November 19, 2013
Bitcoin and how to integrate it into society
 Notwithstanding all the bad news I reported yesterday, Bitcoin moves from strength to strength. It hit $1000 in turbulent trading today -- more in China -- and recently surpassed an exaFLOPS in capacity. It's important to analyse both sides of the coin, so to speak, unless one has resigned ones intellectual fate to being an unremitting fan or unrepentant opponent.
Notwithstanding all the bad news I reported yesterday, Bitcoin moves from strength to strength. It hit $1000 in turbulent trading today -- more in China -- and recently surpassed an exaFLOPS in capacity. It's important to analyse both sides of the coin, so to speak, unless one has resigned ones intellectual fate to being an unremitting fan or unrepentant opponent.
(This essay is written to help me get my thoughts in order for Wednesday's Afrikoin conference, where I'm speaking at a panel on Bitcoin and cryptocurrencies in the African context.)
As an economy, the major problem with Bitcoin is trust. The design of a new money system always lives or dies on whether the end-user can trust the results of a transaction. Technically, we can see that Bitcoin does a single transfer of value from Alice to Bob with some sort of aplomb, but this is not enough to gain the trust of the end-user.
A transaction is generally bi-directional. In this case, Bitcoin moves from Alice to Bob, but something also comes back. And it is in the something coming back that Bitcoin struggles.
Let's talk about classical trust mechanisms so we can get a feel for this. When you walk down the street in a strange town, you know you can walk into a shop and buy things -- engage in a bidirectional trade with some currency. This works because the shop is going to be there tomorrow and the day afterwards -- if the shop rips off its customers, the customers will eventually gang up and destroy the shop. Even if you haven't visited the town before, location is a trust signal, permanence is a trust reinforcer, busy custom is a sign of others' trust.
Likewise, when you deal with greenbacks, you know that at the end of the day, there are 300 million Americans that will take them. And, those 300 million know that at the end of the day, their government will take them back in taxes.
There are many other trust mechanisms; but let's turn back to Bitcoin. What makes trade in it trustworthy? Not a lot. There is no statement of value; this is the same weakness that makes PGP's Web of Trust no more than a curiosity. There is no big brother standing behind it, it doesn't look like a national currency. There is no sense of permanence like a brick&mortar shop, and there have already occurred a hundred or so copycat competitors, many of whom have already folded. It is unlike gold with its ancient history of cross-cultural acceptance. There is no sense of the other person you're dealing with, and indeed there is a designed absence of sense -- the unit is supposed to be psuedonymous, which means you're dealing with a key not a person.
Keys don't make deals, people do.
For trust in Bitcoin, there is only supply and demand, which reduces the unit to the trials and tribulations of the market, with no "underlying" or strength. We have a name for that: speculation, as opposed to investment. Bubbles and Ponzies are other words that are bandied around, with more or less stickiness. Either way, this lack of foundation generally means that Bitcoin is not good for long term trade; you can't price ordinary goods in Bitcoin for example, because the price keeps going up, and down.
So, as a rule of the Bitcoin economy, in participating in bidirectional trades, one has to build ones own trust system in.
As a rather good example, this is exactly what the Silk Road did! Bonds were required of newcomers, and funds were held in escrow until delivery of goods were effected. Silk Road worked, trust was maintain, and deals were done.
At least in its short lifespan, before the trust was irrevocably undermined by the attention of the Feds. It's important to understand that whatever you think about the political or legal questions surrounding the capture of the owner and the closing of the market, its demise is synonymous with, or equivalent to, the end of its offer of trust -- its ability to ensure a safe bidirectional trade.
 Fans would say that Bitcoin carefully separates out the trust equation from the payments equation, allowing us to build it later in markets like the Silk Road; opponents would say it is fundamentally untrustworthy, I would prefer to say that trust in Bitcoin is unfinished business.
Fans would say that Bitcoin carefully separates out the trust equation from the payments equation, allowing us to build it later in markets like the Silk Road; opponents would say it is fundamentally untrustworthy, I would prefer to say that trust in Bitcoin is unfinished business.
