September 16, 2005
PayPal protected with Trustbar and Petnames
Here's how your Paypal browsing can be protected with Trustbar:
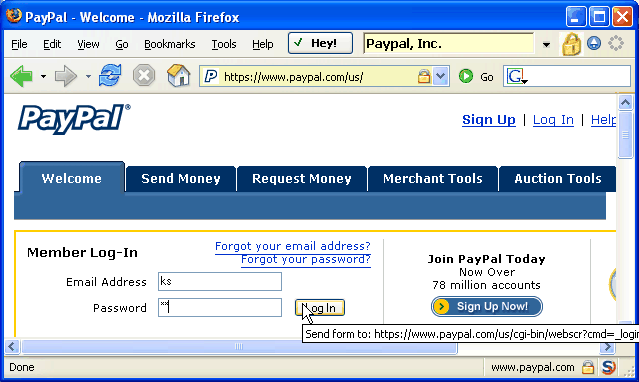
Apologies for the huge image! Notice the extra little window that has "PayPal, Inc" in it. That's a label that indicates that you have selected this site as one of your trusted ones. You can go even further and type in your own label such as "Internet money" or "How I Pay For Things" in which case it will turn green as a further indicator that you're in control.
This label of yours is called a petname, and indicates that Trustbar has found the certificate that you've labelled as PayPal. And, as that's the certificate used to secure the connection, it is really your Paypal you are talking to, not some other bogus one.
Trustbar also allows you to assign logos to your favourite sites. These logos allow you to recognise more quickly than words which site you are at. (Scribblers note: there are more screen shots at Trustbar's new help page.)
These are simple powerful ideas and the best we have at the moment for phishing. You can do the same thing with the Petname toolbar which just implements the own-label part. It's smaller, neater, and works on more platforms such as OSX and FreeBSD, but is not as powerful.

One thing that both of these tools rely heavily upon is SSL. That's because the SSL certificate is the way they know that it's really the site - if you take away the certificate then there is no way to be sure, and we know that the phishers are generally smart enough to trick any maybes that might be relied upon.
Trustbar allows you to assign a name to a site that hasn't SSL protection - but Petnames does not. In this sense, Trustbar says that most attacks occur outside SSL and we should protect against the majorit of attacks, whereas Petnames draws a line in the sand - the site must be using SSL and must be using a certificate in order to make reliable statements. Both of these are valid security statements, and will eventually converge over time.
For security insiders, Philipp posts news of a recent phishing survey. I've skimmed it briefly and it puts heady evidence on the claim that phishing is now institutionalised. Worth a visit!
The Economy of Phishing: A survey of the operations of the phishing marketChristopher Abad
Abstract:
Phishing has been defined as the fraudulent acquisition of personal information by tricking an individual into believing the attacker is a trustworthy entity. Phishing attacks are becoming more sophisticated and are on the rise. In order to develop effective strategies and solutions to combat the phishing problem, one needs to understand the infrastructure in which phishing economies thrive.We have conducted extensive research to uncover phishing networks. The result is detailed analysis from 3,900,000 phishing e-mails, 220,000 messages collected from 13 key phishing-related chat rooms, 13,000 chat rooms and 48,000 users, which were spidered across six chat networks and 4,400 compromised hosts used in botnets.
This paper presents the findings from this research as well as an analysis of the phishing infrastructure.
Closing notes. This page I am updating as new info comes in.
nother note for journalists: over at the Anti-fraud mailing list Anti-Fraud Coffee Room you can find the independent researchers who are building tools based on the nature of the attack, not the current flavour of the month.
Posted by iang at September 16, 2005 09:35 AM | TrackBackIan, few comments on your entry:
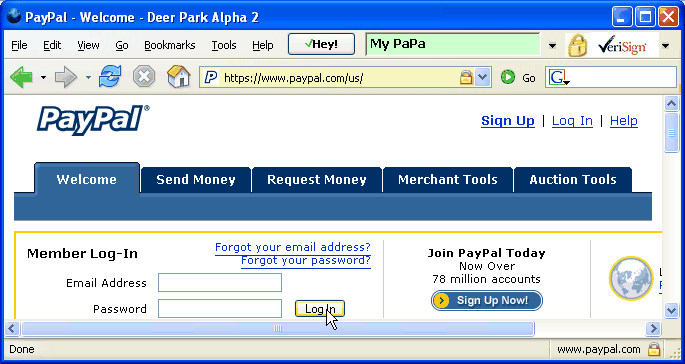
In your screen shot of TrustBar you evidently did _not_ select the name PayPal, Inc. yourself... Like, I suspect, many users, you simply used the automatically-presented identifier (PayPal, Inc.) which TrustBar extracted from PayPal's certificate...
If you _would_ have assigned your own, chosen name to the site, e.g. My PP, this will be marked with green background, see enclosed...
And I think to complete the picture, it would be nice to also show the screen with a user-chosen logo.
One last comment: at the end, you said:
> One thing that neither of those tools will do is work without SSL.
That's not quite true for TrustBar; we allow users to assign names/logos also for unprotected sites. Without SSL, this by itself does not protect users from MITM, but as you often wrote, most attacks, at least so far, were by weaker attackers, so this does provide some value.
Furthermore, in our new releases, we are adding some defenses (even against MITM) for the important case of unprotected login sites (some already available); I'll describe these in separate note.
Best, Amir
Posted by: Amir at September 18, 2005 07:49 AM