June 07, 2013
PRISM Confirmed: major US providers grant direct, live access to the NSA and FBI
 In an extraordinary clean sweep of disclosure from the Washington Post and the Guardian:
In an extraordinary clean sweep of disclosure from the Washington Post and the Guardian:
The National Security Agency and the FBI are tapping directly into the central servers of nine leading U.S. Internet companies, extracting audio and video chats, photographs, e-mails, documents, and connection logs that enable analysts to track foreign targets, according to a top-secret document obtained by The Washington Post.
The process is by direct connection to the servers, and requires no intervention by the companies:
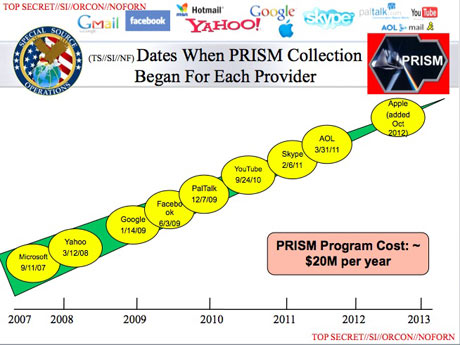
Equally unusual is the way the NSA extracts what it wants, according to the document: “Collection directly from the servers of these U.S. Service Providers: Microsoft, Yahoo, Google, Facebook, PalTalk, AOL, Skype, YouTube, Apple.”....
Dropbox, the cloud storage and synchronization service, is described as “coming soon.”
From outside direct access might appear unusual, but it is actually the best way as far as the NSA is concerned. Not only does it give them access at Level Zero, and probably better access than the company has itself, it also provides the victim supplier plausible deniability:
“We do not provide any government organization with direct access to Facebook servers,” said Joe Sullivan, chief security officer for Facebook. ....“We have never heard of PRISM,” said Steve Dowling, a spokesman for Apple. “We do not provide any government agency with direct access to our servers, ..." ....
“Google cares deeply about the security of our users’ data,” a company spokesman said. “We disclose user data to government in accordance with the law, and we review all such requests carefully. From time to time, people allege that we have created a government ‘back door’ into our systems, but Google does not have a ‘back door’ for the government to access private user data.”
Microsoft also provided a statement: “.... If the government has a broader voluntary national security program to gather customer data we don’t participate in it.”
Yahoo also issued a denial. “Yahoo! takes users’ privacy very seriously,” the company said in a statement. “We do not provide the government with direct access to our servers, systems, or network.”
How is this apparent contradiction possible? It is generally done via secret arrangements not with the company, but with the employees. The company does not provide back-door access, but the people do. The trick is to place people with excellent tech skills and dual loyalties into strategic locations in the company. These 'assets' will then execute the work required in secret, and spare the company and most all of their workmates the embarrassment.
Patriotism and secrecy are the keys. The source of these assets is easy: retired technical experts from the military and intelligence agencies. There are huge numbers of these people exiting out of the armed forces and intel community every year, and it takes only a little manipulation to present stellar CVs at the right place and time. Remember, the big tech companies will always employ a great CV that comes highly recommended by unimpeachable sources, and leapfrogging into a stable, very well paid civilian job is worth any discomfort.
Everyone wins. It is legal, defensible and plausibly deniable. Such people are expert at keeping secrets -- about their past and about their current work. This technique is age-old, refined and institutionalised for many a decade.
Questions remain: what to do about it, and how much to worry about it? Once it has started, this insertion tactic is rather difficult to stop and root out. At CAcert, we cared and a programme developed over time that was strong and fair -- to all interests. Part of the issue is dealing with the secrecy of it all:
Government officials and the document itself made clear that the NSA regarded the identities of its private partners as PRISM’s most sensitive secret, fearing that the companies would withdraw from the program if exposed. “98 percent of PRISM production is based on Yahoo, Google and Microsoft; we need to make sure we don’t harm these sources,” the briefing’s author wrote in his speaker’s notes.
But for the big US companies, is it likely that they care? Enough? I am not seeing it, myself, but if they are interested, there are ways to deal with this. Fairly, legally and strongly.

