December 13, 2005
GP2 - Growth and Fraud - Instructing Security at GP
In the previous discourse (Meet at the Grigg Point), we discussed how growth works, and said that GP was the tipping point at which the demo became a system. From this model, we can make a number of observations, chief of which is about Security to which we now turn.
One of the security practitioner's favourite avisos is to suggest that the security is done up front, completely, securely, with strong integration, not to mention obeisance. Imagine the fiercely wiggling finger at this point. Yet, this doctrine has proven to be a disaster and the net's security pundits are in the doldrums over it all. Let's examine some background before getting to how GP helps us with this conundrum.
Hark to the whispering ghosts of expired security projects. Of those that took heed of the doctrine, most failed, and we do mean most. Completely and utterly, and space does not permit a long list of them, but it is fair to say that one factor (if not the sole or prime factor) is that they spent too much on security and not enough on the biz.
Some systems succeeded though, and what of them? These divide into three:
- those that implemented the full model,
- those that implemented a patchwork or rough security system, and
- those that did nothing.
Of those few systems that heeded the wiggling finger and succeeded, we now have some substantial experience. Heavily designed and integrated systems that succeeded initially went on to expose themselves to ... rather traumatic security experiences. Why? In the worst cases, when the fraud started up (around GP) it simply went around the security model, but by that time the model was so cast in mental concrete that there was no flexibility to deal with it. One could argue that these models stopped other forms of fraud, but these arguments generally come from managers who don't admit the existence of the current fraud, so it's an argument designed to be an argument, not something that pushes us forwards.
Perversely, those systems that did nothing had an easier time of it than even those that implemented a patchwork, because they had nothing to battle.
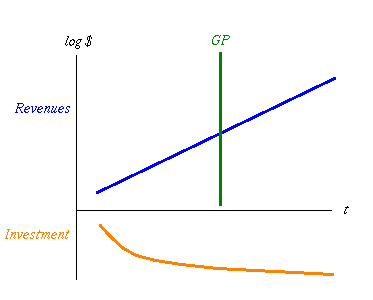
fig 4. Investment directs the Revenue Curve
Why is this? I conjecture that at the beginning of a project the business model is not clear. That is, none of us really knows what to do, but darn it we're inspired! Living and dreaming in Wonderland as we are, this suggests that the business model migrates very quickly, which means that it isn't plausible to construct a security model that lasts longer than a month. Which means several interlinked things:
- until the business model is proven, there is little point in building a security model for security per se as an unproven model doesn't deserve to be protected,
- the more attention that is put into the security model, the more the security model kicks back and insists that the business model stop changing, dammit!,
- the more money that is put into the security model, the less money there is available for business activity, and
- the security system puts a cost on the whole system, slowing growth.
Now, anyone who's aware of compounding knows where to put the value: building the business, and security rarely if ever builds business, what it does is protect business that is already there. It's the issue of compounding we turn to now. Figure 4 depicts the cost of investment down below the horizontal axis, and the growth above. Investment isn't exponential, so it's not a straight line. Initially it grows well, but then hits limits to growth which doom it to sub-exponential growth, which is probably just as well as any investor I've met prefers less than exponential growth in contributions!
While not well depicted in that figure, consider that the pattern of investment fundamentally sets the growth model. The Orange line dictates the slope and placement of the Blue!
Now let's fiddle a bit in figure 5. Assume that investment is fixed. But we've decided to invest upfront in a big way in security, because that's what everyone said was the only way to sleep well at nights. Now the Orange Region of total investment over time is divided into two - above the thin line is what we invest in the business, and below the line is the security. The total is still the same, so security investment has squeezed us upfront.
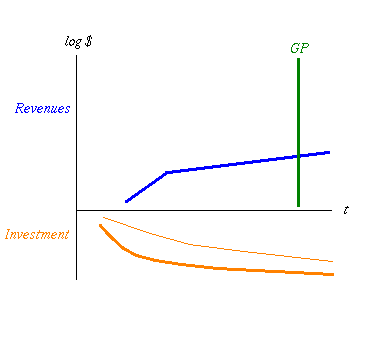
fig 5. More Costs means Growth is Flatter and GP is Later
See what happens? Because resources were directed away from business, into security, the growth curve started later, and when the security model kicked in, the curve flattened up. That's because all security has a cost. If you're lucky, and your security team is hot (and I really do mean blistering here, see what I wrote about "most" above...) the kink won't be measurable.
Why is it so big? And why don't managers wade in there with mallet and axe and bash it back into forward growth before we can say hedonism is the lifeblood of capitalism? Oddly, the chances of a manager seeing it are pretty remote because seeing drivers to growth is a very hard art, most people just can't see things like that and assume that either today goes for ever, or tomorrow will solve everything. The end users often notice it, and respond in one of two ways: they scream and holler or they stop using the system. An example of the former is from the old SSL days when businesses screamed that it sucked up 5 times the CPU ... so they switched to hybrid SSL/raw sites. An example of the latter is available every time you click on a link and it asks you to register for your free or paid account to read an article or to respond to an article.
