October 31, 2011
_Currency Wars_
 If you want some view on the future, James Turk reviews a new book: Currency Wars, by Jim Rickards:
If you want some view on the future, James Turk reviews a new book: Currency Wars, by Jim Rickards:
.... the first part being almost surreal because it reads more like a novel than non-fiction. It details Rickards’ participation in an exercise at the Warfare Analysis Laboratory near Washington D.C. This group is one of the Defense Department’s leading venues for war games and strategic planning, but in a first-ever event, the game in which Rickards joined was not a war-fighting simulation. Rather, several dozen people from the military, academic and intelligence communities fought a global financial war using currencies and capital markets to support national interests. Rickards and two colleagues were invited to give the simulation some real-world, Wall Street expertise about markets, which they certainly did.I guarantee that when you start reading this part, you won’t put the book down until you learn the outcome of the war. It reads better than a suspense novel, even though the ending is somewhat anti-climactic and predictable. While I won’t spoil it for you by divulging the ending, I will note that gold has a big role to play. In fact, gold reappears throughout the whole book.
In the second section, Rickards analyzes the first two currency wars (CWI and CWII). ...
From the "you read it here first" department:
The final section of the book explains why the world is now fighting Currency War III, which Rickards believes began in 2010. He speculates that there are three possible outcomes from CWIII – paper, gold or chaos. Each of these alternatives is analyzed in detail, providing readers with much food for thought.
Actually, the scenes of this war go back to the issuance of the Euro as a credible alternative, and play their part in the great Financial Crisis of the 21st century. For confirmation of the thesis, Goldmoney's blog also pointed at The Real Contagion Risk which makes the same point: watch for the Central Banks to shift out of US Treasuries:
Step 1: As the global growth story frays, global trade decelerates, and the sovereign and total debt burdens of various countries drag at economic growth, fewer and fewer dollars will be accumulated and stored by various foreign central banks. The typical way dollars are stored is in the form of Treasury holdings. Because of this, several years of record-breaking Treasury accumulation by these foreign banks will grind to a halt and foreign Treasury holdings will begin to decline.
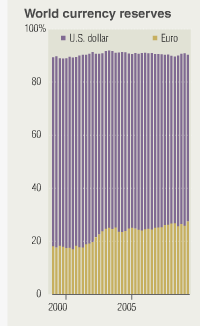
So what's our prediction? Well, it'll be a long slow decline from the dollar as reserve currency. The Euro looked good for a decade, but that's off it's shine now. Expect Central Banks to get back into the currency trading game -- and keep reserves of their bigger partners. And, the next shot in the war will be related to energy -- which is typically priced in dollars.
Gold? Well, everyone expects that to come up. James Turk says:
The harmful effects from abandoning gold still impair economic activity today because the necessary discipline has been removed from the monetary system, creating the global imbalances, debt loads, insolvent banks, risky derivatives and other problems that plague our world. So as economic activity sinks ever deeper into an abyss, think about the cause.
Yeah, and we used to say that governments should go back to the gold standard because we don't trust them with their own units.
Very proven true, no doubt, these days, but there has been a bit of a shift in thinking of late. For me, it was signalled by Alan Greenspan as far back as 1995 (?) when he said "nobody's listening any more." (In response to being asked why he didn't talk about gold anymore.) Fact is, governments will issue their own currencies, whether we trust them or not:
Namely, governments have created this mess, so we cannot rationally expect governments to get us out of it, which is something I have intuitively understood for some time but was also the main conclusion I reached from Rickards’ book.
And, the clanger is this: We don't trust governments, period. We don't trust them to issue their own inflation-protected currency, and we don't trust them to issue a gold-based unit either.
 So, gold goes free. Economists are no longer advising governments to base off gold, because we know it won't work. Gold therefore will remain the independent watchdog it has since the closing of the gold window by Nixon; a three-way tussle between central bankers, gold banks and the buying public.
So, gold goes free. Economists are no longer advising governments to base off gold, because we know it won't work. Gold therefore will remain the independent watchdog it has since the closing of the gold window by Nixon; a three-way tussle between central bankers, gold banks and the buying public.
The future is a world of competitive currencies, USD, Euros, Yen, the Chinese unit ... and gold. With a very slow long decline of the power of the USD.
Disclosure: Author is long gold, and short fingernails.
October 26, 2011
Phishing doesn't really happen? It's too small to measure?
Two Microsoft researchers have published a paper pouring scorn on claims cyber crime causes massive losses in America. They say it’s just too rare for anyone to be able to calculate such a figure.Dinei Florencio and Cormac Herley argue that samples used in the alarming research we get to hear about tend to contain a few victims who say they lost a lot of money. The researchers then extrapolate that to the rest of the population, which gives a big total loss estimate – in one case of a trillion dollars per year.
