December 04, 2014
MITM watch - sitting in an English pub, get MITM'd
So, sitting in a pub idling till my 5pm, thought I'd do some quick check on my mail. Someone likes my post on yesterday's rare evidence of MITMs, posts a comment. Nice, I read all comments carefully to strip the spam, so, click click...
Boom, Firefox takes me through the wrestling trick known as MITM procedure. Once I've signalled my passivity to its immoral arrest of my innocent browsing down mainstreet, I'm staring at the charge sheet.
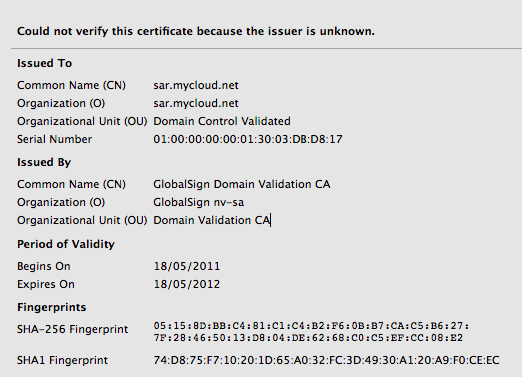
Whoops -- that's not financialcryptography.com's cert. I'm being MITM'd. For real!
Fully expecting an expiry or lost exception or etc, I'm shocked! I'm being MITM'd by the wireless here in the pub. Quick check on twitter.com who of course simply have to secure all the full tweetery against all enemies foreign and domestic and, same result. Tweets are being spied upon. The horror, the horror.
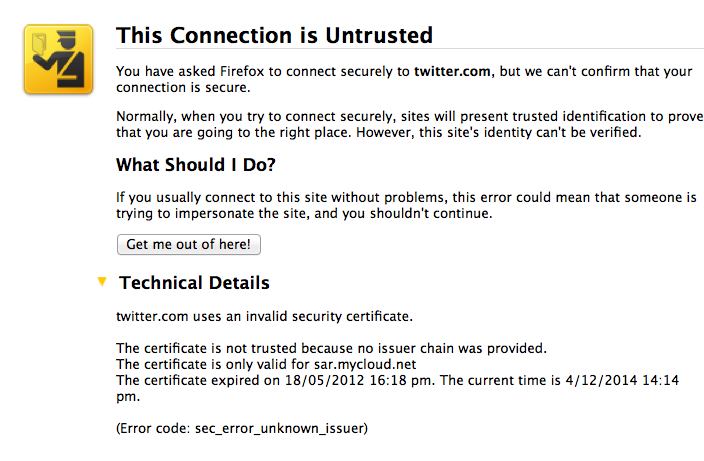
On reflection, the false positive result worked. One reason for that on the skeptical side is that, as I'm one of the 0.000001% of the planet that has wasted significant years on the business of protecting the planet against the MITM, otherwise known as the secure browsing model (queue in acronyms like CA, PKI, SSL here...), I know exactly what's going on.
How do I judge it all? I'm annoyed, disturbed, but still skeptical as to just how useful this system is. We always knew that it would pick up the false positive, that's how Mozilla designed their GUI -- overdoing their approach. As I intimated yesterday, the real problem is whether it works in the presence of a flood of false negatives -- claimed attacks that aren't really attacks, just normal errors and you should carry on.
Secondly, to ask: Why is a commercial process in a pub of all places taking the brazen step of MITMing innocent customers? My guess is that users don't care, don't notice, or their platforms are hiding the MITM from them. One assumes the pub knows why: the "free" service they are using is just raping their customers with a bit of secret datamining to sell and pillage.
Well, just another another data point in the war against the users' security.
Posted by iang at December 4, 2014 09:49 AM^ Like.
Your example makes me think that the proper response for an ideal browser encountering an authentication failure would be:
Server not found.
It's a bit austere I know, but essentially the browser is simply telling you that it is unable to connect with the authentic server you are seeking. Where you go from there is up to you, but "clicking through" is not an option.
So true...
I saw MITM on the public wifi at a U.S. federal agency. I won't say which one, but they are responsible for regulating things like... the internet. I pointed out the problem to their IT team and after an initial bout of confusion, they fixed the problem and claimed some vendor had set that up for them. Despite a full time security team of over a dozen people, nobody noticed the MITM except me (a part time contractor who only pops in periodically).
Whenever I see a non-technical user presented with a certificate error, they always click right through. I have a friend who's an MBA and is fairly security savvy (uses a password manager) and he reflexively clicked through a certificate error while _at a hotel in a foreign country_! (The badness of iOS certificate warnings borders on negligence.) It's just pure muscle memory. Average people have no idea what those certificates are supposed to be doing.
Posted by: Mark at December 4, 2014 04:40 PM