August 30, 2012
Four Planks to support the next evolution in secure browsing
There are now all the preliminary planks in place for the next step in evolution in the business of browser security.
A federal judge has rejected BancorpSouth's plan to use contractual agreements with customers as a shield against liability claims stemming from an online heist of some $440,000 that was illegally wire-transferred from the account of one of the bank's commercial customers in March 2010.
The first plank was an aggressive environment, this turned up in 2011 (by my reckoning).
The second plank was the decision by participants to avoid liability issues and to document that they had avoided liability issues.
The third plank was recognition by experts (as determined by courts) that online banking was insecure. Although I've pointed at this advice for years ("use another browser") courts don't recognise bloggists as experts. However, e.g., Lynn points in comments to USA federal regulatory advice that a single-purpose dedicated PC be used. That's recognised!
The fourth plank was sufficient clarity on how the courts would deal with the question, by means of actual rulings. This was never in doubt, because the courts always go that way in the long run, but while there were no rulings, people could "reasonably" argue that it was cool.
In his four-page ruling, Magistrate Judge John Maughmer says he based his decision about contractual obligations between banks and commercial customers on his interpretation of the UCC. And he acknowledges the waters are murky. "The court, having read the briefing of the parties, finds this to be a very close call," he says.Nevertheless, Maughmer finds that the UCC does not provide blanket protections for banking institutions, in spite of indemnity noted in the contract.
"As enacted in Missouri and other jurisdictions, the Funds Transfers Act (UCC 4A) was not intended to preempt or displace all causes of action between a bank and its customers engaging in money transfers," Maughmer writes. "The uniformity and certainty sought by the statute for these transactions could not possibly exist if parties could opt to sue by way of pre-Code remedies where the statute has specifically defined the duties, rights and liabilities of the parties."
Other Cases. Inherent in the magistrate judge's findings is the question "What is reasonable?" regardless of whether that reasonableness comes from the bank or the commercial customer. What's contained within the contract and what is deemed "commercially reasonable" often are at odds, Navetta says.
The point being that the courts will find fault with an unreasonable contract. Those rulings we are now seeing, as quoted. As somewhat less than coincidentally, close analogues will inform the courts as to how to deal with liability in other browsing security issues. E.g., PKI certificates.
Smarter participants have seen the writing on the wall. VeriSign sold their CA to Symantec, correctly IMHO judging that the business was going to face increasing risks, while not generating the synergies across to other areas of its business to take on those risks. This confirms the truism of the industry - Others acquired market share, VeriSign understood the market.
All that remains is a headline high-value target to serve as the channel of forces. All of the trouble in the marketplace for certificates - a.k.a. secure browsing - has so far been against non-monetary uses of certificates. Paradoxically, the saving grace for the business may be that it never really got used for such high commercial value things as to be relied upon.
August 26, 2012
Use another browser - Kaspersky follows suit
 You saw it here first :) Kaspersky has dipped into the payments market with a thing called Safe Money:
You saw it here first :) Kaspersky has dipped into the payments market with a thing called Safe Money:
A new offering found in Kaspersky Internet Security is Safe Money, Kaspersky Lab's unique technology designed to protect the user's money when shopping and banking online. To keep your cash safe, Kaspersky Internet Security's Safe Money will:
...
- Automatically activate when visiting most common payment services (PayPal, etc.), banking websites, and you can easily add your own bank or shopping websites to the list.
- *Isolate your payment operations in a special web browser to ensure your transactions aren't monitored*.
- Verify the authenticity of the banking or payment website itself, to ensure the site isn't compromised by malware, or a fake website designed to look authentic.
- Evaluate the security status of your computer, and warn about any existing threats that should be addressed prior to making payments.
- Provide an onscreen Virtual Keyboard when entering your credit card or payment information so you can enter your information with mouse-clicks. This will activate a special program to prevent malware from logging any keystrokes on your physical keyboard.
 The #2 tip is the same as the #2 one that's been on this website for years - use one browser for common stuff and another for your online payments. This simple trick builds a good solid firewall between your money and the crooks' hands. What's more, it's easy enough to teach grandma and grandson.
The #2 tip is the same as the #2 one that's been on this website for years - use one browser for common stuff and another for your online payments. This simple trick builds a good solid firewall between your money and the crooks' hands. What's more, it's easy enough to teach grandma and grandson.
(For those lost for clue, download Chrome and Firefox. I advise using Safari for banking, Firefox for routine stuff and Chrome for google stuff. Whatever you do, keep that banking browser closed and locked down, until it is time to bring it up, switch to privacy mode, and type in the URL by hand.)
Aside from Kaspersky's thumbs-up for the #2, what else can we divine? If Kaspersky, one of the more respected anti-virus providers, has decided to dip its toe into payments protection, this might be a signal that phishing and malware is not reducing. Or, at least, the perception has not diminished.
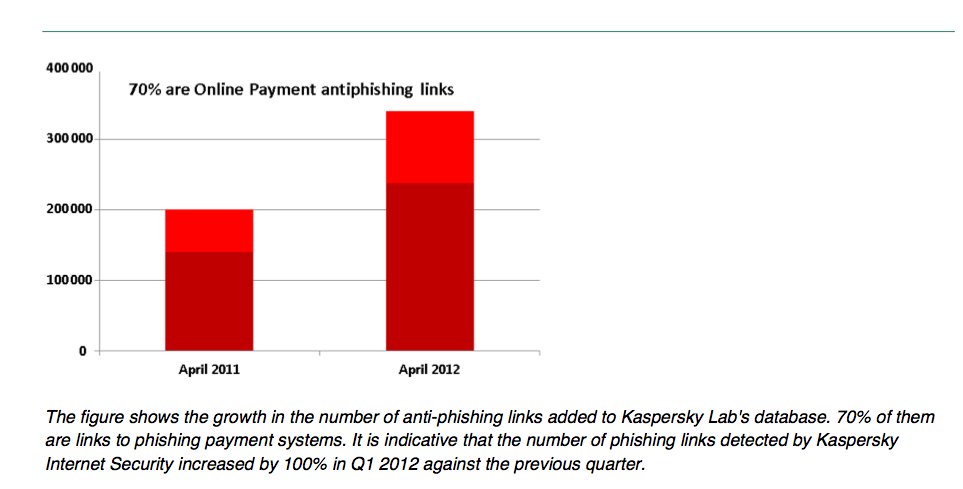
Out there in user-land, people don't really trust browsers to do their security, and since GFC-1 they don't really trust banks either. (They've never ever trusted CAs.) This doesn't mean they can voice, explain or argue their mistrust, but it does mean that they feel the need - it is this perception that Kapersky hopes to sell into.
Chances are, it's a good pick, if only because we're all going to die before any of these providers deals with their cognitive dissonance on trust. Good luck Kaspersky, and hopefully you won't succumb to it either.