September 12, 2017
Over 1.65 Million Computers Infected With Cryptocurrency Miners in 2017 So Far
Over 1.65 Million Computers Infected With Cryptocurrency Miners in 2017 So Far
By Catalin Cimpanu
September 12, 2017 08:33 AM 0
Cryptocurrency mining malware evolution
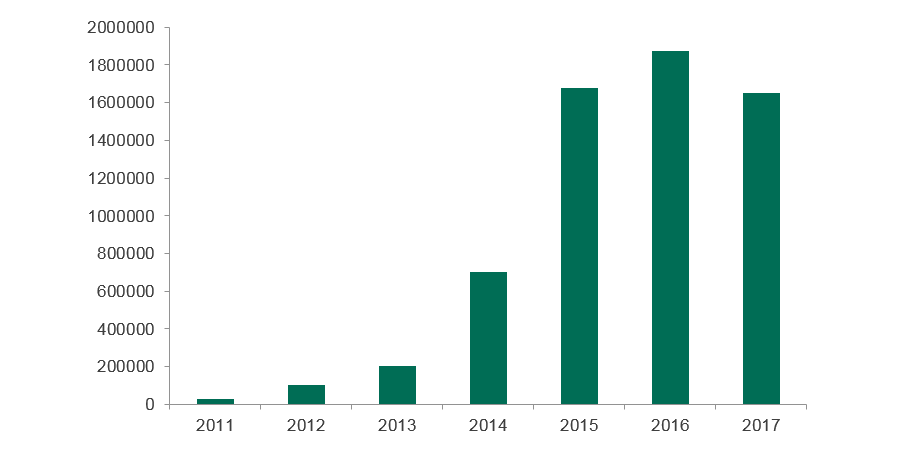
Telemetry data collected by Kaspersky Lab shows that in the first nine months of 2017, malware that mines for various types of cryptocurrencies has infected more than 1.65 million endpoints.
According to Kaspersky, detections for cryptocurrency mining trojans rose from a lowly 205,000 infections in 2013 to nearly 1.8 million in 2016, and 2017 looks like it will easily surpass that number.
Zcash and Monero miners on the rise
Of all virtual currencies, Zcash and Monero were the favorites, primarily because of their support for anonymous transactions, which comes in handy to anyone looking to hide a money trail from criminal operations.
While Monero is a long-time favorite of cryptocurrency mining trojans, Zcash is a recent addition, as the cryptocurrency launched only last November.
Nonetheless, one month later, several criminal mining operations had adopted the currency, with one group's earnings estimated at $75,000/year/~1,000 computers.
A review of past major operations
Since last year, the rise in cryptocurrency mining malware distribution was easily observable by the number of reports put out by cyber-security firms. Such reports often help infosec industry observers to gauge new trends.
Below is a list with the most important malware distribution campaigns that pushed cryptocurrency miners in 2017.
⬗ Terror Exploit Kit dropped a Monero miner back in January
⬗ Even some Mirai botnet variants tested a cryptocurrency mining function
⬗ Adylkuzz cryptocurrency miner deployed via EternalBlue NSA exploit
⬗ Bondnet botnet installed Monero miners on around 15,000 computers, mostly Windows Server instances
⬗ Linux.MulDrop.14 malware mines for cryptocurrency using Raspberry Pi devices exposed online
⬗ Crooks targeted Linux servers via SambaCry exploit to deploy EternalMiner malware.
⬗ Trojan.BtcMine.1259 miner uses NSA's DobulePulsar to infect Windows computers
⬗ DevilRobber cryptocurrency miner became the second most popular Mac malware in July
⬗ Linux.BTCMine.26, a Monero miner that included references to Brian Krebs in its source code.
⬗ CoinMiner campaign that used EternalBlue and WMI to infect users
⬗ Zminer trojan found infecting Amazon S3 servers
⬗ CodeFork gang used fileless malware to push a Monero miner
⬗ Hiking Club malvertising campaign dropped Monero miners via Neptune Exploit Kit
⬗ A CS:GO cheat that delivered a Monero miner for MacOS users
⬗ Jimmy banking trojan adds support for a Monero miner
⬗ New Monero miner advertised via Telegram
These are only some of the major campaigns, but there are countless of other smaller operations that went unreported.
