June 29, 2005
Mozilla drops Open in favour of Smoke Filled Rooms
Open is a big word these days. It started out as open source, being the progression of AT&T's distro of Unix leading to BSD and then to GPL. For computer source code, open works well, as long as you are doing the code anyway and can't figure out how to sell it. Instead of just keeping it secret, share the source and profit on the service.
Or something - the economic ramifications are quite interesting and deserve a much wider attention (especially with our new Hayekian and Misean perspectives, and the changing economics of digital property).
People have also applied open to other things: I apply it to Governance, there is a group working on words and music called Open Commons and this blog is under one of their licences. People have even prepared legal cases in Open forums. The list of experiments in Open This and Open That is quite long. I want to apply it to FC, and indeed we've published many papers and much source code without seeing much or any openness in FC at the project level to date, so it remains a big question: just how far does open go?
One of the things we have found is that open source helps security. People have often thought too much of this - that open source is necessary for security. No such applies, it certainly helps a lot, but so do many other things, and there are plenty of secure systems with closed source. Strangely, open also clashes with the process of fixing bugs. Clearly, if there is a bug in your source, and you know it, you want it fixed before the bad guys find out. Telling everyone that there is a bug might not be the smartest thing to do.
So security is more than source, it's a process. The security process involves many elements. Patching and bug fixes, of course. These are the things that non-security projects know about and the things that the press reports on (like those silly Symantec comments on how many security advisories each competitor has issued).
But there is more, much more, and these are the things that projects with a Security Goal have developed. One of these things is a relatively open process. What this means is that decisions on security are taken openly - in open forums. Even though uncomfortable and noisy, the result is better because the interests of all are heard, including the users, who normally aren't adept enough to enter these highly technical debates. Hopefully someone there will represent the users if they know this is an open process.
The problem with the alternate is "agenda capture" (or co-option?). If a project conducts secret negotiations to do some sort of security thing, then you can bet your bottom dollar that the participants want it secret because they are attempting some sort of coup. They are trying to achieve something that won't work when exposed to the disinfectant of open sunlight. It infringes the interests of one group or another, and if it didn't there wouldn't be any reason to keep it secret.
So it was with sadness that I discovered that the Mozilla Foundation had entered into the smoke filled rooms of secret negotiations for security changes. These negotiations are apparently over the security User Interface. It involves some other browser manufacturers - Microsoft was mentioned - and some of the CAs - Verisign has not been mentioned that I have heard.
There is no doubt that Mozilla has walked into an agenda capture process. It specifically excluded one CA, CACert.org, for what appears to be competitive reasons. Microsoft enters these things frequently for the purposes of a) knowing what people are up to, and b) controlling them. (Nothing wrong with that, unless you aren't Microsoft.) At least one of the participants in the process is in the throes of selling a product to others, one that just happens to leave itself in control. The membership itself is secret, as are the minutes, etc etc.
The rooms were filled with smoke a month or two back. And now, people are reportedly beavering away on the results, which are again secret. Normally, cartel theory will tell you that these sort of approaches won't work positively because of the economics of game theory (check out the Prisoner's Dilemma). But in this case, there was "A Result" and that "Result" is now being used as a justification for not addressing other initiatives in phishing. We don't know what it was but it exists and it has been accepted, secretly, without formal process or proposal, by Mozilla.
I have therefore departed the scene of Mozilla. This is a road to disaster for them, and it is blatently obvious that they haven't the business acumen to realise what they've been sucked into. As the security process is well and truly compromised at this point, there is no hope for my original objectives, which were to encourage anti-phishing solutions within Firefox.
Personally, I had thought that the notion of open source was enough to assume that an open process in security would follow, and a sterling effort by Frank Hecker seemed to support this. But I was wrong; Mozilla runs a closed security process and even Frank's openly negotiated CA ascendency protocol is stalled in closed session. The actual bug fixing process is documented as closed if there are security issues involved, and from that one small exception, the entire process has closed and to my mind stalled (1, 2). The team is a closed shop (you have to apply, they have to ignore the application), any security decisions are taken in secret forums that we haven't been able to identify, and the whole process flips mysteriously between the security team, the security group and the group sometimes known as "staff". Oh, and in their minds, security is synonymous with PKI, so anything and anyone that challenges the PKI model is rejected out of hand. Which is an issue for those that suggest PKI is at the heart of phishing...
So the security process is either closed or it's not present, which in my mind amounts to the same thing, because one becomes the other in due course. And this is another reason that security processes have to be open - in order to eliminate groupthink and keep themselves alive, the process must defend itself and regenerate itself, out in the open, on a regular basis.
My time there has still been very educational. Coming from the high security world of payments and then entering the medium security world of the browser, I've realised just how much there is yet to learn about security. I have a developing paper on what it means to be a security project, and I've identified about 19 or so factors. Comparing and contrasting Security Goal projects like the BSDs and the OpenPGPs with Mozilla has teased these factors out slowly, over a year or so. The persistence of security myths has led me on a search via Adam's security signals suggestion to Michael Spence's job market signalling theory and into a new model for Silver Bullets, another paper that is evolving (draft in the normal place).
But I have to face facts. I'm interested in security and specifically in the security of the browsing process under its validated threat of phishing. If the Mozilla Foundation cannot produce more than an alpha effort in certificate identification in 2.5 years of my being involved in what passes for their open security forum, that has to suggest that Mozilla is never going to meet new and evolving objectives in security.
June 27, 2005
Definitions, competition-by-regulation, and Justice-by-Press-Release
I had a go at upgrading the Wikipedia definition of Financial Cryptography. Anyone can edit it and improve on it, and I left you plenty of room for that!
I also added an article on Token Money as I saw it. Curiously, it may be a definition that only exists in the FC world! The Money entry in Wikipedia saw it differently, referring to tokens as those that had no intrinsic value (by which it meant gold). Any economists in the house to rule on this?
SL points me to Simpay, a pan-european mobile phone payments system that has decided not to roll out everything ... in what appears to be a response to the overbearing regulation by the EU. Donald at linkdump has a few choice words on how the regulators now get to clean up the mess they made:
Mobile operators make money by exploiting their own quick-and-dirty payment mechanisms and (inter)national roaming agreements for the interoperable use of these instruments. With Simpay they found out what it would cost to build and operate a system that really accounts for all transactions. Also, they may have started to discuss interchange fees for Simpay, the applicable Regulation 2560 as well as the future legal framework for payments in the European Market.The conclusion could then well have been that they are far better of with the current grey-area, less-visible payment arrangements than with a formal payment processor that has no business case to work on. The benefit: more income from payments business while maintaining less visibility and transparance.