So how do we finish that which is missing? How do we add the trust back into Bitcoin, or in more accepting terms, how do we augment it with the missing pieces?
One normal trust mechanism that businesses do is an old and boring one: collect the details of who the person is, commonly by looking at their passports/national Ids. There are many pros & cons to this method. For many sectors and trades, it is a waste of money, and an invitation to deception, whereas for others it is a leveraging of the state's identity-trust model, for near-free. And, as we've seen, this method leads to the death of privacy as thousands of marketing businesses and dozens of intelligence agencies aggregate your personal life, starting with your ID.
Bad as identity is, it's worth mentioning because for every finance business that needs to make its peace with a nearby government, this is likely what has to be done, whether they like it or not. It is a trust mechanism, or enough of one for many milder purposes, and it is going to be imposed over Bitcoin to a large extent if & when governments figure out what to do.
Pros and cons! How would we then mitigate the many cons to mass identity collection? What about localised circles of trust -- instead of a global facebook for money, perhaps a google-circles for shared wealth? We could share the information locally in small enough circles such that the trust can be vectored to where it is needed, but there is no necessary or single weakness that can be attacked, that inevitably brings the system down.
This is indeed what I'm doing in my business right now. Building a pure transaction system like Bitcoin (which I called Ricardo) was what I did a long time ago; for many years now I've been building trust systems, which is proving to be far more challenging because people are directly involved in ways that they aren't with mere transactions.
 Which leads me to my final point: *Trust is people-centric*. Payment systems aren't, they are transaction-centric. Bitcoin takes this separation to new levels by reducing even the Issuer to a non-person called a block-chain, in a sense it is pushing further and further
Which leads me to my final point: *Trust is people-centric*. Payment systems aren't, they are transaction-centric. Bitcoin takes this separation to new levels by reducing even the Issuer to a non-person called a block-chain, in a sense it is pushing further and further
In contrast, the same process I took in building this trust system, which is now in place, applies both to my Ricardo and to Satoshi's Bitcoin. If you meld a payment system with a trust system, what you get is a working economy. But the challenge is not the payment system, it's definitely the trust system.
Adding Bitcoin to our system then will be fairly easy -- and *worthy of trust*. Which might propose yet another benchmark to Bitcoin. When you hear about us offering Bitcoin, that might signal that there is sufficient demand *in mainstream marketplace* for it. We can do it easily because we have the trust. Watch this space?
November 10, 2013
The NSA will shape the worldwide commercial cryptography market to make it more tractable to...
In the long running saga of the Snowden revelations, another fact is confirmed by ashkan soltani. It's the last point on this slide showing some nice redaction minimisation.
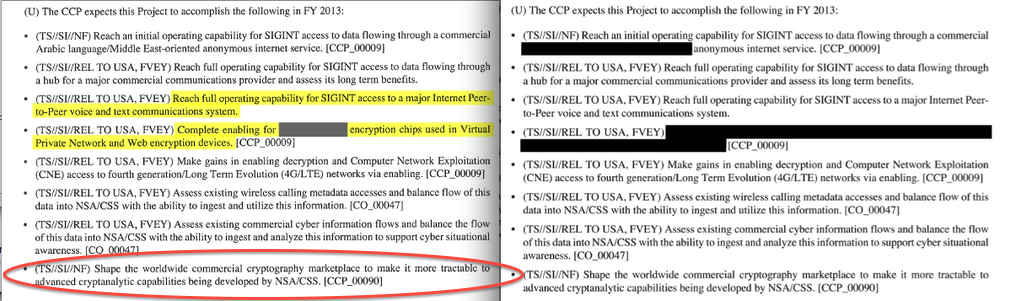
In words:
(U) The CCP expects this Project to accomplish the following in FY 2013:
Confirmed: the NSA manipulates the commercial providers of cryptography to make it easier to crack their product. When I said, avoid American-influenced cryptography, I wasn't joking: the Consolidated Cryptologic Program (CCP) is consolidating access to your crypto.
