December 21, 2014
OneRNG -- open source design for your random numbers
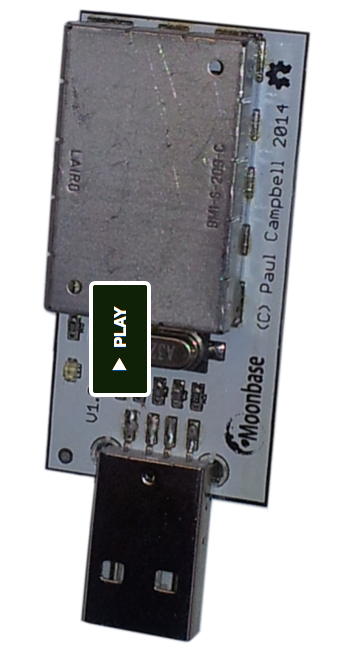 Paul of Moonbase has put a plea onto kickstarter to fund a run of open RNGs. As we all know, having good random numbers is one of those devilishly tricky open problems in crypto. I'd encourage one and all to click and contribute.
Paul of Moonbase has put a plea onto kickstarter to fund a run of open RNGs. As we all know, having good random numbers is one of those devilishly tricky open problems in crypto. I'd encourage one and all to click and contribute.
For what it's worth, in my opinion, the issue of random numbers will remain devilish & perplexing until we seed hundreds of open designs across the universe and every hardware toy worth its salt also comes with its own open RNG, if only for the sheer embarrassment of not having done so before.
OneRNG is therefore massively welcome:
About this projectAfter Edward Snowden's recent revelations about how compromised our internet security has become some people have worried about whether the hardware we're using is compromised - is it? We honestly don't know, but like a lot of people we're worried about our privacy and security.
What we do know is that the NSA has corrupted some of the random number generators in the OpenSSL software we all use to access the internet, and has paid some large crypto vendors millions of dollars to make their software less secure. Some people say that they also intercept hardware during shipping to install spyware.
We believe it's time we took back ownership of the hardware we use day to day. This project is one small attempt to do that - OneRNG is an entropy generator, it makes long strings of random bits from two independent noise sources that can be used to seed your operating system's random number generator. This information is then used to create the secret keys you use when you access web sites, or use cryptography systems like SSH and PGP.
Openness is important, we're open sourcing our hardware design and our firmware, our board is even designed with a removable RF noise shield (a 'tin foil hat') so that you can check to make sure that the circuits that are inside are exactly the same as the circuits we build and sell. In order to make sure that our boards cannot be compromised during shipping we make sure that the internal firmware load is signed and cannot be spoofed.
OneRNG has already blasted through its ask of $10k. It's definitely still worth contributing more because it ensures a bigger run and helps much more attention on this project. As well, we signal to the world:
*we need good random numbers*
and we'll fight aka contribute to get them.
Posted by iang at December 21, 2014 12:59 PMAhem.
"We make sure that the internal firmware load is signed and cannot be spoofed."
And:
"What we do know is that the NSA has [...] paid some large crypto vendors millions of dollars to make their software less secure".
...including RSA Inc (both a big crypto vendor and a public-key algorithm bearing the same name).
So, as public-key crypto can't be trusted, hardware and software claiming to be certified by untrustworthy crypto is certainly suspect.
As OpenSSL has shown, being "open-source" is certainly not a proof of competence, honesty or trustworthiness.
By the way, Dual_EC_DRBG, the "suspected" PRNG is still in use by the "trusted" vendors[1]... 9 years after a 2005 patent[2] demonstrated how to use it to compromize people's encryption keys.
So much for the trust.
[1] http://csrc.nist.gov/groups/STM/cavp/documents/drbg/drbgval.html
[2]
https://projectbullrun.org/dual-ec/patent.html
Hi Claudius,
If you don't wish to trust the firmware image that comes on the device, you are free to provide your own firmware instead, or to recompile the original from source. This requires some effort (and a second hardware device to reprogram the unit) but should help to mitigate the position of not trusting the way the firmware is signed.
This is pretty much the whole point of Open Hardware/Open Software, which was a core fundamental of the design of this unit. If you don't like what has been provided, you have the information needed to change it.
OneRNG's security stance isn't about trust.
-jim, OneRNG team
Posted by: Jim at January 4, 2015 09:49 PM