Well, of course. The regulations were put in place to protect the banks from competition, and the competitors' mission is to avoid the regulations. Society cheers you on! Speaking of regulating banks, what have you to say about the chart 1/3 way down in this article:
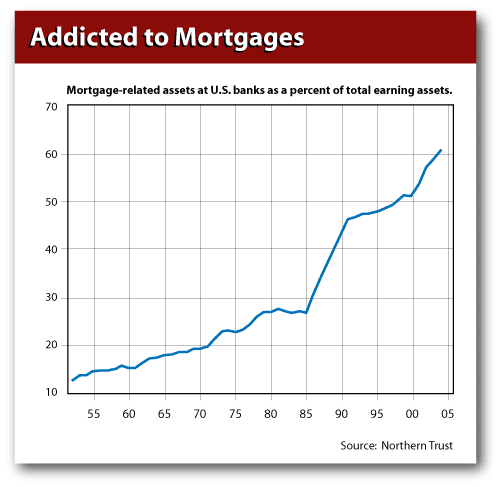
The Economist (thanks, Ron!) weighs in on the data crisis in the USA. Not much to say other than they've picked up a series of soundbites from b-school profs who all think the board should pay more attention. With opinions like that it's no wonder the data gets lost. But it gets worse:
The FTC decided to settle with BJ's Wholesale Club, a retailer whose lax data-protection practices the agency said constituted an “unfair practice that violated federal law.” The firm collected too much data, kept it too long, did not encrypt it, lacked password protections and left its wireless network open. This, in turn, enabled criminals to produce counterfeit credit and debit cards using stolen customer data and rack up millions of dollars in fraudulent charges. The firm has agreed to fix these problems and undergo information-security audits for 20 years.
So the FTC is getting tough, but what's with the "information-security audits for 20 years" nonsense? Straight on to KPMG, then. Confirming the judicial flavour of issuing justice only at arbitrary times and places, the discussion surrounding the pending and alleged KPMG indictment is centering around whether we really need to stick another barb in the already wounded animal known today as the Big Four Accounting Firms:
Some accounting experts said that, while an indictment could surely ground KPMG, it would not bode well for the accounting industry. Dozens of top notch corporations had to scramble around the world to find a new auditor after Arthur Andersen was brought down by an indictment over its role in the accounting fraud committed at energy trader Enron Corp.There does not seem to be any appetite for reducing the number of audit firms any more. It is already difficult enough for a large corporate entity to retain the size and sophistication of auditors. (An indictment) will be intolerable," said Mark Cheffers, head of auditor research firm Audit Analytics.
What ever happened to compassion and the right to a speedy trial? If the audit is dying, put it out of its misery! The public has little faith in audits, so what's the point?
And over in gambling territory, the poker players are calling the US Department of Justice's bluff. The now legendary 5 billion pounds IPO of just one of the online poker companies has drawn out the DoJ in a its approach to gambling - tell everyone that gambling is illegal, but don't actually litigate so aggressively just in case they are wrong.
One has to applaud the poker players in this. If justice is to be done by press release not law, then what happens when various officials decide to misinterpret the law for their own purposes?
I saw a perfect of example of regulation by press release becoming a protection subsidy over at the Wikipedia definition of money where some innocent said that Western economies ban the private issuance of money. That's not actually the case, and it is explicitly not the case to my knowledge in USA, Europe (the eMoney directive), New Zealand, Australia and one supposes any country that has ever trialled a smart card money. Luckily, it looks like someone else saw it and corrected the flaky text in a couple of days. Pretty snappy those Wikipedia folks!
Tao reports (here and here) on the CISSP certification, a common test you can take to become a security professional. So my question is: is a CISSP a neutral signal? And if not is it negative or positive? And what do I do with this CISSP spam I'm now getting?
June 26, 2005
Ian Grigg - Triple Entry Accounting
It was widely recognised since David Chaum's designs first appeared that the new 'digital certificate' model of money was not aligned or symmetrical with accounting techniques such as double entry book keeping. Many people expected the two to compete and indeed many money systems avoided combining them; this is I believe one of the few efforts to integrate the two and show them as better in combination than apart.
The digitally signed receipt, an innovation from financial cryptography, presents a challenge to classical double entry bookkeeping. Rather than compete, the two melded together form a stronger system. Expanding the usage of accounting into the wider domain of digital cash gives 3 local entries for each of 3 roles, the result of which we call triple entry accounting.This system creates bullet proof accounting systems for aggressive uses and users. It not only lowers costs by delivering reliable and supported accounting, it makes much stronger governance possible in a way that positively impacts on the future needs of corporate and public accounting.
Comments below as always!
Nick Szabo - Scarce Objects
Nick Szabo is one of the few people who can integrate contracts into financial cryptograpy. His work with smart contracts echoes around the net, and he last year he gave the keynote presentation at the Workshop on Electronic Contracts. In this paper he seeks to integrate scarcity and property constructs with the object oriented model of programming.
Scarce objects, a.k.a. conserved objects, provide a user and programmer friendly metaphor for distributed objects interacting across trust boundaries. (To simplify the language, I will use the present tense to describe architectures and hypothetical software). Scarce objects also give us the ability to translate user preferences into sophisticated contracts, via the market translator described below. These innovations will enable us for the first time to break through the mental transaction cost barrier to micropayments and a micromarket economy.
A scarce object is a software object (or one of its methods) which uses a finite and excludable resource -- be it disk space, network bandwidth, a costly information source such as a trade secret or a minimally delayed stock quotes, or a wide variety of other scarce resources used by online applications. Scarce objects constrain remote callers to invoke methods in ways that use only certain amounts of the resources and do not divulge the trade secrets. Furthermore, scarce object wrappers form the basis for an online economy of scarce objects that makes efficient use of the underlying scarce resources.
