October 19, 2018
AES was worth $250 billion dollars
So says NIST...
10 years ago I annoyed the entire crypto-supply industry:
Hypothesis #1 -- The One True Cipher Suite In cryptoplumbing, the gravest choices are apparently on the nature of the cipher suite. To include latest fad algo or not? Instead, I offer you a simple solution. Don't.
There is one cipher suite, and it is numbered Number 1.
Cypersuite #1 is always negotiated as Number 1 in the very first message. It is your choice, your ultimate choice, and your destiny. Pick well.
The One True Cipher Suite was born of watching projects and groups wallow in the mire of complexity, as doubt caused teams to add multiple algorithms- a complexity that easily doubled the cost of the protocol with consequent knock-on effects & costs & divorces & breaches & wars.
It - The One True Cipher Suite as an aphorism - was widely ridiculed in crypto and standards circles. Developers and standards groups like the IETF just could not let go of crypto agility, the term that was born to champion the alternate. This sacred cow led the TLS group to field something like 200 standard suites in SSL and radically reduce them to 30 or 40 over time.
Now, NIST has announced that AES as a single standard algorithm is worth $250 billion economic benefit over 20 years of its project lifetime - from 1998 to now.
h/t to Bruce Schneier, who also said:
"I have no idea how to even begin to assess the quality of the study and its conclusions -- it's all in the 150-page report, though -- but I do like the pretty block diagram of AES on the report's cover."
One good suite based on AES allows agility within the protocol to be dropped. Entirely. Instead, upgrade the entire protocol to an entirely new suite, every 7 years. I said, if anyone was asking. No good algorithm lasts less than 7 years.
Crypto-agility was a sacred cow that should have been slaughtered years ago, but maybe it took this report from NIST to lay it down: $250 billion of benefit.
In another footnote, we of the Cryptix team supported the AES project because we knew it was the way forward. Raif built the Java test suite and others in our team wrote and deployed contender algorithms.
October 10, 2018
Market for Scans
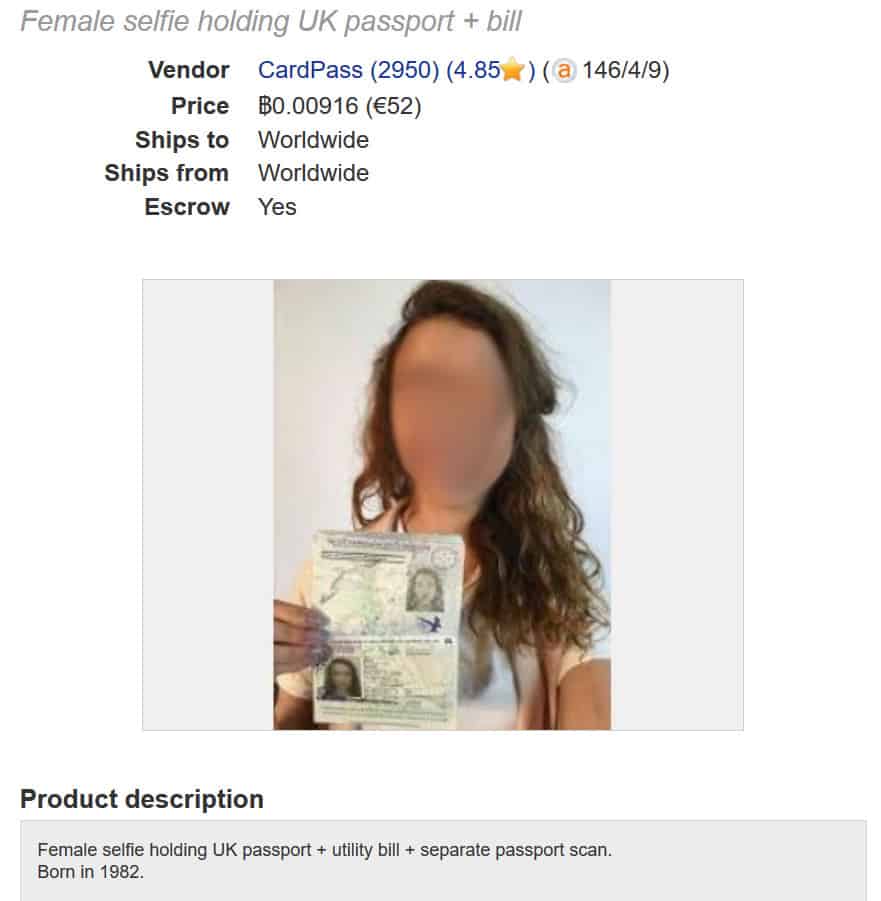
That's the market for scanned passports, not scammed passports, but hey!
