April 22, 2008
Paypal -- Practical Approaches to Phishing -- open white paper
Paypal has released a white paper on their approach to phishing. It is mostly good stuff. Here are their Principles:
1. No Silver Bullet -- We have not identified any one solution that will single-handedly eradicate phishing; nor do we believe one will ever exist. ...2. Passive Versus Active Users -- When thinking about account security, we observe two distinct types of users among our customers. The first and far more common is the “passive” user. Passive users expect to be kept safe online with virtually no involvement of their own. They will keep their passwords safe, but they do not look for the “s” in https nor will they install special software packages or look for digital certificates. The active user, on the other hand, is the “see it/touch it/use it” person. They want two-factor authentication, along with every other bell and whistle that PayPal or the industry can provide. Our solution would have to differentiate between and address both of these groups.
3. Industry Cooperation -- PayPal has been a popular “target of opportunity” for criminals due to our large account base of over 141 million accounts2 and the nature of our global service. However, while we may be an attractive target, we are far from the only one. Phishing is an industry problem, and we believe that we have a responsibility to help lead the industry toward solutions that help protect consumers – and the Internet ecosystem as a whole.
4. Standards-based -- A preference for solutions based on industry standards could be considered a facet of industry cooperation, but we believe it’s important enough to stand on its own. If phishing is an industry problem, then industry standard solutions will have the widest reach and the least overhead – certainly compared to proprietary solutions. For that reason, we have consistently picked industry standard solutions.
(Slightly edited.) That's a good start. The white paper explores their strategy, walks through their work with email signing. Short message: tough! No mention of the older generation technologies such as OpenPGP or S/MIME, but instead, they create plugins to handle their signatures:
To reach the active users who do not access their email through a signature-rendering email client, PayPal started working with Iconix, which offers the Truemark plug-in for many email clients. The software quickly and easily answers the question of “How do I know if a PayPal email is valid?” by rewriting the email inbox page to clearly show which messages have been properly signed.
That's by way of indicating how poorly tools designed in the early 90s from poor security analysis and wrong threat models are coping with real threats.
Next part is their work with the browser. It starts:
4.1 Unsafe browsersThere is of course, a corollary to safer browsers – what might be called “unsafe browsers.” That is, those browsers which do not have support for blocking phishing sites or for Extended Validation Certificates (a technology we will discuss later in this section). In our view, letting users view the PayPal site on one of these browsers is equal to a car manufacturer allowing drivers to buy one of their vehicles without seatbelts. The alarming fact is that there is a significant set of users who use very old and vulnerable browsers, such as Microsoft’s Internet Explorer 4 or even IE 3. ...
Unsafe Browsers are a frequent complaint here and in other places. Some good stuff has been done, but it was too little, too late, and we now see the unfortunate damage that has been done. One of these effects was that it is now up to the big website operators, in this case PayPal, to start policing the browsers. Old versions of IE are to be blocked, and a recent warning shot indicates that browsers that don't support EV will be next.
Next point: Paypal worked through several strategies. Three years ago, they pushed out a Toolbar (similar to the one listed on this blog). However this only works for those who download toolbars, a complaint frequently mentioned. So then Paypal, shifted to working with Microsoft to adopt the technology into IE7, and now they have ridden the adoption curve of IE7 for free.
Again this is exactly what should have been done: try it in toolbars then adopt it in the browser core. A cheap hint was missed and an expensive hit was scored:
4.4 Extended Verification SSL CertificatesBlocking offending sites works very well for passive users. However, we knew we needed to provide visual cues for our active users in the Web browser, much like we did with email signatures in the mail client.
Fortunately, the safer browsers helped tremendously. Taking advantage of a new type of site certificate called ‘Extended Validation (EV) SSL Certificates,’ newer browsers such as IE 7 highlight the address bar in green when customers are on a Web site that has been determined legitimate. They also display the company name and the certificate authority name. So, by displaying the green glow and company name, these newer browsers make it much easier for users to determine whether or not they’re on the site that they thought they were visiting.
This is a mixture of misinformation and danger for PayPal. The good part is that the browser, which is the authority on the CAs, now states definitively "Which Site" and also "Who says!" Green is a nice positive colour, too.
So, when this goes wrong, as it will, the user has more information in order to seek solutions. This shifting of the information back to the user (whether they want it or not) will do much more to causing the alignment of liabilities.
The bad part is that the browsers did not need a proprietary solution dressed up in a consortium in order to do this. They had indeed added the colour yellow (Firefox) and company name themselves, and the CA name has been an idea that I pushed repeatedly. For the record, Verisign asked for it early on as well. There's nothing special in the real business world about asking for "who says so?"
So we now have a structural lock-in placed in the browsers which they could have done for free, on their own initiative. Where does this go from here? Well, it certainly helps PayPal in the short term (in the same way that they could have said to users "download Firefox, check the yellow bar and company name"). But beyond that, I see dangers. As I have frequently written about the costs of the security approach before, I'll skip it now.
Overall, though, I'm pleased with the report. They have recognised that the industry has no solutions (no "silver bullets") and they have to do it themselves. They've implemented many different strategies, discarded some and improved others. Did it work? Yes, see the graph.