Scarce objects are also a new security model. No security model to date has been widely used for distributing objects across trust boundaries. This is due to their obscure consequences, their origins in single-TCB computing, or both. The security of scarce objects is much more readily understood, since it is based on duplicating in computational objects the essential security features of physical objects. This architecture is "affordable" in Donald Norman's sense, since human brains are designed to reason in much more sophisticated ways about physical objects than about computational objects. It is thus also "affordable" in terms of mental transaction costs, which are the main barrier to sophisticated small-scale commerce on the Net. Finally, it will solve for the first time denial of service attacks, at all layers above the primitive scarce object implementation.
Comments below please!
June 22, 2005
Skype - a prince but still covered in warts
Skype might be justly lauded in these pages for doing something that only one other product has ever done - getting crypto to the masses in a usable fashion. And it is fair to say that Skype is a killer app in the making. Truly a rising star, definately a joy to watch its progress.
But other than those positive points, it seems that Skype is just like any other crummy business with a crummy app and a crummy attitude to users. Yesterday I spent an afternoon trying to get it working on a linux box, and failed.
Here's the bug list: no obvious way to test the product, no selftest feature, no button, no ping is evident on the screen for both chat or voice. It turns out there is a voice test server called echo123, but that's buried in a FAQ somewhere. No help for the newbie at all as even in the FAQ it isn't clear what they were talking about unless you happen to have used one of these things before.
Secondly, the FAQs could not help. All the basic "windows user level" stuff like where to find your windows firewall was covered, but what it didn't cover was whatever was wrong with this fairly boring setup. (Linux box, Fedora core 3 distro, behind a DHCP router, all outgoing ports open.) The actual failure mode was this: No connection made for voice - to echo or anywhere else, the application just sits there saying "connecting...." forever. (No timouts even. This is a sick app.)
So without a proper way to test and some sort of feedback, it's not possible to even guess where the problem lies. Oddly, chat would send ONE and exactly one message out, and receive ONE and exactly one message in, before disengaging and shutting up. Restarting the application gets you another one message, in and out.
Meanwhile, within 24 hours of starting, I got sent a phish on the email address I created for the account yesterday. Thanks guys - there is really no point in you collecting email addresses if you are going to give them out to phishers. In this case it was a fairly obvious "answer this survey" but what happens when the phishers get smart and learn how to spell? What happens when I need to change my password and the spam filters have blocked that email address?
June 18, 2005
USA credit system is totally compromised, security-wise
I wondered when we'd see this. Tao points to news that 40 million card data units have been breached:
MasterCard International reported today that it is notifying its member financial institutions of a breach of payment card data, which potentially exposed more than 40 million cards of all brands to fraud, of which approximately 13.9 million are MasterCard-branded cards.MasterCard International's team of security experts identified that the breach occurred at Tuscon-based CardSystems Solutions, Inc., a third-party processor of payment card data."
This AP story mentions "the security breach involves a computer virus that captured customer data for the purpose of fraud" and MasterCard "did not know how a virus-like computer script that captured customer data got into CardSystems' network, which MasterCard said was infiltrated by an unauthorized individual."
At this point, Americans may as well get used to the fact that their entire data set is probably in the hands of criminals. (Up until this one broke, the running totals showed about 5 million.)
In my humble opinion, the credit system of the United States of America is totally compromised, security wise. Given the size of the infrastructure, the complexity, the amount of money being made, the existing mess of laws, and the hidden assumptions, it will take decades to clean it up.
No amount of government intervention is going to make you safer, and will probably make things more dangerous for you. Companies have no interest in your security, only in your continuing payments. Get used to it. About all I can suggest is that each and every American learn how the credit system works; take your own steps to secure your identity - there are some cunning tricks. You are on your own, for the foreseeable future.
Also see Emergent Chaos for likely more pervasive coverage. Slashdot has a rash of jokes:
there are some numbers hackers can't stealfor everything else there's MasterCard
(Accepted all over, even if it's not yours.)
And then there's:
Interest rate: 20%Annual Fee: $40
Randomly being declined because the machine is on the fritz: $1-$1000 purchase down the drain.
Being the target of fraud through no fault of your own: Priceless.
June 17, 2005
Hype is free, Common Sense costs Pennies
Phishing news: puddle phishing (targetting small banks) is on the rise, as is phishing outside the US. Both of these are to be expected as phishers move around and try new things. One might suspect that the major US financial institutions have been 'phished out' but I wouldn't say that yet. The browser infrastructure remains riddled with too much swiss cheese security for any but a politician's declaration of victory, and it will be interesting to see how successful DNS attacks are at raising more funds from the hapless victims.
Amid yesterdays's flood of identity/phishing news, there are reports that identity theft is bigger in the US than anywhere else. Long reported in these pages as primarily a US problem, it turns out that people inside the US have now noticed this: Lower Overseas Rates Of Identity Theft Could Guide U.S. Lawmakers, and Privacy Advocates: Look Overseas For Lower Identity Theft Rates (both the same content).
And if you think your data is being phished by crooks, think again. The US Department of Justice is seeking to make matters worse by mandating data collection by the ISPs. Perry quotes this Article:
The U.S. Department of Justice is quietly shopping around the explosive idea of requiring Internet service providers to retain records of their customers' online activities.
More data collected, more value. More value, more theft. We saw the same kneejerk reaction a few months back when Elliot Spitzer floated the idea of making an extra crime. Truly dumb, truly guaranteed to reduce security.
In crypto news, the how to crack SHA1, SHA0 papers from the Shandong team are now released on Prof Wang's site. Good work, but attention is now switched to Dan Boneh's timing attack on AES (also 1 and 2). Slightly embarrassing for the NIST assessment that didn't pick it up, but no need to panic - make sure your AES is constant time.
In closing, some rare common sense spotted in security reporting. Gartner, long a packager of other people's nonsense, has issued its list of 5 most hyped security issues. And, they actually aren't that far off the mark:
- IP (Internet Protocol) telephony...
- malware for mobile devices...
- Fast-moving worms that infect the entire Internet within minutes...
- Wireless hot spots...
- Sarbanes-Oxley financial reporting rules...
It's about time someone stood up and pointed out who's selling clothes to the Emporer (someone like Tao?).
Are Security Threats Really Overhyped?Some experts say VoIP security and mobile viruses already are serious problems.