But if these victims are unrepresentative of the population, or exaggerate their losses, they can really skew the results. Florencio and Herley point out that one person or company claiming a $50,000 loss in a sample of 1,000 would, when extrapolated, produce a $10 billion loss for America as a whole. So if that loss is not representative of the pattern across the whole country, your total could be $10 billion too high.
Having read the paper, the above is about right. And sufficient description, as the paper goes on for pages and pages making the same point.
Now, I've also been skeptical of the phishing surveys. So, for a long time, I've just stuck to the number of "about a billion a year." And waited for someone to challenge me on it :) Most of the surveys seemed to head in that direction, and what we would hope for would be more useful numbers.
So far, Florencio and Herley aren't providing those numbers. The closest I've seen is the FBI-sponsored report that derives from reported fraud rather than surveys. Which seems to plumb in the direction of 10 billion a year for all identity-related consumer frauds, and a sort handwavy claim that there is a ration of 10:1 between all fraud and Internet related fraud.
I wouldn't be surprised if the number was really 100 million. But that's still a big number. It's still bigger than income of Mozilla, which is the 2nd browser by numbers. It's still bigger than the budget of the Anti-phishing Working Group, an industry-sponsored private thinktank. And CABForum, another industry-only group.
So who benefits from inflated figures? The media, because of the scare stories, and the public and private security organisations and businesses who provide cyber security. The above parliamentary report indicated that in 2009 Australian businesses spent between $1.37 and $1.95 billion in computer security measures. So on the report’s figures, cyber crime produces far more income for those fighting it than those committing it.
Good question from the SMH. The answer is that it isn't in any player's interest to provide better figures. If so (and we can see support from the Silver Bullets structure) what is Florencio and Herley's intent in popping the balloon? They may be academically correct in trying to deflate the security market's obsession with measurable numbers, but without some harder numbers of their own, one wonders what's the point?
What is the real number? Florencio and Herley leave us dangling at that point. Are they are setting up to provide those figures one day? Without that forthcoming, I fear the paper is destined to be just more media fodder as shown in its salacious title. Iow, pointless.
Hopefully numbers are coming. In an industry steeped in Numerology and Silver Bullets, facts and hard numbers are important. Until then, your rough number is as good as mine -- a billion.
October 23, 2011
HTTPS everywhere: Google, we salute you!
Google radically expanded Tuesday its use of bank-level security that prevents Wi-Fi hackers and rogue ISPs from spying on your searches.Starting Tuesday, logged-in Google users searching from Google’s homepage will be using https://google.com, not http://google.com — even if they simply type google.com into their browsers. The change to encrypted search will happen over several weeks, the company said in a blog post Tuesday.
 We have known for a long time that the answer to web insecurity is this: There is only one mode, and it is secure.
We have known for a long time that the answer to web insecurity is this: There is only one mode, and it is secure.
(I use the royal we here!)
This is evident in breaches led by phishing, as the users can't see the difference between HTTP and HTTPS. The only solution at several levels is to get rid of HTTP. Entirely!
Simply put, we need SSL everywhere.
Google are seemingly the only big corporate that have understood and taken this message to heart.
Google has been a leader in adding SSL support to cloud services. Gmail is now encrypted by default, as is the company’s new social network, Google+. Facebook and Microsoft’s Hotmail make SSL an option a user must choose, while Yahoo Mail has no encryption option, beyond its intial sign-in screen.
EFF and CAcert are small organisations that are doing it as and when we can... Together, security-conscious organisations are slowly migrating all their sites to SSL and HTTPS all the time.
It will probably take a decade. Might as well start now -- where's your organisation's commitment to security? Amazon, Twitter, Yahoo? Facebook!
October 20, 2011
next-gen Stuxnet targets SCADA companies for intelligence
As an example of good disclosure that we can use to analyse our risks on new attacks come from Symantec:
Key points:Executables using the Stuxnet source code have been discovered. They appear to have been developed since the last Stuxnet file was recovered.
The executables are designed to capture information such as keystrokes and system information.
Current analysis shows no code related to industrial control systems, exploits, or self-replication.
The executables have been found in a limited number of organizations, including those involved in the manufacturing of industrial control systems.
The exfiltrated data may be used to enable a future Stuxnet-like attack.
Now, Symantec are somewhat 'interested' in this disclosure, in the commercial sense, because they gain reputation and thence sell more defences to more customers. They could just shout FUD out to the world. But in this sense, the market has moved to a sense of competition on solid disclosures, as compared by competitor McAfee also putting its own analysis out there.