If you're wondering why is this rise in cryptocurrency mining malware taking place, the answer is quite simple. During the past year, trading prices for virtual currencies have skyrocketed across the board, almost for all major cryptocurrencies. Bitcoin, Monero, Ethereum, Zcash, and others, have seen huge price spikes that have fueled market speculation and attracted both legitimate users and the criminal underground looking to make a quick buck.
I've copied this completely for the record as it forms the best evidence seen so far of the critical paper on Bitcoin's mining effects: Bitcoin & Gresham's Law - the economic inevitability of Collapse. Posted by iang at September 12, 2017 10:57 AM
Yes, I started research in 2010 - 2012 that collected data on Botnets and GPU mining.
GPUs always lead to criminal groups controlling the system. ASICs can resist malware and can be managed better such that malware is not an issue, hence no botnets
=====
100 ASICs (S9's) == a Botnet of 10 million hosts
So, the Botnet cannot win with ASICs
The Botnet ALWAYS wins with CPU/GPU as they do not pay power
=====
A GAMING SOFTWARE company has been slapped with a $1 million fine after secretly adding bitcoin mining software to a product update earlier this year.
....
Back in the spring, those 30 bitcoins were worth only a few thousand dollars, but at today's rates, it comes closer to $17,000.
The botnet's haul was so good because six months ago, serious gamers like ESEA's customers made excellent soldiers for a botnet army. Gaming machines have powerful graphical processing units that are pretty good at bitcoin mining. Since the spring, however, the bitcoin mining game has become a lot harder, and miners now use custom-designed chips to earn payouts on the bitcoin network.
Posted by: 2013 gaming company fined at November 14, 2017 08:49 AMTERRITORIAL BEHAVIOR AND THE ECONOMICS OF BOTNETS
Craig S Wright
School of Computing and Mathematics
Charles Sturt University
Wagga Wagga, NSW, Australia
Abstract
This paper looks at the economics associated with botnets. This research can be used to calculate territorial sizes for online criminal networks. Looking at the types of systems we can compare the time required to maintain the botnet against the benefits received. In doing this it will be possible to formulate economic defence strategies that reduce the benefits received through the control of the botnet. We look at the decision to be territorial or not from the perspective of the criminal bot-herder. This is extended to an analysis of territorial size. The criminal running a botnet seeks to maximize profit. In doing this they need analyse the costs expended and benefits received against the territorial size. The result is a means to calculate the optimal size of the botnet and the expected returns. This information can be used to formulate security strategies that are designed to reduce the profitability of criminal botnets.
Keywords
Botnets, Economics, Game theory, Internet Security, Malware
The world's largest oil pipeline operator reportedly had some of its computer systems affected by cryptocurrency mining malware.
Russian pipeline giant Transneft, according to Reuters, recently had to clear malware from its systems that clandestinely mined the privacy-oriented cryptocurrency monero. It's not clear how many computers were impacted, but Reuters quoted a senior Transneft official who referenced multiple "incidents" during which the malware was discovered.
"Incidents where the company's hardware was used to manufacture cryptocurrency have been found. It could have a negative impact on the productivity of our processing capacity," Transneft vice-president Vladimir Rushailo reportedly told company executives during a meeting yesterday.
Transneft said that it has moved to shore up its cybersecurity systems in order to prevent those kinds of malware from being downloaded onto its computer systems.
The pipeline company is one of the most high-profile firms to date to be affected by the malware, which effectively operates in the background of a computer and uses spare capacity to mine cryptocurrencies.
Several notable websites have been impacted in recent months, including a pay-per-view platform for Ultimate Fighting Challenge and an on-demand video service run by Showtime.
https://www.coindesk.com/mixed-mining-arts-ufc-website-removes-coinhive-cryptocurrency-code/
https://www.coindesk.com/reports-showtime-websites-used-secretly-mine-cryptocurrency/
According to a cybersecurity report published in October, the CoinHive monero mining software became the sixth-most malware that month.
Posted by: Monero Mining Malware Hits Russian Pipeline Giant Transneft at December 17, 2017 09:48 AM‘A lot of geek clients were really excited when I taught them how to build a mining rig for me so they could mine 24/7 from their home.’
Posted by: OK, not your ordinary abuse: This dominatrix made men mine $1 million in cryptocurrency for her at December 20, 2017 01:44 PM... Exploiting a crucial competitive advantage and motivated by profit and a desire to learn the technology, students around the world are launching cryptocurrency mining operations right from their dorm rooms. In a typical mining operation, electricity consumption accounts for the highest fraction of operational costs, which is why the largest bitcoin mines are based in China. But within Mark’s dorm room, MIT foots the bill. That gives him and other student miners the ability to earn higher profit margins than most other individual miners. ...