Addition: John Young forwarded me the original documents (Guardian and NYT) and their blanket introduction makes it entirely clear:
(TS//SI//NF) The SIGINT Enabling Project actively engages the US and foreign IT industries to covertly influence and/or overtly leverage their commercial products' designs. These design changes make the systems in question exploitable through SIGINT collection (e.g., Endpoint, MidPoint, etc.) with foreknowledge of the modification. ....
 Note also that the classification for the goal above differs in that it is NF -- No Foreigners -- whereas most of the other goals listed are REL TO USA, FVEY which means the goals can be shared with the Five Eyes Intelligence Community (USA, UK, Canada, Australia, New Zealand).
Note also that the classification for the goal above differs in that it is NF -- No Foreigners -- whereas most of the other goals listed are REL TO USA, FVEY which means the goals can be shared with the Five Eyes Intelligence Community (USA, UK, Canada, Australia, New Zealand).
The more secret it is, the more clearly important is this goal. The only other goal with this level of secrecy was the one suggesting an actual target of sensitivity -- fair enough. More confirmation:
(U) Base resources in this project are used to:
- (TS//SI//REL TO USA, FVEY) Insert vulnerabilities into commercial encryption systems, IT systems, networks and endpoint communications devices used by targets.
- ...
and in goals 4, 5:
- (TS//SI//REL TO USA, FVEY) Complete enabling for [XXXXXX] encryption chips used in Virtual Private Network and Web encryption devices. [CCP_00009].
- (TS//SI//REL TO USA, FVEY) Make gains in enabling decryption and Computer Network Exploitation (CNE) access to fourth generation/Long Term Evolution (4GL/LTE) networks via enabling. [CCP_00009]
Obviously, we're interested in the [XXXXXX] above. But the big picture is complete: the NSA wants backdoor access to every chip used for encryption in VPNs, wireless routers and the cell network.
This is no small thing. There should be no doubt now that the NSA actively looks to seek backdoors in any interesting cryptographic tool. Therefore, the NSA is numbered amongst the threats, and so are your cryptographic providers, if they are within reach of the NSA.
Granted that other countries might behave the same way. But the NSA has the resources, the will, the market domination (consider Microsoft's CAPI, Java's Cryptography Engine, Cisco & Juniper on routing, FIPS effect on SSL, etc) and now the track record to make this a more serious threat.
November 01, 2013
NSA v. the geeks v. google -- a picture is worth a thousand cribs
Dave Cohen says: "I wonder if I have what it takes to make presentations at the NSA."
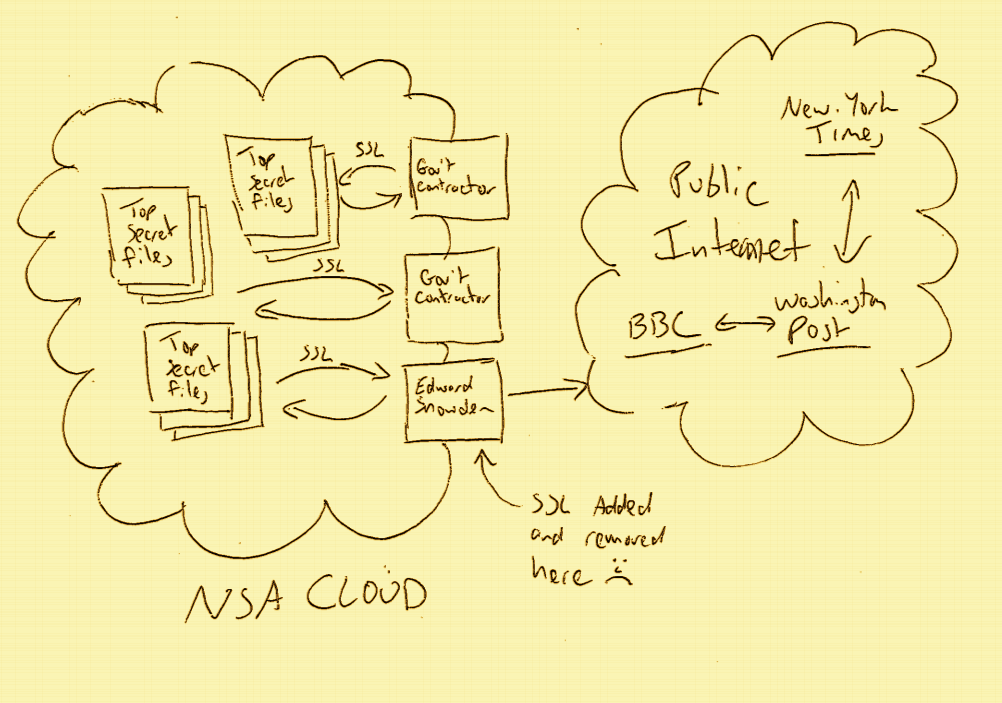
H/t to Jeroen. So I wonder if the Second World Cryptowars are really on?