Grant Gross, IDG News Service Monday, June 13, 2005
Two Gartner analysts released their list of the five most overhyped IT security threats, with IP (Internet Protocol) telephony and malware for mobile devices making the list, but not all IT security vendors agree with the analysts' assessment.
Lawrence Orans, principal analyst at Gartner, and John Pescatore, vice president and Gartner fellow, noted that while attacks on IP telephony and mobile devices may come eventually, current warnings about security problems are ahead of actual attacks.
"Securing IP telephony is very similar to securing a data-only network," Orans said during a presentation last week at the Gartner IT Security Summit in Washington, D.C. "The fact that you could capture packets with e-mail isn't being covered in the trade publications."
Recent concerns about eavesdropping on IP telephony calls have discounted the fact that it's nearly impossible to eavesdrop without being inside of the building where an IP call is initiated or received, with eavesdroppers needing access to the corporate LAN, he said. "It's not really happening on any networks today," he said.
Different Opinion
Not everyone agreed with Gartner's assessment, however. Companies deploying IP telephony or voice over IP services do need to pay attention to security, and users of IP telephony need to protect not only the end-device phones and IP servers, but also signaling and other voice equipment, said Stan Quintana, vice president of managed security services for AT&T. "It's a slightly different, more complex equation than data networks," he said.
The two Gartner analysts see large businesses delaying IT improvements such as wireless LANs because of "overhype" over security threats, they said.
Too much hype on some threats may distract businesses from focusing on other, real threats, added Tom Grubb, vice president of marketing for Vormetric, a data security vendor. This year, a series of massive data breaches at several large companies have occurred, and protecting against data theft, and protecting against insider threats, may be more important than worrying about issues such as malware for mobile devices, he said.
"I think their point was, these things may be threats, but you have to keep your eye on the ball," added Grubb, who attended the Gartner summit.
ID theft and spyware are threats that have gotten a lot of attention lately because they are real, prevalent risks, added Richard Stiennon, vice president of threat research for Webroot Software, an antispyware software vendor.
Going Mobile
Some security vendors have focused on malware for so-called smart phones and other mobile devices, but such devices run on a number of operating systems, unlike the Windows dominance on desktop and laptop computers, Pescatore said. Without a dominant mobile operating system for at least a couple of years, mobile viruses or worms will have a limited impact, he said.
"For any piece of software, somebody can write an attack," Pescatore added. "The key issue is: can somebody write [a mobile attack] that will spread quickly and rapidly and cause more damage to your enterprise than it will cost you to prevent that damage?"
Some security software vendors have hyped mobile malware as a potential problem as a way to expand their business beyond the traditional desktop and laptop markets, Pescatore said. Only about 3 percent of consumers and workers have smart phones and PDAs with always-on wireless connections right now, he added.
"You can see the glint in the antivirus vendors' eyes when they think of the billion mobile phones out there," added Webroot's Stiennon.
A representative of antivirus vendor Symantec said the company isn't trying to hype mobile device threats, but trying to educate users as mobile devices become capable of storing more information. While mobile device security isn't a big issue now, that could change in coming years, said Vincent Weafer, senior director of Symantec Security Response.
"The risk changes dramatically in a short amount of time," Weafer said. "What we're trying to tell people is, if they're deploying these devices, they should deploy them in the right way."
Vormetric's Grubb agreed that mobile malware shouldn't be a top-priority concern for most large businesses, but mobile device security is becoming an issue. As more workers use more powerful mobile devices, companies need to be concerned with the physical security of mobile devices and about what mobile devices are downloading from their networks, he said.
Companies need to be concerned about what kinds of malware mobile devices can bring into a corporate network, added AT&T's Quintana. "The convergence of our networks is a double-edged sword," he said. "It's providing a high level of risk. It's not overhyped."
Also On the List
* Also on the list of overhyped security threats, according to Orans and Pescatore:
Fast-moving worms that infect the entire Internet within minutes will make the Web unreliable for business traffic and virtual private networks (VPNs) . While the SQL Slammer worm in 2003 did much of its damage within 15 minutes, that's the only such example so far of a so-called Warhol worm, Orans said. The analysts predicted that the public Internet will continue to remain a low-cost, safe alternative to closed data networks, although they recommended companies consider using VPNs.* Wireless hot spots are unsafe. While uneducated wireless users can fall victim to hackers, corporations have tools such as VPNs to protect wireless data, Pescatore said. Some wireless carriers and wireless security vendors also offer tools that validate an access point's identity and reduces the risk of connecting to a hacker's access point. Targeted attacks on corporate networks, not picking off wireless user data, is where the money is, said Reed Taussig, chief executive officer of Vormetric. "That's a much larger return on investment than sitting around Starbucks waiting for someone to enter a credit card at Amazon.com," Taussig added. "Hanging around at Starbucks waiting for someone to make a mistake is the definition of a stupid criminal."
* Finally, the Gartner analysts suggested that some vendors are hyping regulatory compliance as a way to achieve security. Regulations such as the U.S. Sarbanes-Oxley financial reporting rules are focused primarily on other issues besides IT, but many corporations remained concerned about compliance reporting, Pescatore said.
"[The hype] often distracts that spending into compliance reporting rather than increasing security," he said.
Steve Roop, vice president of marketing for data loss prevention vendor Vontu agreed. "There's a large number of solutions providers who claim that what they do is the silver bullet," he said.
Pinch me, I must be dreaming!
June 13, 2005
Killing for Pennies, and is AOL, the "gateway drug", cause or cure?
News in virtual gaming property continues to madly echo real life, as a man in China was sentenced for killing a friend after the latter sold his sword for a knight's ransom - 7,200 Yuan (£473). As readers will know, this follows on news of a single island being sold for a fortune and the outrage of cyberspace imitating life (fraud, murder, rape, verbal abuse, hit & run driving discussed in To Kill an Avatar).
A paper at Economics & Security conference on stock market effects from vulnerability announcements got some press.
(to follow: "security isn't working" and the LexisNexus hack...)
When I read that they'd measured a 0.2% drop in Microsoft shares after a vulnerability announcement, I immediately thought this was suspicious. How can the market respond to known news so stupidly? Commentary here is more incisive and critical, pointed to by Adam. Bad news effecting stock prices is a well studied phenomena; there are some other studies on vulnerability and hack announcements.