And, it turns out that Symantec is doubly interested as the new trojan was signed by one of their (Verisign?) certificates:
*Update [October 18, 2011] - *Symantec has known that some of the malware files associated with the W32.Duqu threat were signed with private keys associated with a code signing certificate issued to a Symantec customer. Symantec revoked the customer certificate in question on October 14, 2011. Our investigation into the key's usage leads us to the conclusion that the private key used for signing Duqu was stolen, and not fraudulently generated for the purpose of this malware. At no time were Symantec's roots and intermediate CAs at risk, nor were there any issues with any CA, intermediate, or other VeriSign or Thawte brands of certificates. Our investigation shows zero evidence of any risk to our systems; we used the correct processes to authenticate and issue the certificate in question to a legitimate customer in Taiwan.
Still, I can't fault the disclosure: they investigated and now claim it was a good cert, stolen from the client. They revoked it the same day of being shown the code/sig.
This information is provided in a way we can RELY on it. From this we can make risk management judgements. See more here.
October 18, 2011
Liability & disclosure - the end of an era is in sight?
Liability is increasing slowly for cyber-exposed companies. We're in an exploratory court phase as litigants try different things. For a while, we'll see these filings in USA courts, which won't get far ... but then one will find the formula, and a company will be hit by a huge judgement.
"The US Department of Defense has been hit with a $4.9 billion (£3.1 billion) lawsuit over a recently disclosed data breach involving TRICARE , a healthcare system for active and retired military personnel and their families."
Meanwhile, pressure for breach disclosure increases. Now the SEC is in on the act:
"The SEC guidance clarifies a long-standing requirement that companies report 'material' developments, or matters significant enough that an investor would want to know about them. The guidance spells out that cyberattacks are no exception.For example, the SEC says, a company probably will need to report on costs and consequences of material intrusions in which customer data are compromised. The company's revenue could suffer, and it could be forced to spend money to beef up security or fight lawsuits. In addition, if a company is vulnerable to cyberattack, investors may need to be informed of the risk, the SEC said."
This is also a first step that has increasing and more costly ramifications. May as well get used to it: disclosure will be part of the future. Liabilities are coming.
Perhaps the great age of software freedom is coming to an end, in more ways than one?
October 13, 2011
Founders of SSL call game over?
RSA's Coviello declares the new threat environment:
"Organisations are defending themselves with the information security equivalent of the Maginot Line as their adversaries easily outflank perimeter defences," Coviello added. "People are the new perimeter contending with zero-day malware delivered through spear-phishing attacks that are invisible to traditional perimeter-based security defences such as antivirus and intrusion detection systems." ®
The recent spate of attacks do not tell us that the defences are weak - this is something we've known for some time. E.g., from 20th April, 2003, "The Maginot Web" said it. Yawn. Taher Elgamal, the guy who did the crypto in SSL at Netscape back in 1994, puts it this way:
How about those certificate authority breaches against Comodo and that wiped out DigiNotar?It's a combination of PKI and trust models and all that kind of stuff. If there is a business in the world that I can go to and get a digital certificate that says my name is Tim Greene then that business is broken, because I'm not Tim Greene, but I've got a certificate that says this is my name. This is a broken process in the sense that we allowed a business that is broken to get into a trusted circle. The reality is there will always be crooks, somebody will always want to make money in the wrong way. It will continue to happen until the end of time.
Is there a better way than certificate authorities?
The fact that browsers were designed with built-in root keys is unfortunate. That is the wrong thing, but it's very difficult to change that. We should have separated who is trusted from the vendor. ...
What the recent rash of exploits signal is that the attackers are now lined up and deployed against our weak defences:
Coviello said one of the ironies of the attack was that it validated trends in the market that had prompted RSA to buy network forensics and threat analysis firm NetWitness just before the attack.
This is another unfortunate hypothesis in the market for silver bullets: we need real attacks to tell us real security news. OK, now we've got it. Message heard, loud and clear. So, what to do? Coviello goes on:
Security programs need to evolve to be risk-based and agile rather than "conventional" reactive security, he argued."The existing perimeter is not enough, which is why we bought NetWitness. The NetWitness technology allowed us to determine damage and carry out remediation very quickly," Coviello said.
The existing perimeter was an old idea - one static defence, and the attacker would walk up, hit it with his head, and go elsewhere in confusion. Build it strong, went the logic, and give the attacker a big headache! ... but the people in charge at the time were steeped in the school of cryptology and computer science, and consequently lacked the essential visibility over the human aspects of security to understand how limiting this concept was, and how the attacker was blessed with sight and an ability to walk around.
Risk management throws out the old binary approach completely. To some extent, it is just in time, as a methodology. But to a large extent, the market place hasn't moved. Like deer in headlights, the big institutions watch the trucks approach, looking at each other for a solution.
Which is what makes these comments by RSA and Taher Elgamal significant. More than others, these people built the old SSL infrastructure. When the people who built it call game over, it's time to pay attention.