December 30, 2013
MITMs conducted by the NSA - 50% success rate
One of the complaints against the SSL obesity security model was that all the blabber of x.509/CAs was there to protect against the MITM (man-in-the-middle) attack. But where was this elusive beast?
Now we have evidence. In the recent Der Spiegel article about the NSA's hacking catalogue, it is laid out pretty comprehensively:
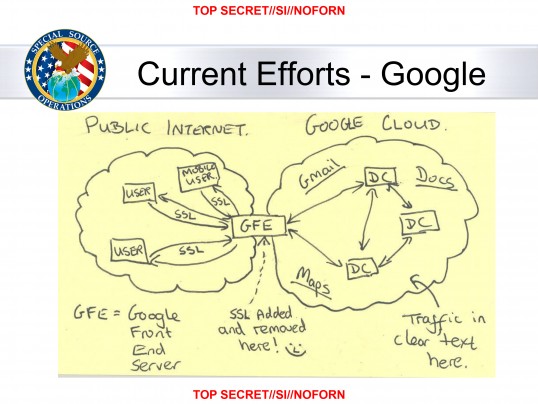
A Race Between ServersOnce TAO teams have gathered sufficient data on their targets' habits, they can shift into attack mode, programming the QUANTUM systems to perform this work in a largely automated way. If a data packet featuring the email address or cookie of a target passes through a cable or router monitored by the NSA, the system sounds the alarm. It determines what website the target person is trying to access and then activates one of the intelligence service's covert servers, known by the codename FOXACID.
This NSA server coerces the user into connecting to NSA covert systems rather than the intended sites. In the case of Belgacom engineers, instead of reaching the LinkedIn page they were actually trying to visit, they were also directed to FOXACID servers housed on NSA networks. Undetected by the user, the manipulated page transferred malware already custom tailored to match security holes on the target person's computer.
The technique can literally be a race between servers, one that is described in internal intelligence agency jargon with phrases like: "Wait for client to initiate new connection," "Shoot!" and "Hope to beat server-to-client response." Like any competition, at times the covert network's surveillance tools are "too slow to win the race." Often enough, though, they are effective. Implants with QUANTUMINSERT, especially when used in conjunction with LinkedIn, now have a success rate of over 50 percent, according to one internal document.
We've seen some indication that wireless is used for MITMs, but it is a difficult attack, as it requires physical presence. Phishing is an MITM, and has been in widespread use, but like apocyphal saying from Star Wars, these MITMs "aren't the droids you're looking for." Or so say the security experts behind web encryption standards.
This one is the droid we're looking for. A major victim is identified, serious assets are listed, secondary victims, procedures, codenames, the whole works. This is an automated, industrial-scale attack, something that breaches the normal conceptual boundaries of what an MITM looks like. We can no longer assume that MITMs are too expensive for mass use. Their economic applicability is presumably enabled the NSA operates a shadow network, capable of attacking the nodes in ours:
The insert method and other variants of QUANTUM are closely linked to a shadow network operated by the NSA alongside the Internet, with its own, well-hidden infrastructure comprised of "covert" routers and servers. It appears the NSA also incorporates routers and servers from non-NSA networks into its covert network by infecting these networks with "implants" that then allow the government hackers to control the computers remotely.
 Tantalising stuff for your inner geek! So it seems we now do need protection against the the MITM, in the form of the NSA. For real work, and also for Facebook, LinkedIn and other entertainment sites because of their universality as an attack vector. But will SSL provide that? In the short term and for easier cases, yes. But not completely, because most set-ups are ill-equiped to deal with attacks at an aggressive level. Until the browser starts mapping the cert to the identity expected, something we've been requesting for a decade now, it just won't provide much defence.
Tantalising stuff for your inner geek! So it seems we now do need protection against the the MITM, in the form of the NSA. For real work, and also for Facebook, LinkedIn and other entertainment sites because of their universality as an attack vector. But will SSL provide that? In the short term and for easier cases, yes. But not completely, because most set-ups are ill-equiped to deal with attacks at an aggressive level. Until the browser starts mapping the cert to the identity expected, something we've been requesting for a decade now, it just won't provide much defence.
Certificate pinning is coming, but so is Christmas, DNSSec, IPv6 and my guaranteed anti-unicorn pill. By the time certificate pinning gets here, the NSA will likely have exfiltrated every important site's keys or bought off the right CA so it doesn't matter anyway.
One question remains: is this a risk? to us?
In the old Security World, we always said we don't consider the NSA a risk to us, because they never reveal the data (unless we're terrorists or drug dealers or commies or Iranians, in which case we know we're fair game).
That no longer holds true. The NSA shares data with every major agency in the USA that has an interest. They crossed the line that cannot be crossed, and the rot of ML seizure corruption, economic espionage and competitive intervention means that the NSA is now as much a threat to everyone as any other attacker.
Every business that has a competitor in USA. Every department that has a negotiation with a federal agency. Every individual that has ever criticised the status quo on the Internet. We're all at risk, now.
Oh, to live in interesting times.
Posted by iang at December 30, 2013 01:39 AM | TrackBack