Rumour of "security isn't working" continues to circulate. Here's a post by Marcus Ranum that tries to draw some conclusions on why security expenditure is sky-rocketing and security is getting worse. Pointed to by Tao. Of course, the conclusions will be easy to disagree with - Marcus assumes binary security values not risk values - but the logic he uses to get to his conclusions is good.
And more on security - if you ever wanted to understand hackers as your threat, have a read of the Wired article on the LexisNexis hack (this is the one where a cop's laptop was breached and this led to getting access to celebrity files and so forth...).
For those who already know what hacking is about, I'll leave you with these choice snippets which address lousy security. The big question - what do we do about lousy security? Is it a fact of life or something we must eradicate? Cause or cure?
Database Hackers Reveal Tactics By Kim Zetter...
Hacking began with AOL
Cam0 is also a suspect in the recent security breach of socialite Paris Hilton's T-Mobile account and was investigated last summer after admitting to Wired News that he hacked America Online and stole AOL Instant Messaging screen names, among other exploits. He has yet to be charged for the AOL breaches but told Wired News on Monday that the AOL activity, which he began in 1997, was the "gateway drug" that emboldened him and other members of Defonic Crew to graduate to other hacking projects.
"If there was a security breach (at AOL), we were all a part of them.... That's how we all started," he said. "We all met up on AOL breaking into their crap. If it wasn't for AOL none of this (LexisNexis stuff) would have happened."
"Shasta," a hacker who knows Defonic Crew but isn't a suspect in the LexisNexis breach, said the success of the AOL breaches made Defonic Crew careless about not covering its tracks in LexisNexis.
"It made them feel invincible," he said. "And they weren't worried about getting caught."
They naturally are circumspect in the face of possible consequences.
"I really wish that I hadn't been able to get access to (the LexisNexis database)," said the 20-year-old, who lives in Rhode Island and goes by the name "Krazed." "Curiosity gets you in trouble."
....
"You start looking at an account that's been logged into 500 times and generated 9,000 reports, for example, that's a lot of information (to examine)," Sibley said. "I'm just saying it's not one group that's compromised LexisNexis. Their security is really bad. This isn't a situation where you're talking about needing an uberhacker to compromise (the system). Their passwords weren't as secure as your average porn site. I think it didn't take a genius to break them. Although I think the way the hackers did it was creative. We'll give them style points."
June 07, 2005
Identity is an asset. Assets mean theft ... and Trade!
This is a good article. It describes what happens when you make a simple number the core of your security system. If you control the number, it becomes valuable. If it becomes valuable then it will either be stolen or traded. Valuable things are assets - which means trade or theft. (See also EC.)
In this case we we see the trade, and this sits nicely alongside the identity theft epidemic in the US: all there because the system made the number the control.
All security is based on assets. Perversely, if you make a number the core of your security system, then it becomes an asset, thus adding one more thing to protect, so you need a security system to secure your security system.
The lesson is simple. Do not make your security depend on a number. Identify what the asset is and protect that. Don't protect stuff that isn't relevent, elsewise you'll find that the costs of protecting might skyrocket, while your asset walks off unprotected.
Some Immigrants Are Offering Social Security Numbers for Rent
By EDUARDO PORTER
Published: June 7, 2005
TLALCHAPA, Mexico - Gerardo Luviano is looking for somebody to rent his Social Security number.
Mr. Luviano, 39, obtained legal residence in the United States almost 20 years ago. But these days, back in Mexico, teaching beekeeping at the local high school in this hot, dusty town in the southwestern part of the country, Mr. Luviano is not using his Social Security number. So he is looking for an illegal immigrant in the United States to use it for him - providing a little cash along the way.
"I've almost managed to contact somebody to lend my number to," Mr. Luviano said. "My brother in California has a friend who has crops and has people that need one."
Mr. Luviano's pending transaction is merely a blip in a shadowy yet vibrant underground market. Virtually undetected by American authorities, operating below the radar in immigrant communities from coast to coast, a secondary trade in identities has emerged straddling both sides of the Mexico-United States border.
"It is seen as a normal thing to do," said Luis Magana, an immigrant-rights activist assisting farm workers in the agriculture-rich San Joaquin Valley of California.
The number of people participating in the illegal deals is impossible to determine accurately. But it is clearly significant, flourishing despite efforts to combat identity fraud.
Hundreds of thousands of immigrants who cross the border from Mexico illegally each year need to procure a legal identity that will allow them to work in the United States. Many legal immigrants, whether living in the United States or back in Mexico, are happy to provide them: as they pad their earnings by letting illegal immigrants work under their name and number, they also enhance their own unemployment and pension benefits. And sometimes they charge for the favor.
Martin Mora, a former migrant to the United States who these days is a local politician preparing to run for a seat in the state legislature in next October's elections, said that in just one town in the Tlalchapa municipality, "of about 1,000 that fixed their papers in the United States there might be 50 that are here and lending their number."
Demand for American identities has blossomed in the cracks between the nation's increasingly unwelcoming immigration laws and businesses' unremitting demand for low-wage labor.
In 1986, when the Immigration Reform and Control Act started penalizing employers who knowingly hired illegal immigrants, most employers started requiring immigrants to provide the paperwork - including a Social Security number - to prove their eligibility to work.
The new law did not stop unauthorized immigrant work. An estimated 10 million illegal immigrants live in the United States today, up from some 4 million before the law went into effect. But it did create a thriving market for fake documents.
These days, most immigrants working unlawfully buy a document combo for $100 to $200 that includes a fake green card and fake Social Security card with a nine-digit number plucked out of thin air. "They'll make it for you right there at the flea market," said David Blanco, an illegal immigrant from Costa Rica who works as an auto mechanic in Stockton, Calif.
This process has one big drawback, however. Each year, Social Security receives millions of W-2 earning statements with names or numbers that do not match its records. Nine million poured in for 2002, many of them just simple mistakes. In response the agency sends hundreds of thousands of letters asking employers to correct the information. These letters can provoke the firing of the offending worker.
Working with a name linked to a number recognized by Social Security - even if it is just borrowed or leased - avoids these pitfalls. "It's the safest way," said Mario Avalos, a Stockton accountant who every year does tax returns for dozens of illegal immigrants. "If you are going to work in a company with strict requirements, you know they won't let you in without good papers."