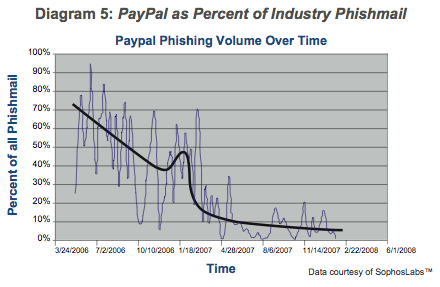
Best of all, they've taken the wraps off and published their findings. One of the clear indications from recent research and breach laws is that opening up the information is critical to success, and that starts with the website people. It's your job, do it, but that doesn't mean you have to do it alone! You can help each other by sharing industry-validated results, which are the only ones of any value.
To conclude, there are some other strategies that I'll suggest, and if PayPal are reading this, then they too can ask what's going on here:
a. Get TLS/SNI into Apache and IIS. Why? So that virtual hosted sites -- the 99% -- can use TLS. This will lead grass-roots-style to an explosion in the use of TLS.
Why's that helpful? (a) it will raise the profile of TLS work enourmously, and that includes server-side and browser-side practices. It will help to re-direct all these resources above into security work in the browser. Right now, 1% of activity is in TLS. Priorities will change dramatically when that goes to 10%, and that means we can count on the browser teams to spend a whole lot more time on it. And (b) if all traffic goes over TLS, this reduces the amount of security work quite considerably because everything is within the TLS security model. Paypal already figured this as "more or less all" their stuff is now under TLS, including the report!
All browsers have already done their bit for TLS/SNI. Webservers are the laggards. Ask them.
b. Hardened browser. Now that Firefox, IE and others have done some work to push attacks away from the user, the phishers are attacking the browsers from the inside. So there is a need to really secure the inside against attacks. Indeed Paypal already noted it in the report.
c. Hardened website. This means *reducing the tech.* The more you please your users, the more you please your attackers.
d. 2-channel authentication over the transaction. Okay, that's old news, but it bears repeating, because my online payment provider can only give me one of those old RSA fobs.
e. The browser website interface is here to stay. Which means we are stuck with a pretty poor combination. What's the long term design path? Here's one view: it starts with client-side certificates and opportunistic cryptography. Why? Because otherwise, transactions are naked and vulnerable, and your efforts are piecemeal.
Which means, don't replace the infrastructure wholesale, but re-tune it in the direction of security. Read the literature on secure transactions, none of it was ever employed in ecommerce, so it means there are lots of opportunities left for you :)
(Firefox and IE are both doing early components in this area, so ask them what it's about!)
f. Finally, bite the bullet and understand that your users will revolt one day, if you continue to keep fees high through industry-wide cooperation on lackadaisical fraud practices. High fraud and high loss means high fees which means high profits. One day the users will understand this, and revolt against your excuse. The manner this works is already well known to PayPal and it will happen to you, unless you adopt a competitive approach to fraud and to fees.
Posted by iang at April 22, 2008 02:27 PM | TrackBackmajority of the information involved in the naked transaction metaphor has additional issues. This is the kindergarten security 101 theme related to security proportional to risk.
a couple recent posts
http://www.garlic.com/~lynn/aadsm28.htm#60 Seeking expert on credit card fraud prevention - particularly CNP/online transactions
http://www.garlic.com/~lynn/aadsm28.htm#64 Seeking expert on credit card fraud prevention - particularly CNP/online transactions
a large amount of the information subject to common leakage/breaches (resulting in fraudulent activity) is worth upwards of one hundred times more to the attackers than the typical value to the defenders. the result is that frequently the attackers can afford to spend 100 times more than the defenders can afford to spend. older post discussing the subject
http://www.garlic.com/~lynn/2001h.html#61
the solution to naked transaction metaphor includes changing the paradigm ... both armoring the transaction as well as eliminating the value of the information to the attacker (since in the current paradigm ... that the attacker will always have the incentive to significantly outspend the defender).
Posted by: Lynn Wheeler at April 22, 2008 05:15 PMI came to distrust the laptop or PC many years ago and see nothing to change my mind. I use it as a communication tool and to make pretty pictures and documents-- in fact, Microsoft hasn't done anything for me, since the 1980s. In fact, their contributions, along with the rest of the software industry, have been nothing but fight with each other over how to extract the most rents by blocking the public from gaining communication or applications we could have built years ago for ourselves.
I've come to conclude, years ago, there's not going to be reliable or private communication over the Internet until the public is allowed to have a secure computer of some sort.
For starters it would be nice to have a hardened device that can at least send and receive small text messages, with some kind of reliable encryption and signatures. Among other things this would allow us to sign contracts, buy and sell, and vote in polls and elections. It would allow persistent reputation to begin to emerge.
I just cannot help but view all these phishing problems, and the deliberately inadequate solutions, with disdain.... I could be wrong but after the last 20 years, I'm kind of getting the message that the powers that be, don't want us to be able to use general computing and communication at all. They just want us dumb barefoot and pregnant, working at our workstations in large, centralized corporations, for subsistence wages.
Posted by: Todd Boyle at April 26, 2008 07:42 PMIt seems paypal is working through very serious security bugs, and refuses to roll back.
http://www.theregister.co.uk/2008/05/27/paypal_glitch_weighs_on_merchants/
Today I saw a live demo of a XSRF Attack, i would guess it is something serious like that, that makes them shutdown a important functionality of their system.