How much should we worry about it? That depends on (a) what is collected, (b) who sees it, and (c) who's asking the question?
There has been “continued exponential growth in tasking to Facebook and Skype,” according to the PRISM slides. With a few clicks and an affirmation that the subject is believed to be engaged in terrorism, espionage or nuclear proliferation, an analyst obtains full access to Facebook’s “extensive search and surveillance capabilities against the variety of online social networking services.”According to a separate “User’s Guide for PRISM Skype Collection,” that service can be monitored for audio when one end of the call is a conventional telephone and for any combination of “audio, video, chat, and file transfers” when Skype users connect by computer alone. Google’s offerings include Gmail, voice and video chat, Google Drive files, photo libraries, and live surveillance of search terms.
Firsthand experience with these systems, and horror at their capabilities, is what drove a career intelligence officer to provide PowerPoint slides about PRISM and supporting materials to The Washington Post in order to expose what he believes to be a gross intrusion on privacy. “They quite literally can watch your ideas form as you type,” the officer said.
Live access to everything, it seems. So who sees it?
My rule of thumb was that if the information stayed in the NSA, then that was fine. Myself, my customers and my partners are not into "terrorism, espionage or nuclear proliferation." So as long as there is a compact with the intel community to keep that information clean and tight, it's not so worrying to our business, our privacy, our people or our legal situation.
But there is no such compact. Firstly, they have already engaged the FBI and the US Department of Justice as partners in this information:
In exchange for immunity from lawsuits, companies such as Yahoo and AOL are obliged to accept a “directive” from the attorney general and the director of national intelligence to open their servers to the FBI’s Data Intercept Technology Unit, which handles liaison to U.S. companies from the NSA. In 2008, Congress gave the Justice Department authority for a secret order from the Foreign Surveillance Intelligence Court to compel a reluctant company “to comply.”
Anyone with a beef with the Feds is at risk of what would essentially be a corrupt bypass of the legal justice system of fair discovery (see this for the start of this process).
Secondly, their credibility is zero: The NSA has lied about their access. They have deceived most if not all employees of the companies they have breached. They've almost certainly breached the US constitution and the US law in gaining warrant-free access to citizens. Dismissively. From the Guardian:
"Fisa was broken because it provided privacy protections to people who were not entitled to them," the presentation claimed. "It took a Fisa court order to collect on foreigners overseas who were communicating with other foreigners overseas simply because the government was collecting off a wire in the United States. There were too many email accounts to be practical to seek Fisas for all."
The FISA court that apparently governs their access is evidently ungovernable, as even members of Congress cannot breach its secrecy.
And that's within their own country -- the NSA feels that it is under no such restrictions or niceties outside their own country.
A reasonable examination of the facts and the record of the NSA (1, 2, 3) would therefore conclude that they cannot be trusted to keep the information secret. American society should therefore be worried. Scared, even. The risk of corruption of the FBI is by itself enough to pull the plug on not just this programme, but the system that allowed it to arise.
What does it mean to foreign society, companies, businesses, and people? Not a lot different as all of this was reasonable anyway. Under the history-not-rules of foreign espionage, anything goes. The only difficulty likely to be experienced is when the NSA conspires with American companies to benefit them both, or when American assets interfere with commercial businesses that they've targetted as assisting enemies.
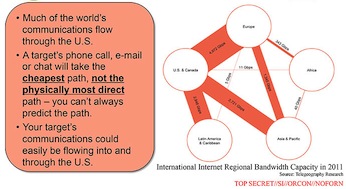
One thing that might now get a boost is the Internet in other countries:
The presentation ... noted that the US has a "home-field advantage" due to housing much of the internet's architecture.
Take note, the rest of the world!
Excellent analysis, Ian, particularly with respect to the surreptitious insertion of employees acting as spies.
Posted by: pc at June 7, 2013 08:11 AMWow this is some interesting stuff. I really like the "home-field advantage" analogy as well.
Posted by: john at June 13, 2013 07:01 AM