While renting Social Security numbers makes up a small portion of the overall use of false papers, those with close ties to the immigrant communities say it is increasingly popular. "It used to be that people here offered their number for somebody to work it," said Mr. Mora in Tlalchapa. "Now people over there are asking people here if they can use their number."
Since legal American residents can lose their green cards if they stay outside the country too long, for those who have returned to Mexico it is useful to have somebody working under their identity north of the border.
"There are people who live in Mexico who take $4,000 or $5,000 in unemployment in the off season," said Jorge Eguiluz, a labor contractor working in the fields around Stockton, Calif. "They just lend the number during the season."
The deals also generate cash in other ways. Most identity lending happens within an extended family, or among immigrants from the same hometown. But it is still a hard-nosed transaction. Illegal immigrant workers usually earn so little they are owed an income tax refund at the end of the year. The illegal immigrant "working the number" will usually pay the real owner by sharing the tax
refund.
"Sometimes the one who is working doesn't mind giving all the refund, he just wants to work," said Fernando Rosales, who runs a shop preparing income taxes in the immigrant-rich enclave of Huntington Park, Calif. "But others don't, and sometimes they fight over it. We see that all the time. It's the talk of the place during income tax time."
Done skillfully, the underground transactions are virtually undetectable. They do not ring any bells at the Social Security Administration. Nor do they set off alarms at the Internal Revenue Service as long as the person who lends the number keeps track of the W-2's and files the proper income tax returns.
In a written response to questions, the audit office of Social Security's inspector general acknowledged that "as long as the name and S.S.N. on an incoming wage item (i.e., W-2) matches S.S.A.'s record" the agency will not detect any irregularity.
The response noted that the agency had no statistics on the use of Social Security numbers by illegal immigrants. It does not even know how many of the incorrect earnings reports it receives every year come from immigrants working unlawfully, though immigration experts estimate that most do.
Meanwhile, with the Homeland Security Department focused on terrorism threats, it has virtually stopped policing the workplace for run-of-the-mill work violations. Immigration and Customs Enforcement arrested only 450 illegal immigrants in the workplace in 2003, down from 14,000 in 1998.
"We have seen identity fraud," said John Torres, deputy assistant director for investigations. But "I haven't heard of the renting of identities."
Immigrants on both sides of the transactions are understandably reluctant to talk about their participation.
A 49-year-old illegal immigrant from Michoacan who earns $8.16 an hour at a waffle factory in Torrance, Calif., said that she had been using a Social Security number she borrowed from a friend in Mexico since she crossed illegally into the United States 15 years ago. "She hasn't come back in this time," the woman said.
There are risks involved in letting one's identity be used by someone else, though, as Mr. Luviano, the beekeeping instructor, learned through experience.
Mr. Luviano got his green card by a combination of luck and guile. He says he was on a short trip to visit his brother in California when the 1986 immigration law went into effect and the United States offered amnesty to millions of unauthorized workers.
Three million illegal immigrants, 2.3 million of them from Mexico, ultimately received residence papers. Mr. Luviano, who qualified when a farmer wrote a letter avowing he had worked for months in his fields, was one. Once he had his papers, though, he returned to Tlalchapa.
He has entered the United States several times since then, mostly to renew his green card. But in the early 1990's, concerned that long absences could put his green card at risk and spurred by the chance to make a little extra money, he lent his Social Security number to his brother's friend. "I kept almost all the income tax refund," Mr. Luviano said.
Mr. Luviano decided to pull the plug on the arrangement, however, when bills for purchases he had not made started arriving in his name at his brother's address. "You lend your number in good faith and you can get yourself in trouble," he said.
But Mr. Luviano is itching to do it again anyway. He knows that Social Security could provide retirement income down the line. And there's always the tax refund.
"I haven't profited as much as I could from those documents," he said ruefully.
Copyright 2005 The New York Times Company
http://www.nytimes.com/2005/06/07/business/07immigrant.html
June 06, 2005
Save Thyself - Russia's WebMoney Payment System (translated)
by Nikita Sechenko
Translated from the Russian by Daniel Nagy
There are two approaches to one's personal safety. The first one is difficult: never leave the iron plugged in, never smoke in bed, do not place the gas stove near the window. The second approach is a lot easier: you don't follow any rules and hope that there will be no fire. Same with WebMoney. There's a difficult way: for example, read "Security Encyclopedia" and follow all the rules in there. This, of course, requires time and effort, which is unacceptable for many. The other method -- not reading anything, ignoring all the warnings in the Keeper (WM's wallet application), indiscriminately opening all your email, launching all sorts of suspicious programs, not using antivirus software and firewalls. This article is dedicated to those who have chosen this easy way. Since there is a substantial risk that the money from your pruses will be stolen, it's useful to know how to get them back. That's what we'll talk about below.
So, the bad guys have "planted" a virus on your computer (you like opening email attachments, don't you?), found the *.kwm key-files on your harddrive (you don't keep them on removable media, do you?), caught the passphrase as you typed it, and sent all of that to their mailbox (your *.kwm files weighed a mere 50K, didn't they?). Then he connects to your WMID using his computer (you have, of course, turned pre-activation by email and IP blocking off) and stole all the title certificates in there. What can you do?
First, don't panic. You should know that the staff of WebMoney, in particular the arbitration service and tech support, are responsive to pleas of help in case of stolen keys and assets from purses. Be assured, they will do everything they can. Secondly, the solution of the problem should not be postponed. You should act as fast as possible. Every minute counts. Your main task is to get ahead of the bad guys. Taking into account their head start, it will be difficult, but still possible. Finally, the third rule is not giving up. From my experience as an arbiter, I can tell that returning your assets is often possible even in situations that look hopeless at first.
And now for the concrete measures. Your actions will depend on several factors. First and foremost whether or not you have lost access to your identifier.
If you do have access to your WMID and you can check your transaction history and find out the WMID of the offender, the most effective way of proceeding is filing a complaint under "unauthorized payment" against that WMID at the website of the arbitration service (http://arbitrage.webmoney.ru). At this point you will need to pay the arbitration fee immediately, as doing so automatically block payments from the WMID with a certification level lower than "initial" (note of the translator: basically, it means blocking anonymous accounts). This way, the assets on the defendant's account will stay there until the arbitration comission rules on the case. WMIDs with an initial level certificate or a registrator level certificate can be blocked only with a sanction of the arbitration comission, but holders of such certificates are not in the theft business, as a rule.