Posted by: The secret lives of students who mine cryptocurrency in their dorm rooms at January 9, 2018 04:19 AM...
The goal of this article, is to explain how can be done the attack of MITM (Man(Person)-In-The-Middle) to inject some javascript in the html pages, to force all the devices connected to a WiFi network to be mining a cryptocurrency for the attacker.
The objective is to have a script that performs autonomous attack on the WiFi network. It’s what we have called CoffeeMiner, as it’s a kind of attack that can be performed in the cafes WiFi networks.
...
When Stensul CEO Noah Dinkin visited a Starbucks in Buenos Aires recently, he probably didn’t expect to be served some sneaky cryptocurrency miner code along with his coffee. But thanks to the store’s internet provider, that’s exactly what he got.
“Hi Starbucks, did you know that your in-store wifi provider in Buenos Aires forces a 10 second delay when you first connect to the wifi so it can mine bitcoin using a customer's laptop?” Dinkin tweeted on December 2. “Feels a little off-brand.” Dinkin wrote that Bitcoin was the digital currency being mined, but CoinHive, the company that provided the code for the miner, only works with Monero, a competing coin.
Surreptitious cryptocurrency mining has become a bit of a phenomenon of late. The value of digital currencies is skyrocketing across the board, so companies and websites are getting in on the gold rush by injecting a user’s browser with code that hijacks their processing power to generate digital tokens. This process, known as “mining,” is resource-intensive and can significantly impact performance.
Read More: A 'Fortnite' Cheat Maker Duped Players Into Downloading a Bitcoin Miner
On December 11, Starbucks responded to Dinkin’s tweet, acknowledging the issue and announcing that it’s been resolved. ...
Posted by: Starbucks Wi-Fi Hijacked People's Laptops to Mine Cryptocurrency at January 11, 2018 04:45 PM... The ads contain JavaScript that mines the digital coin known as Monero. In nine out of 10 cases, the ads will use publicly available JavaScript provided by Coinhive, a cryptocurrency-mining service that's controversial because it allows subscribers to profit by surreptitiously using other people's computers. The remaining 10 percent of the time, the YouTube ads use private mining JavaScript that saves the attackers the 30 percent cut Coinhive takes. Both scripts are programmed to consume 80 percent of a visitor's CPU, leaving just barely enough resources for it to function. ...
Posted by: Now even YouTube serves ads with CPU-draining cryptocurrency miners at January 28, 2018 06:44 PMWe saw a pretty big event take place over the weekend where a 3rd party provider was compromised and their JS library was altered. The alteration introduced a crypto mining script that was then subsequently included on over 4,000 websites that I know of, many of which were Government websites...
Posted by: CryptJackin! at February 11, 2018 06:28 PMMiners and more
Amid the cryptocurrency boom, cybercriminals are increasingly moving away from ‘classic robbery’ to a new method of making money from their victims – namely mining cryptocurrency using the resources of an infected computer. All they have to do is run a mining client on the victim computer and specify the details of their cryptocurrency wallet.
Scenario #1
...
Ummm, so yeah, this is *bad*. I just had @phat_hobbit point out that @ICOnews has a cryptominer installed on their site... 😮
(and dozens of other pages...)
Posted by: cryptominers... at February 13, 2018 07:05 PMAttacker has generated about $2,000 in digital coin so far in a scam that remains active.
DAN GOODIN - 1/17/2018, 10:20 PM
Satori—the malware family that wrangles routers, security cameras, and other Internet-connected devices into potent botnets—is crashing the cryptocurrency party with a new variant that surreptitiously infects computers dedicated to the mining of digital coins.
A version of Satori that appeared on January 8 exploits one or more weaknesses in the Claymore Miner, researchers from China-based Netlab 360 said in a report published Wednesday. After gaining control of the coin-mining software, the malware replaces the wallet address the computer owner uses to collect newly minted currency with an address controlled by the attacker. From then on, the attacker receives all coins generated, and owners are none the wiser unless they take time to manually inspect their software configuration.
Records show that the attacker-controlled wallet has already cashed out slightly more than 1 Etherium coin. The coin was valued at as much as $1,300 when the transaction was made. At the time this post was being prepared, the records also showed that the attacker had a current balance of slightly more than 1 Etherium coin and was actively mining more, with a calculation power of about 2,100 million hashes per second. That's roughly equivalent to the output of 85 computers each running a Radeon Rx 480 graphics card or 1,135 computers running a GeForce GTX 560M, based on figures provided here.
