $250. The price jumps up for higher-quality documents, such as IDs with magnetic strips containing real information — often from victims of identity theft.
Maybe that's where I got the idea from...
Please note that the purpose of collecting this information is for security researchers to form a validated view of what it costs an attacker to breach their designs (so I won't bother to point out where you can buy them).
Most security designs simply assume that collecting the identity of someone grants the holder magical security properties; unfortunately the truth is far less encouraging and the result is that relying on identity collection is probably only reliable for stopping honest people and your poorer class of criminal from defrauding the system.
Here's my predicted benchmark - forging any identity costs approximately 1000 (in today's major units). I'll update that as we get better into it.
20 dollars IDs foil immigration officials The Yomiuri Shimbun
Colombians arrested here over their suspected involvement in a burglary ring entered Japan on fake passports and other forms of counterfeit identification purchased for only 20 dollars, police learned Thursday.
The Hyogo prefectural police quoted one of the suspects as saying there is an organization in Colombia that forges such documents.
The ring is suspected of committing more than 100 burglaries in 11 prefectures, including Osaka and Hyogo, over the last three years, netting items and cash worth hundreds of millions of yen.
The Hyogo prefectural police and other police headquarters have arrested 12 members of the ring, nine of them Colombians. The police reported that some of the suspects said that in addition to the forged passports, they bought bogus driver's licenses and cash cards before entering Japan for only 20 dollars.
Some of the suspects reportedly told the police that many houses are left unlocked in Japan, and people here pay little thought to crime prevention.
The suspects are believed to have sold electrical appliances and other stolen items and sent the money to relatives in Colombia.
According to the Hyogo prefectural police, one of the suspects previously had been deported from Japan, but returned on a fake passport.
The police arrested the alleged ringleader Akihiro Nagashima, 36, and two Colombian men in November on suspicion of stealing a television and other items from a house in Wakayama. Nagashima has been indicted on the charge.
The burglary ring is believed to comprise about 20 members, about 80 percent of whom are believed to be Colombians.
(Jan. 28, 2006)
¿ The Yomiuri Shimbun.
http://www.yomiuri.co.jp/dy/national/20060128tdy02001.htm
Addendums.
20060305 USA reports how much it costs to find false identities:
Glendining offers his doormen $20 gift certificates for each fake ID pulled. In recent years, the fake IDs have gotten better. “You really gotta make the best effort you can,” Glendining said.The bar keeps a sample of real and fake IDs around for doormen to learn from. Telltale signs of a fake include IDs that crack when bent, eye color or height that doesn’t match or a nervous person shuffling. But oftentimes, it comes down to the feel of the ID.
Spotted in EC.
20060223. Israel:
The Israeli passport is considered to be one of the easiest passports to forge and can be purchased in Asia, and especially in Thailand's markets, for anywhere from USD 500 to 2000. The Israeli passport is in great demand because people carrying it can enter Asian countries without a visa. .... During interrogation, [six Iranians] confessed that they purchased the passports in Thailand for USD 1,000 for the purpose of entering Macau easily.
20060216, Britain:
LONDON: The head of security at Arsenal’s new stadium ran a racket supplying guards on the site with fake passports. Ademola Adeniran, 39, an illegal immigrant, supplied documents stamped with "indefinite leave to remain" for men working there. Adeniran, of Hackney, was caught with more than 100 fake Nigerian and South African passports when police raided his home. They are thought to be worth £200 each on the black market.
20060212. In Britain
London is a major centre for Asian and African gangs based in Thailand to sell counterfeit European passports, mostly to people from the Middle East, immigration police chief Pol Lt-Gen Suwat Thamrongsrisakul says. Immigration police last year seized 572 fake passports, of which 184 were Belgian, 155 Portuguese, 139 Spanish and 94 French, he said yesterday. All the counterfeits were printed in Bangkok, taken to London and sold for about 1,000 (about 68,000 baht) each by brokers who made about 20% profit on them, he said.
20060516. In Britain
"I charge £700 for each one but can give you a £100 discount if you order two. I can do most EU countries including Greece, Denmark, Spain, Italy, Poland, Latvia and Lithuania."
February 02, 2006
Negotiation and the rule of three favours
Over on Guy's blog I noticed his "The Art of Schmoozing" which concludes with these two crossovers to our local work on favour currencies:
#8 Give favors. One of my great pleasures in life is helping other people; I believe there's a big Karmic scoreboard in the sky. God is keeping track of the good that you do, and She is particularly pleased when you give favors without the expectation of return from the recipient. The scoreboard always pays back. You can also guess that I strongly believe in returning favors for people who have helped you.#9 Ask for the return of favors. Good schmoozers give favors. Good schmoozers also return favors. However, great schmoozers ask for the return of favors. You may find this puzzling: Isn't it better to keep someone indebted to you? The answer is no, and this is because keeping someone indebted to you puts undue pressure on your relationship. Any decent person feels guility and indebted. By asking for, and receiving, a return favor, you clear the decks, relieve the pressure, and set up for a whole new round of give and take. After a few rounds of give and take, you're best friends, and you have mastered the art of schmoozing.
These two points are actually related in game theory. It works like this: negotiation is split into two separate sides (by what is called the prisoner's dilemma, but please save that for another day). These sides are known as win/win and win/lose, and they are like yin and yang.
Most people can figure out what that means just from the titles - when in a win/win we are looking for how we benefit from each other and both come out ahead in the long run. When in win/lose, I try to win at your expense.
Our problem is focussed then on knowing whether we are in win/win or in win/lose. If we are in win/lose, then we definately should walk away from any deal. Schmoozing, in Guy's terms, is pointless in win/lose, because this just gets you deeper into a potential loss. One day, if not today, when you might win.
So how do we determine which we are in? It's not as easy as one would think.
The answer is definately not in words; and in my experience, if someone attempts to impress you with statements like "let's search for the win/win," it's as good a signal that they may be thinking win/lose as win/win. Be careful not to be lulled in by such mere words, as they are stock in trade for the win/loser.
One way to determine is what I think of as the rule of three favours. In this tactic, you offer three unrelated favours to your counter-schmoozer (Guy's #8), and you also put yourself in the position of desiring the return of those favours (see Guy's #9).
But don't desire it too aggresively - the essence here is to see whether the person will accept the favours, and naturally return same when given the opportunity.
Why does this work? It works because win/win and win/lose are very very deep-seated human patterns of behaviour. People are generally either one way or the other. Most people naturally fall into win/lose, probably from childhood battles and the general darwinian environment of the kindergarten. As we grow older and mature some, a lucky few of us discover the higher plain of win/win, and we work hard to develop that attitude.
So if you offer three nice juicy favours to a normal, natural win/lose schoolyard bully, it will be beyond their ability and their understanding to avoid abusing the offering. Which means they will take the favours and not return them. Even if a natural win/loser understands the theory of win/win, he has a choice - either practice win/win at some short term practical and emotional cost, or go with his gut instincts. Either way, he reveals to you whether he is ready for some serious business.
And thus you differentiate your partner. We need to try three times, as one test can be accidental, either way. Two can be a pattern, but three is consensus.
A final tip - don't forget to uncorrelate the favours, so don't mark them all with a pressed flower!