In order to file an "unauthorized payment" complaint, a pseudonym certificate suffices (note of the translator: these are given to whoever asks without any verification). The arbitration fee is 10% of the contested payment. First, it can make sense to file a minimal complaint, as low as 1 WMZ and pay a 0.1 WMZ fee. Filing the complaint will take only a few minutes.
However, as the funds could have been transfered a number of times in order to confuse the investigation, after filing the complaint, you can immediately contact the arbitration service's administrator (WMID 937717494180, arbitrage@webmoney.ru) and ask him to trace the chain of payments, should one exist. The administrator (after careful consideration), may block all the accounts along the chain and will send you a report on how much money has been "caught" where. You will need this information for further arbitration proceedings. Keep in mind, however, that arbitration is a service for resolving conflicts, not a 911 service. They work from monday to friday between 10am and 6pm.
If the offender has left, for some reason, funds on your WMID or you have other WMIDs for the security of which you cannot vouch after the attack, contact the tech support (+7 095 727-43-33, support@wmtransfer.com, WMID 941977853154) and ask them to temporarily block outgoing payments from your accounts as well.
As we have said, filing a complaint is the best solution in this situation. But what can be done if everything has been stolen up to the last penny, and quickly finding a few WMZ to pay the arbitration fee is not an option? In this case, you should email and telephone tech suport and arbitration asking them to block the WMID of the offender, after which you should, nevertheless, file a complaint initiating arbitration proceedings as quickly as you can. Keep in mind that tech support can only block WMIDs, but they have no means of tracing the payment chain along which your money has been siphoned off. The arbitration sercive, on the other hand, can block accounts, trace payments and check balances.
But, as you understand, thieves typically do not transfer funds to their purses or if they do, they don't leave them there for a longer period of time in order to buy ebook classics, should they get bored, but try to hide their traces and get rid of evidence as quickly as they can. In order to do so, they exchange stolen WM for assets in other payment systems, typically e-gold. Then exchange them back to WM and repeat a number of times. In this case, the problem becomes significantly more complex. You should contact the administration of the automated exchange through which the exchange has been transacted and find out the fate of your assets (filing a complaint against the exchange makes no sense, see below). Later the administrator of the arbitration service will send a query to the other payment system, but that seldom helps. E-gold, for example, having received a request from WebMoney, blocks offending accounts, but gives transaction information out only at the requests of courts and law enforcement.
In the worst case, the offender uses an "offline" exchange, cashing the stolen assets. In this case, arbitration cannot help: the exchange did their job and had no means of knowing about the origin of the funds. Hence, the accounts of the exchange won't be blocked and they are under no obligation whatsoever to return your funds. This is when you should turn to law enforcement and hope that the exchange has checked and recorded the passport data of their clients as required by the rules of our system.
If, however, you have lost access to your WMID (the attacker has changed the password or the key file), then you should immediately contact tech support and ask them to block your WMID, just in case there is some money left there. In addition, you should contact the administrator of the arbitration service and report the loss of access to your WMID. It is desirable to correspond using the same email address that is indicated in your certificate and in the Keeper's personal data section. In your email, you should give information as comprehensive as possible in order to establish that you are, indeed, the legitimate owner of the WMID in question. Namely, your WMID, the purses' numbers, the last transactions complete with dates and so on. The administrator, in turn, will tell you the current balance of your purses, where funds were transfered and whether they were successfully blocked. The rest of the procedure is analogous to the one described in the previous section.
That's all. I hope, you will make the right conclusions and choose for yourself that difficult way of protecting yourself from calamities. Remember: lost nerve cells cannot be recovered.
* * *
Note from the translator: This is a translation for which I have not received a permission from the author, completed for purely educational purposes. I have done my best to provide an accurate translation, but take no responsibility for its correctness.
June 02, 2005
A shortcut for bootstrapping trust
From the light-hearted threats department, Mark points to an article on how to bypass trusting defences.
Scientists develop revolutionary 'trust spray'
MICHAEL BLACKLEY
A REVOLUTIONARY nasal spray could have the power to make a person more trusting, scientists have found.
Experiments show that after a few squirts of a spray containing the hormone oxytocin, humans were significantly more trusting. It has even been suggested that the spray could be used as a therapy for trust-diminishing conditions, such as autism or some social phobias.
The research, carried out by a team of American and Swiss scientists and published in today’s issue of Nature, showed that after using the spray, volunteers became more willing to risk losing money to a stranger.
One of the scientists who worked on the project, Dr Michael Kosfeld, of the University of Zurich, said those who had sniffed oxytocin gave away their money much more easily. He also said animal studies had proved that oxytocin takes away the unwillingness to approach strangers. "It helps animals approach one another - which is a parallel with trust in our game," he said. "In companion with psychotherapy it could have a positive effect."
Oxytocin has traditionally been seen as a "love hormone", and is released during orgasm. It has also been proved to be released when cuddling or touching takes place, and women release it when in labour and during breastfeeding.
The idea that it could be released when people express feelings of trust was first raised in 2003, but this research is the first attempt to show that increasing the amount of the hormone present in the body could directly influence the extent that one person trusts another.
Antonio Damasio, a neurologist at the University of Iowa, who reviewed the experiments for Nature, believes the findings could be significant scientifically. He said:
"Some may worry about the prospect that political operators will generously spray the crowd with oxytocin at rallies of their candidates.
"The scenario may be rather too close to reality for comfort, but those with such fears should note that current marketing techniques - for political and other products - may well exert their effects through the natural release of molecules such as oxytocin in response to well-crafted stimuli."
However, the idea that it could be used to help autism was met with scepticism by the National Autistic Society. A spokeswoman said: "The outcome of any approach will depend on the needs of the individual, which vary greatly, and the appropriate application of the intervention."
Addendum Zooko recommends Neuromarketing: Peeking Inside the Black Box
June 01, 2005
Software Licensing and the Know-how to Issue
Software charging for big ticket sellers is getting more complex again, as dual cores from AMD and Intel start to invade the small end. Oracle, which made billions charging on the muscle power of CPUs, will have to do something, and we've by now all seen IBM's adverts on TV suggesting "on demand" with its concommitant charging suggestion: You demand, we charge.