From comparitech comes research on what it takes to get digital scans for opening KYC/AML procedures - presumably bank accounts.
Here are our key findings:
- The average price of a digital passport scan is $14.71.
- If proof of address or proof of identification -- a selfie, utility bill and/or driverís
- license -- is added to a passport scan, the average price jumps to $61.27.
- Australian passport scans were the most common, and yet, the most expensive ($32).
- The average price of a real, physical passport is $13,567.
- The average price of a counterfeit, physical passport is $1,478.
Aside from a lot of interesting detail on scans and templates, here's the real deal:
Authentic, state-issued passports are hard to come by and cost a lot, ranging from $8,216 (Germany) to $17,116 (UK). The average price of the eight supposedly genuine passports was $13,567. At least one vendor claims these passports came from "our corrupt immigration police contacts," though we have no way of verifying this. In many cases buyers are given the option to specify what details are included in the passport, including stamps for specific countries.
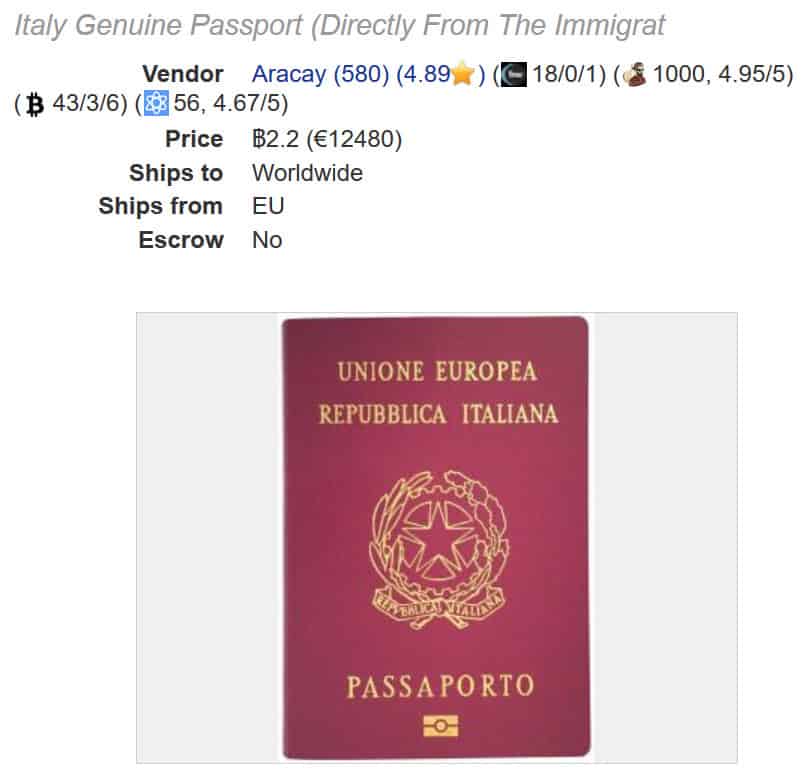
This puts a little more colour on the rough benchmark of a thousand per set - this might predict that any passport in such a deal needs to be a forgery. Or, I suspect there may be several distinct marketplaces - this research by comparitech was over "dark web" online interfaces where you as purchaser exchange your money for the goods/docs online, primarily with Bitcoin. Other research has worked with migrant channels where hard-at-luck locals are giving up their physical documents and reporting them stolen/lost.
Commentary on this will have to wait for another day.