...
Posted by: New botnet infects cryptocurrency mining computers, replaces wallet address at February 15, 2018 05:37 AMSurreptitious mining of cryptocurrency by hackers is spreading very, very fast.
The news: Over 4,000 websites, including those of the US federal judiciary and the UK National Health Service, have been weaponized by hackers to mine the cryptocurrency Monero on their behalf.
How it worked: Hackers injected malware into a widely used plug-in called Browsealoud that reads web pages our loud as a way of helping partially sighted people navigate the internet. The malware is based on the popular app Coinhive, a piece of software that uses processing power on someone’s device to mine cryptocurrency. The malicious version of the app does this without people's knowledge, coopting their computing power to enrich hackers.
Why it matters: Cryptojacking is rapidly becoming one of the world’s biggest cyberthreats. This news shows how easy it is for crooks to spread the trick, by infecting a single product used across multiples sites with a single hack.
Posted by: A cryptojacking attack hit thousands of websites, including government ones at February 15, 2018 09:09 PMAuthorities in China have arrested a man for allegedly stealing a significant amount of power in order to fuel a clandestine cryptocurrency mine.
Police in the eastern Chinese province of Anhui Province seized more than 200 computers used for bitcoin and ether mining after the local power grid company reported a spike in electricity use, according to Xinhua news agency.
One suspect allegedly stole 150,000 kW hours of electricity between April and May 2018, when the power grid first alerted police of the theft. The Chinese national, identified only by his surname Ma, reportedly told police that he dreamed of making money through crypto mining.
He bought the hardware in April, but later found out the daily power cost was over 6,000 yuan ($921). As a result, Ma said, his mining operation was not profitable at the time of his arrest.
Allegations of power theft have led to the arrest of bitcoin miners in China before. In April, there were at least two cases where bitcoin miners were taken into custody for allegedly stealing power, as previously reported by CoinDesk.
In another instance, six individuals were arrested in Tianjin. Police alleged that the suspects used 600 cryptocurrency miners to generate bitcoin with power taken from the local power grid. Xinhua News agency said that this may have been the "largest power theft case in recent years."
Posted by: Chinese Police Arrest Crypto Miner for Power Theft at June 25, 2018 07:54 AMIn most cases, fake Flash updates pushing malware are not very stealthy. In recent years, such imposters have often been poorly-disguised malware executables or script-based downloaders designed to install cryptocurrency miners, information stealers, or ransomware. If a victim runs such poorly-disguised malware on a vulnerable Windows host, no visible activity happens, unless the fake updater is pushing ransomware.
However, a recent type of fake Flash update has implemented additional deception. As early as August 2018, some samples impersonating Flash updates have borrowed pop-up notifications from the official Adobe installer. These fake Flash updates install unwanted programs like an XMRig cryptocurrency miner, but this malware can also update a victim’s Flash Player to the latest version.
Because of the legitimate Flash update, a potential victim may not notice anything out of the ordinary. Meanwhile, an XMRig cryptocurrency miner or other unwanted program is quietly running in the background of the victim’s Windows computer. ...
Posted by: Fake Flash Updaters Push Cryptocurrency Miners at October 18, 2018 01:47 AMMonero (XMR) is by far the most popular cryptocurrency among criminals deploying mining malware, according to a new study.
Two researchers, Sergio Pastrana and Guillermo Suarez-Tangil, from Universidad Carlos III de Madrid and King's College London, respectively, published their report last week, estimating that hackers have mined at least 4.32 percent of the total monero in circulation.
Pastrana and Suarez-Tangil write:
"Overall, we estimate there are at least 2,218 active campaigns that have accumulated about 720K XMR (57M USD). Interestingly just a single campaign (C#623) has mined more than 163K XMR (18M USD), which accounts for about 23% of the total estimated. This campaign is still active at the time of writing."
...
Posted by: Crypto Mining Malware Has Netted Nearly 5% of all Monero, Says Research at January 10, 2019 09:27 AM7 years after we called the cancer that is criminal activity in Bitcoin-like cryptocurrencies, here comes a report that suggests that 4.3% of Monero mining is siphoned off by criminals. ...
Posted by: see also... Gresham's Law thesis is back - Malware bid to oust honest miners in Monero at January 11, 2019 05:33 PM