Our MissionTo bring the world our unique end-to-end encrypted protocol and architecture that is the 'next-generation' of private and secure email. As founding partners of The Dark Mail Alliance, both Silent Circle and Lavabit will work to bring other members into the alliance, assist them in implementing the new protocol and jointly work to proliferate the worlds first end-to-end encrypted 'Email 3.0' throughout the world's email providers. Our goal is to open source the protocol and architecture and help others implement this new technology to address privacy concerns against surveillance and back door threats of any kind.
Could be. In the context of the new google sniffing revelations, it may now be clearer how the NSA is accessing all of the data of all of the majors. What do we think about the NSA? Some aren't happy, like Kenton Varda:
If the NSA is indeed tapping communications from Google's inter-datacenter links then they are almost certainly using the open source protobuf release (i.e. my code) to help interpret the data (since it's almost all in protobuf format). Fuck you, NSA.
What about google? Some outrage from the same source:
I had to admit I was shocked by one thing: I'm amazed Google is transmitting unencrypted data between datacenters.
is met with Varda's comment:
We're (I think) talking about Google-owned fiber between Google-owned endpoints, not shared with anyone, and definitely not the public internet. Physically tapping fiber without being detected is pretty difficult and a well-funded state-sponsored entity is probably the only one that could do it.
Ah. So google did some risk analysis and thought this was one they can pass on. Google's bad. A bit of research shows BlackHat in 2003:
Commercially available taps are readily available that produce an insertion loss of 3 dB which cost less than $1000! Taps currently in use by state-sponsored military and intelligence organizations have insertion losses as low as 0.5 dB!
 That document indicates 2001 published accounts of NSA tapping fibre, and I found somewhere a hint that it was first publically revealed in 1999. I'm pretty sure we knew about the USS Jimmy Carter back then, although my memory fades...
That document indicates 2001 published accounts of NSA tapping fibre, and I found somewhere a hint that it was first publically revealed in 1999. I'm pretty sure we knew about the USS Jimmy Carter back then, although my memory fades...
So maybe Google thought it hard to tap fibre, but actually we've known for over a decade that is not so. Google's bad, they are indeed negligent. Jeroen van Gelderen says:
Correct me if I'm wrong but you promise that "[w]e restrict access to personal information to Google employees, contractors and agents who need to know that information in order to process it for us, and who are subject to strict contractual confidentiality obligations and may be disciplined or terminated if they fail to meet these obligations.
Indeed, as a matter of degree, I would say google are grossly negligent: the care that they show for physical security at their data centers, and all the care that they purport in other security matters, was clearly not shown once the fiber left their house.
Meanwhile, given the nature of the NSA's operations, some might ask (as Jeroen does):
Now that you have been caught being utterly negligent in protecting customer data, to the point of blatantly violating your own privacy policies, can you please tell us which of your senior security people were responsible for downplaying the risk of your thousands of miles of unsecured, easily accessible fibers being tapped? Have they been fired yet?
Chances of that one being answered are pretty slim. I can imagine Facebook being pretty relaxed about this. I can sort of see Apple dropping the ball on this. I'm not going to spare any time with Microsoft, who've been on the contract teet since time immemorial.
But google? That had security street cred? Time to call a spade a spade: if google are not analysing and revealing how they came to miss these known and easy threats, then how do we know they aren't conspirators?