June 22, 2005
Google payment system confirmed - let the trimming of tall poppies begin
Google confirms they are doing a payment system. It may be like Paypal's but I wouldn't bet on it. Google claims it will be unlike. Either way a new sport is about to erupt in the payments systems world - sniping at Google's payments system.
Let's just be clear about this - it already has a name, it's called chopping down the tall poppies. This is a game of envy and spite. It comes because a successful player uses its money and muscle to take on a new field in which others have failed, when all the smart people knew how to get in there but couldn't muster that money and muscle (in this case, I'm referring to cognitive muscle as well as user base muscle).
It's going to happen so get used to it, guys. I'll go first: I'll bet you didn't think of this:
I was opening up my almost brand new Dell 600m laptop, to replace a broken PCMCIA slot riser on the motherboard. As soon as I got the keyboard off, I noticed a small cable running from the keyboard connection underneath a piece of metal protecting the motherboard.

I figured "No Big Deal", and continued with the dissasembly. But when I got the metal panels off, I saw a small white heatshink-wrapped package. Being ever-curious, I sliced the heatshrink open. I found a little circuit board inside.
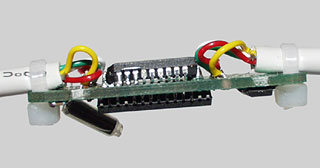
Being an EE by trade, this piqued my curiosity considerably. On one side of the board, one Atmel AT45D041A four megabit Flash memory chip.
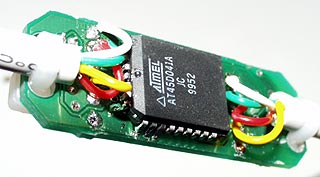
On the other side, one Microchip Technology PIC16F876 Programmable Interrupt Controller, along with a little Fairchild Semiconductor CD4066BCM quad bilateral switch.

Looking further, I saw that the other end of the cable was connected to the integrated ethernet board.What could this mean? I called Dell tech support about it, and they said, and I quote, "The intregrated service tag identifier is there for assisting customers in the event of lost or misplaced personal information." He then hung up.
A little more research, and I found that that board spliced in between the keyboard and the ethernet chip is little more than a Keyghost hardware keylogger.
The reasons Dell would put this in thier laptops can only be left up to your imagination. It would be very impractical to hand-anylze the logs, and very CPU-intensive to do so on a computer for every person that purchased a dell laptop. Why are these keyloggers here? I recently almost found out.
I called the police, as having a keylogger unknown to me in my laptop is a serious offense. They told me to call the Department of Homeland Security. At this point, I am in disbelief. Why would the DHS have a keylogger in my laptop? It was surreal.
So I called them, and they told me to submit a Freedom of Information Act request. This is what I got back:

Google are entering into the payments system world at a dangerous time. This could be a unique time in the history of payments systems, simply because all those theoretical threat models that we have all trained with, sweated over and loved for a decade or more, now, are coming true. There's one you'll have to deal with, and you won't have the luxury of saying "oh, that's not our problem" this time.
This change has occurred in these pages mostly under the cover of a runctous attack on the idle ostriches of the browser world. Phishing is just the headline, but the real story is that there is now an industrial scale threat to payment systems. Some very few engineers know how to deal with these threats on a real basis - primarily those grounded in European banking experience - but for the most part a lot of the payments systems are learning the hard way right now.
For google, the lessons will be different. There will be no breathing space, no easy ramp up to the critical mass. It is I predict highly likely that from day one, attention will bear down on them from the phishing attackers. I suspect google will weather the security storm, but that's only a guess. The problem here is that there is a difference between facing statistical or safety threats and the aggressive crook. Security goods are different because they have an unruly third party in the transaction.
It will also shoot all the profitability figures to outhouse. Because the attacks will take up a larger support component per transaction than expected then there will be only a loss-leader rationale for the payments system for many a year. I would still do it, but I'm a strategic kinda guy, still if google are in this for anything but the long term, save yourselves the trouble and exit stage left now. Or cull your team of short term thinkers.
(There is a perfect face-saving way out, but it'll cost the price of a Dell *equivalent* laptop ;-) )
(Expect Dell laptops to drop like a stone if this pans out...)
(Expect all hell to break loose if this is true...)
(Are we living in interesting times again?)
(But even if not true, it's the perfect description of a "today" threat model!)
(Looks like we have confirmation ... see comments below!)
Posted by iang at June 22, 2005 09:21 AM | TrackBack(Adam Shostack, CC: cryptography, Wed Jun 22 15:04:45 2005)
On Wed, Jun 22, 2005 at 01:54:34PM +0100, Ian Grigg wrote:
| A highly aspirated but otherwise normal watcher of black helicopters asked:
|
| > Any idea if this is true?
| > (WockerWocker, Wed Jun 22 12:07:31 2005)
| > http://c0x2.de/lol/lol.html
|
| Beats me. But what it if it was true. What's your advice to
| clients?
"Duuude, stop buying Dell."
The Secret service isn't part of DHS. DHS seal is different. The photos don't really show that cable in a laptop, and if they do, they don't show it in a Dell laptop.
It is most likely a hoax:
http://www.boingboing.net/2005/06/16/conspiracy_theory_of.html
As to your second question. There are several options available to you depending on your level of paranoia:
1. Run a personal firewall (assuming you can find one that doesn't have a trojan that talks back to the manufacturer <cough> zone alarm </cough> ).
2. Monitor and review all traffic that flows from your ethernet card using Ethereal, TCPDump or some other program.
3. Use an on-screen keyboard.
allan
Hi Iang,
> It's going to happen so get used to it, guys. I'll go first: *I'll
> bet you didn't think of this:*
>
> http://c0x2.de/lol/lol.html
Its a hoax... it had me going for a while, I even sent it out to a couple of friends based on your email.
http://www.engadget.com/entry/1234000317047049/
I suppose keyghost loggers as easily available tho.
Cheers,
-v.
--
https://rayservers.com/
Computers. Installed Secure. OpenPGP. AES Encrypted HD. Colocation.
Tel:+1-607-546-7300 Fax:+1-607-546-7387 Skype: rayservers
PGP/GPG Key: https://rayservers.com/keys/0x12430522.asc
4856 01AB F8BA E0EB F128 A57F 59D9 16FD 1243 0522
Your Privacy and Security are our Business [TM]
They will use a brokerage firm because of the loopholes a national as in US payment system cost $6 Million in net capital with little or no value added a Broker Dealer captures the payments and the capital markets. Google sees this and will not buy the banking scenario. Google will adopt a multi-currency money market and avoid the banks like the plague. You must ask yourself who is the most influencial person at Google? The answer will tell you what direction they are heading. That person is Tim Armstrong a Paul Allen student and a microcurrency dude. Google will mint I tell you and mint from within a brokerage firm just like mutual funds do.
"Tim Armstrong presides over Google's US advertising sales and operations effort as leader of the company's national sales team. Armstrong has gained wide recognition as a proponent of online advertising and is frequently asked to present to industry leaders on how best to generate online advertising ROI.
"Armstrong joined Google from Snowball.com. As that company's vice president of Sales and Strategic Partnerships, he managed a team of 100 people and built the revenue foundation needed to take the company public in just 16 months. Armstrong was also responsible for key strategic partnerships that included equity and marketing investments by New Line Cinema and an exclusive partnership with the NFL.
"Prior to his role at Snowball.com, Armstrong served as national sales manager for IDG's first Internet magazine, I-Way before founding and serving as director of Integrated Sales & Marketing at Starwave's and Disney's ABC/ESPN Internet Ventures. Armstrong is a graduate of Connecticut College with a double major in Economics and Sociology.
Posted by: Jimbo at June 22, 2005 10:52 AMhttp://c0x2.de/lol/lol.html is BS; the same photos appear at http://www.dansdata.com/keyghost.htm.
Posted by: JD at June 22, 2005 11:23 AM>> http://c0x2.de/lol/lol.html
googling 'dell keylogger' certainly turns up a lot of sites who insist that this is a hoax.
> Beats me. But what it if it was true. What's your advice to clients?
Um, be suspicious of keyboard changes? Bring your own if you're paranoid? Remove any "harmless" extension cables that suddenly attach themselves? Most server-class hardware already has 'tamper-detection' hardware that
will warn you if the machine has been opened, which should cover the "internal keylogger" case...
(suggests reasons why Dell was picked)
http://www.ioerror.us/2005/06/17/keylogger-found-in-dell-laptop/
Posted by: InfoDept at June 22, 2005 11:29 AMAllan Liska wrote:
> 3. Use an on-screen keyboard.
For extra points, try Dasher.
http://www.inference.phy.cam.ac.uk/dasher/
Posted by: Ben Laurie at June 23, 2005 04:10 AMGuys, do you really believe that any "decent IQ value" PC manufacturer whould build a mega visible device in tiny laptops to spy on your keyboard? No need to comment further . ROTFL.