November 17, 2009
Timeline for an SSL protocol breach -- what's the size of your OODA loop?
SSL is a protocol that gives a point-to-point connection with some protection against MITM (man-in-the-middle). Attacks against SSL as a security paradigm can be characterised in three levels:
- within the protocol,
- within the application (but outside the protocol), and
- within the business (outside the application, but inside the personal relationships).
The reason we have to see this holistically, and include all three levels, is that SSL as a tool is worthless if the wider attacks are not dealt with, SSL is only valuable to the extent that they are dealt with, and SSL gets in the way to the extent that it imposes unreasonable responsibilities or expectations on the application or user.
Classical Phishing is the latter case, in that an email is sent to a user, who then clicks on a link. The application is not attacked, the "business" is. This is the MITM that caused the explosion in phishing around 2003. MITB (man-in-the-browser) is the next level down, attacking the application directly. The perverse linkage to the MITM of phishing is that the phishing explosion financed the move into application-level attacks.
 Now, all of that is security as it is delivered to users. There is then protocol security, and here SSL has generally excelled. It meets its internal protocol goals very well, and always has done so. Now news has surfaced of a rare thing: an in-protocol attack against SSL:
Now, all of that is security as it is delivered to users. There is then protocol security, and here SSL has generally excelled. It meets its internal protocol goals very well, and always has done so. Now news has surfaced of a rare thing: an in-protocol attack against SSL:
Members of an industry-wide consortium had been meeting in secret since late September to hash out a fix that will be rolled into thousands of individual pieces of hardware and software that implement the TLS protocol. The bug became public when it was disclosed by a researcher not involved in the project. So far, OpenSSL is the only provider that is close to releasing a patch, according to this status page.
How serious is this? Initial comments were that it was hard to exploit, but now news is filtering through that Anil Kurmus has written an exploit against Twitter.
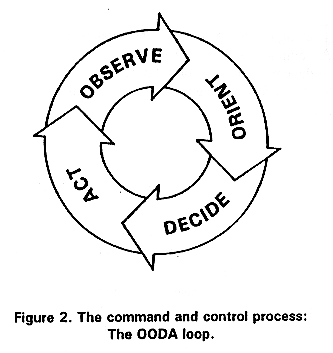
It's an evolving topic. What I find interesting however is that this represents a good event to make some OODA observations. Here's what I've gathered so far:
| "late September" | bug announced to industry consortium secretly? (name?) | 0m |
| 20091104 | public disclosure by Marsh Ray and Steve Dispensa | 2m |
| 20091110 | twitter exploit announced | 2m |
The interesting conclusion to draw here is we can possibly measure the size of the OODA loop for the SSL industry, at least in this one event.
And here is what is emerging over time:
| 20091207 | fix for Mozilla's NSS crypto library announced by Nelson Bolyard | 3m |
| 20100208 | Firefox nightly builds now include partial patch announced by Daniel Veditz | 5m |
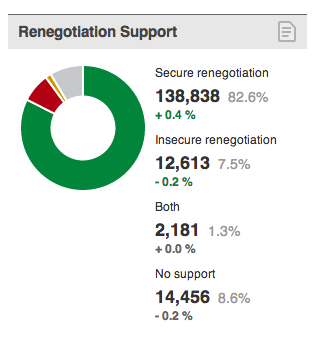
| 20130409 | SSL Pulse reports 80.3% of SSL sites patched and protected (picture shows 20130905) | 41m |
(Editor's note: Second table added and augmented after original publication.)
Posted by iang at November 17, 2009 10:46 AM | TrackBackFigure 2 is not Boyd's OODA loop.
Posted by: Purpleslog at March 12, 2012 10:35 PM