I've done a lot of thinking over the years about how to licence big ticket items like issuance software. In practice it is very difficult, as the only revenue model that makes sense for the supplier is for large up front licence fees to recover large up front capital and sunk costs. But for the demander (issuer and user of the software) the only model that makes sense is to pay later, when the revenues start flowing...
Issuance software has all the hallmarks of an inefficient market and I don't think there has been successful case of issuance licencing yet, as those two "sensible" options do not leave any room for agreement. This may be rational but it's very frustrating. Time and again, we see the situation of people wanting to get into the issuance market who think they can produce the software themselves for a cheaper price. And they always end up spending more and getting a lesser quality product.
In practice what we (Systemics) have been doing is this: running the software ourselves as "operator", and charging operating costs, with some future licencing or transaction flow revenues. Yet, the deal for future revenues is always based on a promise and a prayer, which is already asymmetrical given that most startups do no more than start up. (And it isn't just me bemoaning here - if you look back through history there are literally hundreds of companies that tried to build value issuance and sell it.)
Which leads to the freeware model. In the freeware world, big ticket items are given away and money is made on the consulting. This has worked relatively well in some areas, but doesn't work so well in issuance. I'm unclear of the full reason why open source software doesn't work in issuance, but I think it is mostly the complexity, the sort of complexity I wrote about in FC7. It's not that the software can't capture that complexity but that the financial cryptography business often finds itself so squeezed for management complexity that partnering with a strong software supplier are beyond capabilities.
What will potentially help is p2p issuance. That is, "everyone an issuer." We've always known this model existed even as far back as 1995, but never really considered it seriously because too many questions arose. Little things like how we teach grandma to sign a digital contract. We've now done enough experiments in-house to confirm that the corporate internal issue and the individual issue are workable, sustainable economic models but we have to get other companies and individuals to do that and for the most part they still don't do anything they don't understand.
I'm guessing the way forward here is to turn client software into issuance software. This brings up a whole host of issues in financial cryptographic architecture. For a start it can never seriously scale simply because people do silly things like turn off their laptops at night.
But, more and more, the barriers to issuance and financial cryptography in general I believe are spreading the knowledge, not the tools and tech. Every year our tools and tech get better; but every year our real barriers seem the same - how to get users and customers to make their first tentative issue of a currency of value. Oh, and how to make money so as to keep us all alive, which was the starting point on this long rant of liberal licence.
A couple of footnotes: In a similar thread over at PGP Inc, Will Price reveals how they've managed to get out of the legacy freeware version trap:
"When the 30 Day Trial version of PGP Desktop Home expires, it reverts to a set of functionality comparable to what used to be known as Freeware, and said functionality remains available indefinitely -- under the same license conditions as Freeware used to be under."
Nice one. That works for client software, not for server software.
Here's a further article on how the big companies are also working out how big ticket software isn't the way to go:
Two Hot Whistleblowers
The concept of whistleblowing informs our deepest designs. We cannot secure everything, so we go to the next best thing: we document everything. Extraordinarily, we can put together extremely strong systems that use the humble message digest to create chains of signatures and time entanglement, not because this is perfect, but because we know that if someone is looking, they can find.
As our deepest difficulties lie not in external security but in protecting against the insider, audit trails and wide dissemination of information is one of our hottest tools. For the financial cryptographer, our hope is to leave a trail so well buried and indicative that any investigator is supported with some real evidence and doesn't need to rely on anything but the evidence.
That's an ideal, thought, and it doesn't normally happen quite so well. Sometimes spectacularly so. Here are two whistleblowing stories from the US that provide colourful background to our efforts to secure systems and processes.
In what has turned into a festival of hand-wringing moralising, Deep Throat has revealed himself to be Mark Felt, the Deputy Director of the FBI during the Watergate Affair....
Deep Throat was the fabled secret source who prodded the journalists and provided the crucial inside tips to keep the story alive until it swept over and destroyed the corrupt and arrogant administration of Richard Nixon. (See google.news for a squillion articles.)
How could he, write many of Washington's finest. The act of treachery, the traitor!
How could he not? I ask. When your administration is corrupt, what do you do? What is the press for? What is that much exported model of freedom there for if not to dig out the dirt and keep politicians honest? And is Mark Felt an employee of a corrupt administration first and always? Or is he human being, a member of a society? (Americans would ask if he was an American, but that always confuses me.)
I think it is pretty clear that all our institutions, and also our models of financial cryptography support the concept and presence of whistle blowers. It may be hell when he's not on your team, but that's a different issue.
And in story #2, the Arthur Andersen conviction was overturned in the US Supreme Court by a unanimous decision. Arthur Andersen went down with Enron, which was done in by a public whistleblower when other, inside whistleblowers failed to do it.
What can done say about the Supreme Court's ruling - one of the most reputable names in accounting was wiped out by the original decision and now we are told it was wrong?
The obvious - too late for the 28,000 workers - has been written about elsewhere, but I can't help thinking such is simply the wrong way to look at the judicial process. Did it do the right thing or the wrong thing? I can't see the wrong thing having been done here. The prosecutor had a good case, and won the conviction. But he overstepped the mark and now it has been overturned. What else is there to say?
That's the way the process works, it's called checks and balances. If those that think this dreadful mistake means we should scrap the prosecutorial process, or "reel in the prosecution" then they need to think up a process to replace it. Regardless of the 27,000 or however many innocent workers at Arthur Andersen, that company was selling its soul.
So we need a process to stop that, and the current process just happens to do that. Sometimes. If anything, I think we need another big N accounting firm to go down for just such another scandal, as we know they were *all* doing it (as I've oft reported, I know all but one were doing it, and I just never heard what the other one was doing...).
Literally, yes, if the system needs to work that way, we need another 27,000 innocents to be turned onto the streets in order to get the message to the 1000 or so bad apples who will lie and cheat and basically sell their company's reputation for 30 pieces of silver. Remember, there are thousands of shareholders and the millions of california tax payers who also lost big time, and nobody's bemoaning their fate much. And nobody owns a job, whether they work for a corrupt company or an honest one.
But I'm all ears to a better system. Many older and legacy systems think they can protect themselves with an audit, and for the sake of all those who think that, well, their only real defence is an occasional spectacular bust of those selling unreliable audits. Or, to get serious about auditing and learn about financial cryptography :-)