Students of security will be crying foul at this point because security does good. So they say. In fact what it does is less bad: until we draw in the fraud curve which security nicely attempts to alleviate the bad done by fraud, security is just a cost. And a deadweight one at that. Which brings us to our third observation: the upfront attention to security has pushed GP way over to the right, as it must do if you agree with the principle of GP.
So where is all this leading us? At this point we should understand that security is employed too early if employed at the beginning - the costs incur a dramatic shift of the curve of growth. Both to the right, and a flattening due to the additional drain. And we haven't even drawn in the other points above: restarts and kickback.
This logic says that we should delay security as long as we can, but this can't go on forever. The point where the security really kicks in and does less bad is when the bad kicks in: the fraud curve that slides up and explodes after GP. Then, the ideal point in which to kick security is after GP and before the fraudulent red line runs in ink onto the balance sheet.
Which leads us to question - finally, for some, no doubt - When is GP?. That is saved to another day :-)
Posted by iang at December 13, 2005 07:22 PM | TrackBackThe implied security prior to formalization from a business standpoint is always present and the investment beyond what is foreseen within the implied security will never be sold or funded beyond the shock and awe type sale. So Mr. X buys ribbons from Mr. Y they come in and if Mr. X likes what he sees Mr. Y gets paid. Until one day Mr. X decides to see what happens if he tells Mr. Y that the cardboard box was empty and since there are no ribbons Mr. Y will not be paid. Mr. X is telling a lie and Mr. Y knows this because he packed the box with the ribbons himself. The boundaries have eroded between these two merchants based on a fraud being committed against Mr. Y. The solution needs to be derived by the injured party so Mr. Y implements a signed receipt and bill of laiding policy and never accepts and order from Mr. X again without prepayment. If Mr. X keeps pulling the same trick on other ribbon merchants information might pass from merchant to merchant and a network of untrustworthy X type people is circulated. We have a defensive response that has used a cultural tool of passing important information against a common enemy. The first instance of security being needed was caused by a loss and the expansion of that security to include a more advanced method of a circulated list was caused by more losses.
The first question to ask prior to designing a security response to a threat is what is the merciless kick between the legs that will render you useless? Addressing the nightmare is always fun and reveals the imagined threat from the real one. What if scenarios are always fun if the participants are symmetrical in nature and transactional behavior. The next series of examinations must address the asymmetrical attack scenarios like advanced participants taking advantage over less advanced. It is my experience that a lesser funded brokerage firm must always ask beg and demand proper payment from a more well funded one. At the same time well funded brokers always ask for extra special favors and demand bargains with little or no treatment in kind. In this sense the standards of practice in the United States are upside down the banks sells you goods but does not deliver yet all the customer receives is accusations against their intelligence. Microsoft sell snake oil and highly suspect software but it is the consumer that poor dum slob of a user that messes everything up. By implementing a campaign against the injured party US participants in commerce have stopped a security response by those they hurt. The culture of kicking the guy while he is down and lifting him up based upon an arbitrary need to look virtuous has rendered the discussion of security useless in the this culture and as it spreads variants they infest other cultures and has evolved into more complex structures and even improved. The globalization of fraudulent practices is advancing to the level that security is questioned as a proper response rather than simply passing the ball around. As a result there are no more medium sized brokerage firms, no middle class, no affordable housing, no reasonable value for money spent on food, and no educated population to respond. We are lost in the tyranny of the consumed society one that is eaten from the inside out starting with the soul. So the issue is what is the cost effective manner to implement a security design from within an established business? I think that what sells is what will be done and that is tied to the arbitrary nature of the fates so when it becomes sexy to be secure or at least claim to be then money will be spent with no regard for the reward. I expect that any day a Czar will be proclaimed at Micronoodle and declare security to be the number one priority and they will brand the shit of it. You will think one Micronoodle and security within a fraction of a second. So how will Micronoodle achieve this lofty task , it is simple they will lie about it. Once the beating up of the consumer proves to be uneconomical they will create posse composed of those same consumers to ferret out the bad people and Sheriff Bill will clean up Dodge City. Micronoodle will create a parade and lead the band of course after someone else has thought of it and shown it works. So get your rope ready for a hanging and grease up the old tuba where gonna have a hanging and a brass band show all in one as soon as Google starts to create public forums for reported theft of id, child porn, stock manipulation, and whatever else comes along. John Wayne did not appear as a major movie star until after the World Wars and the demographic was composed of those that did not serve. Battle envy so expect your best buddy on the net to see chance to be the Micronoodle undercover agent of the month by reporting you for using another name to sign in with so no one knows your id and watch this get taken to a level of insanity that knows no bounds. Security is the next big boom and it will be a bursting bubble so jump on board and forget about logical assumptions its time to sell snake oil to the masses let Brother Bill lead the way.